Since June 2022, Maltego has launched a new social media campaign that provides Maltego users and investigators with cheat sheets showing how to best use our Hub items for certain workflows. Check out the Investigator Toolkit December roundup in this article!
Investigator Toolkit: Quick Starts to Using Maltego Hub Items in Real-life Investigations 🔗︎
Presented to you by Maltego, the Investigator Toolkit series showcases each Maltego Transform Hub item with a sample workflow applicable to certain types of investigations. This series aims to help you quickly learn how to include a particular Hub item in your existing workflows.
Where to Find the Investigator Toolkit? 🔗︎
You can find the Investigator Toolkit series on our Twitter and LinkedIn channels, with the hashtags #MaltegoMonday and #InvestigatorToolkit. Every Monday, each Investigator Toolkit post comes with a workflow cheat sheet and a blog article or webinar as an additional demonstration.
All Previous Investigator Toolkit Roundups 🔗︎
- Investigator Toolkit July 2022
- Investigator Toolkit August 2022
- Investigator Toolkit September 2022
- Investigator Toolkit October 2022
- Investigator Toolkit November 2022
Investigator Toolkit October Roundup 🔗︎
In December, we featured the following four Hub items and their use cases in the Investigator Toolkit series:
Let’s dive straight into how to use these Hub items for threat intelligence investigation, threat actor group investigation, malware investigation, and threat hunting investigation!
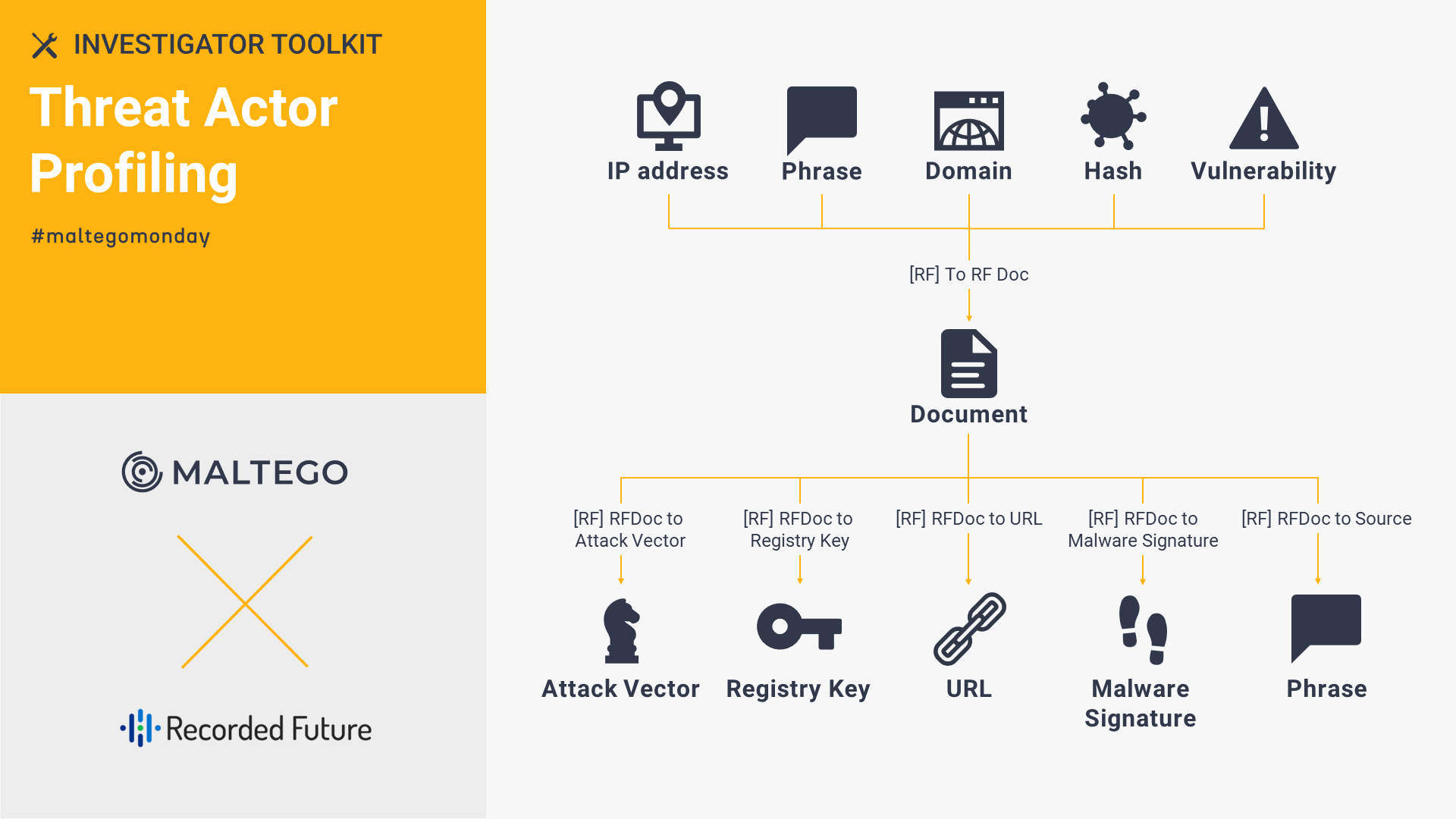
Recorded Future: Threat Actor Profiling 🔗︎
To understand your adversaries and the current and upcoming risks, you can build a threat actor profile with Recorded Future by pasting a Phrase Entity containing country names. See how we profile a threat actor with SOCMINT by combining Recorded Future and Silobreaker.
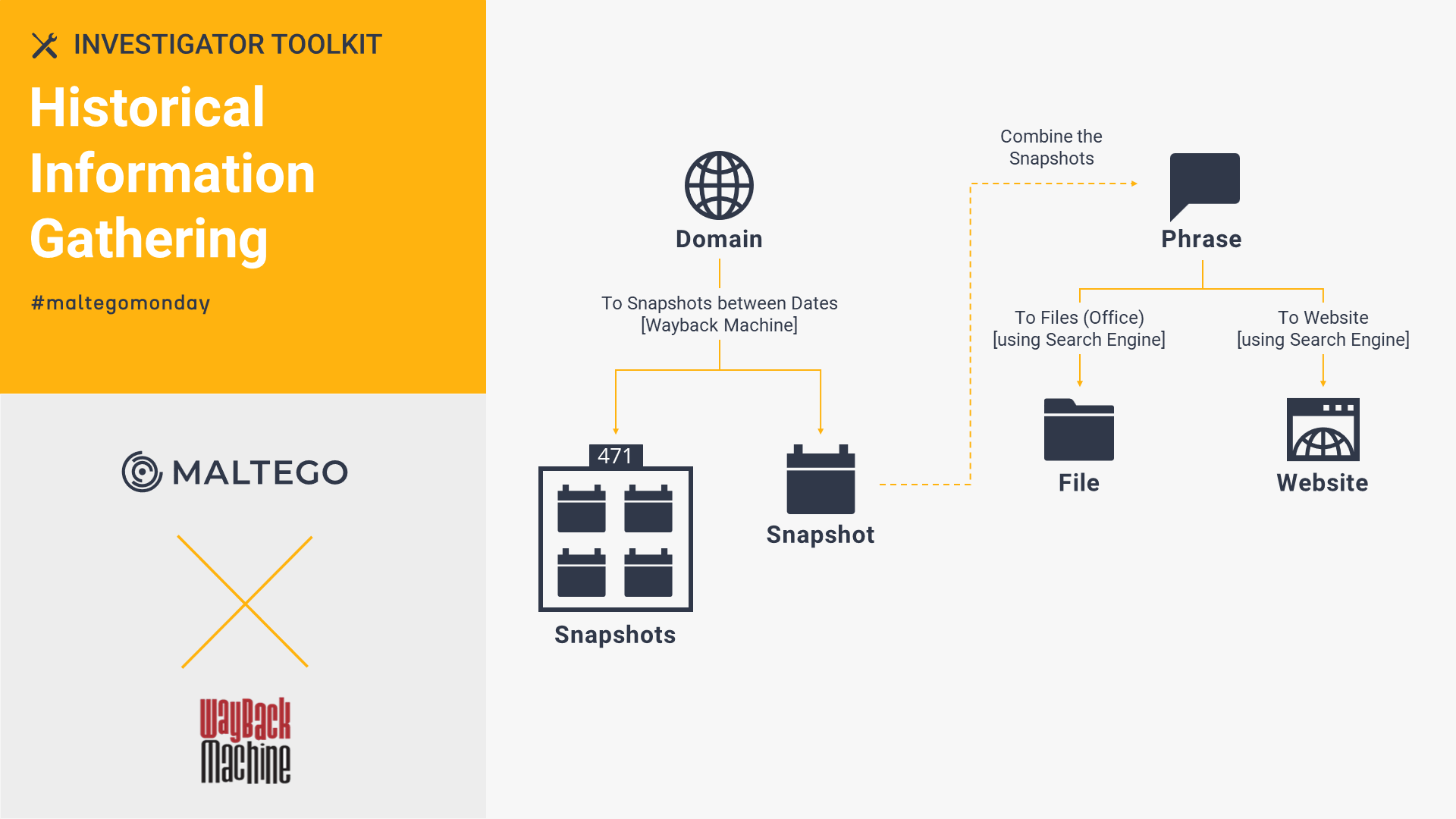
Wayback Machine: Historical Information Gathering 🔗︎
To gather information on historical events, take advantage of the Wayback Machine Transforms in Maltego to fetch snapshots of deleted pages, hidden files, and changed content. See how we combine Wayback Machine and Maltego Standard Transforms to research dark web chatter of a shooting, a patent dispute, and an authoritarian news agency.
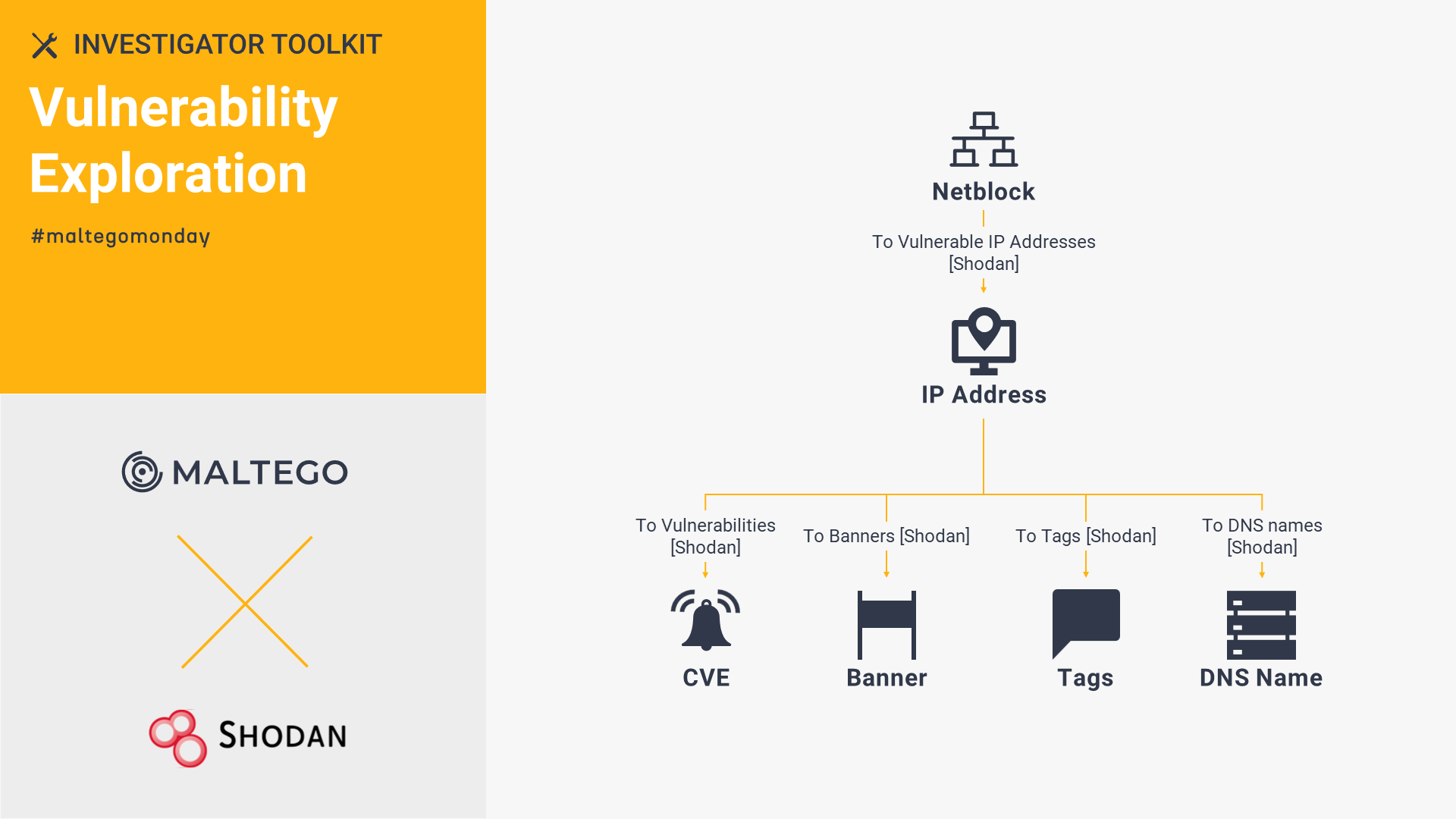
Shodan: Vulnerability Exploration 🔗︎
Shodan helps organizations reduce possible risks by exploring a network’s vulnerability and risk landscape. Looking from the angle of a CERT or Red Team analyst, we exemplify how to investigate unpatched servers and thus protect proprietary systems with Shodan in Maltego.
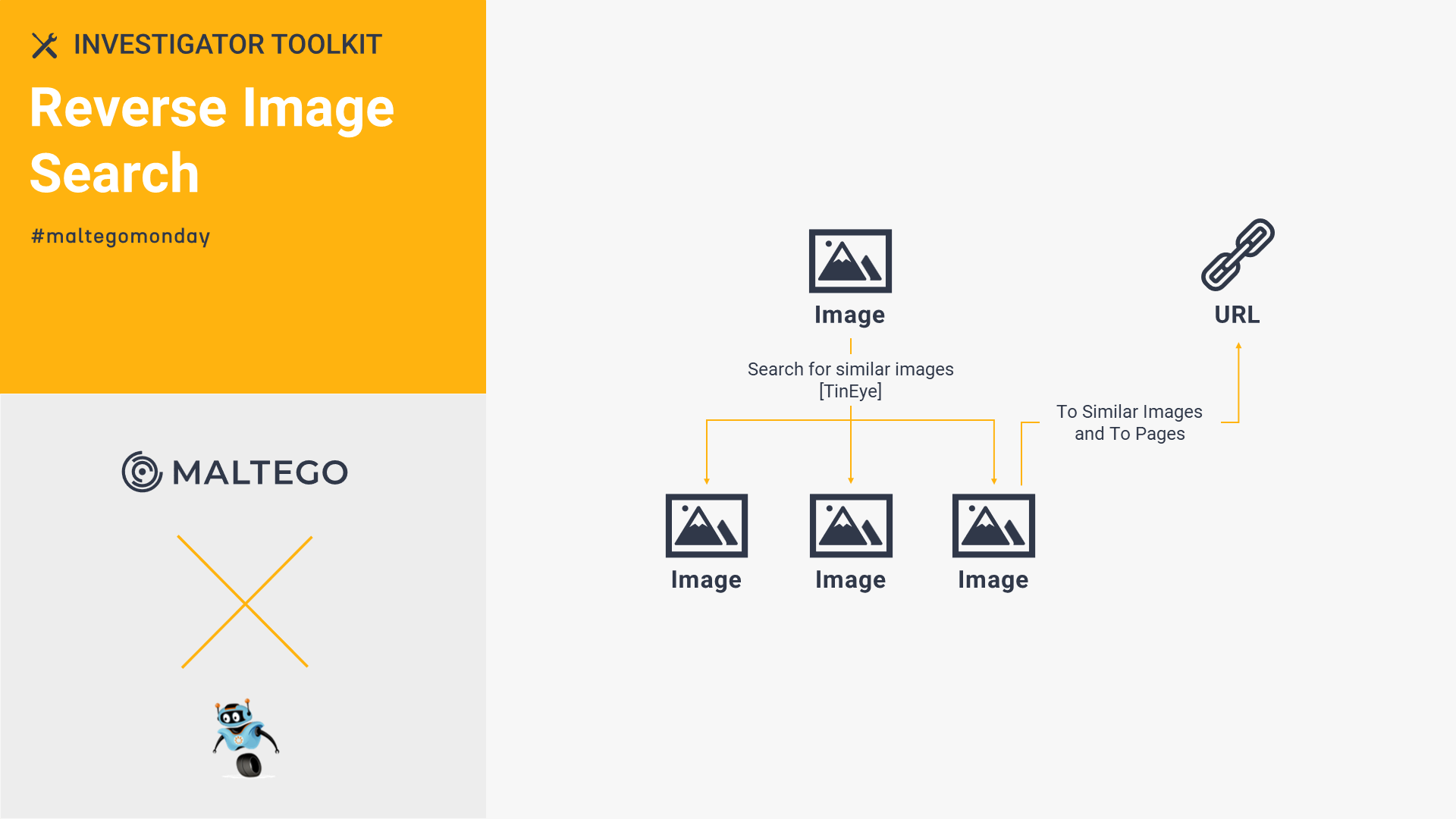
TinEye: Reverse Image Search 🔗︎
TinEye helps investigators monitor and identify the weaponized memetic content used to spread propaganda, misinformation, and disinformation. You can track the spread of a single image or uncover the connections between multiple images with TinEye. See how we conduct reverse image research in Maltego.
Check out the Investigator Toolkit series now! 🔗︎
In the following months, we will continue digging into different Hub items available in Maltego and providing best practice tips for investigators.
Follow us on Twitter and LinkedIn now to make sure you don’t miss any updates!
Happy Investigating!