Since June 2022, Maltego has launched a new social media campaign that provides Maltego users and investigators with cheat sheets showing how to best use our Hub items for certain workflows. Check out the Investigator Toolkit October roundup in this article!
Investigator Toolkit: Quick Starts to Using Maltego Hub Items in Real-life Investigations 🔗︎
Presented to you by Maltego, the Investigator Toolkit series showcases each Maltego Transform Hub item with a sample workflow applicable to certain types of investigations. This series aims to help you quickly learn how to include a particular Hub item in your existing workflows.
Where to Find the Investigator Toolkit? 🔗︎
You can find the Investigator Toolkit series on our Twitter and LinkedIn channels, with the hashtags #MaltegoMonday and #InvestigatorToolkit. Every Monday, each Investigator Toolkit post comes with a workflow cheat sheet and a blog article or webinar as an additional demonstration.
All Previous Investigator Toolkit Roundups 🔗︎
Investigator Toolkit October Roundup 🔗︎
In October, we featured the following five Hub items and their use cases in the Investigator Toolkit series:
Let’s dive straight into how to use these Hub items for Bitcoin investigation, network footprinting, attack surface management, malware identification, or IP address investigation!
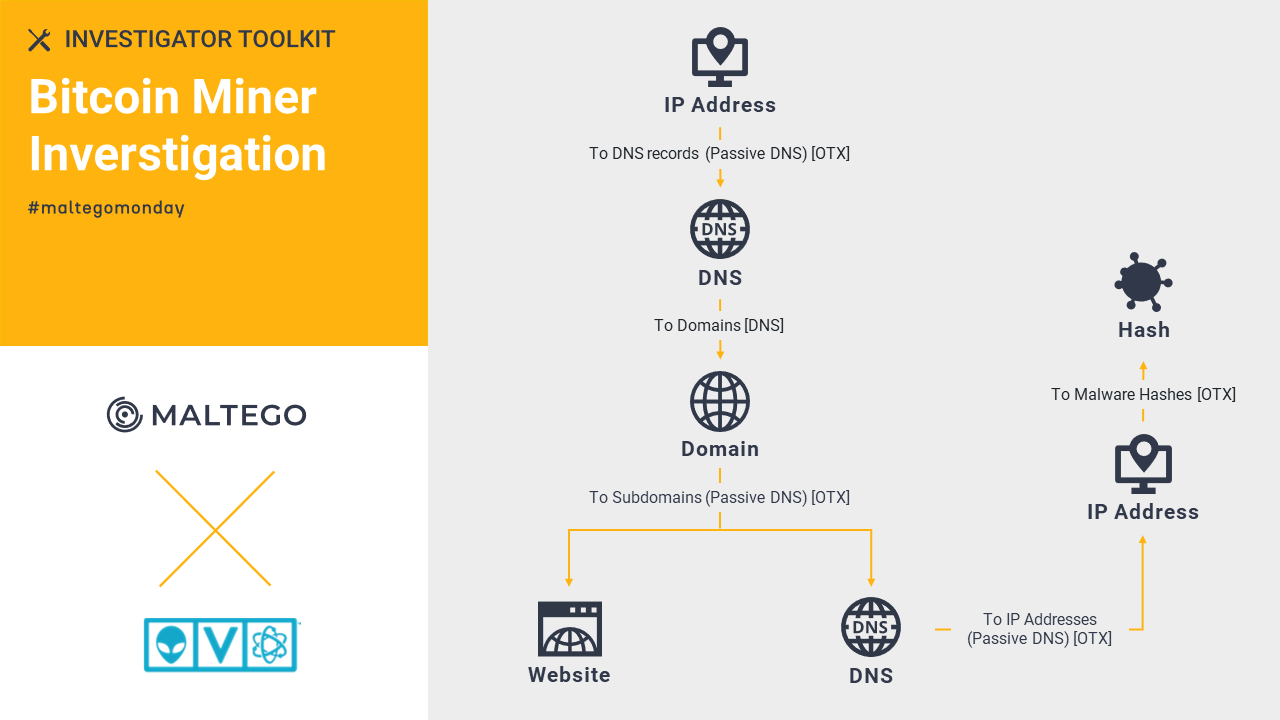
AlienVault OTX: Bitcoin Miner Investigation 🔗︎
With the community-powered threat data from AT&T Cybersecurity’s AlienVault OTX, you can pivot from an IP address or a domain to query information such as hash, CVE, hostname, etc. Read about how we examine the C2 Bitcoin miner with relevant pulses provided by AlienVault OTX in Maltego.
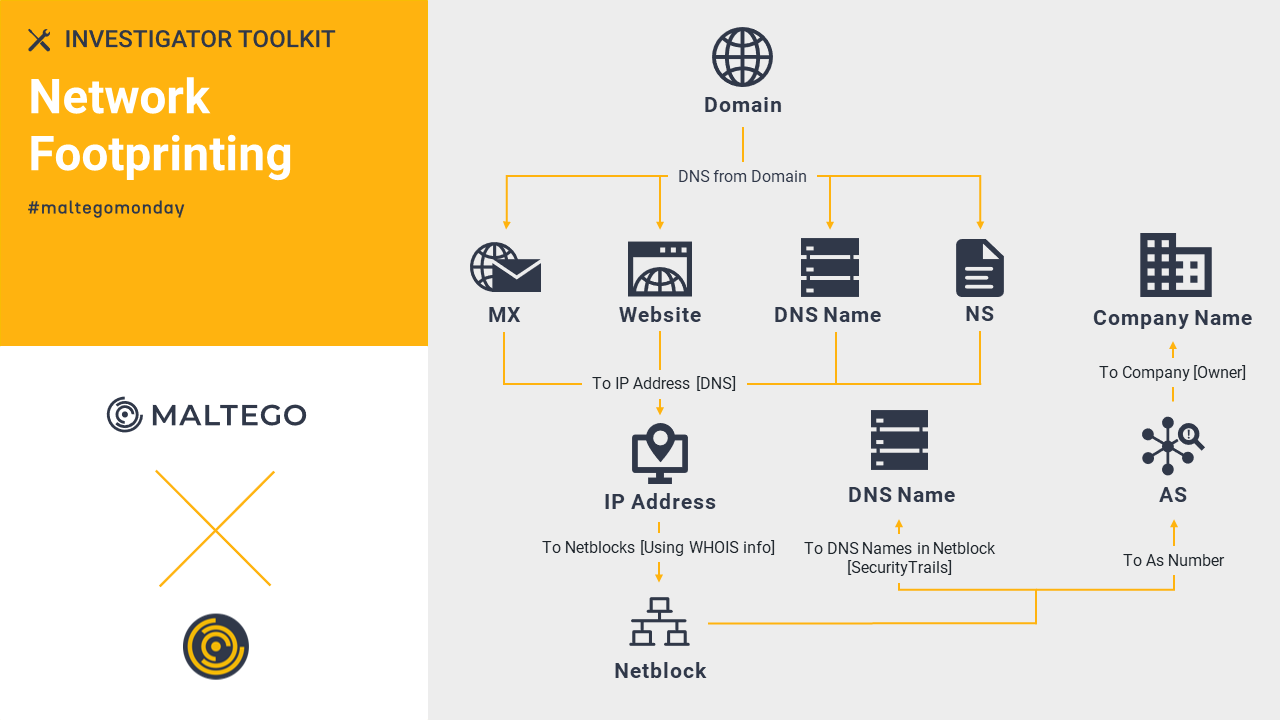
Maltego Standard Transforms: Network Footprinting 🔗︎
The Maltego Standard Transforms are out-of-the-box OSINT Transforms. One of its features allows investigators to obtain an overview of the target’s network infrastructure with a domain Entity. Learn how we outline the relationships between each of the data points and visualize the infrastructure in a graph using the Maltego Standard Transforms.
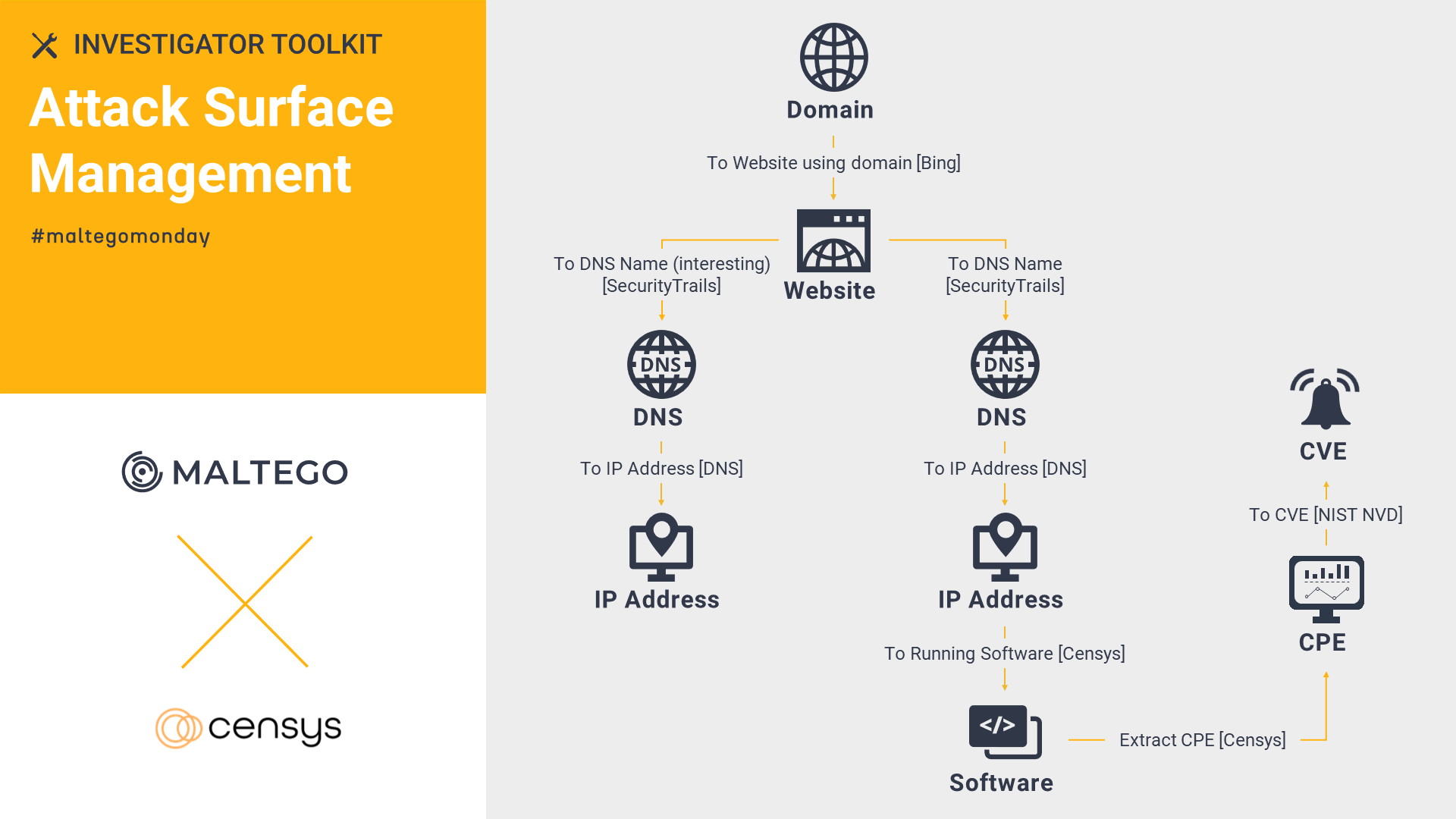
Censys: Attack Surface Management 🔗︎
With Censys, you can quickly conduct an attack surface assessment to evaluate what parts of your infrastructure are vulnerable. Give it a shot and catch potential vulnerabilities now!
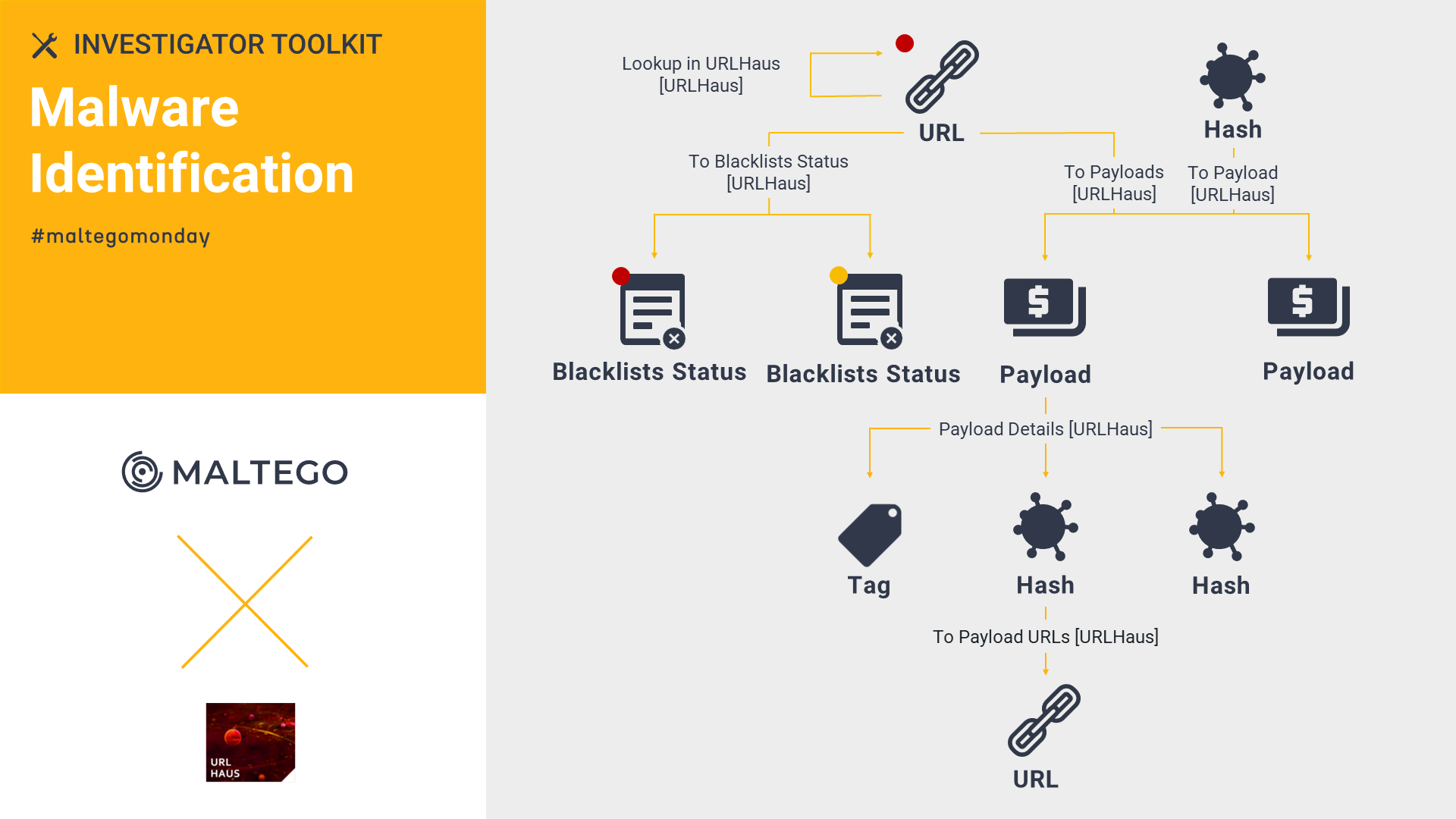
Abuse.ch URLhaus: Malware Identification 🔗︎
Operated by Abuse.ch, URLhaus collects, tracks, and shares malware URLs, allowing analysts to quickly pin down the malicious URLs and their payloads.
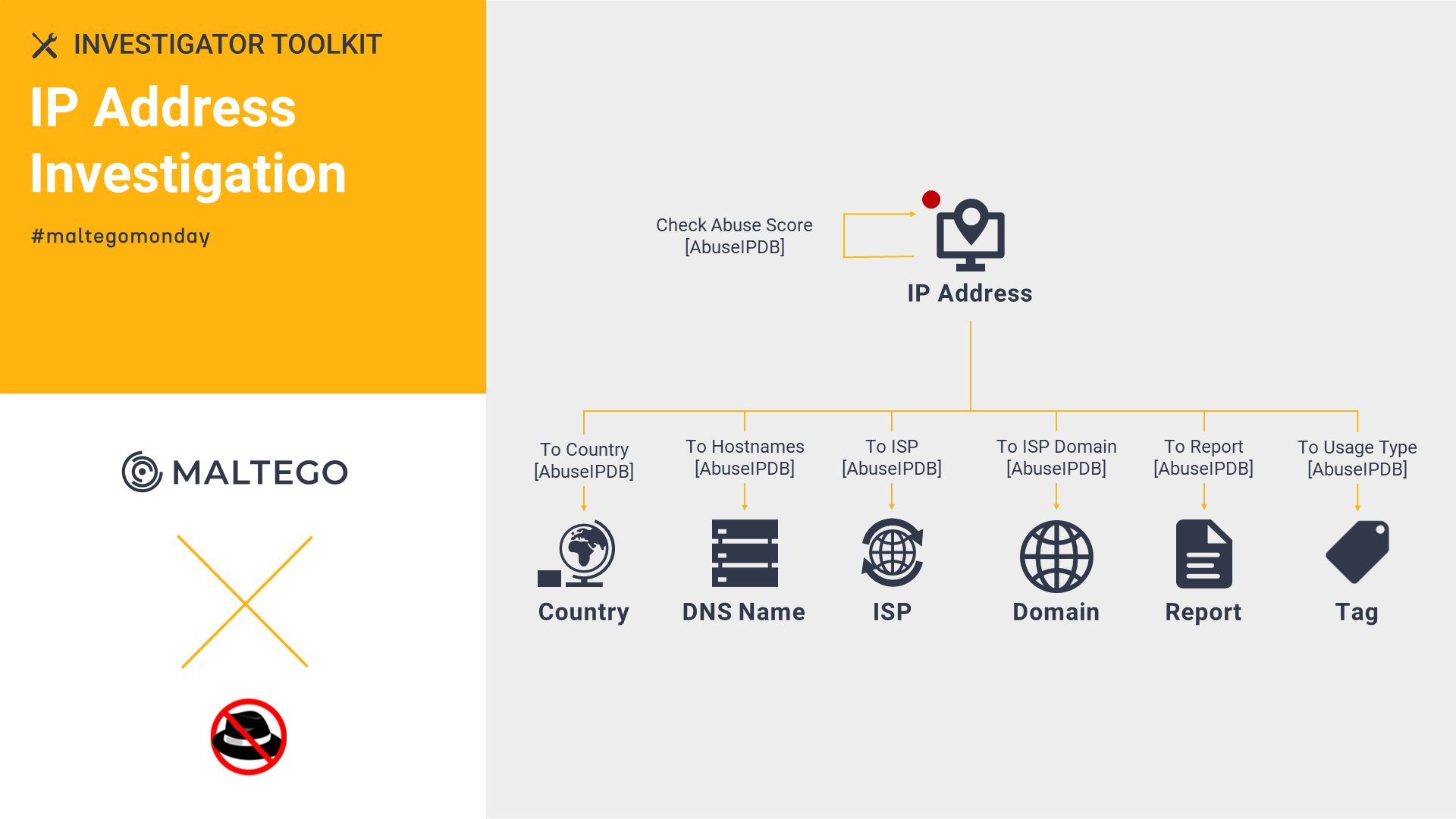
AbuseIPDB: IP Address Investigation 🔗︎
The AbuseIPDB Transforms in Maltego help speed up IP address investigations by extracting details like abuse score, ISP, hostname, etc. You can also report a malicious IP address.
Check out the Investigator Toolkit series now! 🔗︎
In the following months, we will continue digging into different Hub items available in Maltego and providing best practice tips for investigators.
Follow us on Twitter and LinkedIn now to make sure you don’t miss any updates!
Happy Investigating!


 4.5 rating
4.5 rating