Since June 2022, Maltego has launched a new social media campaign that provides Maltego users and investigators with cheat sheets showing how to best use our Hub items for certain workflows. Check out the Investigator Toolkit November roundup in this article!
Investigator Toolkit: Quick Starts to Using Maltego Hub Items in Real-life Investigations 🔗︎
Presented to you by Maltego, the Investigator Toolkit series showcases each Maltego Transform Hub item with a sample workflow applicable to certain types of investigations. This series aims to help you quickly learn how to include a particular Hub item in your existing workflows.
Where to Find the Investigator Toolkit? 🔗︎
You can find the Investigator Toolkit series on our Twitter and LinkedIn channels, with the hashtags #MaltegoMonday and #InvestigatorToolkit. Every Monday, each Investigator Toolkit post comes with a workflow cheat sheet and a blog article or webinar as an additional demonstration.
All Previous Investigator Toolkit Roundups 🔗︎
- Investigator Toolkit July 2022
- Investigator Toolkit August 2022
- Investigator Toolkit September 2022
- Investigator Toolkit October 2022
Investigator Toolkit October Roundup 🔗︎
In November, we featured the following four Hub items and their use cases in the Investigator Toolkit series:
Let’s dive straight into how to use these Hub items for threat intelligence investigation, threat actor group investigation, malware investigation, and threat hunting investigation!
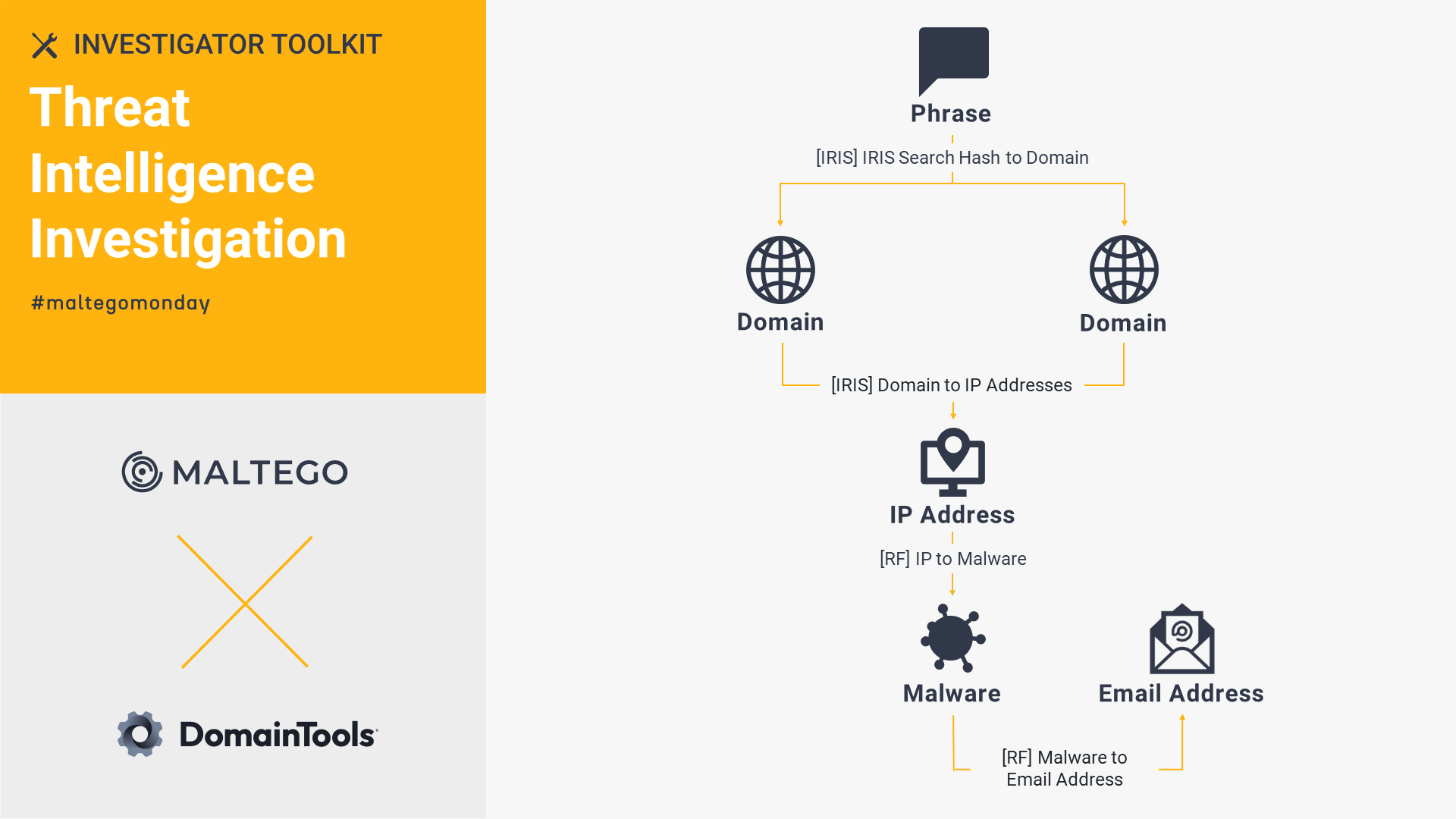
DomainTools Iris: Threat Intelligence Investigation 🔗︎
Export your DomainTools Iris search query as a Phrase Entity in Maltego and run the Transforms to seamlessly collect relevant data about the threat actors and highlight any risky domains. See how we leverage DomainTools Iris and Recorded Future to outline the hosting infrastructure and assess risk scores of known phishing domains run by TA413 threat actor group.
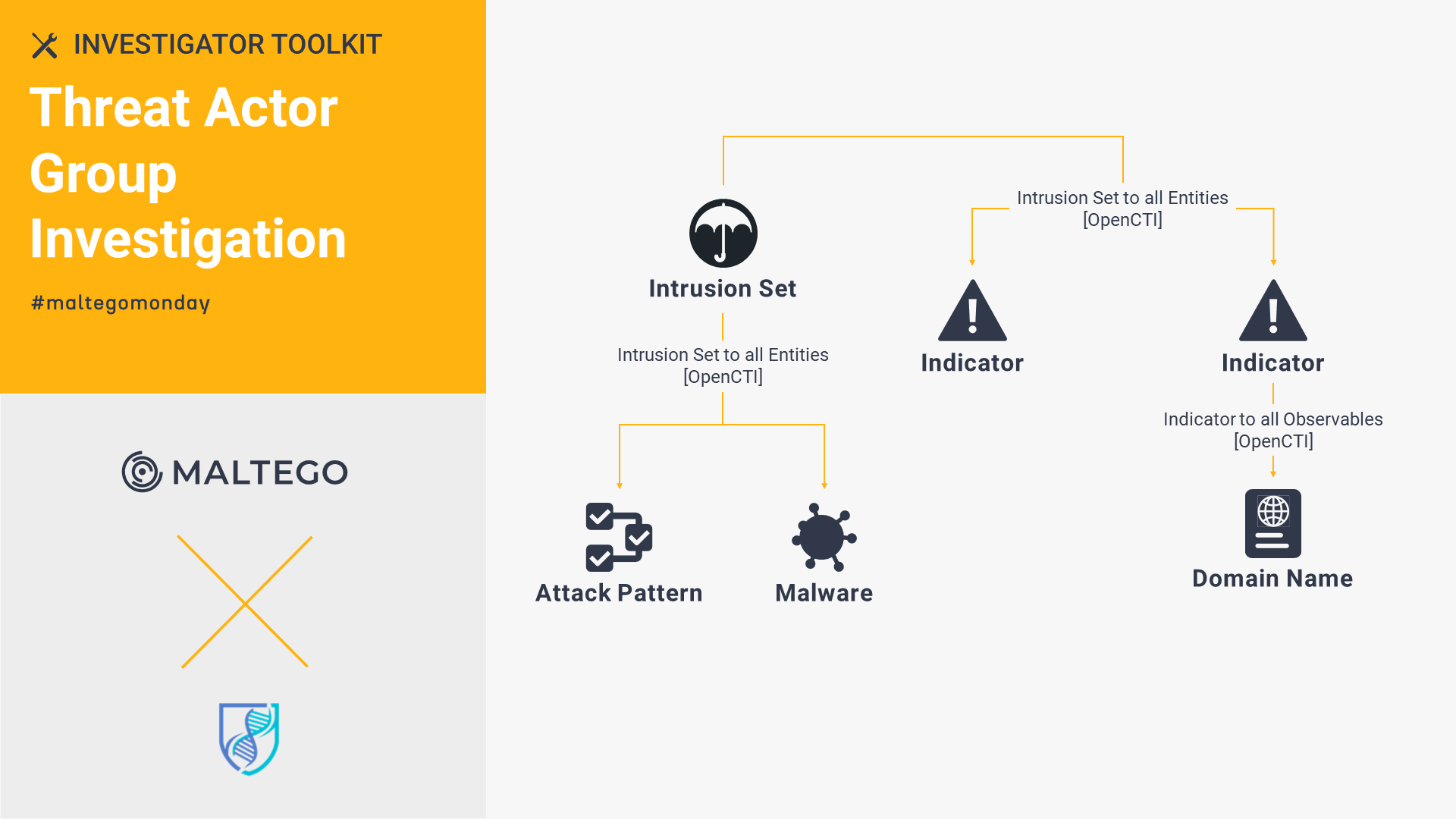
OpenCTI: Threat Actor Group Investigation 🔗︎
To boost your threat intelligence investigations, drop the STIX Standard ID of your target group into Maltego and run the OpenCTI Transforms to map their infrastructure. See how we leverage OpenCTI, VirusTotal Public API, and PeeringDB to map infrastructure used by TA413 threat actor group for their campaigns, such as domains, IP addresses, file names, and hashes.
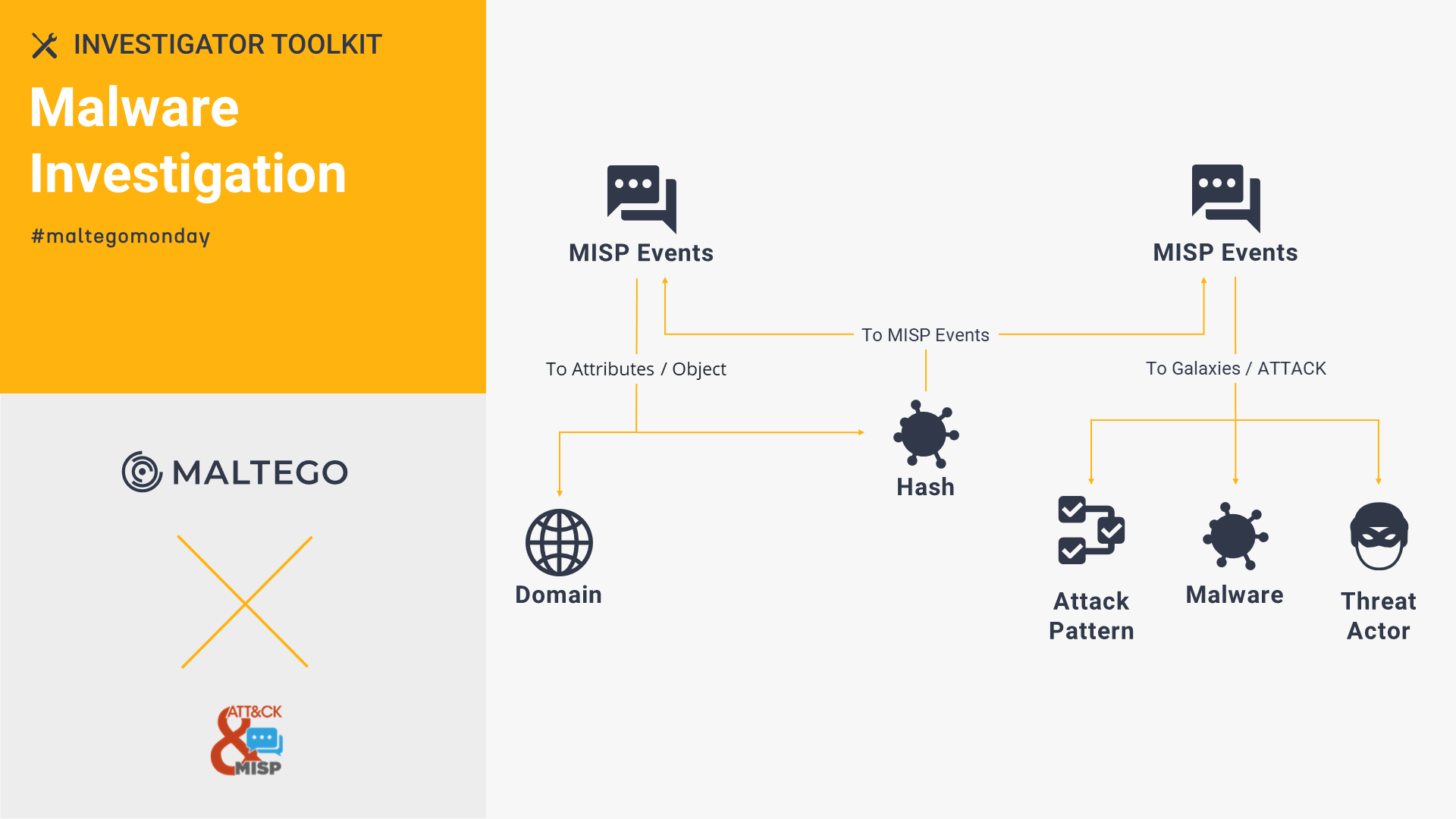
ATT&CK MISP: Malware Investigation 🔗︎
With MITRE ATT&CK’s MISP, you can identify whether a hash is a false alert and query details like threat actors, MISP events, tools, and IP addresses. Check out this walk through to see how we use ATT&CK MISP, VirusTotal Public API, and ZETAlytics Massive Passive to identify C2 malware hashes and examine possible phishing IP addresses.
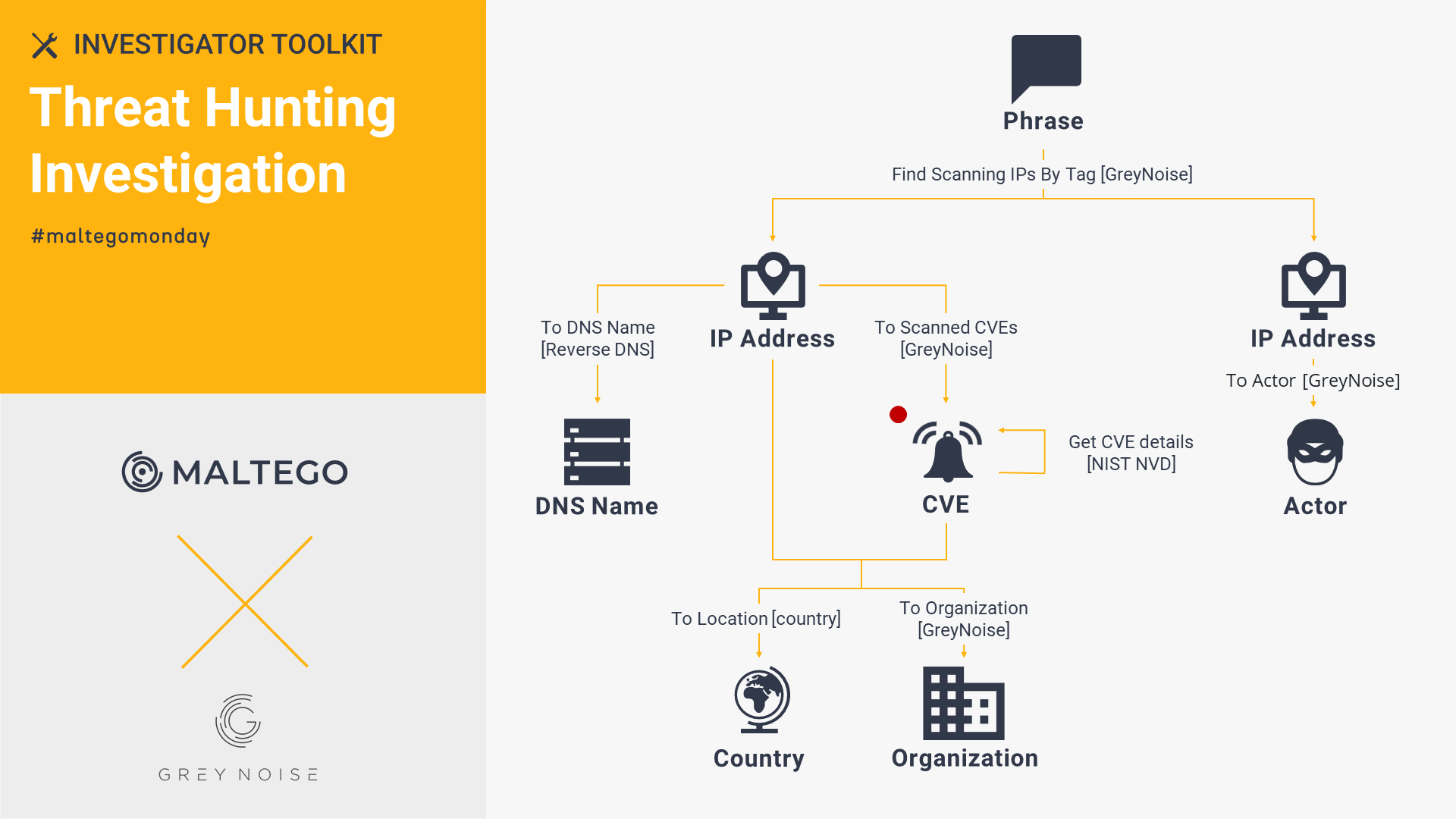
GreyNoise Enterprise: Threat Hunting Investigation 🔗︎
Starting with an IP Address, AS Number, or CVE Entity, investigators can use GreyNoise Enterprise to identify the extent of malicious activities against an organization. With GreyNoise Enterprise, we looked into the ongoing activities of the massive scanners with an extensive picture beginning with a Phrase Entity.
Check out the Investigator Toolkit series now! 🔗︎
In the following months, we will continue digging into different Hub items available in Maltego and providing best practice tips for investigators.
Follow us on Twitter and LinkedIn now to make sure you don’t miss any updates!
Happy Investigating!