Since June 2022, Maltego has launched a new social media campaign that provides Maltego users and investigators with cheat sheets showing how to best use our Hub items for certain workflows. Check out the Investigator Toolkit October roundup in this article!
Investigator Toolkit: Quick Starts to Using Maltego Hub Items in Real-life Investigations 🔗︎
Presented to you by Maltego, the Investigator Toolkit series showcases each Maltego Transform Hub item with a sample workflow applicable to certain types of investigations. This series aims to help you quickly learn how to include a particular Hub item in your existing workflows.
Where to Find the Investigator Toolkit? 🔗︎
You can find the Investigator Toolkit series on our Twitter, LinkedIn, and Mastodon channels, with the hashtags #MaltegoMonday and #InvestigatorToolkit. Every Monday, each Investigator Toolkit post comes with a workflow cheat sheet and a blog article or webinar as an additional demonstration.
Investigator Toolkit October Roundup 🔗︎
In October, we featured the following four Hub items and their use cases in the Investigator Toolkit series:
Let’s dive straight into how to use these Hub items for supplier network investigations, malicious domain investigations, breached data investigations, and social media online footprint examination!
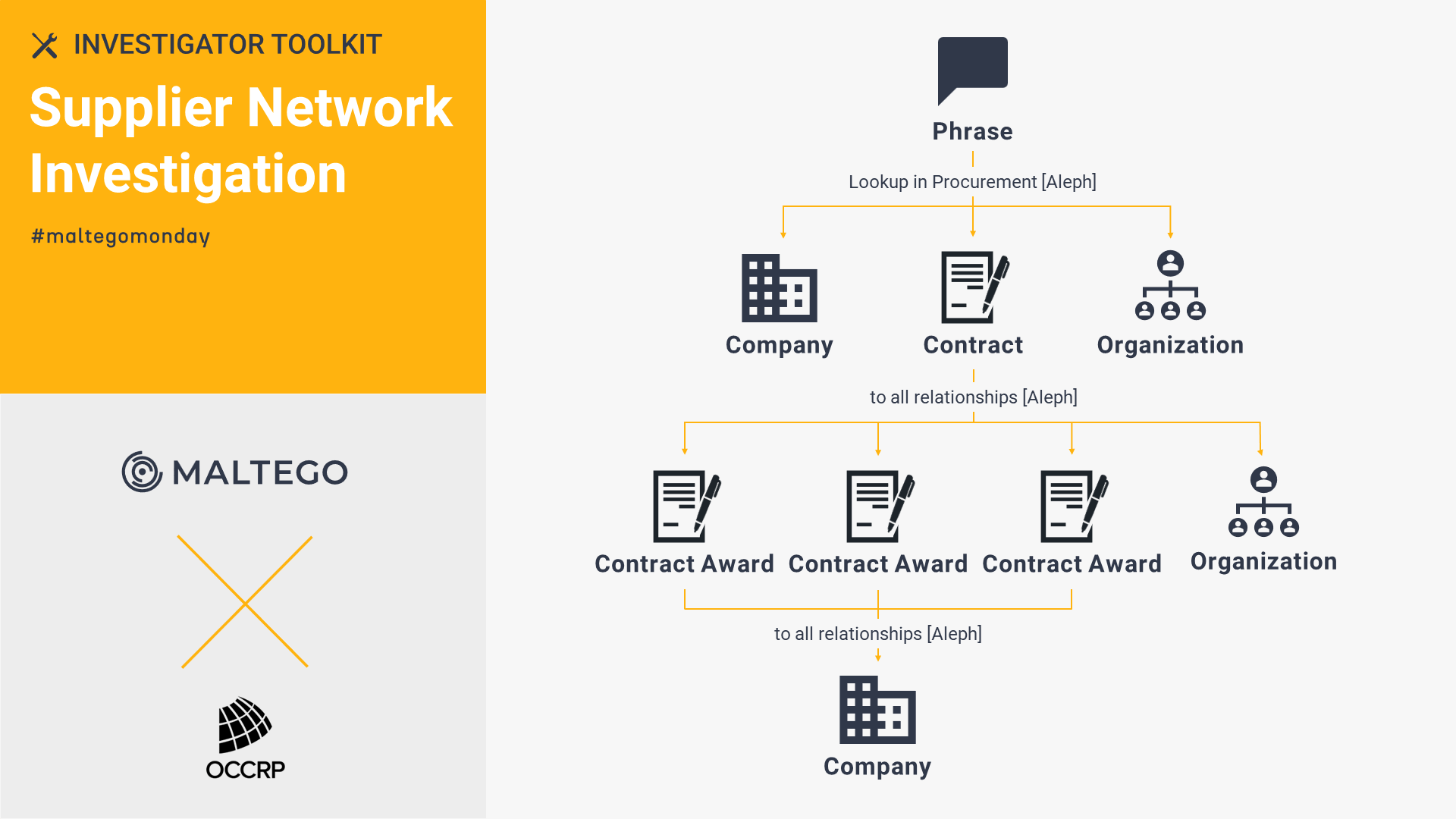
OCCRP Aleph: Supplier Network Investigation 🔗︎
With the OCCRP Aleph Transforms in Maltego, investigators can securely access large amounts of data, querying companies’ registries, contracts, procurement databases, and many more in a single interface.
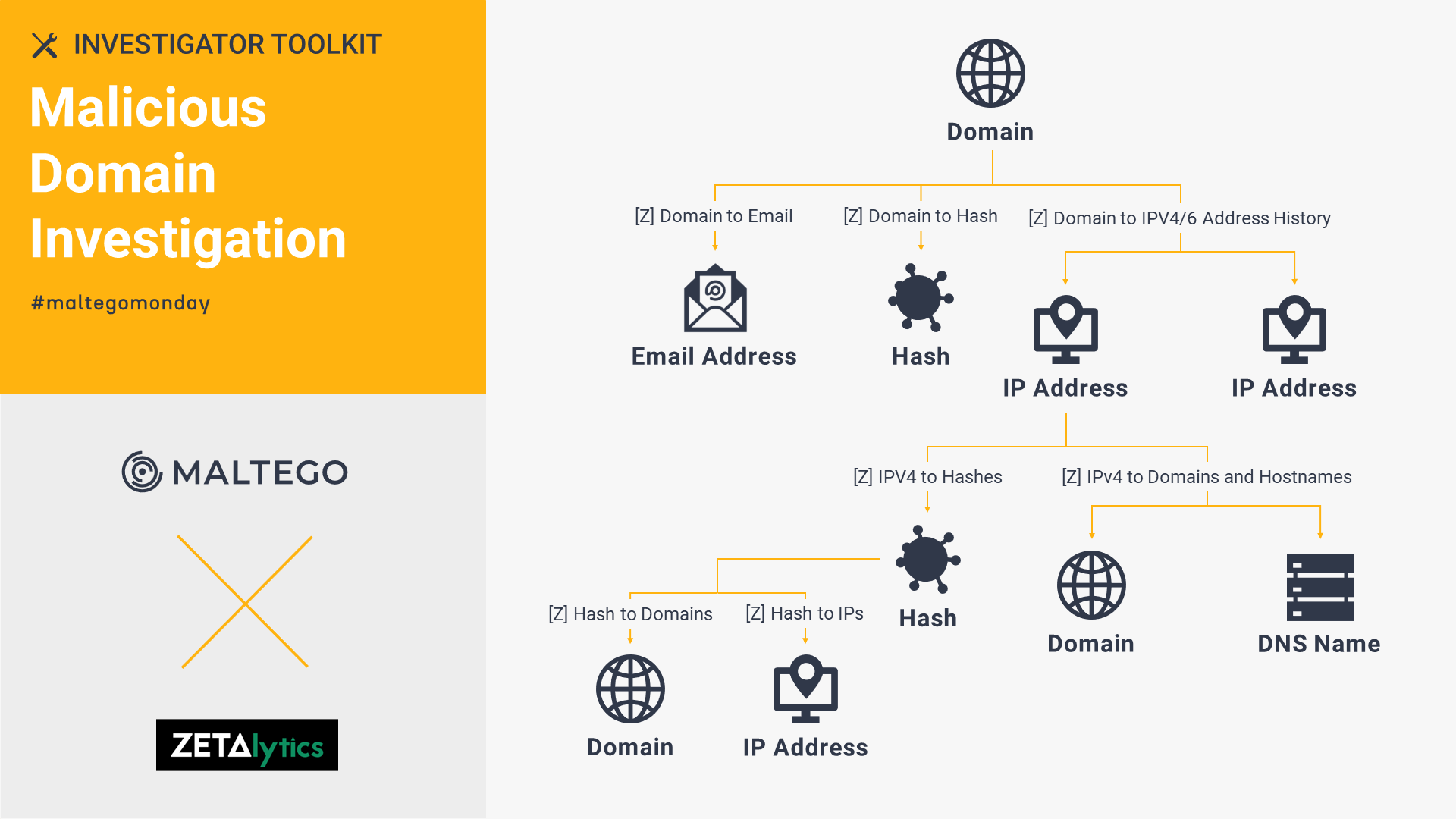
ZETAlytics Massive Passive: Malicious Domain Investigation 🔗︎
By leveraging the ZETAlytics Massive Passive Transforms in Maltego, investigators can query historical domains, email addresses, and name servers, spotting relationships between different threat actors and known associates.
Check out how we investigate suspicious IP addresses and trace back to the source of malware entry starting from a Domain Entity, exploring one network infrastructure point to another with ZETAlytics Massive Passive’s comprehensive database.
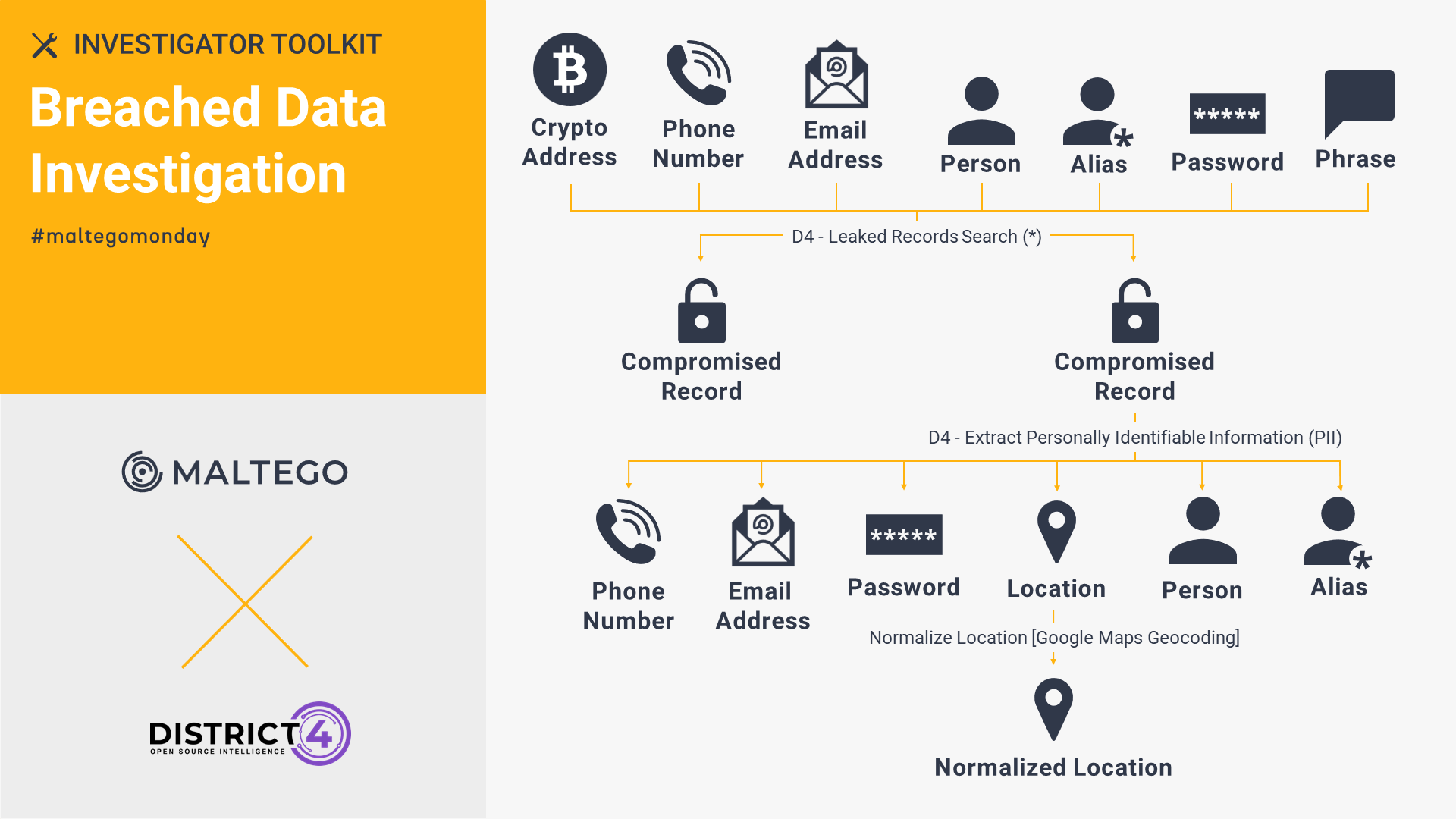
Darkside: Breached Data Investigation 🔗︎
To unravel a subject’s online presence, investigators can utilize the Darkside breach database built by District 4 Labs, gathering personally identifiable information.
In our latest joint webinar, Maltego SME, Mathieu Gaucheler, and our partner, District 4 Labs, showed how investigators can use breached data to spot hidden patterns in large volumes of data within Maltego, conducting a live demo with leaked FSB agent phone numbers.
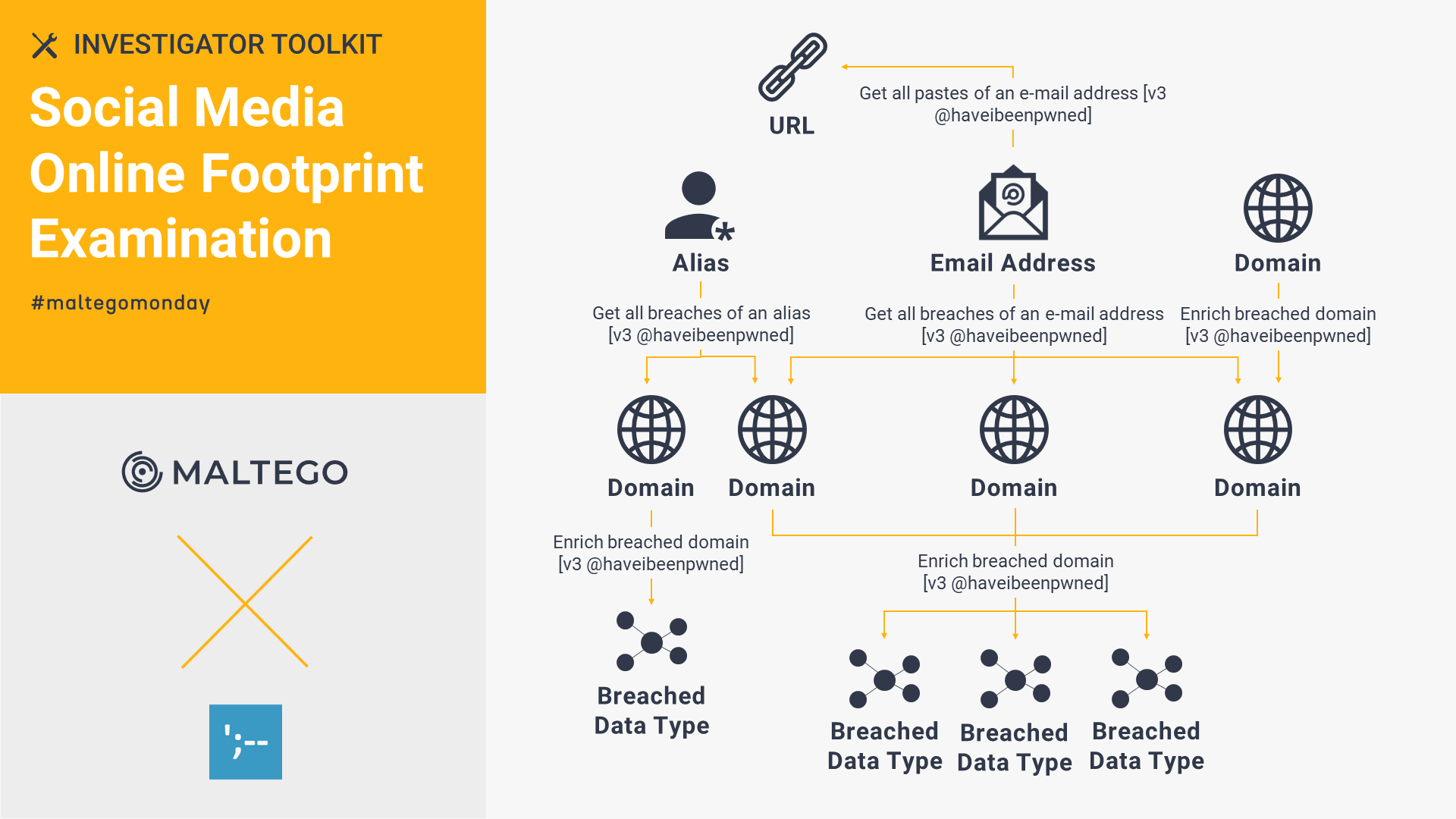
Have I Been Pwned: Social Media Online Footprint Examination 🔗︎
Using the Have I Been Pwned Transforms in Maltego, investigators can easily check if their online account has been compromised in a data breach and whether they are at risk of potential cyber threats.
And that’s a wrap for the Investigator Toolkit series! 🔗︎
To better assist and provide our community with up-to-date information about Maltego Hub items, we are bringing an end to the Investigator Toolkit series to launch a new and exciting campaign. Thank you all for showing your support toward this initiative!
While we are working on the re-upcoming campaign, don’t forget to follow us on Twitter, LinkedIn, and Mastodon so that you don’t miss any updates!
Happy Investigating!