Malware and phishing attacks are among the most common cybersecurity threats that organizations and corporations constantly deal with. Attackers typically attempt to compromise a computer or network systems by planting malware on the target’s machine via a phishing domain or an email attachment. The goal of the compromise can range from paralyzing internal systems to stealing user credentials and confidential business intel.
Command-and-control malwares (aka C2 malwares) are often used for such attacks. Once the target opens the phishing link or attachment, the C2 malware payload is automatically and quietly downloaded and planted in the target’s computer. After the C2 malware successfully compromises the target network, it waits for further commands from the attacker until it strikes—taking control of the machine or infiltrating valuable data.
Using Maltego to Identify and Investigate on C2 Malware in Your Network 🔗︎
Maltego has a number of data integrations especially helpful for cybersecurity professionals and threat hunters seeking to identify hidden threats in the organization’s network and trace the origin of said threats. In this tutorial, we will demonstrate how you can use Transforms from ATT&CK - MISP, VirusTotal Public API, and ZETAlytics Massive Passive to acquire threat intel, find hashes related to certain domains and IPs, and uncover threat actor network.
Note: You will need to install all three Hub items in the Maltego Desktop Client before you proceed with this tutorial.
MISP Transforms in Maltego 🔗︎
MISP is an open-source threat intelligence platform for sharing, storing, and correlating indicators of compromise (IOC) of targeted attacks, threat intelligence, and information on financial fraud, vulnerabilities, or even counterterrorism. Using the MISP Transforms, investigators may query data from a MISP threat sharing instance, and browse through other MISP events, attributes, objects, tags, and galaxies.
While the ATT&CK Transforms are available for all Maltego users, MISP Transforms require a link and an API key for users to gain access to. You can start by visiting the MISP community page to find the most relevant data for your investigations. In this use case, we will be using the MISP data from a COVID-19 related MISP community.
VirusTotal Public API Transforms 🔗︎
VirusTotal is a service that analyzes files and URLs for viruses, worms, trojans and other kinds of malicious content. By querying the VirusTotal Public API data with Maltego Transforms, investigators can return information about associating IP addresses, hashes, domains, and URLs.
To access the VirusTotal Public API Transforms, please register for the free API key here.
ZETAlytics Massive Passive Transforms 🔗︎
ZETAlytics Massive Passive provides investigators with pivots and data including billions of records for historical domains, email addresses, IPs, and name servers. Using the ZETAlytics Transforms, threat hunters can identify the relationships between historical IPs and hostnames, connections of malware hashes to domains, links between name servers and domains, and so on.
ZETAlytics provides Maltego users free-trial API keys with query limitations. To access the ZETAlytics Transforms, please sign up for the free trial here.
Use Case: Hunt Down C2 Malware Threats Found in Company Network 🔗︎
Imagine, for this scenario, that we are a threat hunter whose job is ensuring the security of a company’s network. One day, during a regular network analysis, we discover a few hashes in the infrastructure. We quickly trace the location of the hashes to a few colleagues’ workstations and pull out their traffic logs to see a list of domains they visited recently.
Now, we need to identify whether these are false alerts and if not, what the hashes are and where they came from.
Step 1: Identify Whether Hashes are False Alerts 🔗︎
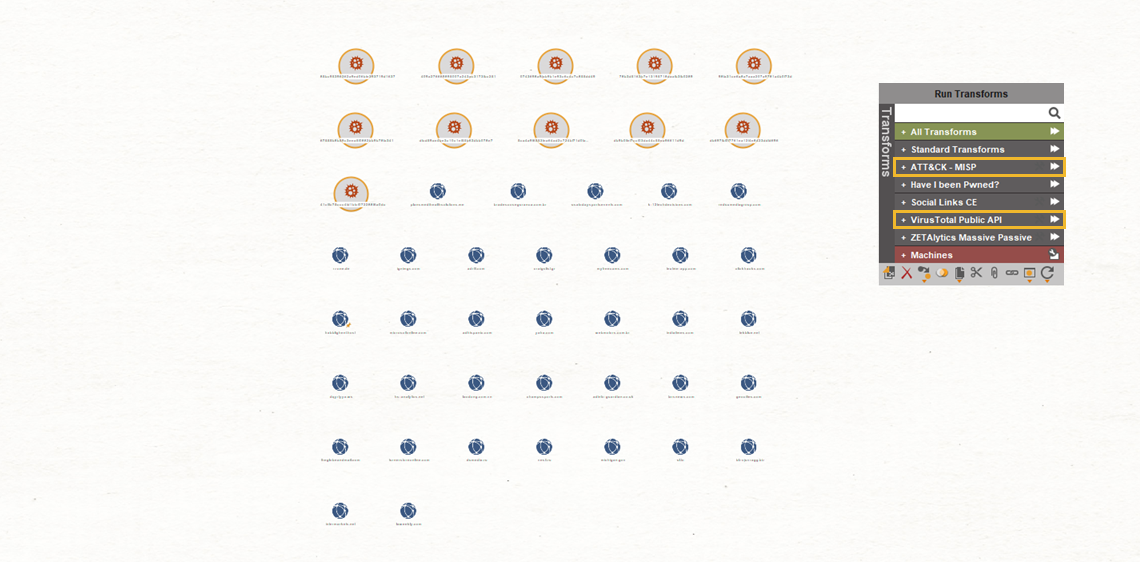
To do so, we import the hashes and domains by copy-and-pasting them into Maltego and run all the VirusTotal Public API Transforms as well as ATT&CK – MISP Transforms on the hashes. This way, we can quickly find out if any of these hashes are existing, reported threats.
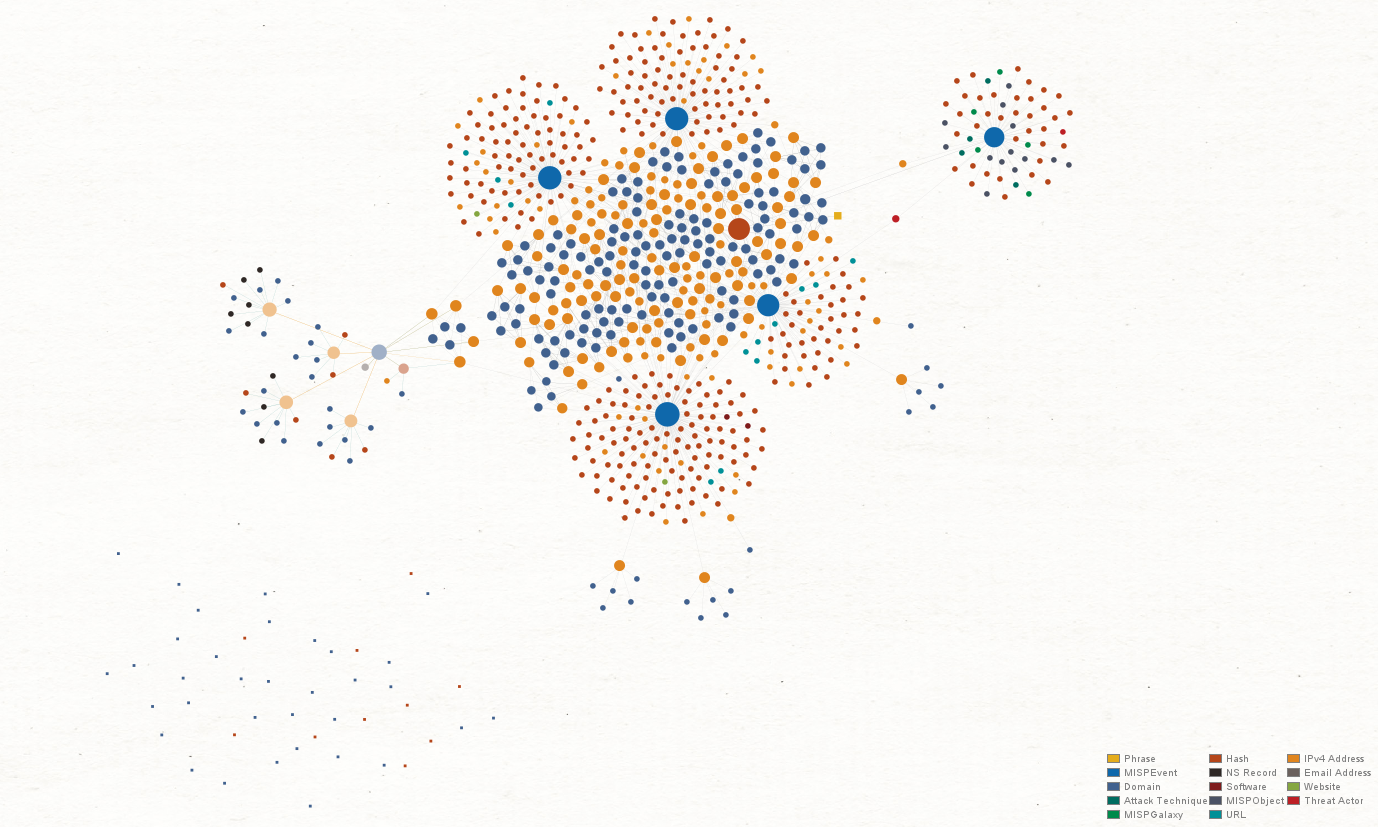
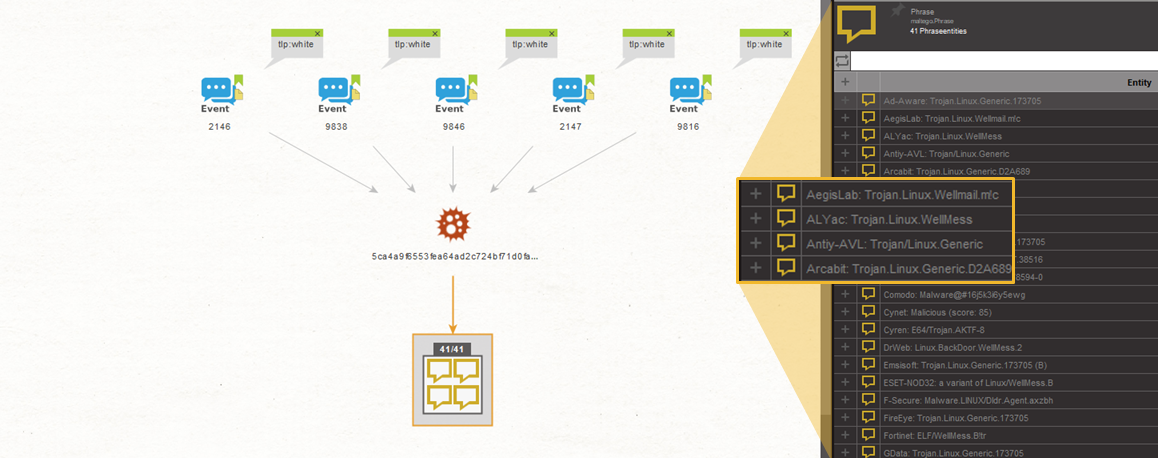
Out of the 11 Hash Entitles, only one of them returns MISP Events and VirtusTotal results.
Taking a look at the VirusTotal results in the Detail View located at the right sidebar, we see that a large number of reports and mentions on this hash is related to a Trojan malware called “WellMess.”
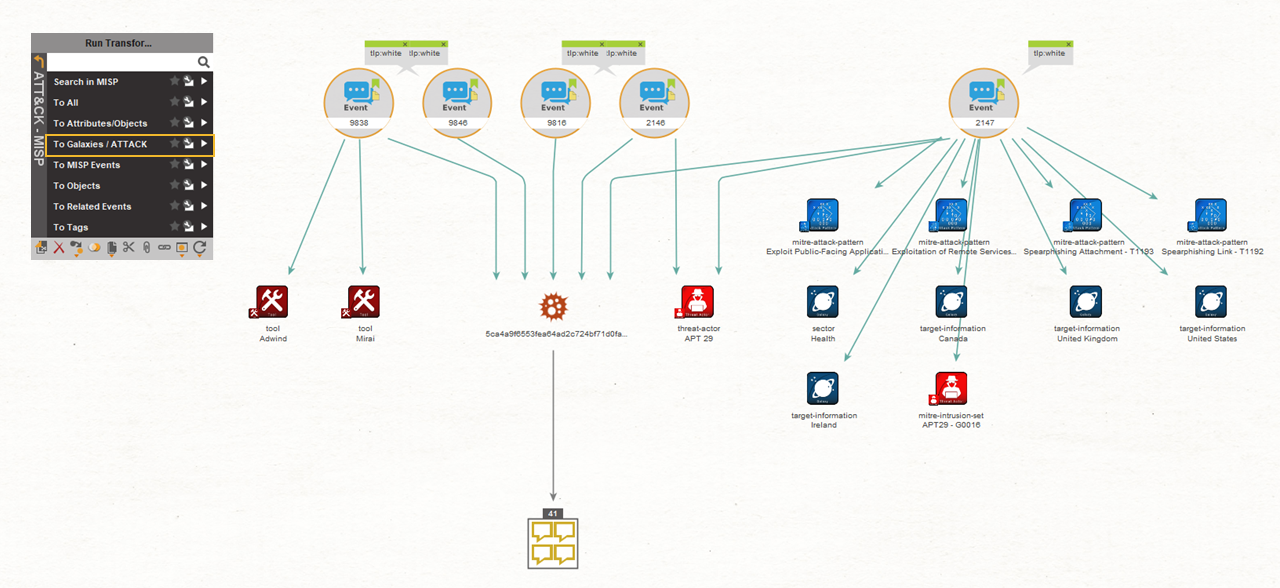
A quick Google search reveals that “WellMess” is actually a malware targeting companies developing COVID-19 vaccines. We also find that the threat actor behind this malware goes by the Alias, “Blue Kitsune” (aka. APT29, Cozy Bear, and the Dukes), which we confirmed by running the To Galaxies / ATTACK Transform on the MISP Event Entities.
Now we can be sure that our organization is under some sort of malware threat and we want to know how this hash made its way into our network.
Step 2: Find Out Relevant IP Addresses using MISP Transforms 🔗︎
Next, we want to find out which IP addresses are associated with the MISP Events. Before doing so, we will mark all the Hash and Domain Entities currently on the graph with a blue bookmark. This way, we can still quickly distinguish between new Entities from the hashes and domains found in our system.
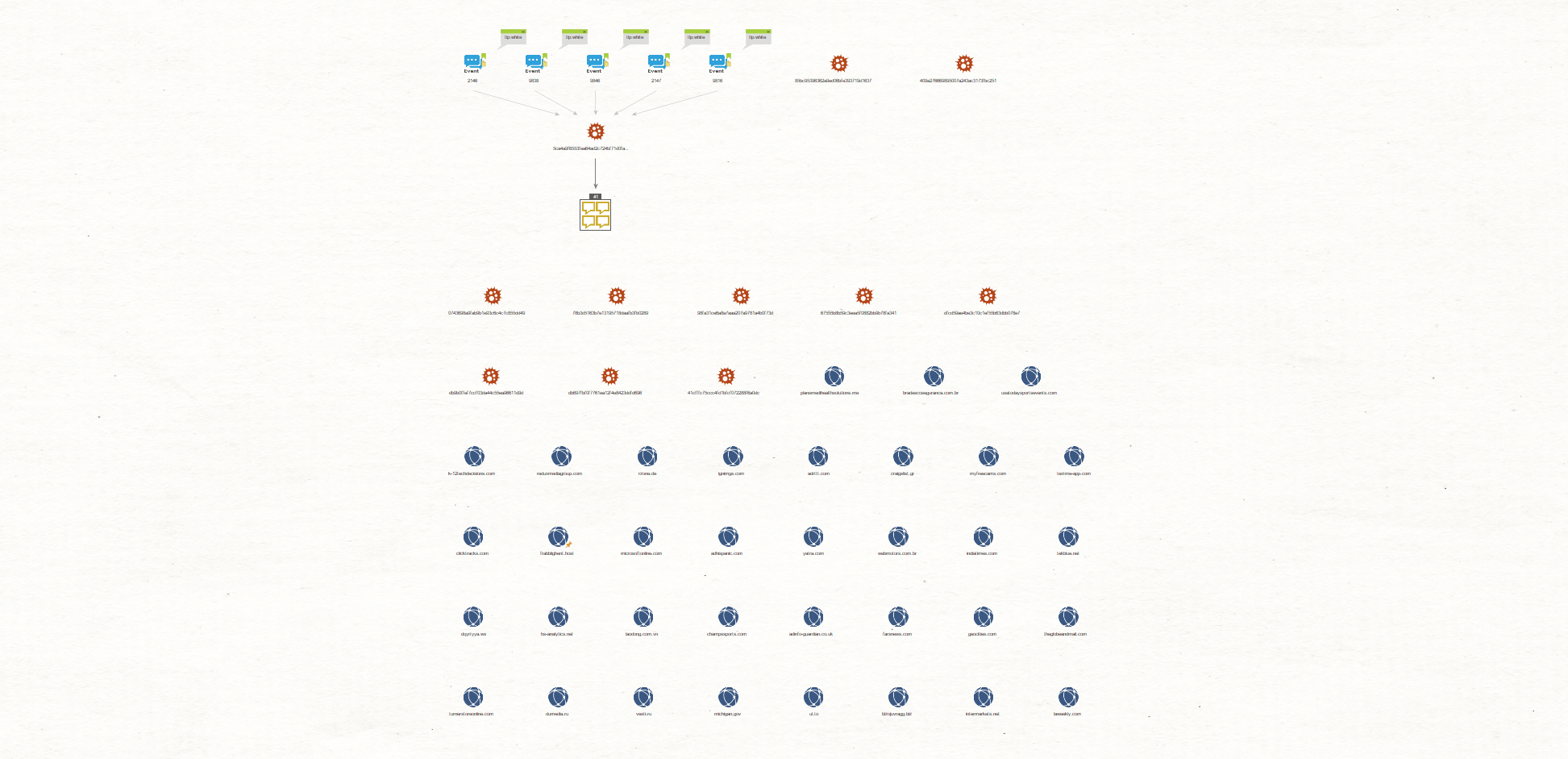
Now that we bookmarked our Entities, we will select the MISP Events again and run the To Attribute/Objects Transform.
Shown in the resulting graph above, the Transform returned several new Hash and IP Address Entities related to these MISP Events associated with the Hash originally found in our network system.
Step 3: Investigate on Suspicious IP Addresses using ZETAlytics Transforms 🔗︎
As mentioned before, ZETAlytics Passive Massive is a comprehensive database of historical domains, name servers, IP addresses, and email addresses, making it a useful Hub item to pivot from one network infrastructure point to another.
Now that we have discovered the IP addresses associated with this malware attack, we want to find out which of the domains our employees visited which were the source of this malware.
We select all the IP Address Entities on the graph and run the [Z] IPv4 to Domains and Hostnames Transform.
Note: If you are using ZETAlytics free trial API key, the Transform will only return limited results.
While Transforms return and add new Entities to a Maltego graph, if an Entity matching the result is already on the graph, Maltego will also automatically link to this Entity. Therefore, as the ZETAlytics Transform returns the domains related to these suspicious IP addresses, we can also check whether the original domains marked in blue are connected to them.
Step 4: Identify How the Malware Entered the Company Network 🔗︎
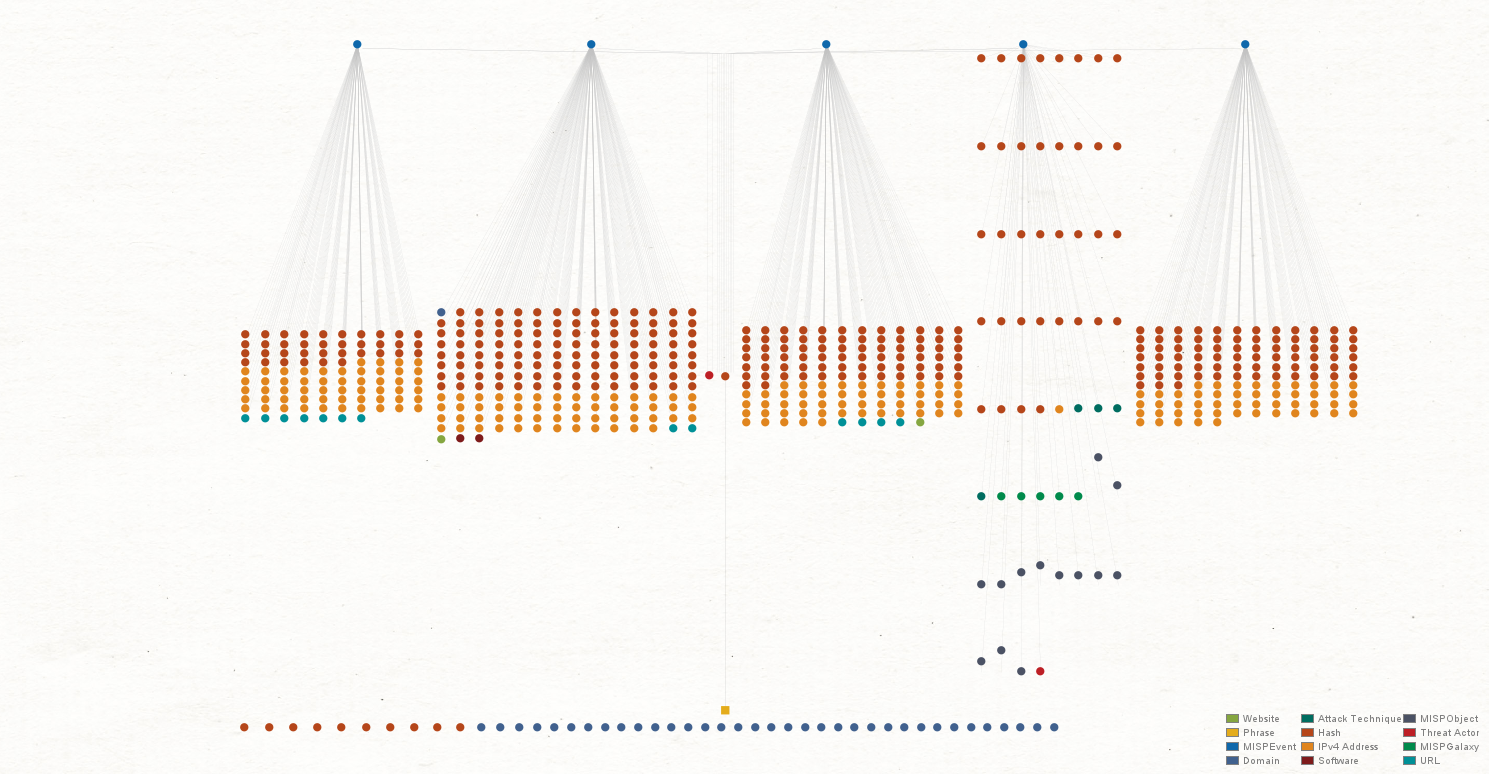
Selecting all Domain Entities and checking each Domain Entity marked blue, we quickly find that one domain out of all of those visited by our colleagues is connected to the IP addresses associated with the WellMess hashes and threat events.
We can now assume that this domain “frabblighent[.]host” is likely a phishing domain used to spread the malware. Our colleagues’ computers are also likely to be compromised based on visiting this domain.
Step 5: Deep-Dive into Malicious Domains to Find the Source of Malware Entry 🔗︎
To confirm our assumption, we will take a closer look at this suspicious domain.
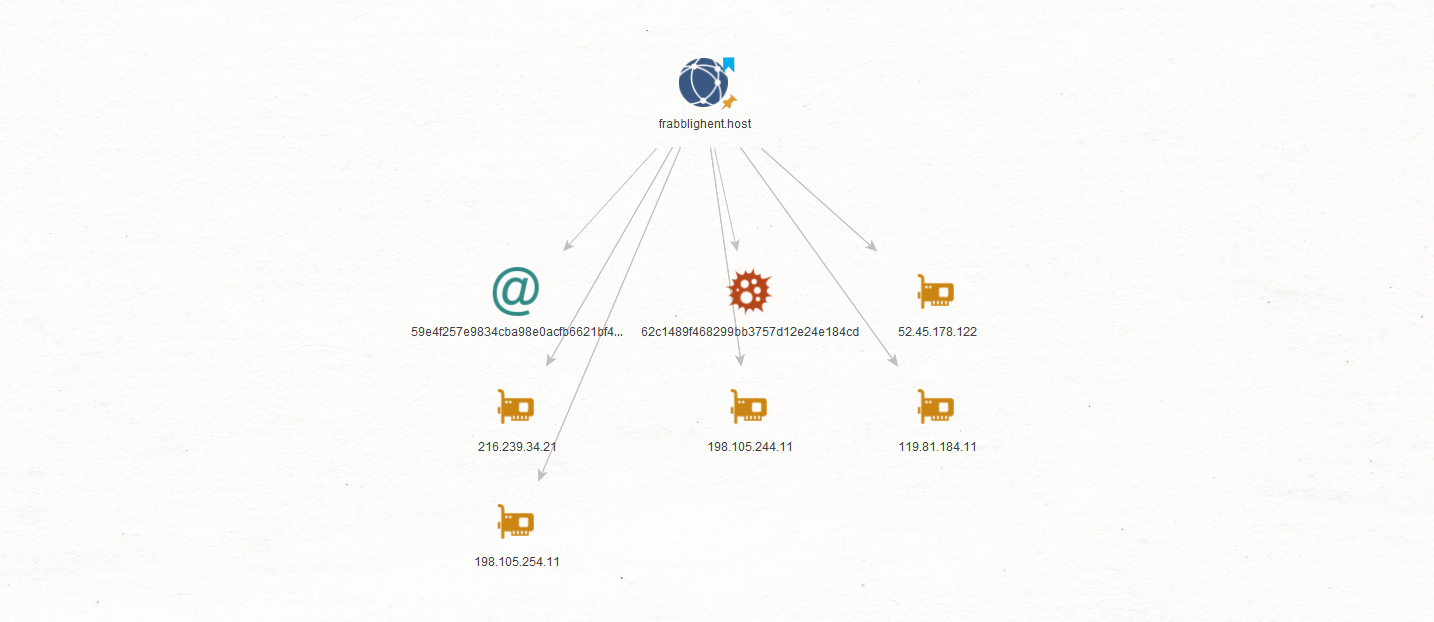
Pasting the Domain Entity to a new graph, we ran all the ZETAlytics Transforms again.
The Transforms quickly return a Hash Entity, which further reinforces our assumption that this domain is malicious and is being used for phishing purposes.
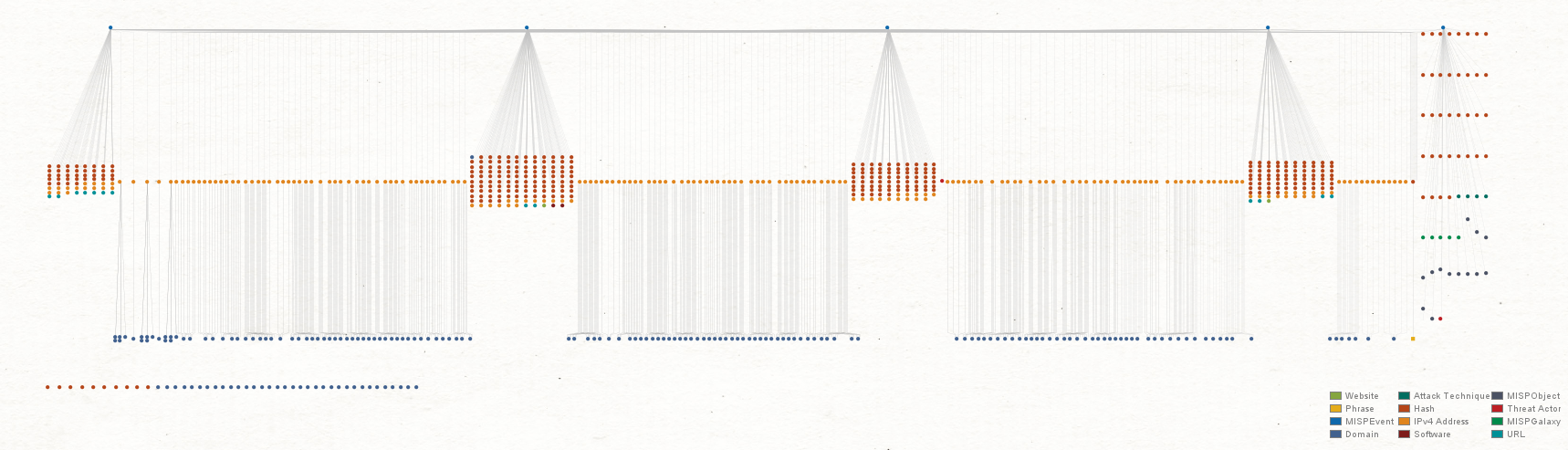
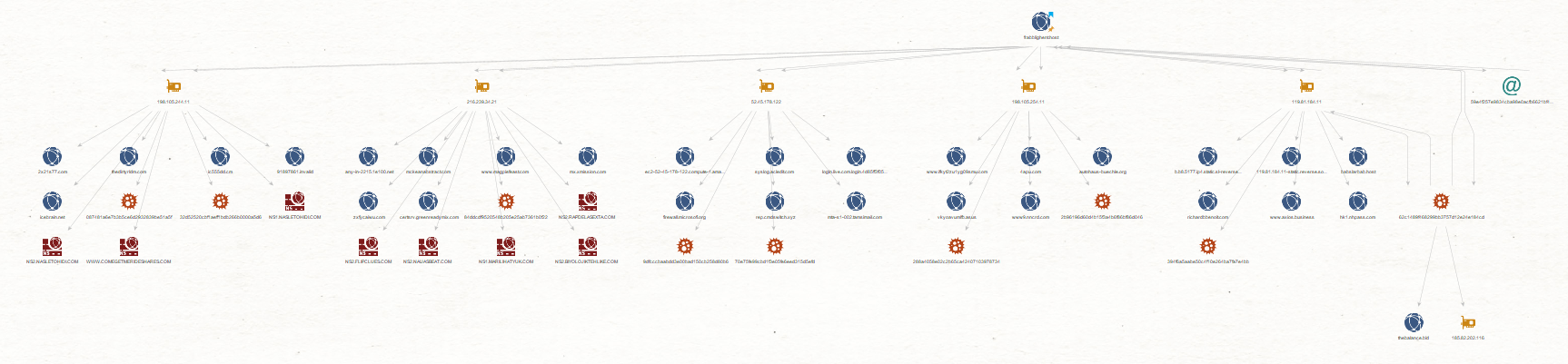
We then select all the resulting Entities and run the ZETAlytics Transforms again to find out whether there other relevant evidence of threats exists:
The result shows that multiple domains and hashes related to the IP addresses are associated with the “frabblighent[.]host” domain. We can now confirm that this is a phishing domain and is the cause of our network compromise.
Investigate Further on Phishing Baits and Hashes 🔗︎
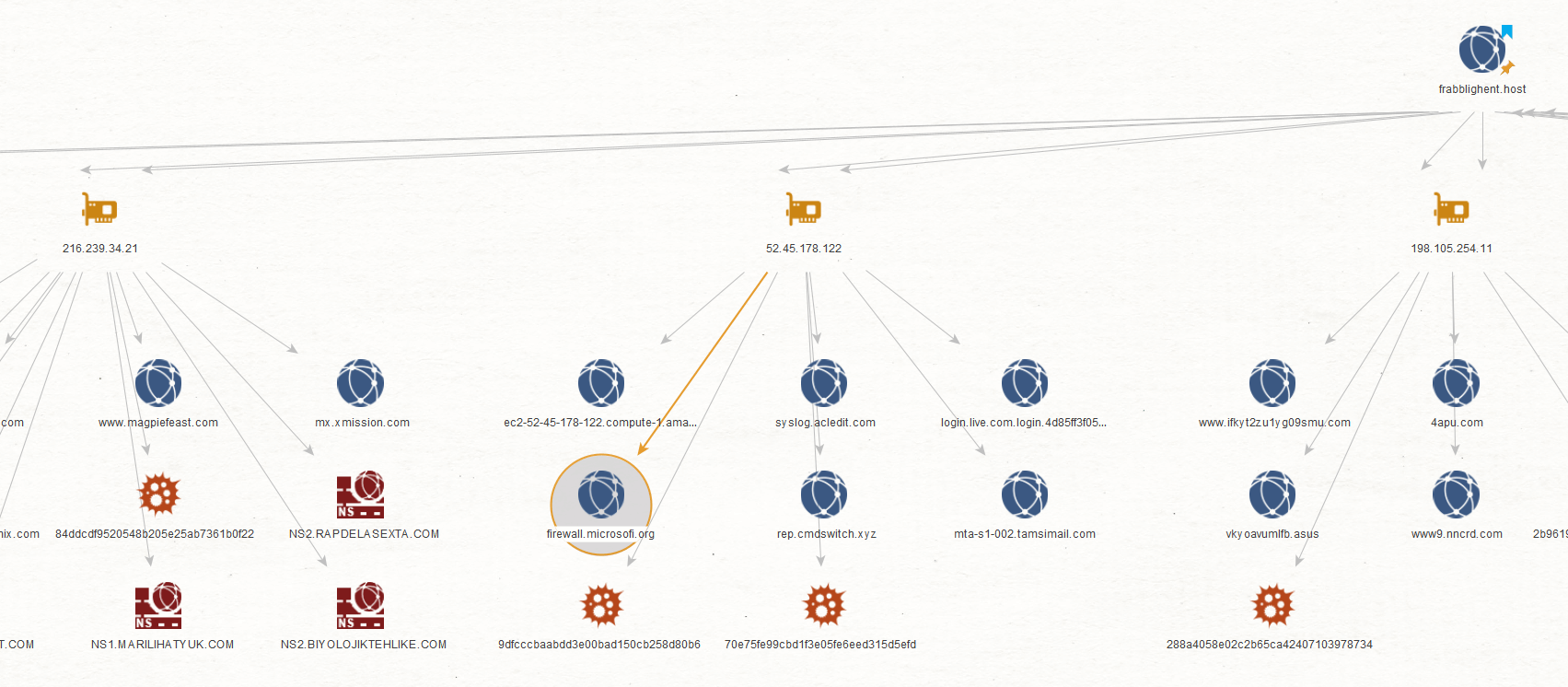
If you are a threat hunter or a phishing analyst, you can inspect the IP addresses and domains resulted from Step 5 even further. For example, some of the IP Address Entities are linked to domains that are most likely used for phishing, such as “firewall[.]microsofi[.]org”.
You can run the ZETAlytics Passive Massive Transforms, VirusTotal Public API Transforms, and/or the MISP Transforms recurrently to further investigate these domains, IP addresses, hashes, and the threat details and networks.
You can also use the Maltego Standard Transforms to expand the investigations, footprinting the phishing network or pivoting into other website-based queries.
We hope that this tutorial has been useful to you. Follow us on Twitter and LinkedIn or subscribe to our Email newsletter to stay updated with the latest use cases and tutorials!
Happy investigating!