In the era where the internet is the go-to place to search for information, having an online presence is essential for anyone wanting to reach out and communicate with the crowds. According to Internet Live Stats, as of end of 2020, Google processes an average of over 40,000 search queries per second, which means millions of webpages are looked up and displayed to searchers every second.
Websites as the Means to Compromise Internet Security with the Spread of Fraudulent Information 🔗︎
Websites are used to publish, distribute, spread, and communicate information. While businesses may create websites as part of their digitalization efforts i.e., for brand promotion and commercial growth, enthusiasts establish them to exchange knowledge and form communities around certain topics.
Websites, however, are also used by threat actors to conduct malicious activities. From phishing attackers attempting to steal critical information and credentials to recruiting victims for indoctrination or radicalization, malicious and fraudulent actors are everywhere, hiding behind seemingly legitimate and appealing messages published on harmless-looking websites. And, to magnify their potential targets while flying under the radar, they may often create multiple websites, each with different content, in order to reach a broader audience.
In the case of a disinformation campaign, the threat actor could spread one piece of fake news on several “news media websites” or “non-profit websites” in an attempt to increase its credibility and harness more exposure.
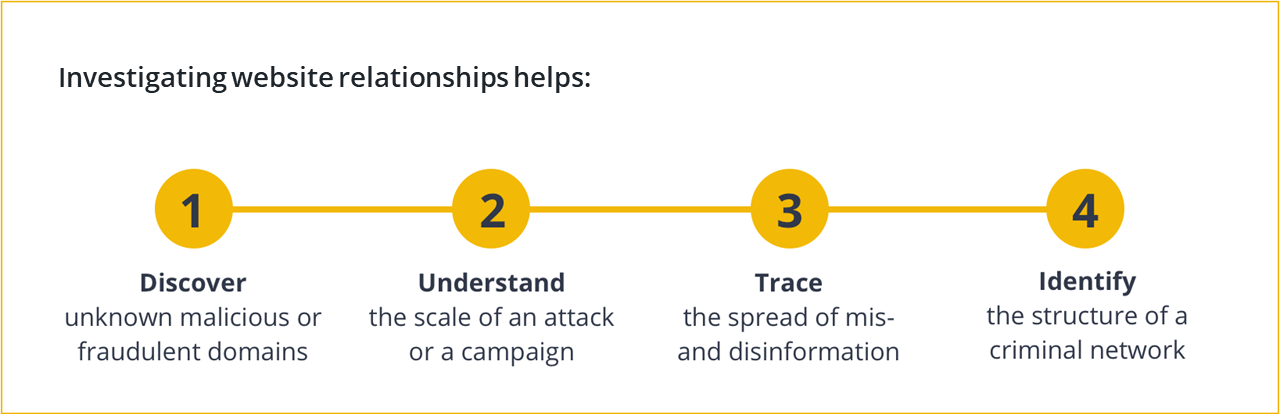
This is why it is important to study the internet relationships of a target website in order to investigate the criminal network possibly hidden behind it, understand the scale of a malicious campaign, or identify the threat actors who may stand to profit from it.
Study Website Relationships to Investigate Criminal Networks and Threat Actors 🔗︎
There are various ways to find websites associated to the target website and depending on the method used, the revealed relationships may also have varying implications. But first, how do we go from the one website we know to discovering all other seemingly irrelevant websites connected to it?
In this article, we list out four methods investigators can use to uncover hidden website relationships in Maltego, with the help of open source intelligence (OSINT) data.
4 Ways to Uncover Hidden Website Relationships with Maltego and OSINT 🔗︎
There are 4 ways to map and identify website relationships using Maltego and OSINT data:
- Network Footprinting with OSINT and Infrastructure Transforms
- Reverse Image Search using TinEye Transforms
- Website Tracking Codes with BuiltWith Transforms
- External Links on Webpage with Standard Transforms
Let us dive right in.
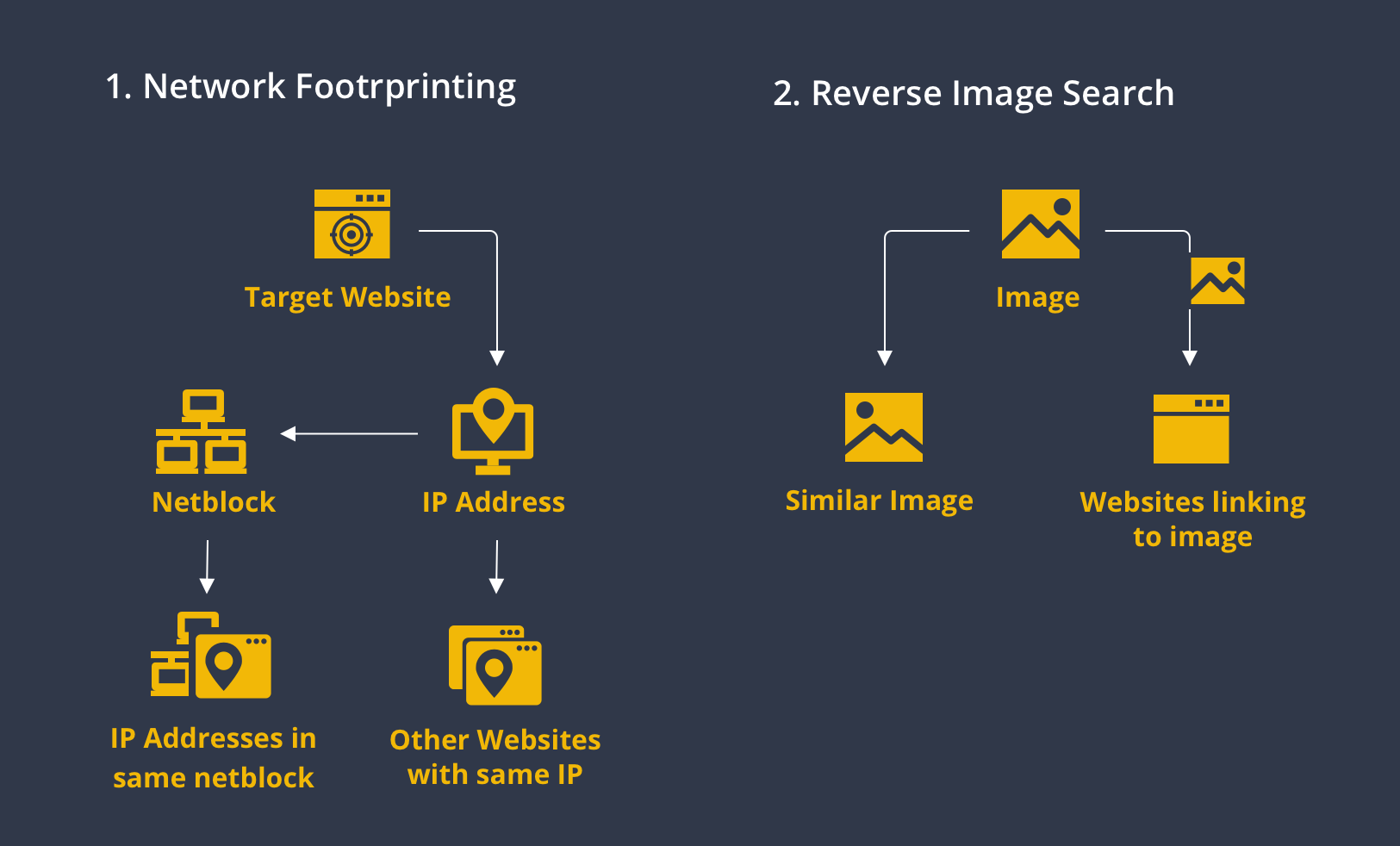
1. Network Footprinting (Network Reconnaissance) with Infrastructure Transforms 🔗︎
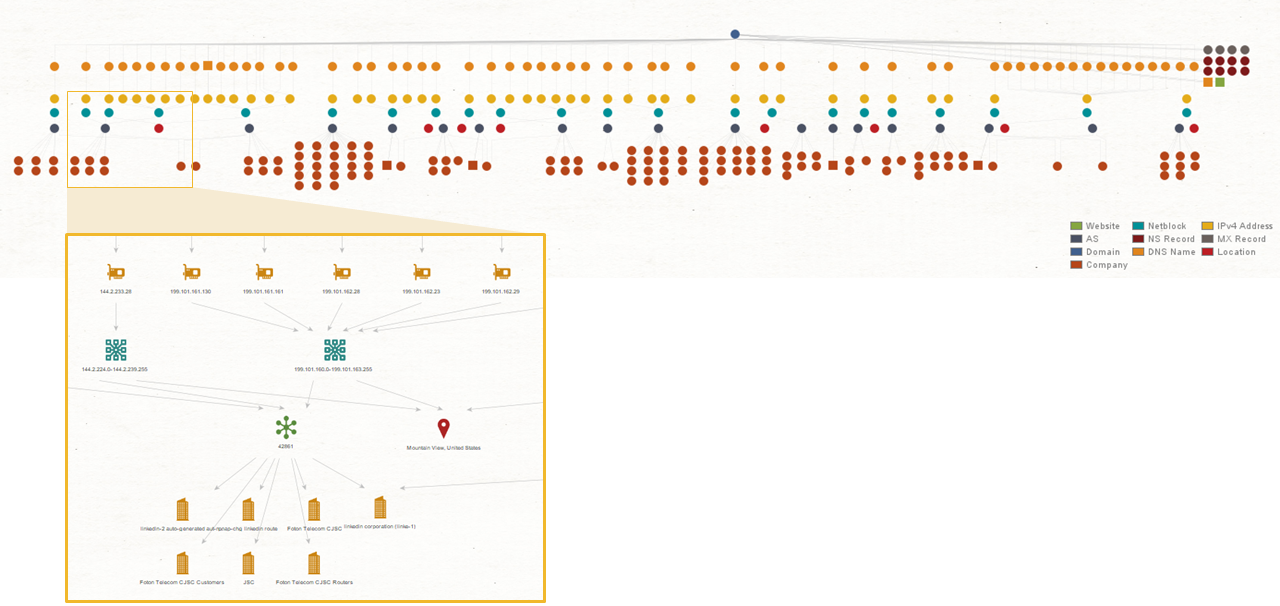
One of the most common approaches to mapping out connections between internet artifacts is through network footprinting. Also known as network reconnaissance, network footprinting is the technique used to gather information about a specific network environment.
Through network footprinting, investigators and cybersecurity researchers can identify whether websites or domains are hosted on the same IP address or if the IP addresses belong to the same netblock. On one hand, this indicates that the websites are in the same network infrastructure, which may lead to a single threat group. On the other hand, threat hunters can identify IP addresses hosting known malicious websites, block them to protect their network, and investigate further on the relevant websites.
Maltego has a collection of Transforms useful for network footprinting that pull infrastructure data both passively and actively from OSINT sources, as well as from integrations with third-party data providers like Shodan, PassiveTotal, Farsight DNSDB, PeeringDB, and more. Investigators can even automate the network footprinting process with Maltego Machines to speed up the workflow.
2. Reverse Image Search with TinEye Transforms 🔗︎
A second approach—specific to tracing the spread of disinformation and radicalization by means of visual elements and propaganda—is through reverse image search using the TinEye Transforms in Maltego.
TinEye’s reverse image search Transforms can be used for two types of queries:
- Images similar to the target image
- Websites linking to images similar to the target image
This helps investigators understand the spread of a particular piece of visual content containing misinformation or propaganda across the internet. Websites sharing similar content are likely run by those with similar mindsets, values, and goals.
Analysts might be able to identify the persons or groups manipulating such information by looking at which websites are sharing the same misleading images, and to whom or what these websites are related.
3. Website Tracking Codes with BuiltWith Transforms 🔗︎
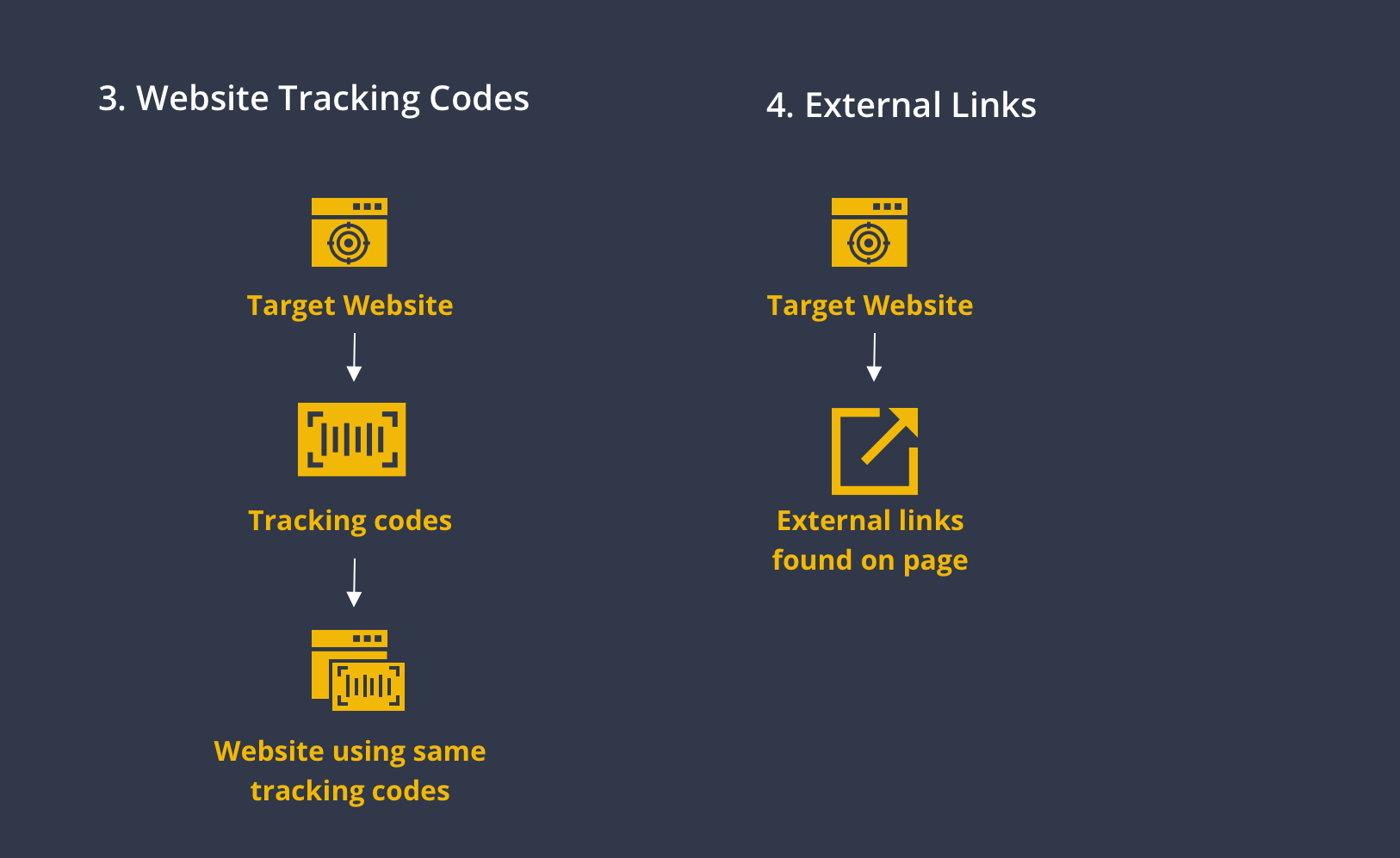
The third approach to discover hidden website relationships is through tracking codes.
Tracking codes are a couple of lines of JavaScript codes inserted into the “head” section of the HTML source code of a website. These codes connect the website with services like Google Analytics, Google Tag Manager, Facebook Pixel, and similar ones that website owners use to track and analyze traffic performance, user behavior, and more.
In every tracking code, there is a unique tracking ID that serves as the identifier of the property—websites or webpages—and account the tracking code is generated for.
The Maltego Transform To Relationships [BuiltWith], powered by the online internet research tool BuiltWith, finds and returns all tracking codes—among other internet technologies—found on the target website.
Running the To Matches [BuiltWith] Transform on these tracking codes will then return all websites BuiltWith came across before that are using the same tracking codes.
Having the same tracking codes can indicate various types of connections. The websites sharing tracking codes could possibly be run by the same individual or organization, be built by the same developers, or simply hosted on a mutual third-party platform. In any case, this is a quick and easy way to explore internet relationships.
4. External Links on Webpage with Standard Transforms 🔗︎
Finally, we can look at external links found on the target website to potentially uncover leads to common networks. The Maltego Standard Transforms include three Transforms that search the target webpages for external links:
- Mirror: External links found: This Transform mirrors the target website partially and extracts all external links found on the site.
- To Links [Found on web page]: This Transform scrapes the HTML source code of the target webpage and returns all external links found even if they are not visible on the actual webpage.
- To Websites [Links on this web page]: This Transform connects to the website where the target webpage is hosted, downloads the page, and looks for external links on that page.
With these Transforms, investigators can easily spider a target website and extract relevant external links that might represent connections between phishing websites, disinformation campaigns, and criminal networks.
Investigate Who and What are Behind A Website in Maltego 🔗︎
That concludes our tutorial of how to discover hidden relationships between websites and potentially identify the threat networks behind an attack or campaign. Of course, you can use these four methods separately or together—for example, by conducting a network footprint on websites sharing the same tracking codes. These four methods are also just entry points to start an effective threat hunting investigation or trace suspicious disinformation campaigns.
Don’t miss out on our latest tutorials, use cases, and development—follow Maltego on Twitter and LinkedIn and subscribe to our newsletter.
Happy investigating!


 4.5 rating
4.5 rating