Social media intelligence (SOCMINT) is considered a subdiscipline of open-source intelligence (OSINT). SOCMINT can be defined as the techniques, technologies, and tools that allow for the collection and analysis of information from social media platforms.
SOCMINT can be harnessed by government or non-state actors, such as private intelligence agencies or marketing companies, to gain knowledge about specific individuals, groups, events, or other targets. While SOCMINT generally falls under the category of OSINT, there are some key differences worth noting.
In this article, we will walk you through everything you need to know about social media intelligence and the best practices for conducting social media investigations. For a more extensive version with practical workflows, you can download the handbook below!
Table of Content 🔗︎
SOCMINT vs. OSINT 🔗︎
SOCMINT is not as straightforward as OSINT because there is a belief, particularly by users and privacy advocates, that there is some expectation of privacy when using a social media platform. While OSINT investigators may not agree with this expectation, there is another aspect of SOCMINT worth considering.
OSINT investigations focus solely on publicly available information while SOCMINT investigations also use information found on social media platforms that was intended only for a specific audience. For instance, an investigator might join a private group or create a fake account to gain access to information provided by a person of interest. These situations make SOCMINT more difficult to navigate for investigators, and every effort should be made to comply with laws, regulations, and policies around intelligence gathering and investigations.
In these investigations, government investigators will likely go through the court system to request subpoenas or warrants to obtain information directly from the social media platform. Often, some SOCMINT techniques will have already been employed to gather the data used to support the issuance of those subpoenas or warrants.
SOCMINT Concepts and Terms 🔗︎
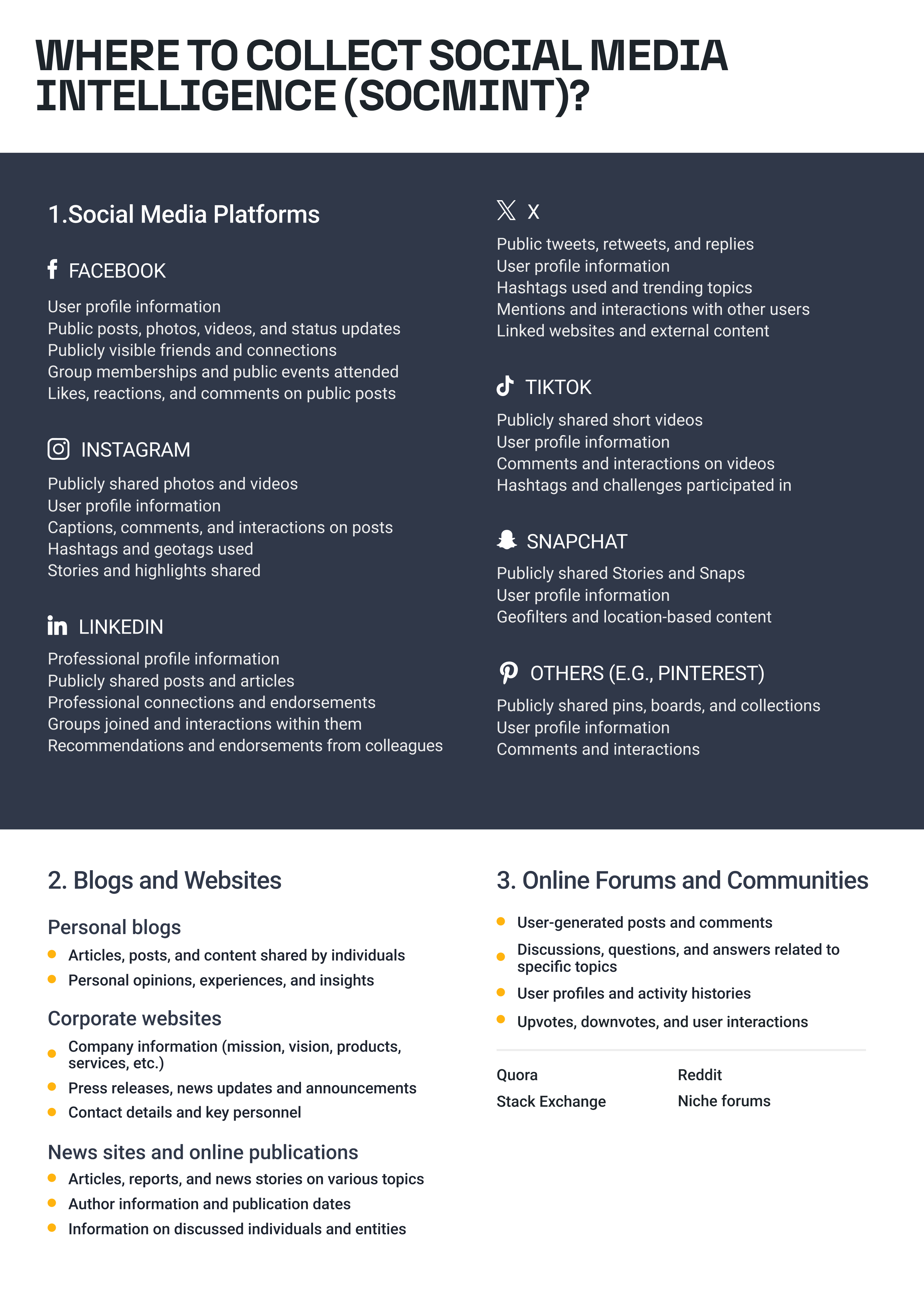
There are many nuances in the field of SOCMINT, including the type of information that can be gathered and the type of platforms that can be used to gain information.
First, it is important to understand that SOCMINT includes all social media platforms, not only social networking sites. Social networking sites, like Facebook and LinkedIn, only make up one portion of the platforms that can be used to gather data. Information can be found on media-sharing sites like Instagram, forums like Reddit, image-sharing sites like Pinterest, video-sharing sites like YouTube, microblogging platforms like Twitter, social gaming platforms like Xbox Live, and blogs created using platforms like WordPress.
Next, it is important to know the types of information that can be gathered from social media platforms. We can break this information down into three general categories:
- Profile Information: Static information provided about a specific user that is observable by those who access the profile. On LinkedIn, for instance, this might include a user’s job title, current and former employers, skills, and contact information.
- Interactions: Users on a social media platform can interact with the platform or other users in many ways. These forms of interaction include posting/commenting, replying to someone else’s content, posting pictures or videos, and liking or reacting to existing content.
- Metadata: Information found on social media platforms is not limited to text and pictures. It can also include contextual information about said pieces of content. Metadata can include the location tagged in a post, the time that the post was made, or even the type of device used to take a picture.
Uses for SOCMINT 🔗︎
SOCMINT is commonly associated with investigations of a group or individual involved in criminal activity, but that isn’t the only scenario where it can be useful. Other types of investigations where SOCMINT could be employed include:
- Terrorism
- Organized Crime
- Human Trafficking
- Child Sexual Exploitation
- Disaster Prediction and Response
- Population Density
- Economic Analysis
- Health and Disease Monitoring
- Drug Use and Trends
- Cybercrime
While this is not an exhaustive list, it is meant to demonstrate that SOCMINT has many uses outside of those common to law enforcement. While state actors are prolific users of SOCMINT, private companies and organizations also use SOCMINT to collect information to better inform business decisions, improve marketing, ensure brand protection, and identify patterns and trends.
SOCMINT Challenges 🔗︎
Though there is a wealth of information available through social media platforms, that does not mean that the use of SOCMINT is easy or simple. There are several challenges that face investigators who employ it.
- Number of Users: Social media platforms like Facebook and Twitter boast billions of users each month. With the sheer amount of data available, it can be difficult to find the information relevant to a particular investigation.
- Identification of Users: Many platforms operate with the intention of keeping their users’ identities private, creating challenges for investigators. Additionally, the increased prevalence of fake accounts and bots on these platforms can make it extremely hard to figure out which data is accurate, available, and useful.
- Compromising Trust: There has been an abundance of stories over the last few years about data leaks and user information being compromised, which can cause users to think twice before sharing information online. Additionally, as governments continue to employ SOCMINT techniques, they risk violating the privacy of their citizens, creating an unstable relationship between authorities and the people they serve and protect.
About Social Media Investigations 🔗︎
SixDegrees.com launched in 1997. It is often described as the first social media where users would have their real name, a list of friends, and personal information displayed on their profile. At its peak, it boasted more than 3.5 million users. Since then, other websites and apps have replaced it, and it’s estimated that billions of people use social media nowadays. This means that for any given investigation, it is likely that some data or clues can be harvested from social media.
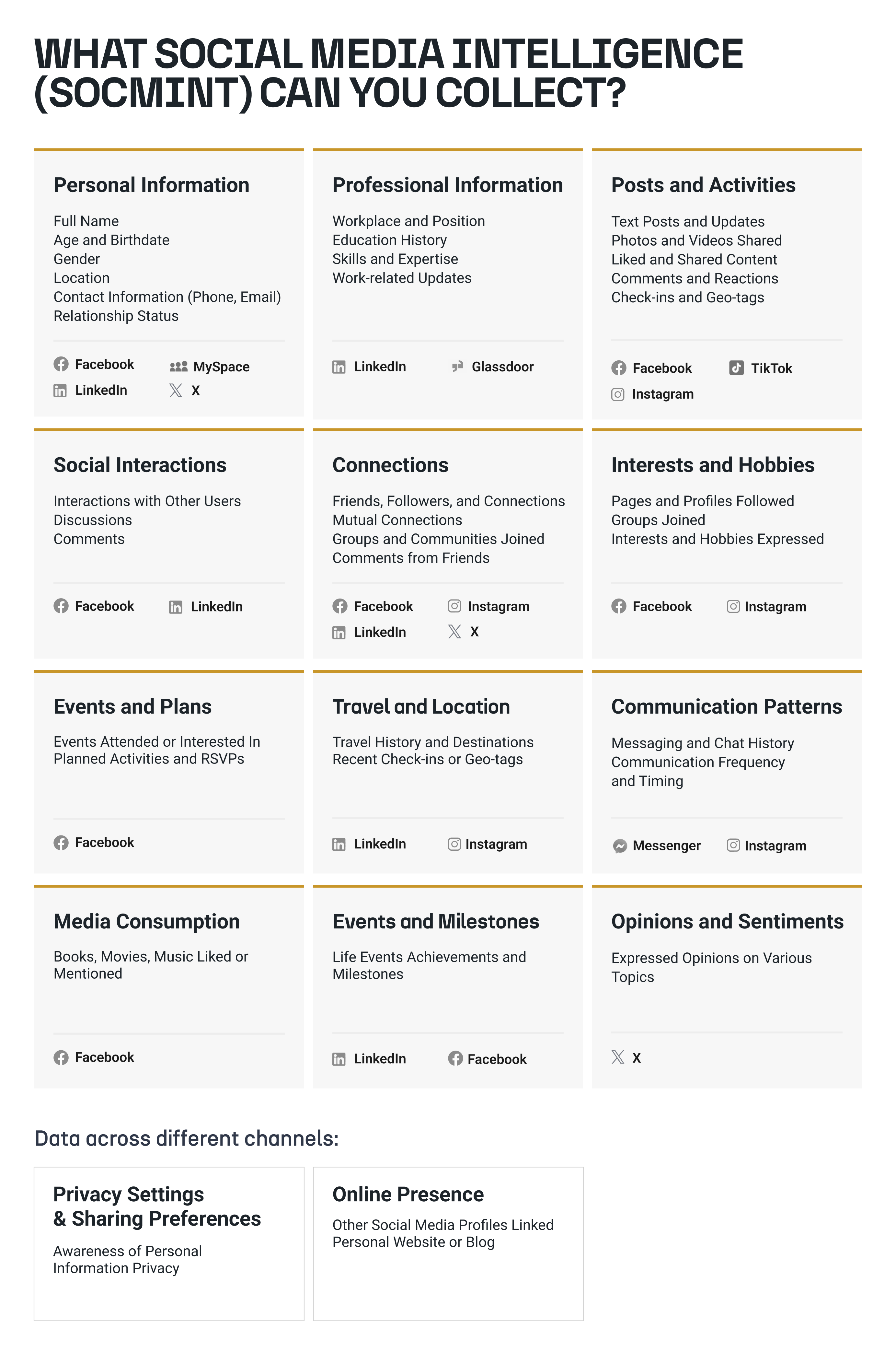
What Can Be Found Using Social Media? 🔗︎
What you can find on social media depends vastly on the individual or entity you’re looking into, and on the platform itself. Some, like LinkedIn, have by design a userbase wanting to be found and desiring to use their profile to display their professional experience.
Others, like Twitter, have profiles that may be less informative but may provide more context in the contents of the posts made by an account. While the information on LinkedIn tends to be more curated because it’s geared towards a professional environment, not everyone expects other people to pay attention to their tweets.
How Can You Find a Profile To Investigate? 🔗︎
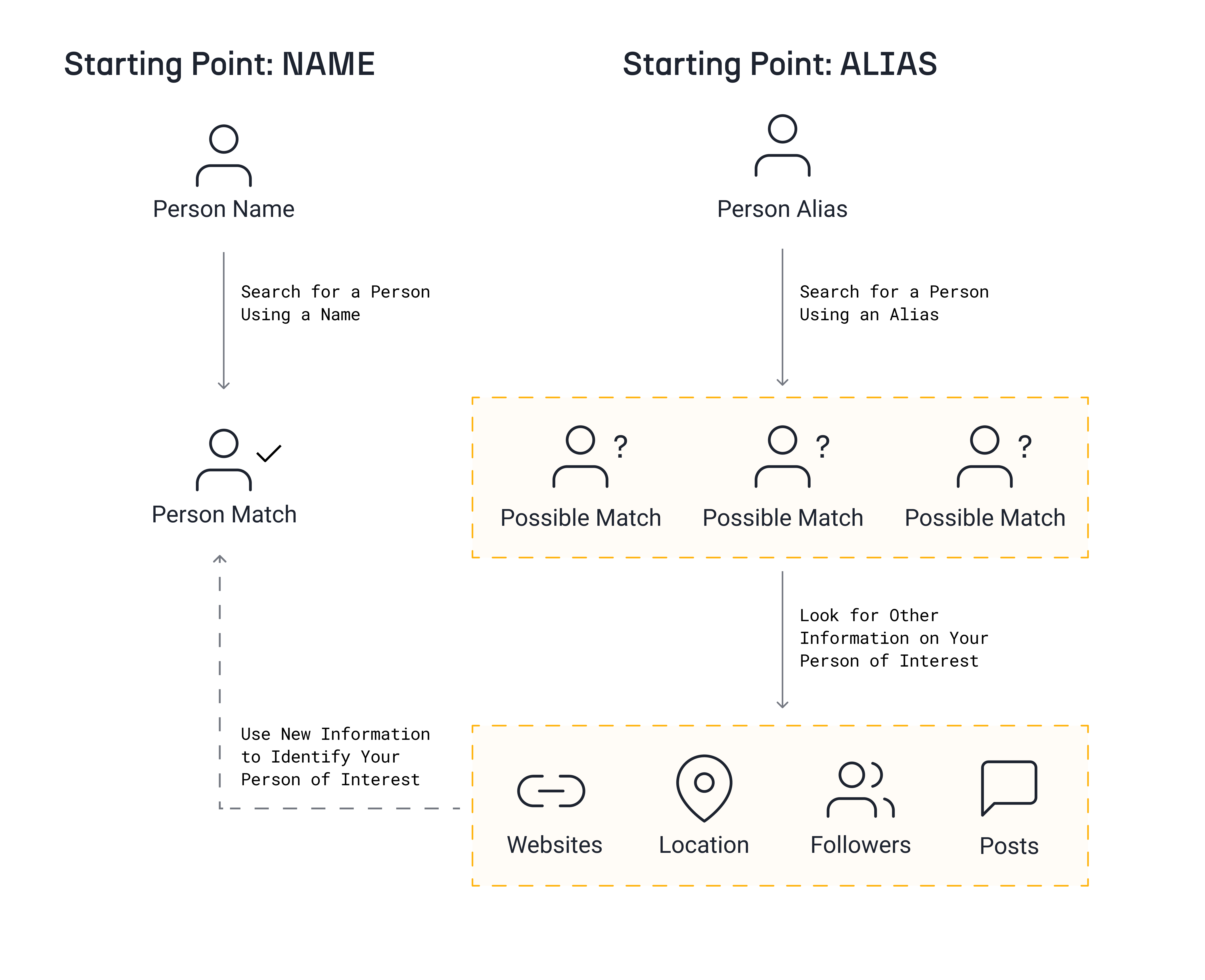
The first thing to do when investigating someone on social media is to find the account that belongs to that person. This can be done in several different ways, but we can identify at least six pivot points that will help us find social media accounts belonging to an individual:
- Name: The name of a person is a good starting point as it will often return a Facebook, Myspace or LinkedIn account. However, it is also the first personal identifier people will avoid using or disclosing if they do not want to be found.
- Email address and phone number: These are great starting points because they’re usually only shared between accounts, and thus, individuals, that are somehow connected. If two accounts on different platforms share the same phone number or email address, it indicates a connection. The problem with these data points is that they usually aren’t easily searchable (Skype is a notable exception) and are not displayed on the profile of a person of interest.
- Alias: Also known as username or the pseudonym, alias is often reused across different social media platforms. The advantage of this data is that it is extremely easy to search: Any social media platform that has usernames allows you to search for and connect with users with a particular alias, as it is often a core concept of the platform. The main issue with this is that aliases are only as good as they are unique: One can assume that two accounts on different platform sharing a rather specific username such as “LittleTroll15245” are likely to be operated by the same person. But even then, one would need to investigate further to corroborate the link. If the account has a more generic username like “BlueDragon,” finding an account on another platform belonging to the same individual solely based on the alias might prove difficult.
- Profile pictures: Profile pictures fall into the same kind of category as aliases, which means that with luck, doing a reverse image search from a picture found on a profile might just lead you to an account operated by the same person. However, it can also be that two different people thought that a particular image would look good on their profiles. Searching for accounts by a picture is also much more difficult because you rely on reverse image search engines, which is usually not a feature supported by social media platforms. The only advantage of profile pictures is that not everyone is aware that they can be used as a pivot point. Thus, they tend to reuse them more often than aliases.
- Address and bio: Addresses and bio might be the most difficult pivots to exploit. Seldom will an individual reveal their physical address on social media. Platforms that scrape online information such as Pipl are more likely to yield relevant results from that kind of information. On the other hand, bio should always be scrutinized as some individuals link their social media accounts using their bio.
What Can Be Automated and What Do You Need To Verify? 🔗︎
There are two types of information that can be found on social media:
- Information that the user wants to share
- Information that the user forgot to hide—for a lack of concern for their privacy or because they didn’t notice
The main difference between the two, from our point of view, is that the first type of information can be automated and thus obtained pretty easily: Jump into Maltego Graph to pull the list of friends of both profiles. The friends in common will appear before your eyes.
The second type of information, however, will often require an investigator to pay close attention to the sometimes-extensive content displayed on a social media profile. This content analysis can be simplified and accelerated in Maltego Evidence, which automatically collects social media data from multiple platforms in a standardized way.
Maltego Evidence (formerly Social Network Harvester), included in the Maltego Organization plan, enables investigators to scrape, analyze, and cross-reference text, images, videos, and other forms of interaction between multiple social media profiles. The Maltego Organization plan also gives you access to Maltego Monitor (formerly PublicSonar), which allows analysts to perform real-time social media monitoring and AI-powered sentiment analysis of potential and ongoing public safety disruptions across multiple platforms.
Are You Investigating the Right Profile? 🔗︎
The first thing you should do when conducting a social media investigation is to make sure you have the right profile. There are some platforms where, using your real name, displaying information about yourself, and having an actual photo of your face as a profile picture is the norm (e.g., LinkedIn). In this scenario, it is pretty easy to cross-reference data at hand and identify the profile related to a person of interest. This type of profile is the one you will obtain when starting your search from a name.
However, starting your search from an alias might yield other kinds of profiles where there is less information available for you to establish the difference between an account that coincidentally happens to have the same alias used by the person of interest, and an account that belongs to said person of interest.
To properly draw conclusions, you can first check information such as the location or the other social media they link in their bio (if any). If there is no such information, looking at their posts and account followings might help.
- Are they posting about a particular topic that you know is connected to your person of interest?
- Are they following an account tied to a particular location like a local police department or a small town mayor?
To verify these things, you can pull the list of posts and followed accounts into your Maltego Graph, or visualize and show this in one of the interfaces in Maltego Evidence.
How Can You Access the Information on a Profile? 🔗︎
Maltego will provide you with Transforms to pull most of the data available on a profile directly into your graph. This will save you a great deal of time as you won’t have to comb through the profile yourself which, depending on the platform, might require you to have an active account.
It should be noted that an investigator should never use a personal account to collect information. A sock puppet account reserved for research purposes should be created to do so. Be aware that some platforms tell their user when someone has seen their profile, as is the case of LinkedIn.
Download Handbook 🔗︎
In this handbook, we will show you 6 standard investigative workflows using the Maltego Graph and SOCMINT, pivoting from the following starting points:
Download the resource
We hope this handbook will help you collect relevant social media intelligence and find online traces of your person of interest in Maltego.
For more insights, check out our other resources:
- Social Media Data Recommended to Build Your Criminal Case
- How to Use Sock Puppet Accounts to Gather Social Media Intelligence
- Unmask Cybercriminals’ Real Identities with Constella and Maltego
Don’t forget to follow us on Twitter and LinkedIn and sign up to our email newsletter, so you don’t miss out on updates and news!
Happy investigating!


 4.5 rating
4.5 rating