Hashtags, location filters, reverse image searches, Google Dorks, archive services – using these advanced open-source intelligence (OSINT) techniques have become the bread and butter of today’s OSINT investigators.
And there are other tools and tricks of the trade at your disposal. With them, you can achieve much more as an OSINT analyst and improve the effectiveness and accuracy of your analyses.
In this article, we will share investigative tips and resources that will help you become a more valuable OSINT investigator.
Table of Content 🔗︎
How to Stay at the Top of Your Game as an OSINT Analyst 🔗︎
Sharpening your OSINT skills works similarly to how you put together fragmented pieces of information from open-source databases to make connections.
The catch is that, much like the cases you work on, there is no single path, definitive course, or playbook containing all OSINT knowledge that guarantees success. (Though some would argue that Michael Bazzell’s fifth edition of “Open Source Intelligence Techniques” comes remarkably close!)
On the bright side, there are methods and approaches that you can include and replicate to improve the accuracy and integrity of your OSINT analysis.
1. Be Ruthlessly Selective and Validate, Validate, Validate! 🔗︎
Avoid information overload when you add unclassified data to your existing intelligence processes without validating it.
The rule of thumb is to be meticulously selective and strategic about which OSINT data to incorporate and whether you’ll have the means to cross-reference the data, assess the source, and explain its relevance to other collaborators and stakeholders. You should be especially vigilant now with the explosion of AI-generated content, to avoid falling for manipulated information.
Once you have made some assumptions based on data that is available to you, try to poke holes in your own logic. Look for evidence that proves or disproves your hypothesis, and ask the following questions:
- Can I validate it?
- Can I vouch for this data’s authenticity?
- Can I explain its relevance to the overall investigation?
- What techniques can I apply to avoid bias?
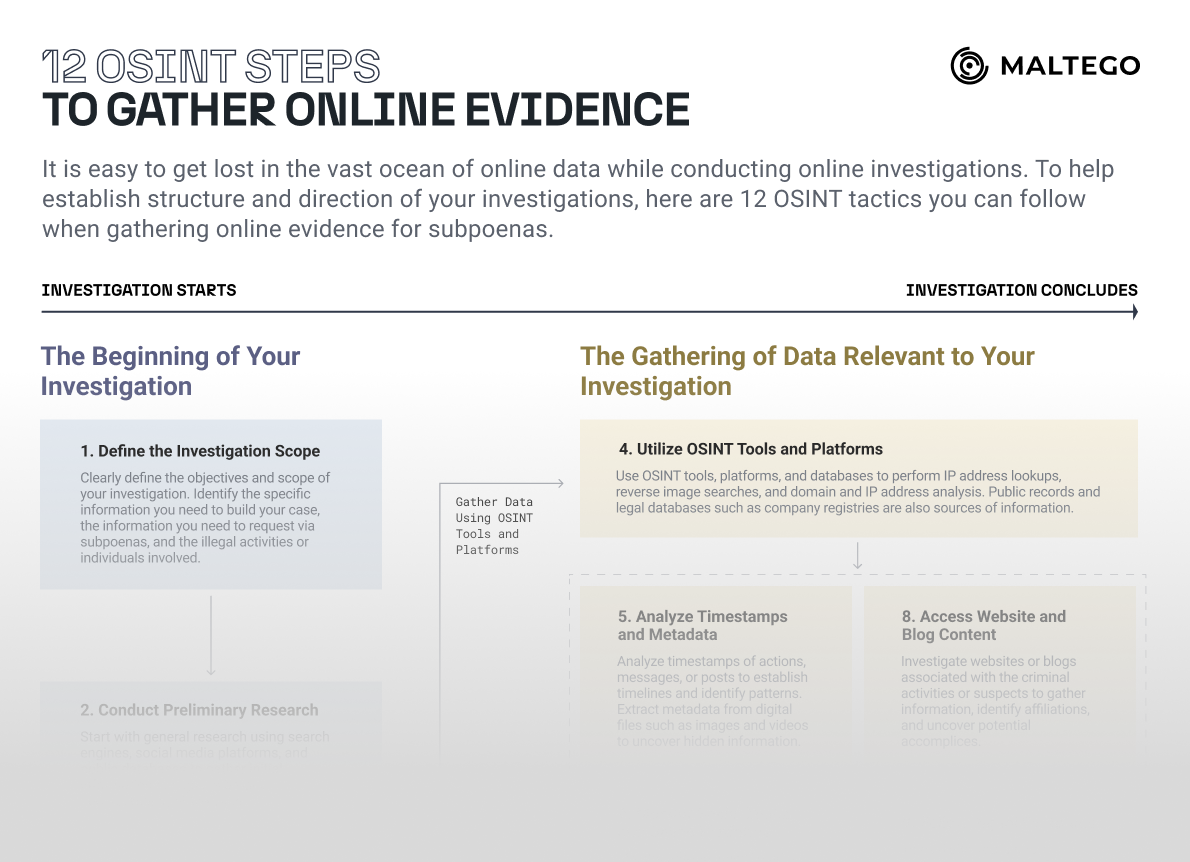
INVESTIGATOR TIPS To help you in the process of finding answers to these questions, you can also make use of some additional materials on our blog: Our cheat sheet outlining 12 essential OSINT tactics also supports you to be truly selective among the vast amounts of online data coming from various sources. These guidelines will help you establish structure and direction for your investigations, whether you are gathering online evidence for ongoing cases or preparing to request subpoenas.
2. Repeat the Motto: Security, First! 🔗︎
We have already used up a lot of digital ink on our blog to list the best operational security (OPSEC) principles and practices and how to apply them in your daily work. But the topic of compromised credentials is so vast and crucial that it’s impossible not to mention it when speaking about increasing your professional skills.
Expert investigators not only follow the OPSEC rules of the company where they work. They independently and proactively check whether their own or their collaborators’ credentials have been compromised, and advocate for new principles and measures to be adopted by their peers.
What if a compromise does occur? Keep a cool head at all times and inform whoever needs to be informed while keeping your ego in check. A valuable investigator is not only someone who can effectively complete investigations but also someone who can admit a mistake sooner (way sooner!) rather than later.
After all, what counts is making your operation safe, and it’s a team effort. Having an immediate response checklist at your disposal to refer to and informing the rest of the team without hesitation can only improve the speed at which you can assess, contain, and recover from data breaches, adding another point to your resume.
INVESTIGATOR TIPS Here are some additional tools that can help you protect your identity, which you might find useful to try: For more information on adding an extra layer of security to your operations, explore our other resources:
3. Learn from Other Investigators 🔗︎
Many OSINT professionals and enthusiasts write about their experiences and share case studies on their blogs or in closed forums. The key: Instead of merely reading about an interesting case, you should actively try to replicate those use cases. This helps you identify systematic approaches to data collection, analysis, and verification, along with developing useful workflows for future reference.
Additionally, you learn about the capabilities and limitations of various tools and technologies in a practical setting. You can then use this knowledge to assess whether your current toolkit is sufficient for the types of investigations you conduct and which methodologies are effective for the investigators you follow.
Although you won’t always have access to exactly the same data or tools, you will be able to identify and utilize the patterns and approaches in the investigator’s train of thought when tasked with a similar case.
INVESTIGATOR TIPS If you want to connect with fellow OSINT investigators, check out our ready-to-download list featuring 15 reliable OSINT and cyber threat intelligence (CTI ) organizations and associations. For more OSINT learning materials, check out our list of over 100 websites, blogs, podcasts, YouTube channels, and books, covering not only OSINT but also Cybersecurity, Cybercrime, and Trust and Safety insights.
4. Build up Your Credibility 🔗︎
While communities like these offer a wealth of practical knowledge, administrators of more closed and niche groups may be selective and careful when admitting new members.
The reason is that investigators may be hesitant to reveal all their techniques in public spaces because they need to be cautious about disclosing information in case malicious actors exploit their expertise. How can you prove you’re there for the right reasons?
There is some work to be done on your part to help open the doors for you to access this wealth of knowledge. Demonstrating that you work for a renowned organization is one thing, but don’t let it be your only ace in the hole.
You can build your credibility by sharing your contributions in various other, more accessible communities, attending industry events, participating in capture-the-flag contests, and expanding your network.
INVESTIGATOR TIPS While you’re working on your contributions to the community, keep these things in mind:
5. Be Critical of Expert Information 🔗︎
Do you remember the first tactic? “Be Ruthlessly Selective and Validate, Validate, Validate!” – this applies not only to the use of data in your investigations, but also to the expert information you consume.
Be mindful of whose advice you follow. If an investigator consistently shares faulty results, this should be a clear signal to you.
What if you only follow “the most popular” and “the most renowned” experts?
Always Question Ready Assumptions!
Continuously question the status quo and scrutinize your own reasoning by seeking out evidence that supports or contradicts hypotheses.
6. Collect Insights from Maltego Experts and Partners 🔗︎
Our Maltego Subject Matter Experts are also keen to contribute to the OSINT community. We share our expertise and often leverage our network to partner with other industry experts.
We consistently publish insights on applying OSINT in cybercrime investigations and cyber threat intelligence:
- Explore thought leadership and ready to replicate workflows on our blog
- Attend webinars featuring insights from Maltego SMEs and industry partners
- Subscribe to our newsletter for the latest updates and insights
For existing and new Maltego users, we also offer access to our learning platform, Spark, where you can explore a full catalog of courses, both live and on-demand, and participate in live sessions hosted by Maltego SMEs. These resources enable investigators to leverage their OSINT knowledge to the fullest within the platform.
Download Your OSINT Resources 🔗︎
While this article has provided some insights and methods to enhance your investigative skills, there’s always more to discover and apply in the ever-evolving field of OSINT.
Below you can find resources we recommended in this article to further equip you with more knowledge for advanced open source intelligence work:
12 OSINT Steps to Gather Online Evidence 🔗︎
Download the resource
15 OSINT and CTI Communities and Organizations to Follow 🔗︎
We hope these materials will inspire you to continue learning and refining your skills with Maltego. Keep investigating, stay curious, and don’t forget to check back for more insights that we share on our blog, Twitter, LinkedIn, and Mastodon, or email newsletter.
Happy investigating!
About the Author 🔗︎
Daphnée Aguilar 🔗︎
Daphnée is a Criminologist with more than 10 years of experience as an Intelligence Officer. She specialized in developing actionable intelligence for identifying, preventing, and neutralizing threats and risks from Transnational Organized Crime. Driven by the feminist movement, her last research was on the Effects of Gender and Racial Bias on Gender-Based Violence Policies. She considers herself a professional taco taster.










