In November 2023, amid the bustling holiday sales, with buyers eagerly clicking on Black Friday discounts and Cyber Monday specials, phishing incidents saw a staggering 237% increase in the first half of the month, compared to the period between September and October.
This article will analyze why and how attackers use phishing and how you can use Maltego to detect and investigate the malicious infrastructure behind these attacks.
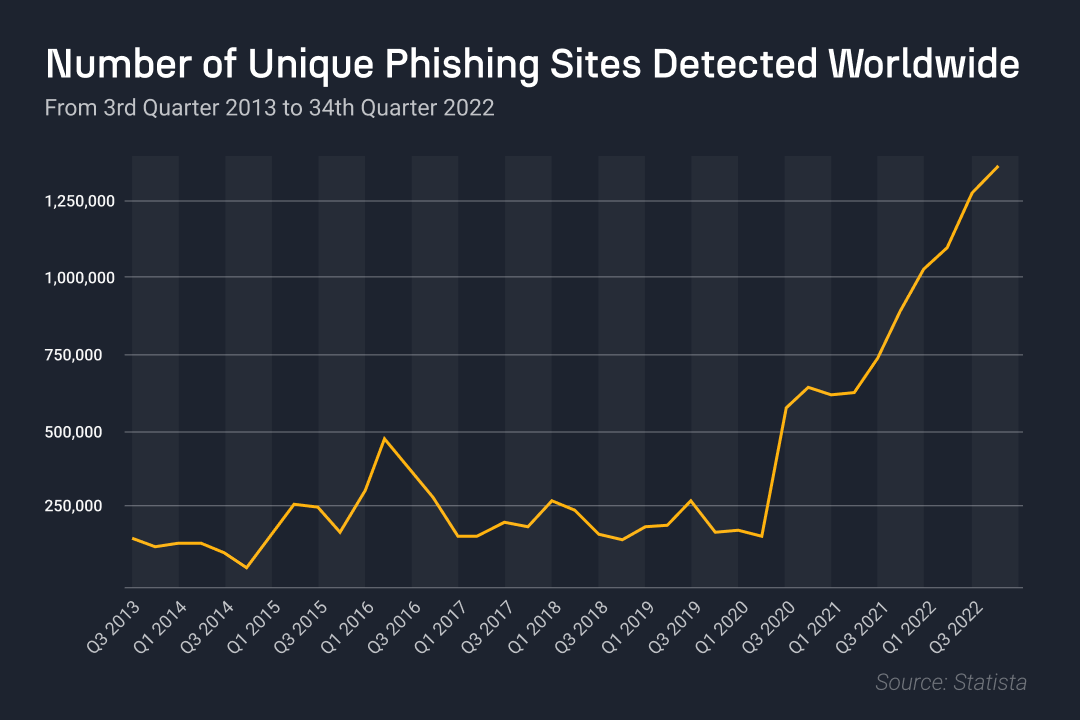
Source: Statista
In addition to a skyrocketing surge in phishing incidents, we have seen a dramatic increase in new phishing sites in recent years, especially around significant events such as after the COVID-19 pandemic or during the holiday season.
Attackers exploit the eagerness for deals and the season’s general chaos around these events to increase their campaigns’ success rate. It is estimated that 90% of successful cyber-attacks start with phishing.
What Companies Should Know about Phishing 🔗︎
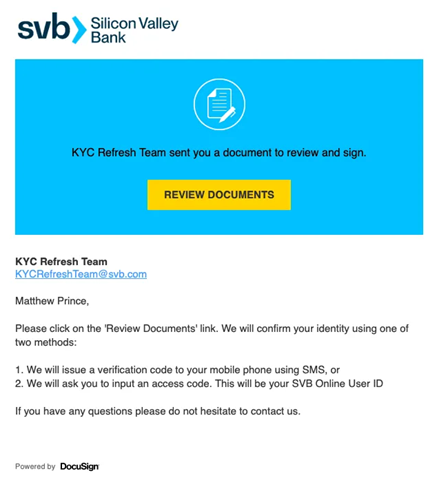
By now, most of us are familiar with spam – those unsolicited commercial emails companies send, pushing their products or services. But hidden among those annoying emails lies a more sinister type of communication: phishing emails.
Between May 2022 and May 2023, Cloudflare detected over 250 million suspicious emails, that’s more than 700 thousand emails, like the one below, flooding our inboxes daily.
Source: Cloudflare
This is important because responding to and mitigating the effects of phishing attacks requires significant resources. Cybersecurity teams are already swamped with thousands of alerts daily, so they must be especially vigilant and prepared to deal with an increased volume of potential threats during the holiday season to protect their organization and its assets.
How Phishing Works 🔗︎
Unlike straightforward spam, phishing emails are crafted with the intent to deceive through identity impersonation. This method of attack isn’t limited to just emails, it also occurs through other channels such as text messages via SMS or messaging platforms like WhatsApp.
These messages often create a sense of urgency or invoke fear - such as a warning about an unauthorized login attempt on your bank account or an incredible deal that expires soon. They might also include requests for a delivery address or to update your data immediately. By pushing the recipient into hasty action, the attacker hopes to bypass rational scrutiny.
Attackers generally use phishing to:
You can read more about phishing in our article “Phishing Attacks Part 1: What You Should Know About Phishing Activities."
Common Techniques in Online Frauds 🔗︎
The typical Tactics, Techniques, and Procedures (TTPs) used by attackers in online frauds, especially during high-traffic shopping events like Black Friday and Cyber Monday, can be sophisticated and varied.
These threat actors frequently resort to proven techniques such as cloning legitimate websites of well-known brands and waiting until the last minute to register their domains to avoid detection. Let’s talk about these commonly used TTPs in phishing.
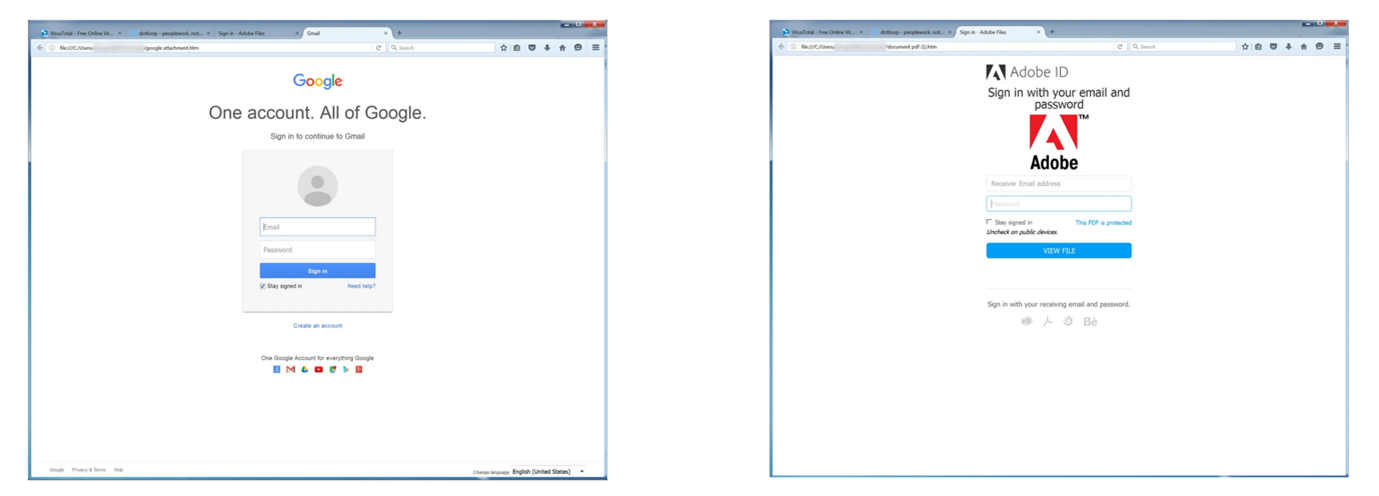
Cloned websites 🔗︎
One of the most common and successful techniques attackers use is the impersonation of legitimate brands or websites. According to Proofpoint’s 2023 State of The Phish report, 44% of people think an email is safe if it comes from a familiar brand, which is why threat actors love this technique.
Source: KnowBe4
Attackers clone and host fake instances of legitimate websites to trick their victims and harvest personally identifiable information (PII), credentials, and banking details. This data is then sold on dark web forums or leveraged to launch social engineering attacks.
Newly Registered Domains 🔗︎
According to Cloudflare’s 2023 Phishing Threats Report, one-third of detected threats featured newly registered domains. These domains usually resemble legitimate brands like Amazon to trick their victims.
Generally, most phishing domains, especially those themed around events like Black Friday, are registered within 24 hours of the event to avoid detection.
INVESTIGATOR INSIGHT In order to test this, we can perform a review searching for registered. domains that contained keywords like Amazon, (black+friday), and (cyber+monday). 3 million new domains can be found between November 1st and November 30th. An important spike in domain registrations within 24 hours of Black Friday and Cyber Monday was found, confirming our mentioned hypothesis. We can also observe that the registrations drop back to zero immediately after the events. These results underscore the vigilance and preparedness of cybersecurity teams during this season, emphasizing their crucial role in maintaining security amidst these trends. 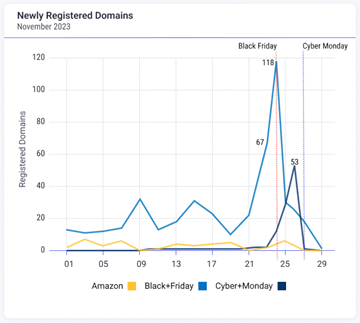
Using Maltego to Find Phishing Domains 🔗︎
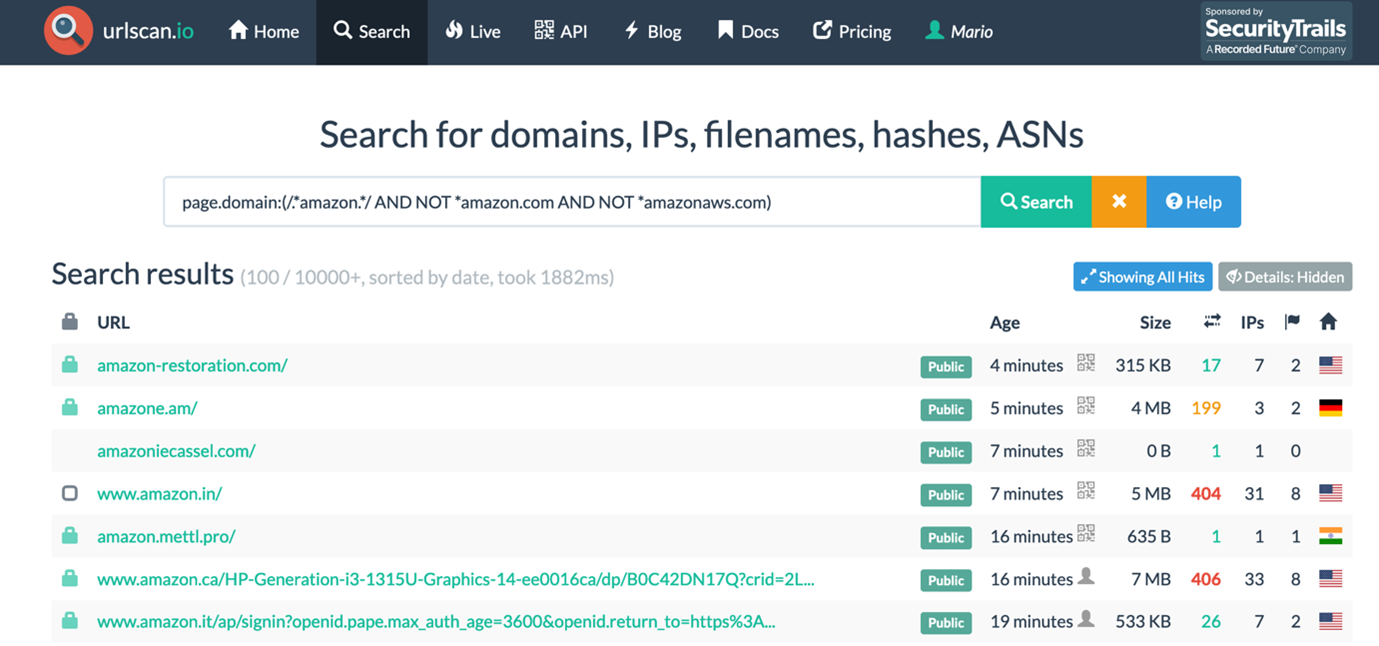
Maltego already has great articles describing how to investigate phishing domains. Building on this, we will illustrate how to use Maltego to identify suspicious domains while filtering irrelevant data. Additionally, we will show you how to get a fresh list of interesting domains using urlscan.io, a free service to scan and analyze suspicious URLs.
Urlscan.io allows you to search for domains, IP addresses, hashes, filenames, and more. It also offers multiple filters to help you achieve the best results, which we will take advantage of.
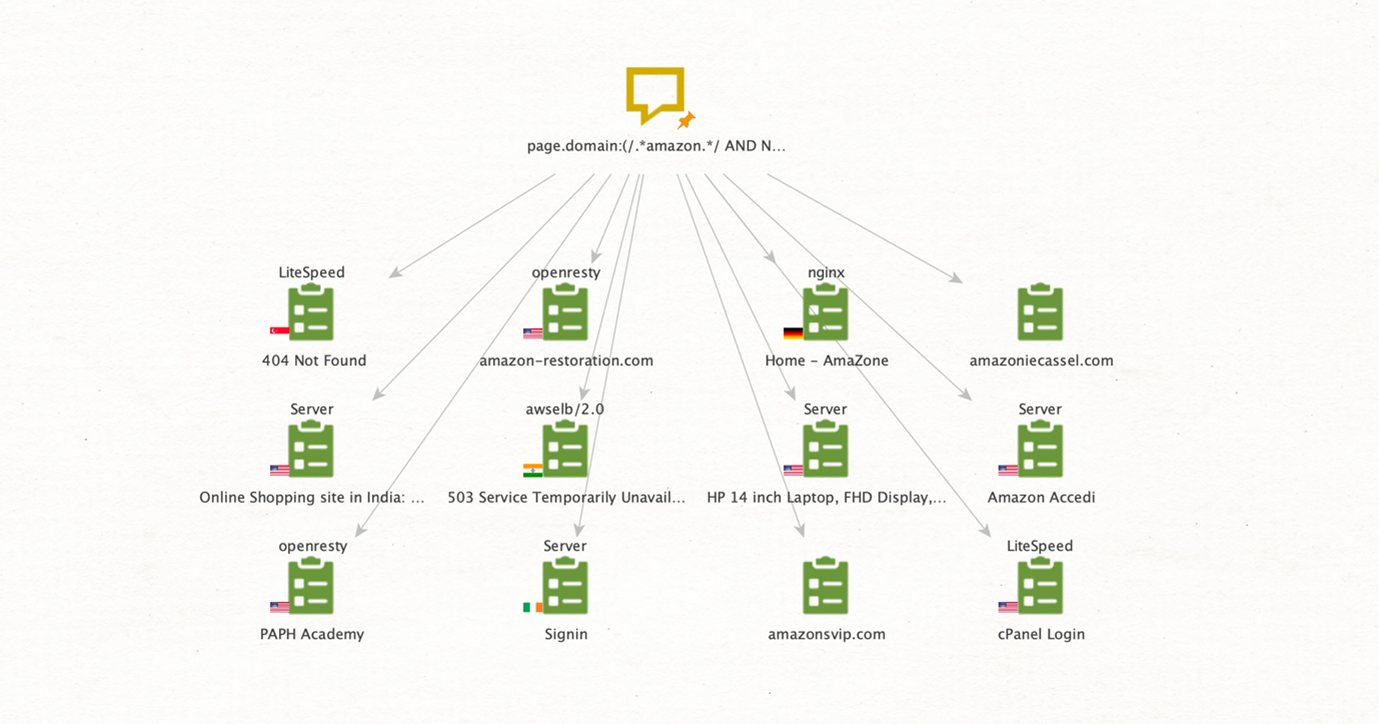
Our goal is to find domains that mention Amazon in their name but are not related to standard Amazon domains like amazon[.]com or amazonaws[.]com. Considering this data source has a rich query syntax, we can use the following one to get what we are looking for.
Some interesting domains like amazone[.]am can be easily spotted, and a few that might be legitimate Amazon domains like amazon[.]in or amazon[.]it Don’t worry, we can use Maltego to find the bad ones. In fact, we don’t need to go to urlscan’s website at all, as we can get the same results directly in Maltego.
All you need to do is add a Phrase Entity to a new graph in Maltego, paste the same query we have just used on urlscan’s website, and then run the Search in Other Scans [urlscan.io] Transform.
Keep in mind to adjust the Results slider depending on the number of maximum hits you want to manage, by default Maltego returns 256 urlscan Result Entities.
These types of Entities contain a lot of useful information like the URL, the website title, and the geolocation of the website.
Now, we need to extract the URL from the properties to continue our investigation. Let’s select all the urlscan Result Entities and run the Extract Submitted URL [urlscan.io] Transform.
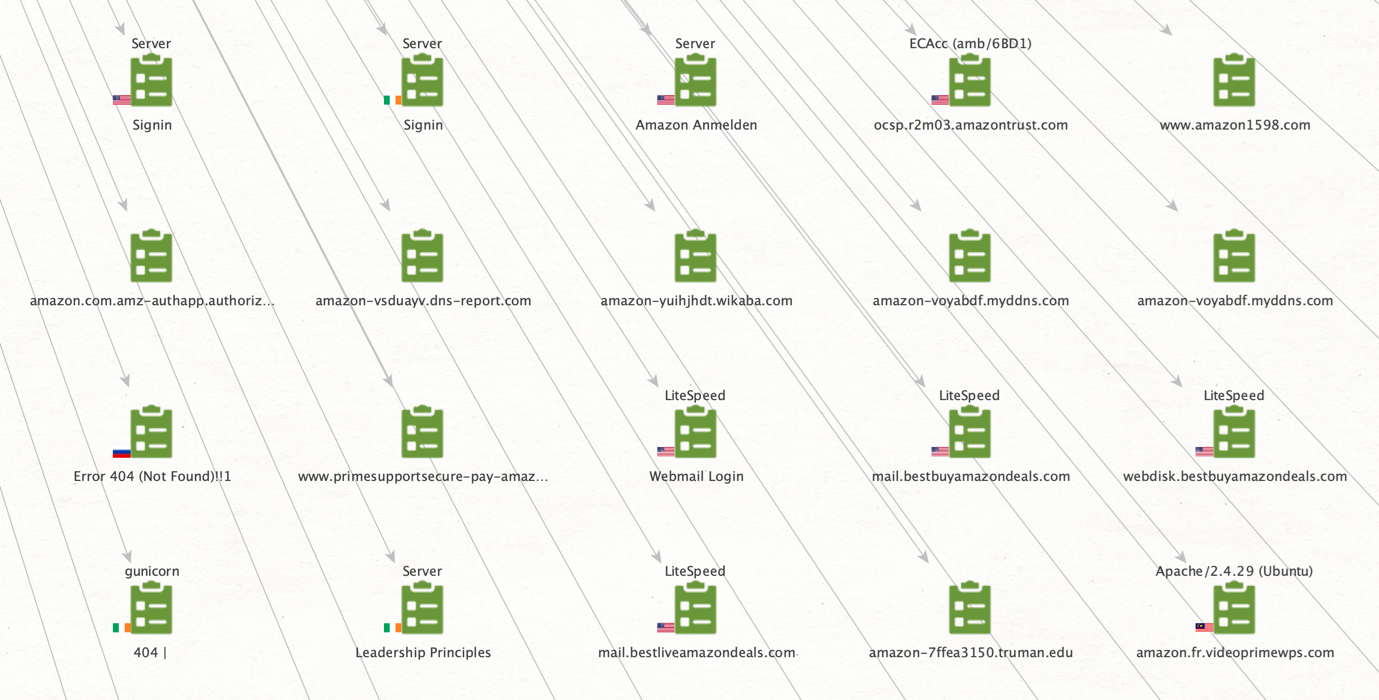
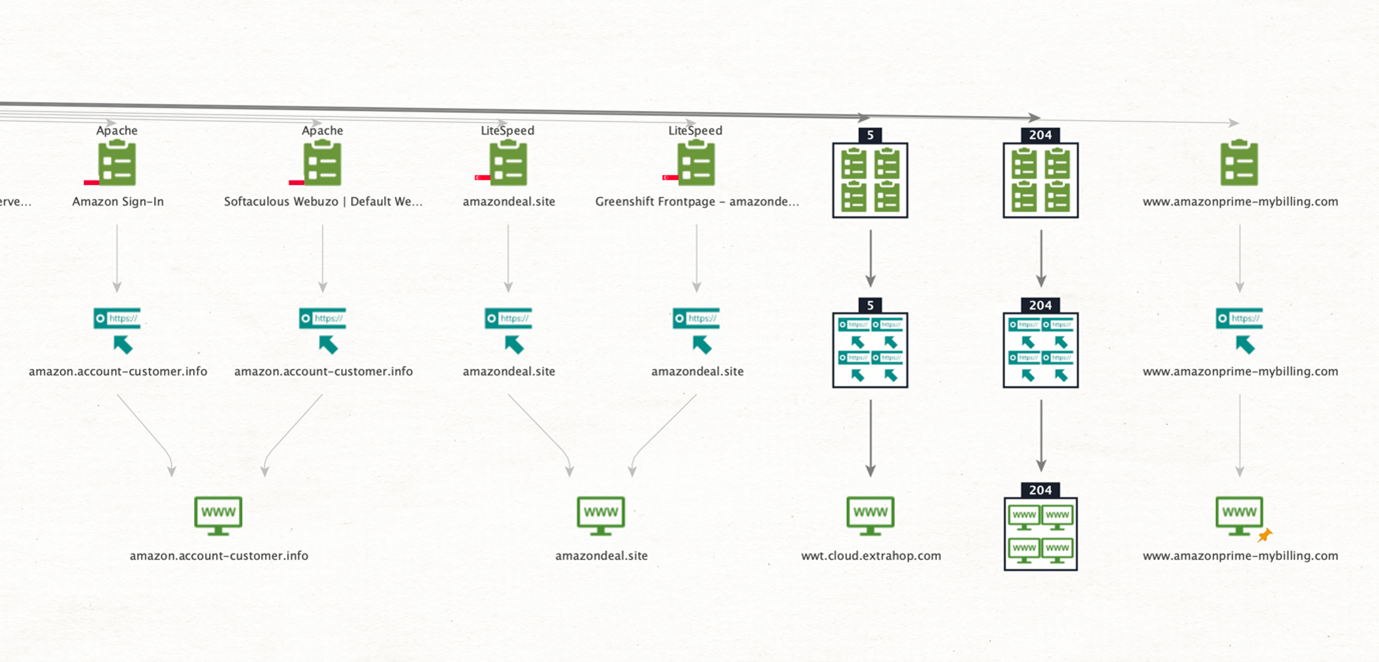
We can immediately observe some legitimate sites between the suspicious URLs. A few of these might be associated with the same website. We can run the To Website [Convert] Transform to group URLs into their main site to find those connections.
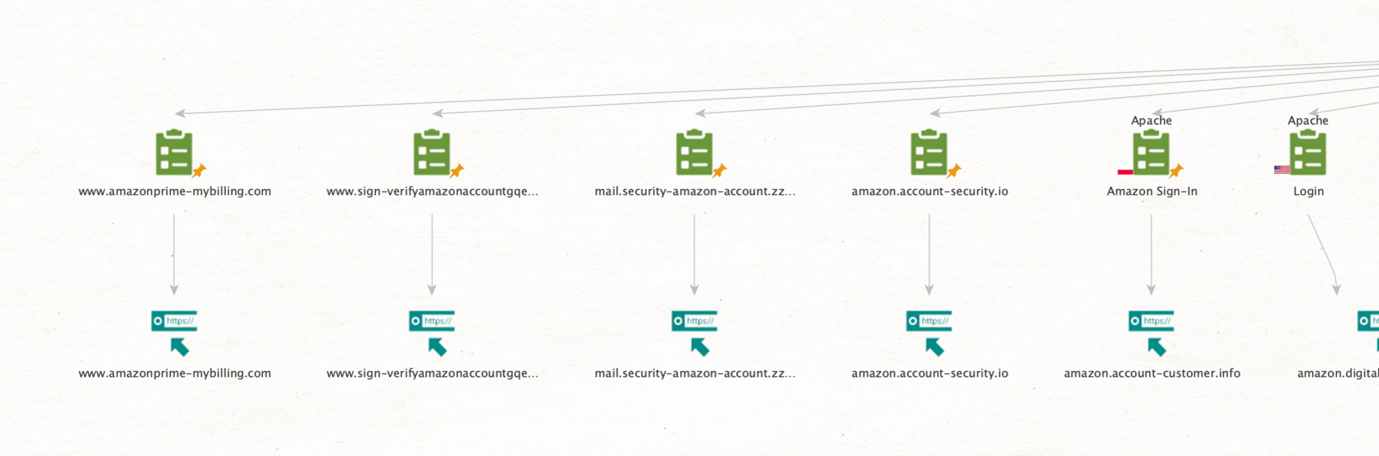
Phishing domains tend to use the name of the legitimate site they are impersonating or use keywords like login, access, billing, and account, so a couple of sites immediately stand out from the results. A quick search for those keywords returned the following results.
Let’s check when these were registered. Phishing domains have a short lifespan, so if any of these were recently registered, that would increase the chances of these being used for malicious purposes.
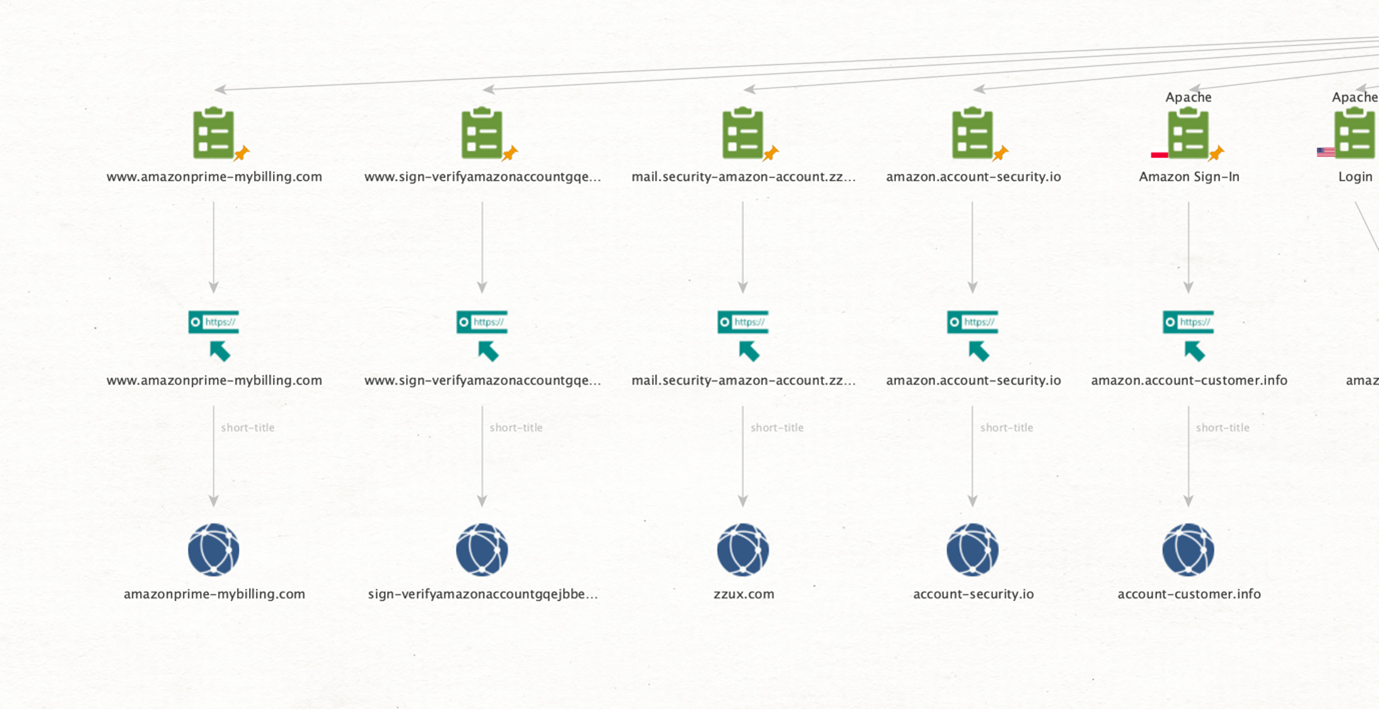
First, we need to extract the domain connected to the URLs. Let’s run the To Domains [within Properties] Transform on the URL Entities.
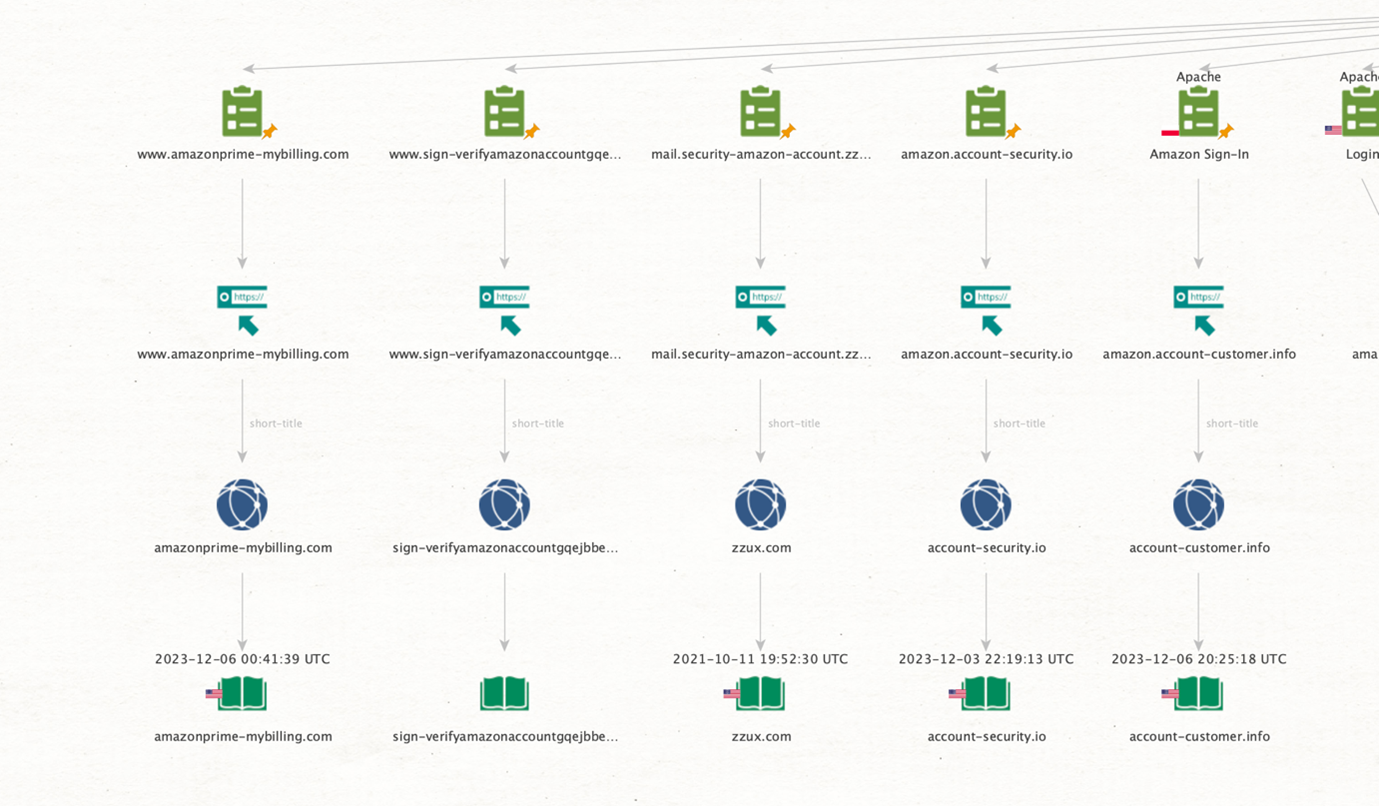
Then, run the To WHOIS Records [WhoisXML] Transform to extract the latest WHOIS records for each domain.
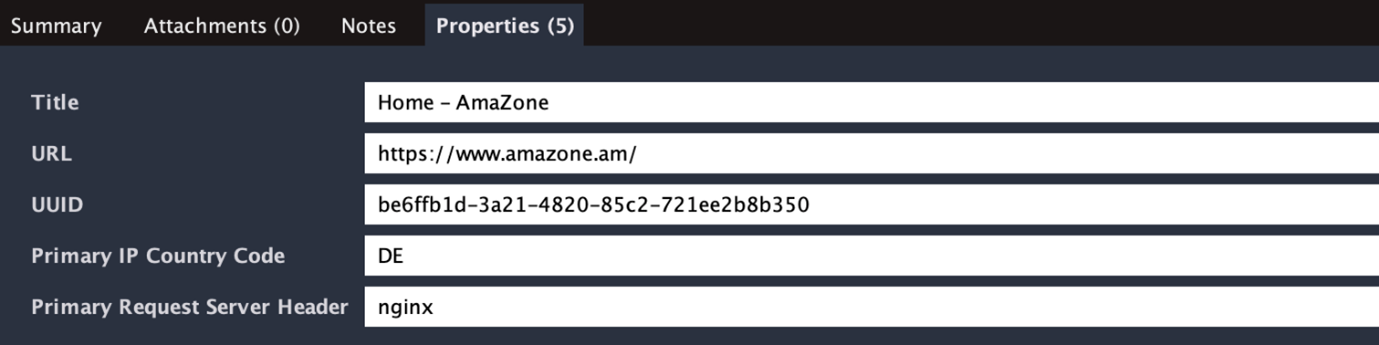
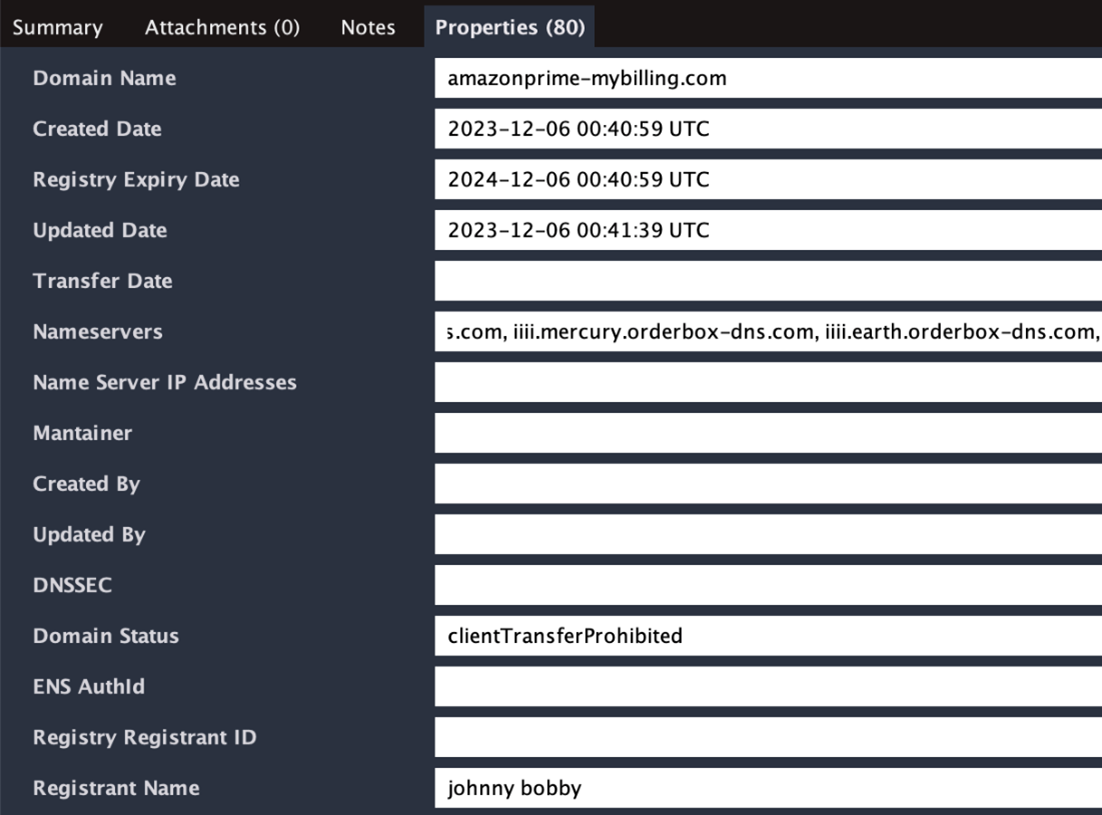
As we suspected, most of these were recently registered. Let’s check the information for one by double-clicking a WHOIS Record Entity.
We can see this one was registered just a few days ago, and I’m pretty sure Jeff would not ask someone named Johnny Bobby to register its domains but use corporate legal names for this. This domain has all the red flags of an actual phishing domain, but I will let you confirm that.
Here’s a guide extracted from the Phishing Attacks Part 2: Investigating Phishing Domains article to help you with the next steps.
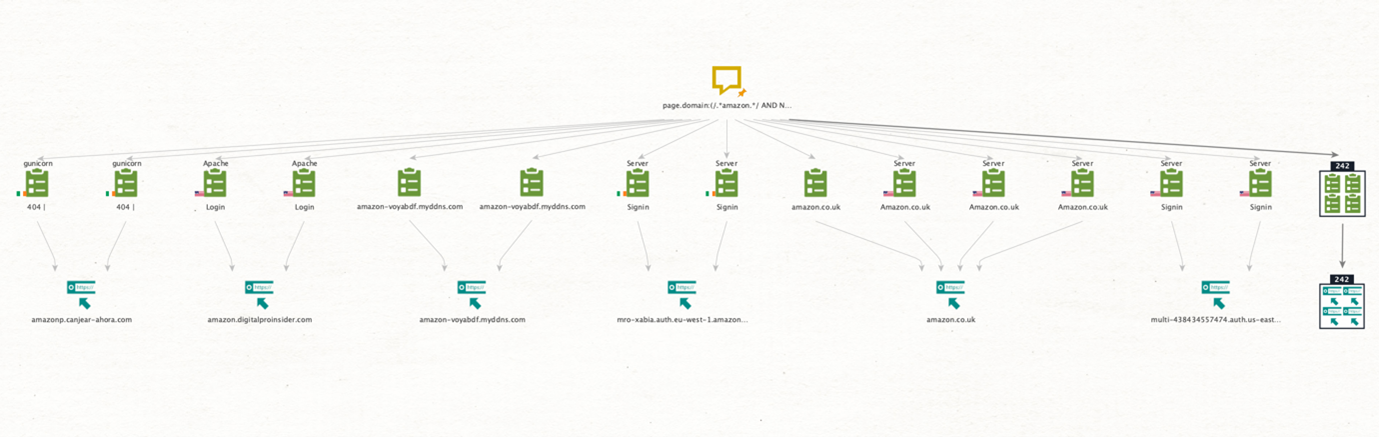
In case you want to deep-dive to find the scope of this threat, historical information can be used. We can continue by using the To Historical WHOIS Records [WhoisXML] Transform to extract the email used to register the investigated domain.
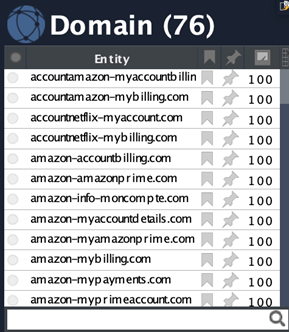
This freshly found email can be now extremely useful to search other domains registered by the same identity through the dtEmail2HistoricDomains Transform available from our partner DomainTools:
It looks like Amazon was not the only target (Netflix, UPS, amongst others) of our “friend” Johnny Bobby. ;)
I hope you found this guide useful, and if you decide to follow along, please share your graphs with us on social media and tag @MaltegoHQ and @MarioRojasChin with the #madewithmaltego and #phishing hashtags.
Conclusion 🔗︎
Phishing attacks typically operate on a large scale, with threat actors launching multiple operations under the guise of legitimate websites to entrap as many individuals as possible. In this context, the urgency to preemptively detect and neutralize phishing domains cannot be overstated. The key to thwarting these threats is identifying phishing domains before attackers exploit them against unsuspecting users.
To actively track down a potential cybersecurity threat and gain insight into its network, tools like Maltego can be instrumental. Maltego enables us to uncover and analyze these fraudulent domains efficiently. By leveraging Maltego’s extensive list of integrations, we can stay ahead of cybercriminals. Remember, in the battle against phishing, proactive defense isn’t just a strategy – it’s our most robust line of defense.
Stay informed and connected with us on Twitter, LinkedIn, and Mastodon, and sign up for our email newsletter, so you never miss any updates and news!
Happy Hunting!
About the Author 🔗︎
Mario Rojas 🔗︎
Mario Rojas is a former Cyber Security and Threat Intelligence Subject Matter Expert at Maltego with more than 14 years of experience in the cybersecurity field. His expertise in open-source intelligence (OSINT) allows him to effectively map and visualize complex relationships and connections between entities, from IP addresses and domain names to social media profiles and Darkweb forums.