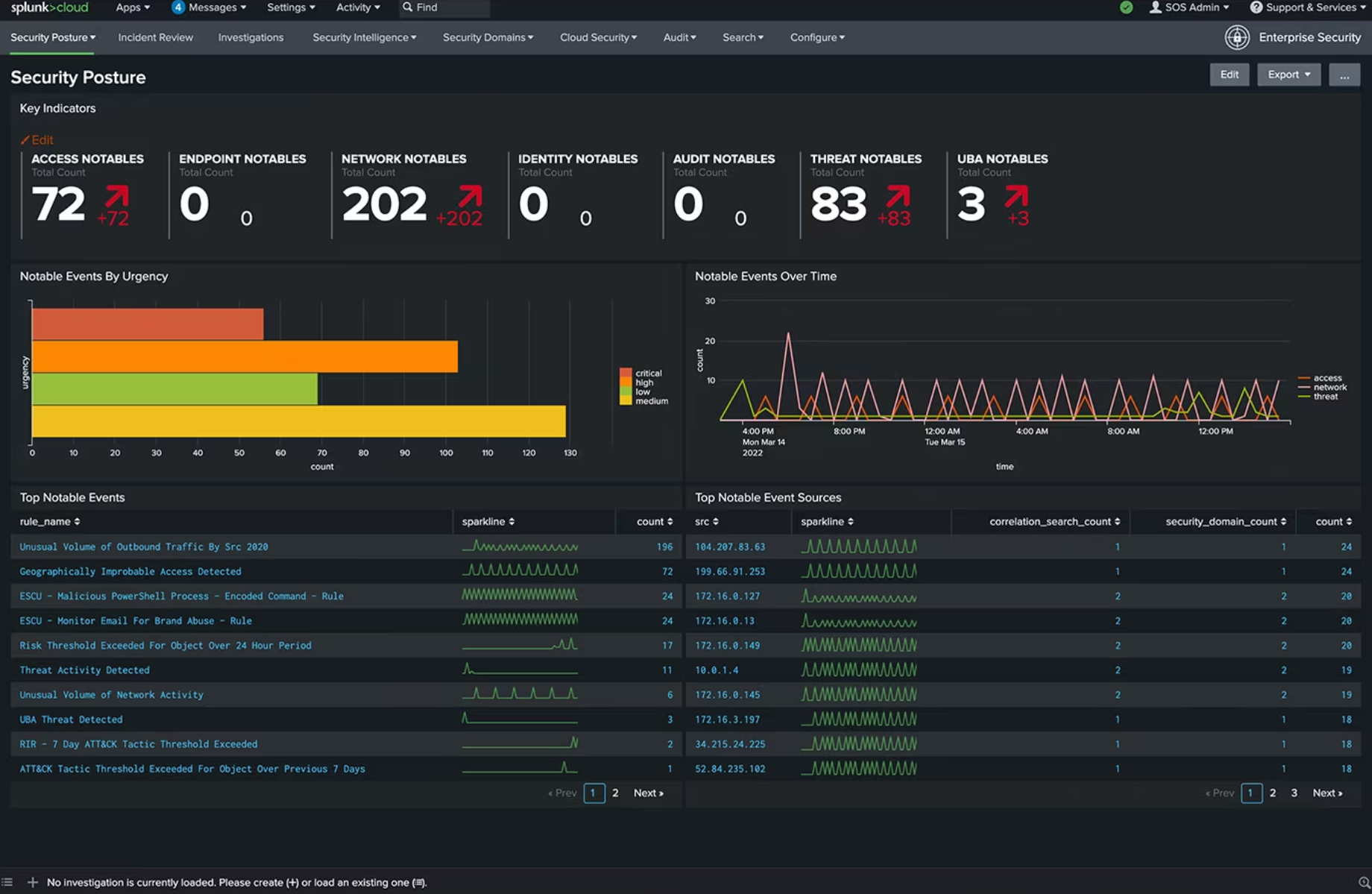
One of the main challenges Security Operations Center (SOC) teams face is the lack of integration between security tools. The burden on SOC teams is further amplified by the overwhelming volume of alerts and data that each device generates daily and the seemingly endless flow of false positives.
Source: Optiv
This article will discuss the leading causes and consequences of the lack of integration between tools and explore potential solutions.
Lack of Integration between Security Tools 🔗︎
The lack of integration between tools increases the time that security analysts spend manually correlating events between tools. This, in turn, increases the time required to confirm whether an alert is a security incident or just another false positive and could even cause the analyst to miss critical security events.
Among the main reasons for the lack of integration is the use of tools that are not designed to work together. Vendors generally use different formats for their data, making it hard to integrate, combine and correlate data from multiple sources.
Consequences of the Lack of Integration 🔗︎
Let’s take some time to discuss the main challenges caused by the lack of integration between security tools.
- Tool Fatigue: occurs when SOC teams have to use and manage multiple disparate tools. Constantly switching between different interfaces, each with its own user experience, data representations, styles, and even query languages, slows down the analysis workflow and makes incident detection and response less efficient.
- Alert Fatigue: caused by exposing security analysts to large numbers of security alerts (many of which may be false positives) and usually results in the analysts becoming desensitized to the alerts due to the overwhelming number of alerts they receive on a single day.
- Data Silos: appear when important security information is confined to one tool and unavailable to others. When security tools are not well-integrated, they cannot effectively share information with one another.
- Time to Confirm a False Positive: We already talked about increased incident response times, but another task requiring fast results for security analysts is in confirming whether an alert is a false positive or not. Switching between multiple tools to verify if an IOC (indicator of compromise) is a false positive wastes time that the analyst could use to focus on actual threats.
- Vendor Lock-in: Organizations may feel stuck with certain vendors when tools don’t integrate well with others, even if their needs evolve or better solutions become available.
The Need for a Unified Interface 🔗︎
The lack of integration between security tools has challenged security teams for many years. This led to the development of Security Information and Event Management (SIEM) platforms, such as Splunk.
Source: Splunk
SIEMs aim to provide a more integrated and holistic view of security by collecting, correlating, and analyzing data from various sources. But, even though they are very powerful and have become a must in SOCs of all sizes, these platforms come with their challenges.
A study by Panther Labs from 2021 highlights some of the main challenges identified by a group of 400 IT security professionals who actively use a SIEM as part of their job.
Below are some of the key findings highlighted by the study.
In my time as a security analyst and threat hunter, I got to experience all of these challenges firsthand on many occasions. Let me share a short story with you.
Real-Life Example 🔗︎
I remember a case where we received an alert from a user about a suspicious email they had received. After a quick check with the network team, we were informed that the email security gateway (ESG) had also flagged the email as suspicious. It turned out that the rule that was supposed to trigger in our SIEM was broken, so an alert for this event was never received.
I started running queries in our SIEM, searching for all the users who received the email and trying to confirm if anyone had clicked on the link mentioned in the email. The process was sluggish, the platform was overwhelmed with data, and the queries took considerable time.
While I was working on that, a peer looked into sources like VirusTotal, AlienVault OTX, and AbuseIPDB for any additional insights into the sender’s IP address, the URL mentioned in the email, the sender, and other relevant information. This back-and-forth between multiple platforms took time and effort.
When the SIEM was done processing, the results revealed that several employees had not only received the email but also clicked on the malicious link. This discovery required another round of investigations using even more tools.
The investigation lasted several hours, a laborious process filled with tool-switching, manual data correlation, slow response times, and the involvement of multiple teams. This incident highlighted the glaring need for a more streamlined and integrated approach.
Solutions to the Lack of Integration between Security Tools 🔗︎
Organizations must adopt an integrated approach to their security infrastructure to overcome the challenges of the lack of integration between tools. This involves ensuring interoperability among tools and adopting solutions that can effectively manage and interpret the data generated by these tools.
SIEMs 🔗︎
SIEMs were the first approach and the go-to by many organizations trying to solve the lack of integration. As we already discussed, there are many strengths and weaknesses associated with these platforms. To help improve SIEMs, these are usually paired with other solutions such as Security Orchestration, Automation, and Response (SOAR) systems.
SOARs 🔗︎
SOARs are very effective at streamlining security procedures by coordinating and automating security tasks between tools and teams, thus reducing some of the repetitive tasks assigned to security teams. However, these platforms require significant time and resources to implement and maintain, representing a major challenge for most organizations.
Maltego 🔗︎
Maltego presents itself as a possible solution for most challenges presented by the lack of integration between tools.
Although Maltego does not intend to replace solutions like a SIEM, its data integrations can significantly reduce the burden on SOC teams in at least three areas:
- Cybersecurity Operations
- Threat Intelligence
- Threat Hunting
Another strength of Maltego is its use of Transforms. These allow analysts to interrogate data without requiring them to learn a new query language and even guide them by providing specific outputs that each piece of information can provide.
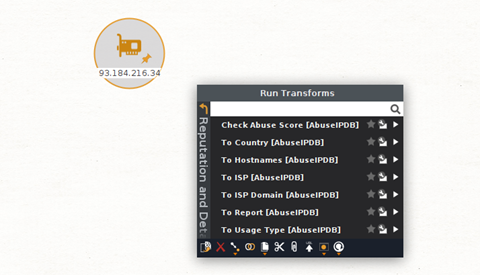
For example, while looking for information on an IP address, an analyst may check AbuseIPDB on Maltego and see the following Transforms:
By simply clicking on one or more Transforms, the analyst could confirm whether the IP is malicious or not, obtain geolocation information, find hosts associated with the IP, which could be C2 (Command and Control) servers, and even get insights into the type of infrastructure related to the IP address (CDN, Hosting, Shared, Dedicated).
These are just a few ways Maltego can help SOC teams with the challenges created by the lack of integration. If you want to learn more, we recommend reading about Maltego Machines, which help you automate workflows by running Transforms in pre-defined orders, and the collaboration feature, which allows you to share and collaborate via live graphs between team members.
Conclusion 🔗︎
The lack of integration between security tools represents a significant challenge for security teams. Tool fatigue, slow responses, missed threats, and alert fatigue are just a few of the problems caused by the lack of integration.
The journey to streamlined cybersecurity operations may be complex, but it is necessary for today’s ever-evolving threat landscape. By leveraging tools like Maltego, SOC teams can simplify and improve their processes, combine disparate data sources into a single interface, and effectively combat the consequences of tool disintegration.
If you found this article useful and would like to see more updates on intelligence gathering or other related topics, you can follow us on Twitter and LinkedIn or subscribe to our newsletter.
Mario Rojas 🔗︎
Mario Rojas is a former Cyber Security and Threat Intelligence Subject Matter Expert at Maltego with more than 14 years of experience in the cybersecurity field. His expertise in open-source intelligence (OSINT) allows him to effectively map and visualize complex relationships and connections between entities, from IP addresses and domain names to social media profiles and Darkweb forums.