Ban evasion has been affecting businesses since the first online platforms and digital products were launched, and it shows no signs of diminishing. In addition to undermining the integrity and enforceability of a platform’s rules and policies, ban evasion contributes to a less secure and less trustworthy environment for users and advertisers alike.
But are all industries equally affected and vulnerable? How can ineffective handling of ban evasion impact your business, and what are effective strategies to combat ban evaders? Finally, how does Maltego help in tackling ban evasion? These are some of the questions we will explore in this article.
Table of Contents 🔗︎
Industries Particularly Affected by Ban Evasion 🔗︎
Ban evasion occurs when individuals or organizations bypass restrictions meant to block them from a platform or service. Banning users and restricting the use of a platform’s services through multiple accounts is often used as a tool by platforms to prevent product abuse. At times, this may involve egregious violations such as spreading illegal content, while at other times, it may be due to violations of policies like signing up for multiple accounts or abusing promotions and coupons.
Ban evasion is a problem across various sectors, but it mostly affects three areas: social media platforms, online sales, and financial services.
Here are typical examples of how ban evasion manifests in these industries:
1. Social Media Platforms
Banned users often create new accounts using alternate login credentials, especially if they were previously banned for reasons like spreading hate speech or misinformation.
They commonly use VPNs or proxy servers to alter their IP addresses and evade detection, enabling them to set up new accounts. There may be situations when platforms ban a range of IP addresses or unique network identifiers when there is known suspicious activity such as bot networks.
Some users may also resort to tweaking their personal information, such as altering their names, dates of birth, or even profile pictures, as a means to slip past detection measures and continue using the platform.
2. Online Sales
Similarly, sellers whose accounts were banned for fraudulent activities or selling counterfeit products often return to the same platforms by creating new user profiles. There are those who go to the extent of managing multiple accounts under various aliases, effectively dodging detection.
They frequently change their contact and payment information and even their physical addresses. Some sellers also employ IP-masking tools and services to further obscure their activities.
There’s also a tendency to engage in feedback manipulation, where sellers create fake buyer accounts to purchase their own products, deceitfully boosting their review scores. This manipulation can easily mislead genuine buyers who often trust these ratings, leading them to believe in a falsely earned reputation on the platform.
3. Financial Services
Within the financial services sector, ban evasion takes on a more complex form. Individuals or companies previously banned for fraudulent activities might attempt to access services again under different business names. This tactic is particularly prevalent among those who are currently under sanctions.
Ban evaders are also known for creating and using shell companies to open new accounts or carry out transactions. Through this practice, they manage to conceal the identities of the actual account holders who have been banned.
Lastly, legitimate accounts are sometimes hijacked through identity theft or social engineering, which are then used to circumvent personal bans. These strategies highlight the extent to which individuals or entire organizations will go to bypass restrictions in the financial sector.
If you have observed instances of ban evasion on your product or platform, you can use your internal data in Maltego to prevent new ban evaders or tackle existing ones. You will find out how to do this in the final section of this article. Click the button below to discover the steps now.
Impact of Ban Evasion on Your Business and Platform 🔗︎
The effects of mishandling ban evasion or failing to act decisively can be broadly categorized into two main areas: platform health and business impact.
Platform Health 🔗︎
- Influx of Inappropriate Content: When ban evaders return, they often bring along content that violates platform guidelines. From mildly offensive to outright illegal material, this content compromises the integrity and safety of the platform.
- Loss of Trust: If harmful activity continues and inappropriate content circulates on the platform, user trust erodes, a value that is difficult to restore.
Business Impact 🔗︎
- Decline in Genuine User Engagement: A drop in activity from genuine users as a result of the unpleasant environment created by the continuous harmful activity and fake or inappropriate content. This decline in engagement can also lead to a decrease in valuable user-generated content.
- Increased Incidence of Fraud: Particularly in online sales and the financial sector, ban evasion may lead to a rise in fraudulent activities and direct financial losses. For example, online sales platforms may suffer from fraudulent transactions, while financial services might face unauthorized access to sensitive financial data.
- Legal and Regulatory Consequences: In the heavily regulated financial sector, failure to effectively manage ban evasion can lead to hefty fines and legal compliance issues. Non-compliance with regulatory standards can tarnish the reputation of the institution and lead to long-term trust issues with clients and regulators.
- Loss of Advertisement Revenue: Advertisers prefer to associate their brand with safe and reputable platforms. If a platform is perceived as poorly managed or unsafe, advertisers may pull out and cause losses in revenue.
Strategies to Fight Ban Evaders 🔗︎
The two most impactful strategies your team can follow to fight ban evaders are:
As part of the sign-up and access process, platforms collect the identity data of users as well as other data such as browser-agent data, IP addresses, device identifiers, and unique cookies. These data points allow platforms to make inferences about ban evaders who change some of these characteristics to bypass registration controls. Even seemingly uninteresting data, such as account creation time, can help make these inferences. For example, analyzing the time elapsed between a ban and the creation of a new account can provide insights.
However, in thousands of lines of records, it is often not straightforward to make connections. In the demo example presented below, we will show how to address this challenge in Maltego, using the different user data points just explained. Through manual investigative work in more advanced and complicated cases, platforms employ user reviews not just on their platform but on the same actor’s behavior across other accounts as well, to identify whether they are ban evaders. In doing this, platforms often use techniques such as social network analysis to identify intersecting connections, reposting the same or similar content, causing coordinated harm, and other. Platforms also focus on looking for violations of the policy for which a user was banned in the first place.User Data Analysis 🔗︎
Manual or Automated Pattern Analysis 🔗︎
Steps in Fighting Ban Evasion with Maltego 🔗︎
To put these strategies into practice, and even automate some parts for better and quicker response, your team can investigate ban evaders in Maltego.
Your first step would be to import internal data directly into Maltego where you will be able to visualize networks and look for connections between ban evaders on your graph.
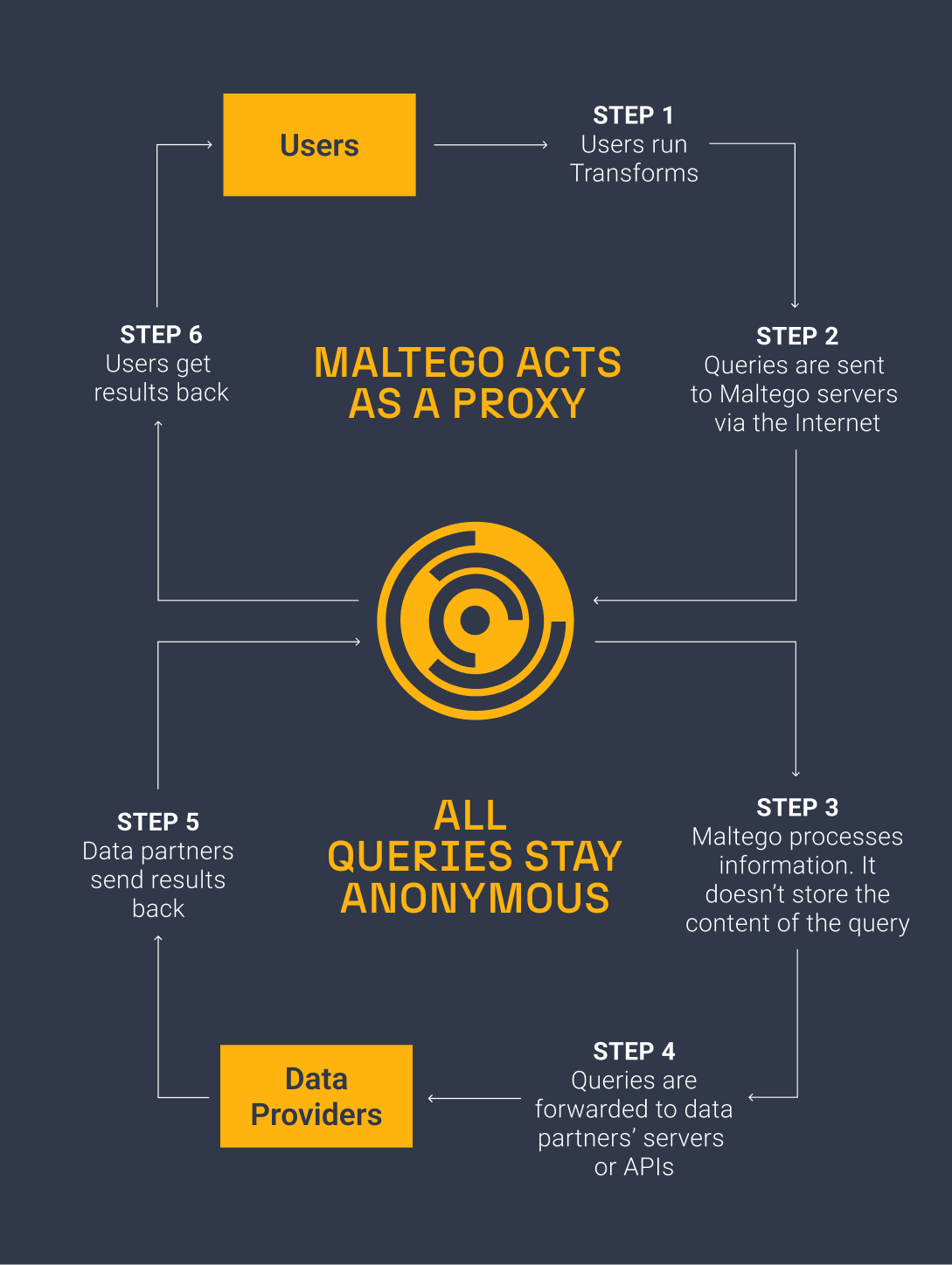
In fighting ban evaders, one of the ways of combatting ban evasion effectively is to figure out the real identity behind the person setting up the accounts or discern a common pattern of behavior. Maltego enables investigators to do so with its access to reputable breach data and dark web investigative capabilities, all done in a safe and anonymous environment.
To understand the steps needed, we will now mimic a potential platform and ban evaders to illustrate a short investigation in Maltego. For the convenience of referencing our example, we will name this fictitious platform ‘XYZ.’ We will use canned data and a set of custom Transforms that you can easily build within the tool to show you how it all looks and gets connected.
To understand the steps needed, we will now fabricate a potential platform and ban evaders to illustrate a short investigation in Maltego.
Maltego in Practice 🔗︎
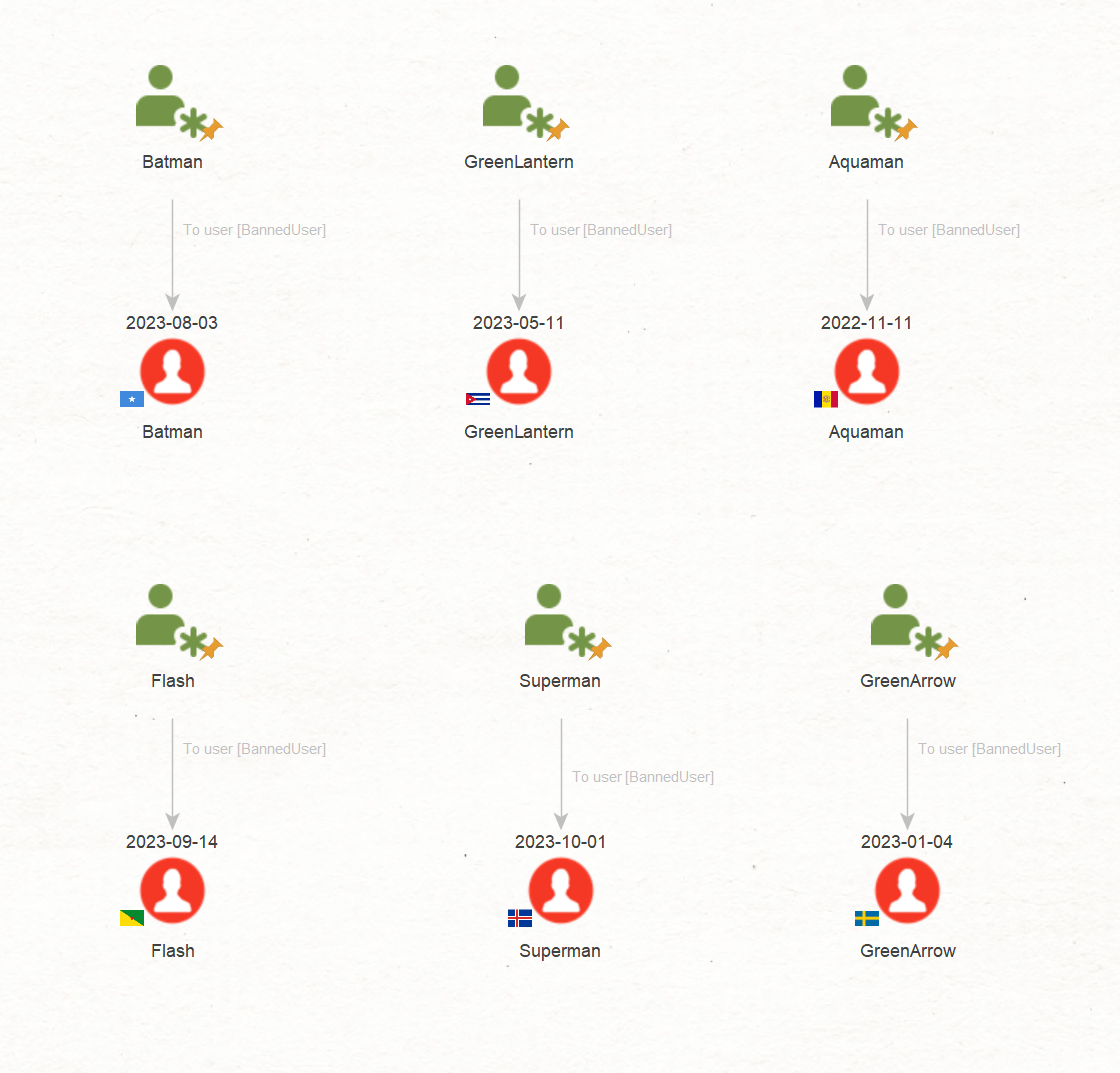
As the first step, we will paste a number of accounts from our internal database. These are accounts that recently signed up to the XYZ platform. Our aim is to investigate them to see whether and how they are connected.
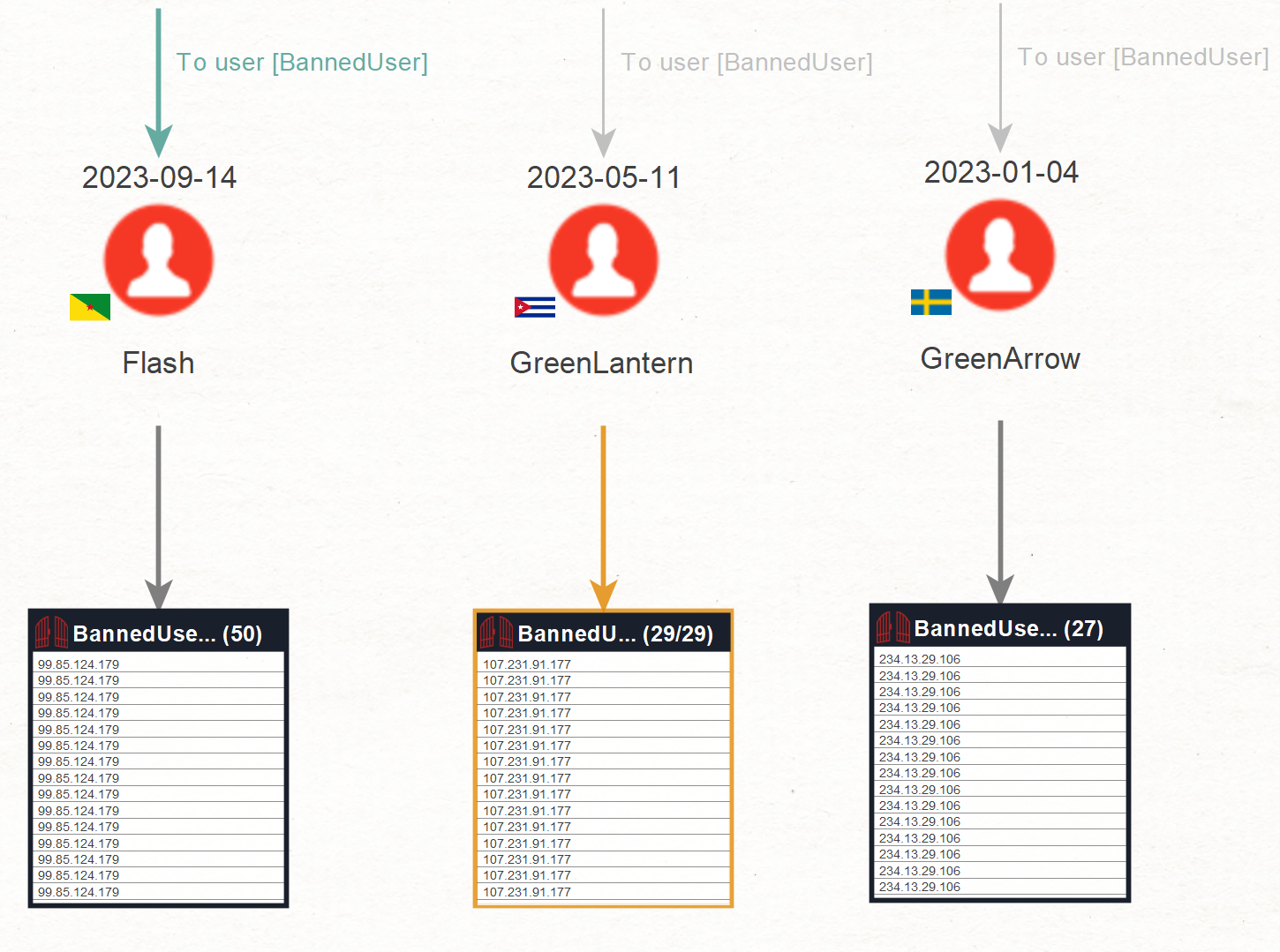
We will run a local Transform To user [BannedUser], specifically designed for this investigation. It will retrieve User Entities on the XYZ platform that come from the previously imported database. This will be the first step towards visualizing static data points in a graph.
What all the User Entities have in common are logins, or in other words, records indicating the details of when they logged in, on what device, using which browser, or even the operating system. This is precisely the kind of data we want to extract.
The custom To login [BannedUser] Transform populated our graph with numerous logins, or in other words, records of every time a user has logged in.
Every application or platform keeps track of this data, and you can take advantage of it in investigations like this one.
Depending on the range of results you have initially set up, your graph will display from a few login data points to hundreds of logins.
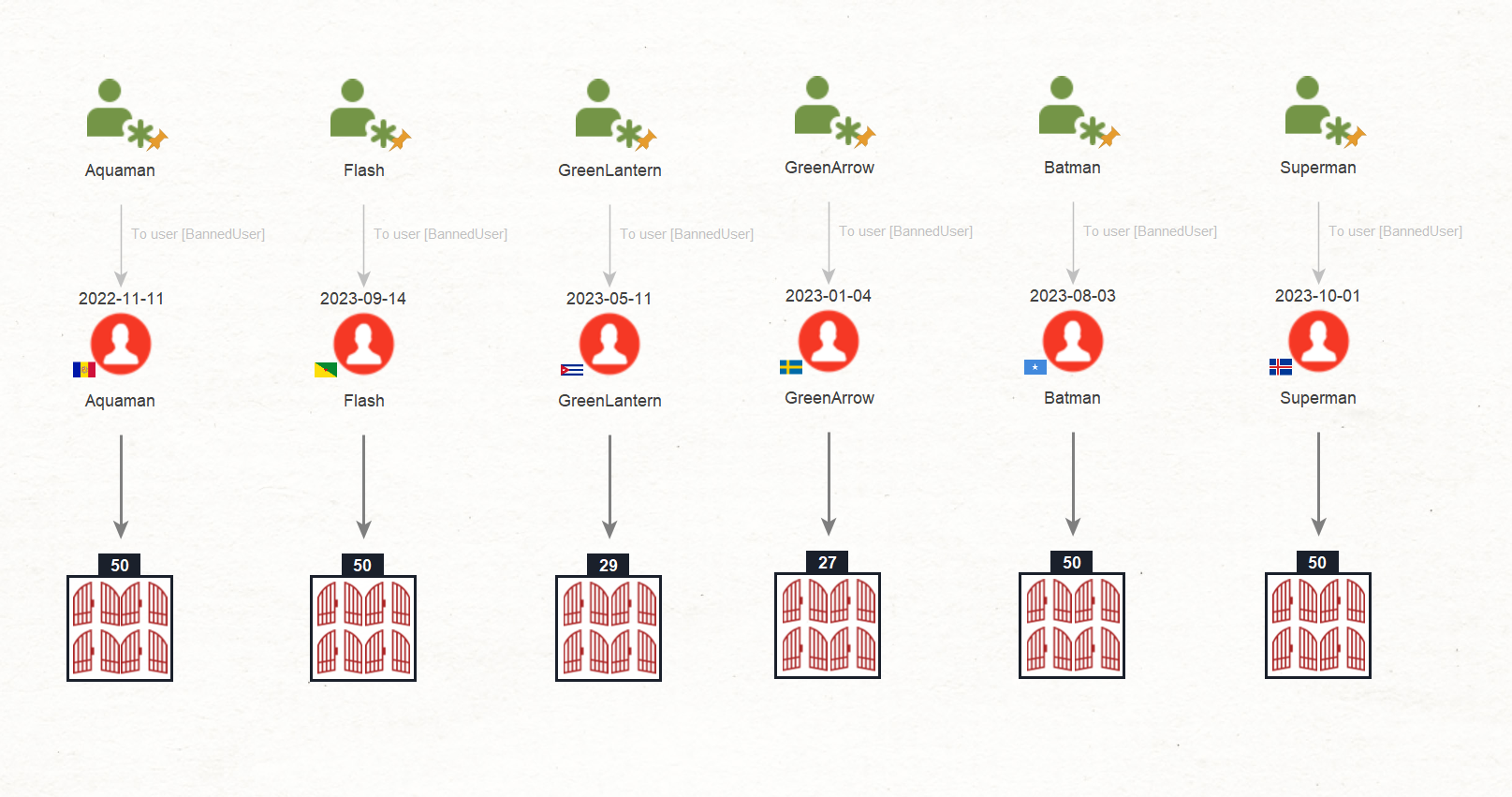
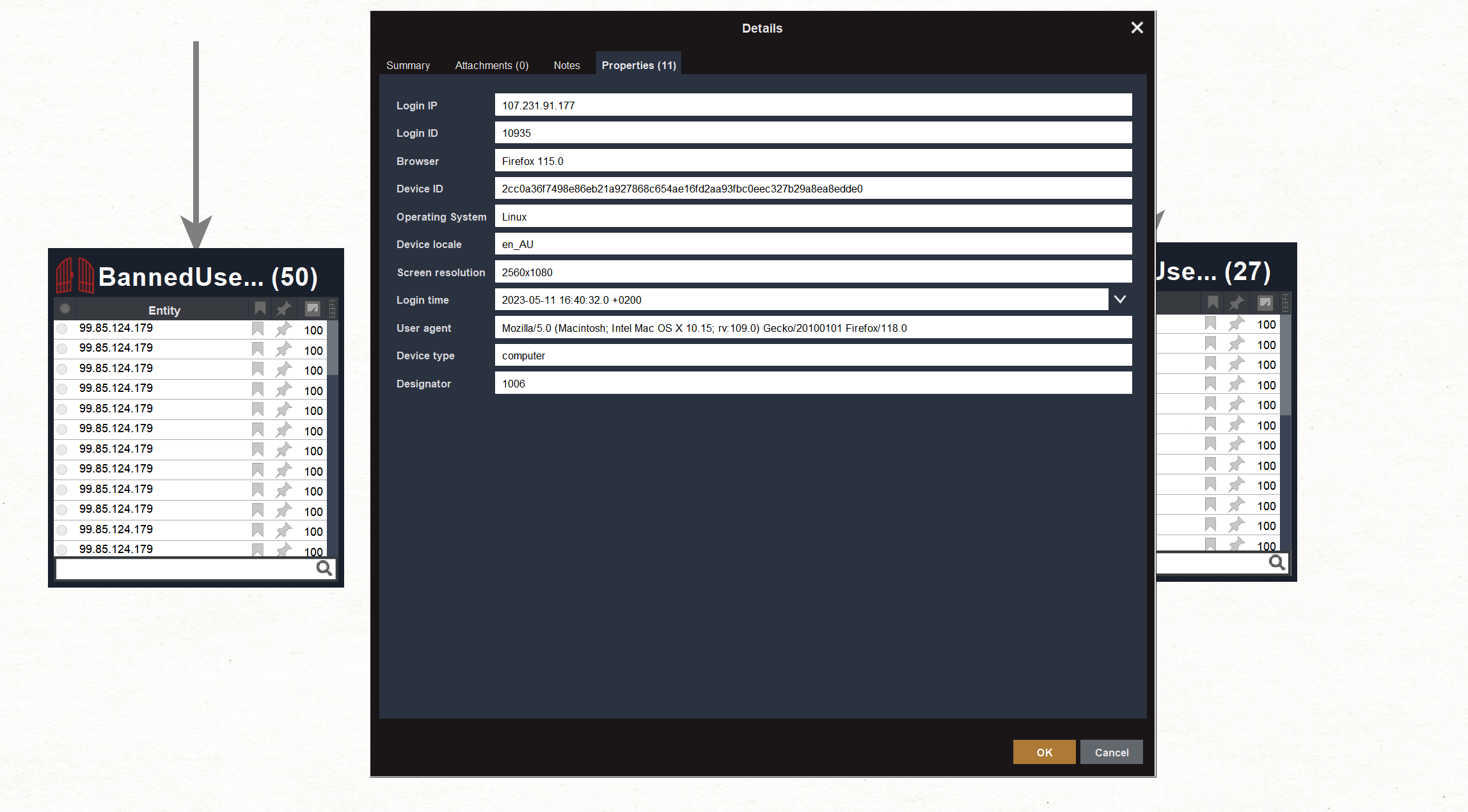
Once you open the Login Entity in your Maltego, you will see, among other things, information about the device language, time of login, device type, login IP, login ID, browser, operating system, and screen resolution – all valuable data points that will help us determine whether these accounts are connected.
INVESTIGATOR TIP: If you find a list of users with the same properties, but who, for example, logged in 2 minutes after they were banned from a different account, this gives you a good reason to assume they’re connected, and you should investigate further. That is an interesting direction to take but also difficult to execute if you can only rely on manual means. However, we do not want to spend hours combing through the data and opening each login, as this would take time and, in the meantime, the ban evaders might be causing more damage. For this reason, Maltego provides the advantage of selecting all the data points and searching through them automatically using dedicated custom Transforms.
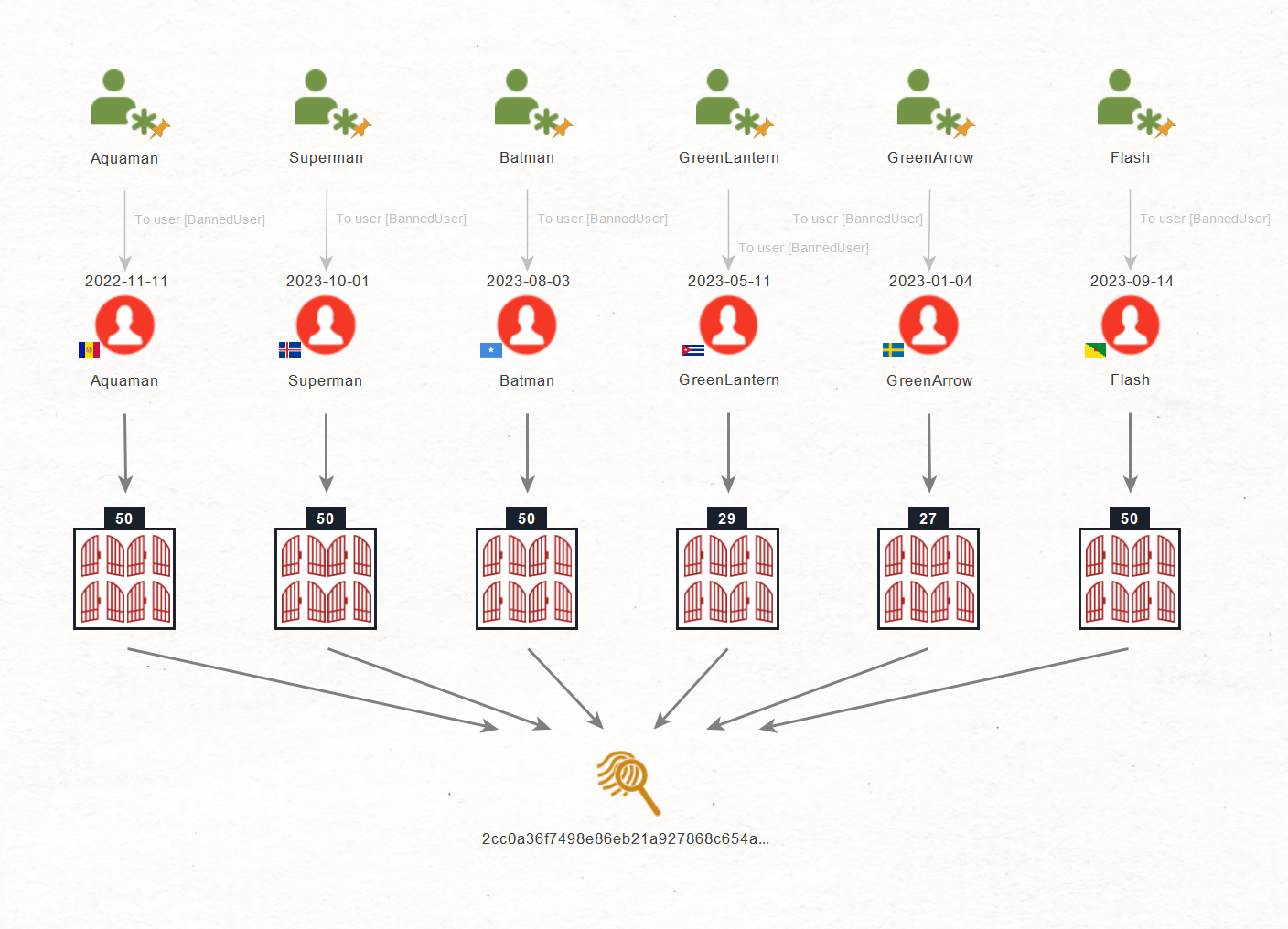
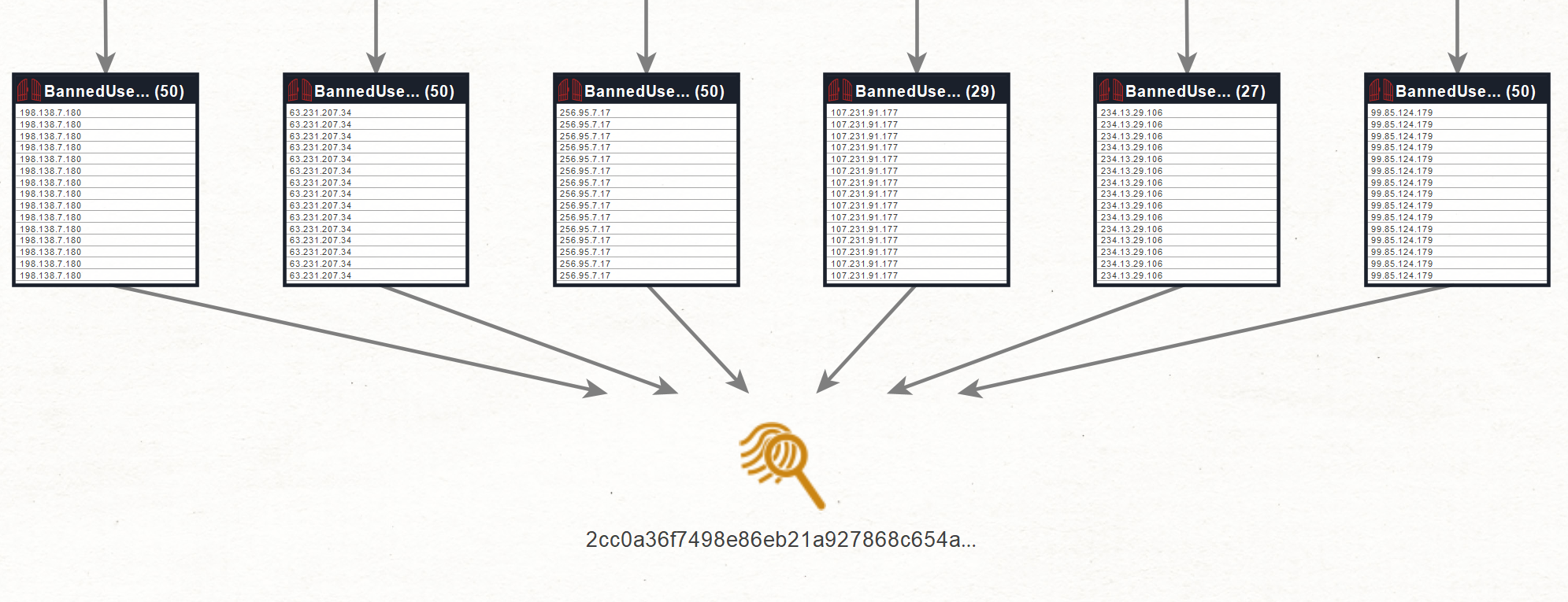
For this investigation, we will run the To Device ID Transform, and see how these different Login Entities are connected.
You can observe that Maltego retrieved a unique hash connected to over 250 Login Entities. This means that all these users connect from the same device, a strong indicator that you are dealing with the same individual.
Maltego Use Cases for Protecting Your Brand and Product Integrity 🔗︎
Fighting ban evasion is just one of the many use cases that Maltego can serve. It’s a pre-built tool used by analysts from teams like Risk Management, Fraud Detection, Digital Security, and Trust and Safety that deal with:
- Brand protection
- Product and platform abuse
- Combating the illegal sale of counterfeit goods
- Preventing fraudulent transactions
- Conducting background checks
As each platform and product is different, the challenges faced by fraud and security teams also vary. However, the core use of Maltego remains the same: accelerating and simplifying investigations through link analysis with easy internal and external data integrations.
Without Maltego, it would take much longer to conduct investigations, and the chances of following the wrong leads would increase drastically. Essentially, Maltego displays only what is relevant. Instead of stifling through mountains of data, the data relationships are painted on the Maltego graph. With the time saved, we can investigate deeper into the assets and currency laundering before the assets actually land in the players’ wallets.
Maksym Gryshchenko 🔗︎
CCP Games Security Team 🔗︎
If you want to discover a real-life story of how one security team used Maltego to suspend over 90,000 malicious user accounts, check out our case study below. You will learn how the CCP Games company deployed Maltego to become the go-to tool they use to detect and identify in-game fraud.
You can download your free copy now:
Download the resource
On our blog, you can also read more about product and platform abuse or check out how to further automate your investigations by using Maltego Machines with our step-by-step guide.
Don’t forget to follow us on Twitter, LinkedIn, and Mastodon, and sign up to our email newsletter, so you don’t miss out on updates and news!
Happy investigating!