Cryptocurrency Fraud and Scams 🔗︎
With the skyrocketing popularity and high adoption of cryptocurrencies, as well as increased interest from the general public, crypto frauds and scams are unfortunately also on the rise today. These illicit activities often entice gullible people on social networks into shady and fraudulent schemes which at the end may cost them a lot of money.
Crypto frauds and scams investigations can be performed from different perspectives. The ultimate goal of online fraudsters is cashing out the stolen funds. In the cryptocurrency world, various exchange services are used for that. This said, the first and foremost problem to investigate is “following the money”: Basically, this means tracing funds until their final destination in an attempt to take a legal action, as licensed crypto exchanges are subject to regulation and compliance with KYC / AML procedures.
Example Cases 🔗︎
Maltego is a powerful tool for link analysis and investigation, and in real life cases, it can be used together with other specific tools (both free and proprietary) which help an investigator in obtaining additional data and building a complete picture.
In this article, we will highlight different methods which can be used for investigating crypto fraud and scam schemes, and following cryptocurrency network activity. We will use only free Maltego Transforms (namely, Blockchain.com Transform set), and also complement the investigation by using some free external tools to get additional data related to investigation.
We will go through the investigation process of a few cases:
- Investigating activity and flow of funds related to two scammer’s Bitcoin addresses
- Visualizing activity of a fraud related address in Ethereum network
Bitcoin Investigation Concepts 🔗︎
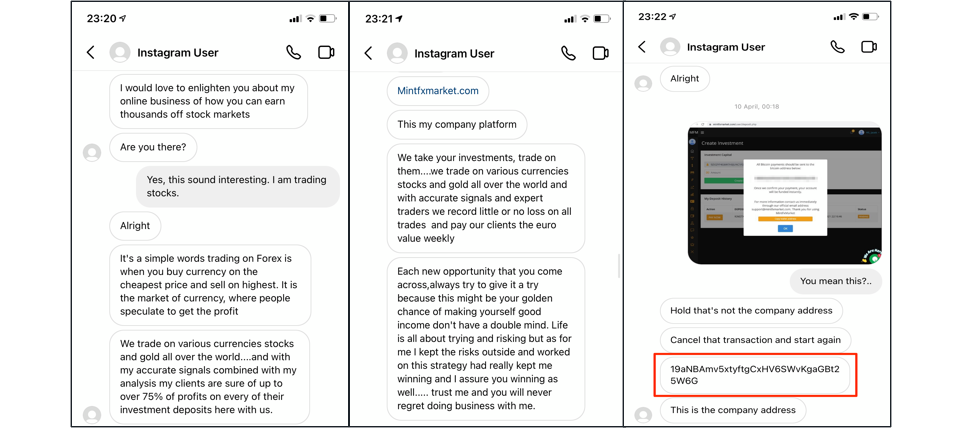
Some of the readers have probably met this kind of scam activity on Instagram and other social networks. A stranger approaches you in the chat and talks you into “investing” in Bitcoin trading or mining, with promises of immediate sky-high returns.
Actual schemes can vary, but at the end they all boil down to talking a victim into sending bitcoins to some Bitcoin address controlled by the attacker. In our case, a scammer uses Instagram chat to encourage victims to register on a website they share, which then requires the victim to send a “deposit” to a specified Bitcoin address. It’s very easy to guess that a victim will never see their money again once they send it.
Below are some screenshots from a chat as it happened on Instagram, where a scammer reveals a Bitcoin address to which a victim is expected to send money:
As the first example, we will investigate this scam address. The actual scam attempt happened in April, so we need to investigate April activity and money flow related to the scammer’s Bitcoin address.
Aims of the Blockchain Investigation 🔗︎
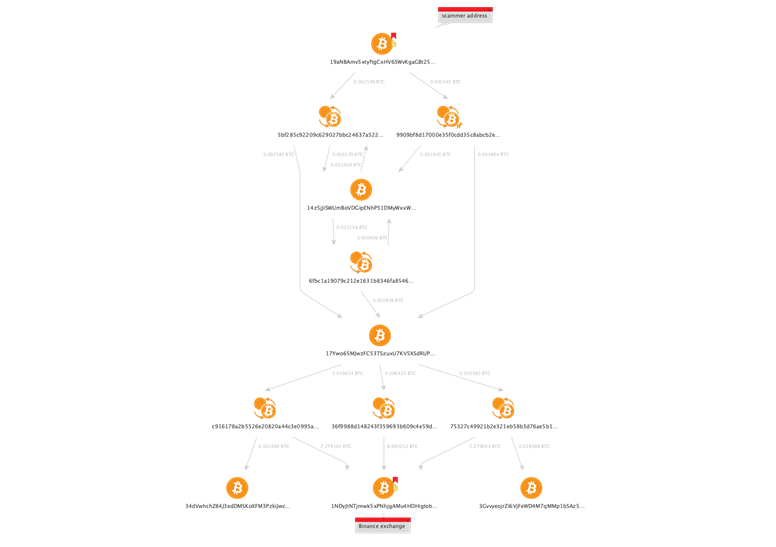
As we already mentioned, the main objective an investigator must keep in mind is to follow the money and understand the relation of the investigated scammer’s address with key entities of interest on the Bitcoin network, like crypto exchanges which are used for cashing out the funds.
Below is an example of one graph we came up with, which shows a logical connection between the investigated wallet and the Binance crypto exchange, which in our case can be a place for cashing out the funds originated from scammer’s address:
In the following chapters, we will follow a step-by-step process to see how this certain graph is built starting from a single Entity, in our case a scammer’s Bitcoin address.
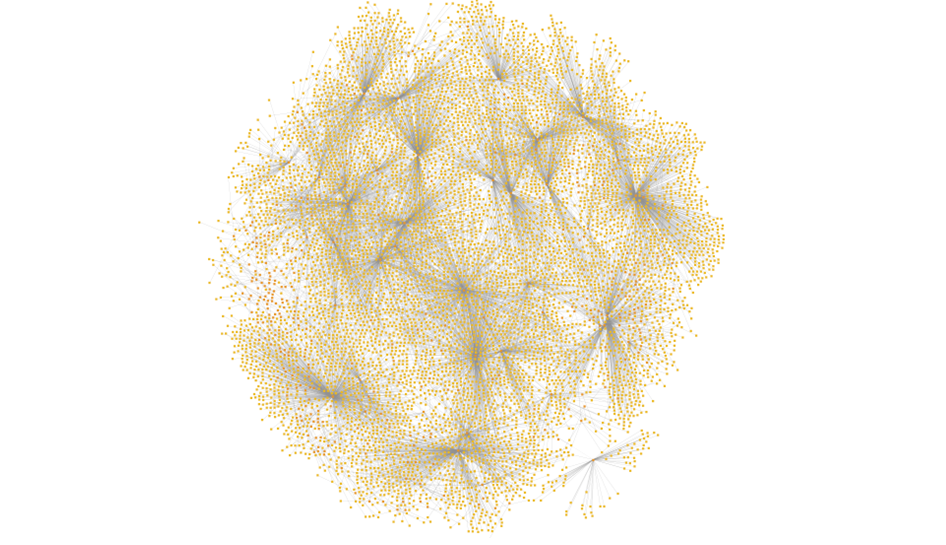
We will also learn how to work with large graphs in Maltego (containing thousands of Entities) representing Bitcoin transactions and narrow down the most interesting and important Entities.
How do you think we will be able to extract valuable information from the following graph with over 8000 Entities?
Transaction-based Network Concept 🔗︎
One must have noticed that Bitcoin transactions presented in the Maltego graph follow the same concept: Bitcoin Address Entities are connected with each other through Transaction Entities.
One may ask, why bother putting on the graph bitcoin transactions and addresses using separate transforms? Cannot we make it simpler and trace the bitcoins movement directly from address to address? Actually, no, and there’s a reason for that.
Remember that the Bitcoin network is transaction-based, and it is essentially a transaction which is recorded into the blockchain. Each transaction may have multiple input and output addresses, so nominally any bitcoin address (unlike for example, a bank account) does not hold any bitcoins: its “balance,” hence the spending ability, is only defined by the sum of all input transactions.
Let’s take a look at a very simple example to illustrate this concept.
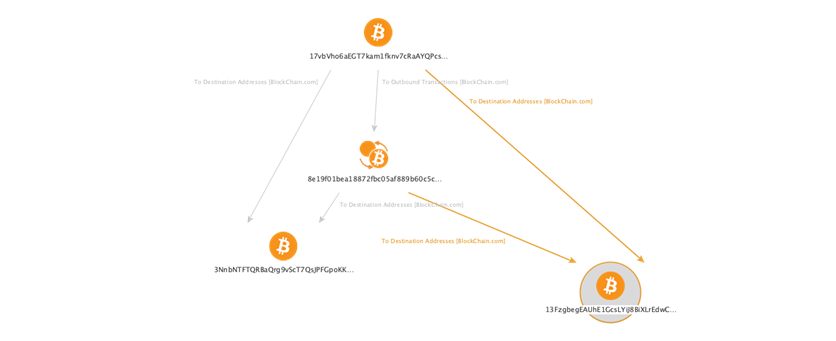
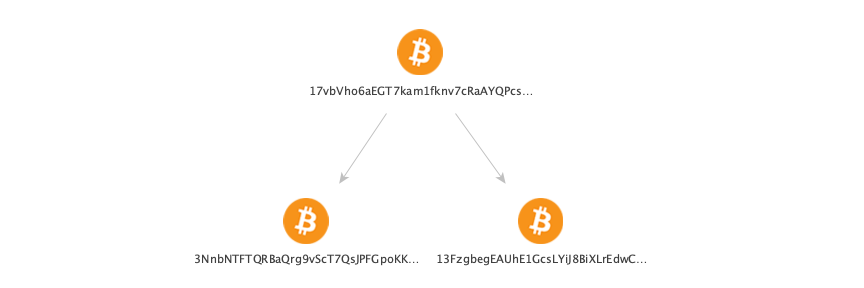
Consider a single bitcoin address to which we apply To Destination Addresses Transform:
This graph shows that address 17vbVho6aEGT7kam1fknv7cRaAYQPcsQFm has sent some funds to addresses 3NnbNTFTQRBaQrg9vScT7QsJPFGpoKKMXG and 13FzgbegEAUhE1GcsLYiJ8BiXLrEdwCshV, but we don’t know the exact amounts sent, and we also don’t know if they were sent at the same or different times.
Now let’s actually see how we can add transaction entities to this graph.
On first step we run the To Outbound Transactions [BlockChain.com] Transform for 17vb… address and get one Transaction Entity, which is 8e19f01bea18872fbc05af889b60c5c91ecd2f2c7264f803b16bb28c650a4775:
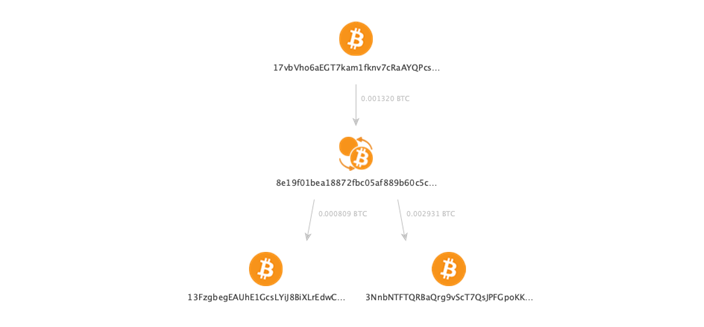
On the next step we run the To Destination Addresses [BlockChain.com] Transform on this transaction:
Voila! Now we have a transaction on the graph which is connected to the same destination addresses, but we also see the amounts (shown as links labels) and understand that bitcoins were moved in the course of a single transaction with one input 17vb… and two outputs 3Nnb… and 13Fz….
Tip: We can switch the links labels from custom format which shows transaction amount (uncheck Show Custom Link Labels) to transform names (check Show Transform Link Labels) in View menu:
Using this tip, the logic of using blockchain Transforms in a proper way (Address → Transaction → Address) is illustrated even more clearly by the corresponding labels:
In order not to overload the picture with redundant information, in real life cases we actually don’t need to use any links “Address → Address” on the graph. This said, the final correct graph view would be this:
So far, for all following graphs we will follow the same principle of tracing flow of funds: Address → Transaction → Address.
More on Building Graphs of Bitcoin Transactions and Visualizing Ethereum Activities 🔗︎
Download the complete whitepaper now to learn more about how to conduct follow-the-money investigations on the Bitcoin and Ethereum blockchains. In this whitepaper, you will learn:
Bitcoin Investigations 🔗︎
- How to trace and build comprehensive graphs of Bitcoin transactions
- The step-by-step process of finding important Bitcoin addresses
- Case Study: Analyzing large Bitcoin graphs
Ethereum Investigations 🔗︎
- How to visualize activities on the Ethereum network
- Working with and importing external data sources into Maltego
- Case Study: Analyzing large Ethereum graphs
Besides Blockchain.com, Maltego also integrates with cryptocurrency intelligence data sources like CipherTrace and Tatum. Both CipherTrace and Tatum allows investigators to expand their cryptocurrency analysis to blockchain infrastructures other than Bitcoin, such as Ethereum, Bitcoin Cash, Litecoin, and more. Check out CipherTrace and our flexible data subscriptions, or try out Tatum for free!Other Useful Cryptocurrency Integrations in Maltego 🔗︎
Download the resource
Don’t forget to follow us on Twitter and LinkedIn or subscribe to our email newsletter to stay tuned to more updates, tutorials, and use cases.
Happy investigating!
About Vladimir Mikhnovich 🔗︎
Vladimir is an expert and consultant in data science, fraud detection, blockchain investigations and open source intelligence (OSINT). His current research interest is in the field of online scam prevention and awareness, which includes both technical and social aspects of modern con artistry involving cryptocurrencies. He runs a consulting company and is also involved in public speaking, writing articles and educating on the subject matters.
To learn more about Vladimir’s work, visit his LinkedIn profile.




![Run To Outbound Transactions [BlockChain.com] Transform in Maltego](/images/uploads/cryptocurrency-investigation_005.png)
![Run To Destination Addresses [BlockChain.com] Transform in Maltego](/images/uploads/cryptocurrency-investigation_006.png)