In our last article, we detailed the features and functionalities of the new VirusTotal Hub items.
In this article, we will walk you through a scenario where analysts take advantage of the VirusTotal Transforms in Maltego to speed up incident response once a SIEM alert has been triggered.
How Maltego Helps Accelerate Incident Response 🔗︎
Incident response is the process designed to manage, contain, and—when possible—reduce the consequences of a cyberattack in a fast-paced and efficient manner. In combination with VirusTotal’s data, Maltego can help incident response teams carry out rapid analyses of digital artifacts that have triggered such a response protocol.
With Maltego, analysts will not need to spend valuable time switching between VirusTotal and Maltego, or writing a report detailing their findings for other teams and decision makers to act upon. Instead, they can carry out their analysis with VirusTotal data on Maltego and present their results directly on the graph, which will help them reduce time during the triage and analysis phase.
We will walk you through such a scenario using a malware hash as an entry point into our Maltego investigation. Notice that to be able to carry out this type of analysis, both the public and the premium API Transform Hub items, as well as the Maltego Standard Transforms Hub item need to be installed.
Investigating Malware Hashes with Maltego and VirusTotal 🔗︎
Finding VirusTotal Files of Target Hashes in Maltego 🔗︎
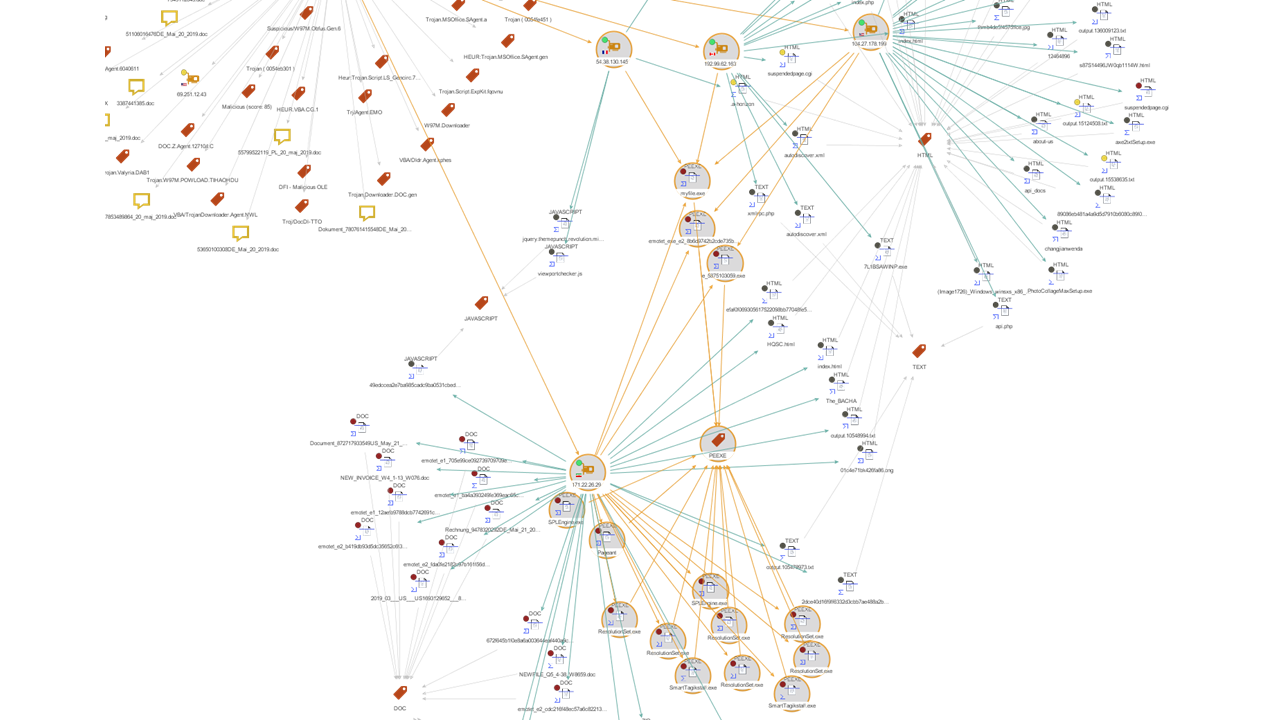
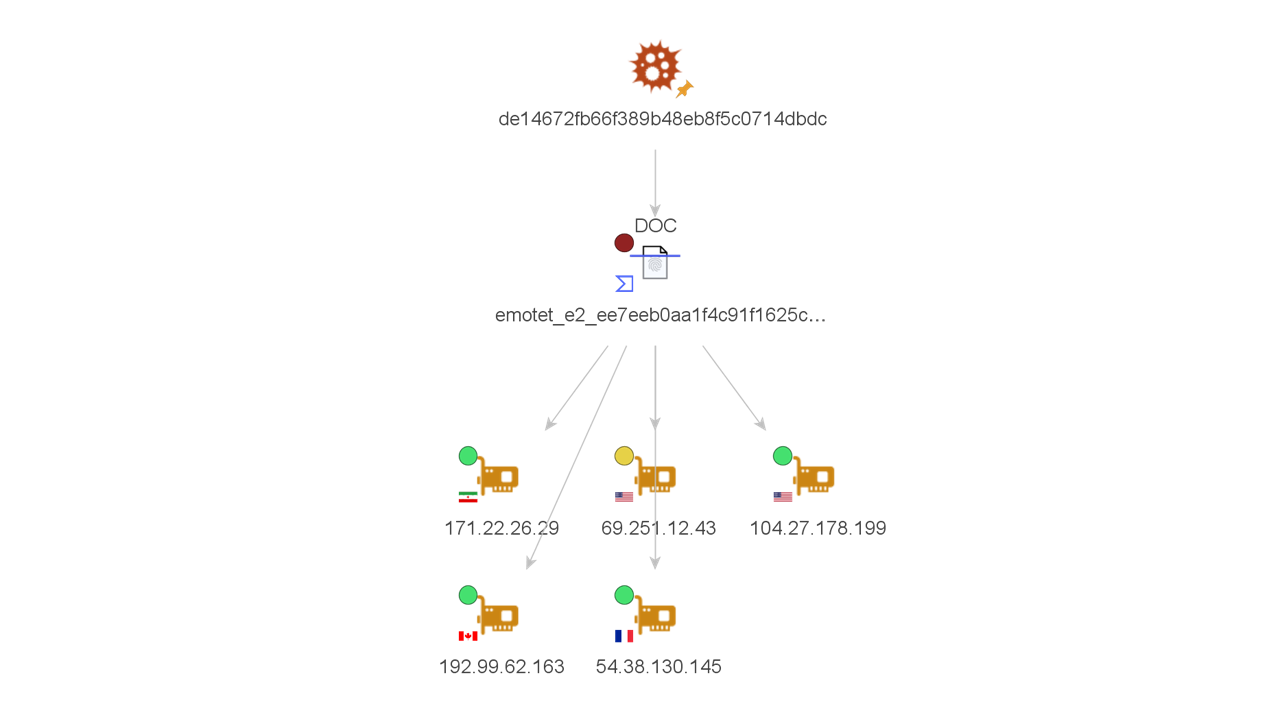
As we just mentioned, let us imagine that our SIEM (Security Information & Event Management) has just triggered an alert containing a suspicious file hash. We picked and dragged a Hash Entity into our graph and ran the To VirusTotal File [VirusTotal Public API] Transform, which returned a VirusTotal File Entity (subclass of a hash) with a MS Word Document that appears to be related to emotet.
Finding IP Addresses Related to the VirusTotal File 🔗︎
Next, we look for IP addresses and domains that might be embedded in the file or that have communicated with it by running the To Contacted IP Addresses [VirusTotal Public API], and the To Embedded IP Addresses [Virus Total Premium API] Transforms.
The resulting IP addresses may be provided to those responsible for the firewall in order to analyze the traffic originating to and from there. They may also ultimately be handed over to those in charge of updating SIEM and other detection tools policies.
In this scenario, VirusTotal did not return any IP addresses for the To Embedded IP Addresses [VirusTotal Premium API] Transform. However, we can see there were 5 different ip addresses that the file appeared to have attempted to communicate with during execution. Notice again the overlay indicating the VirusTotal score for each IP as well as the country flag pointing to their locations.
Finding Related Filenames 🔗︎
We will now move on to looking for related filenames. To do so, we select the VirusTotal File Entity and run the To Filenames [VirusTotal Public API] Transform.
The Transform returned a total of 28 Entities, which can be used to search on the same and/or different machines for related malware files that may have been modified to generate a new malware hash.
At this point, we would also want to compare the filenames obtained with those provided by the system— SIEM or otherwise—that triggered the alarm. The results from this comparative analysis can potentially help update the system’s policies and rules accordingly.
Additionally, we could also run the To Hash [VirusTotal Public API] Transform, which will return other known hashes (e.g. vhash, md5, sha1, sha256, ssdeep and aunthentihash) for the sample, which are also valuable cyber threat intelligence and can be submitted to the SOC (Security Operations Center) team.
Finding Relevant Dates to Cross-Reference with SIEM Alerts
As a next step, it would be important to study the dates linked to the VirusTotal file in order to compare them to those in the file detected by our system and see if it fits the range. To do so, we will make use of one of the Transforms included in the Maltego Standard Transforms Hub item called To DateTime [within Properties].
The Transform returns three different dates:
- First submission date (2019-May-20 9:35:55.0)
- Last submission date (2019-May-20 14:7:49.0)
- Last analysis date (2020-Nov-19 1:44:7.0)
The dates can help the incident response team understand the life cycle of the malware and find out if the organization has been hit by a brand-new campaign or late phase of an existing one.
Find Relevant VirusTotal Analysis on the Files 🔗︎
One more interesting piece of information that could be useful to the investigation would be the results of the analysis done on the file by VirusTotal. We can retrieve said information by running the To Analysis Results [VirusTotal Premium API] Transform on the file Entity.
The results of the analysis will help verify the type of malware we are dealing with. We may also be able to use the information in search for attribution. For example, the rootkits, scripts, and downloaders will be helpful in correlating the threat actors using this specific malware.
Search for Other Files Communicating with Known IP Addresses 🔗︎
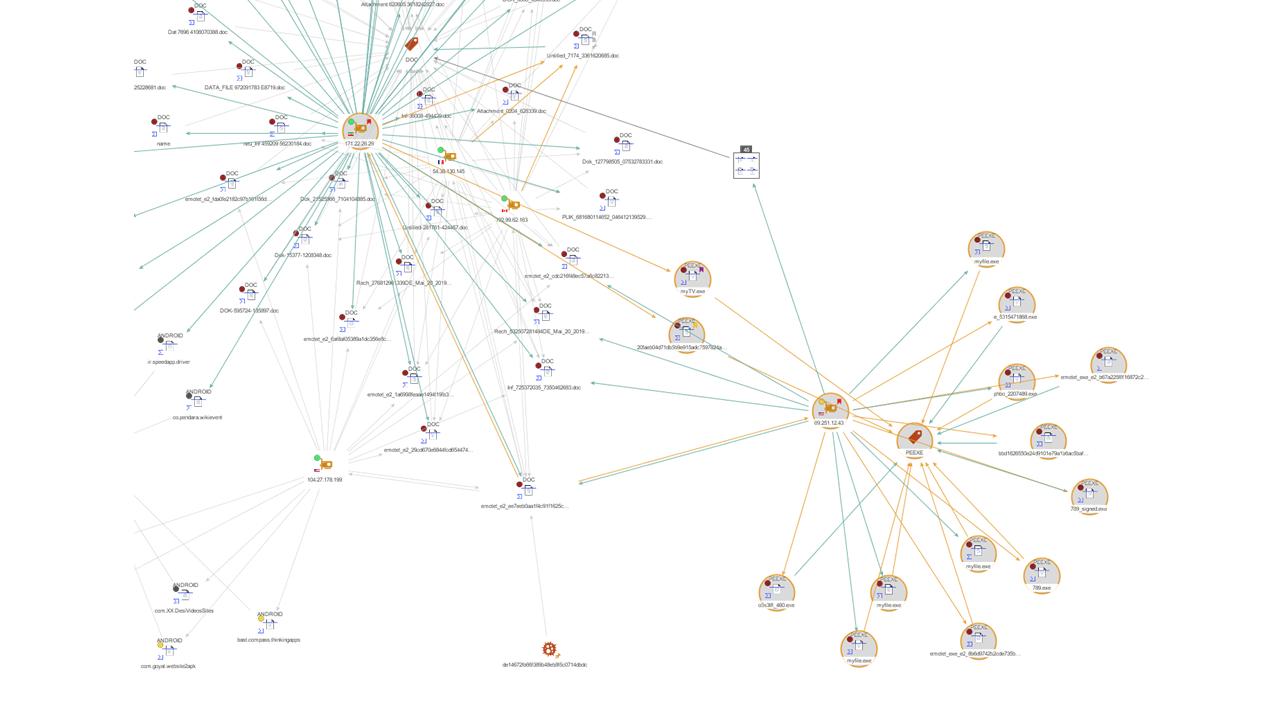
Now that we have collected all the information related to our sample, we can search for outward relationships by selecting the IP addresses and running the To Communicating Files [VirusTotal Public API] Transform, to help us find files which have been observed communicating to the IP addresses.
The output of the Transform has added the files which communicated with the five IP addresses, and we will focus on them now. For this investigation, we will look at the files with which the IP addresses communicated with, and group them according to their type in search for executables.
Instead of looking at one file at the time, we will select the IP addresses by type, use the Add Children feature from the Investigate tab to select the File Entities, and run the To File Type [VirusTotal Public API].
By changing our layout to Organic mode and changing our view to Ball Size by Rank, we are able to easily visualize the three file types we are dealing with:
- DOC (document)
- PEEXE (executables)
- ANDROID
Since we are focusing on executables, we will go back to our graph view, select the PEEXE Entity, and then click on the Add Parents button on the Investigate tab to see which of the IP addresses are connected to this type of files.
Identifying Which IP Addresses are Serving Malware 🔗︎
We can now see that only two of the five IP addresses are known to interact with malicious executables. This is a good indication, but if we want to be one hundred percent certain that any of the IP addresses are serving malware, we will need to run the To Downloaded Files [VirusTotal Premium API] Transform on them and repeat the previous two steps.
The resulting graph shows downloaded files for four of the five IP addresses, and that all of them have served the malicious executable PEEXE file type. This example shows how, combined with VirusTotal, Maltego can help investigators improve and fulfill their organization’s cyber resilience strategy.
This is, however, not all. Malware investigations with VirusTotal can be further enhanced with the use of other Maltego Hub items.
For example, Shodan may be used to analyze the IP addresses and servers, confirm whether they are still online, and identify which services they are serving without exposing our source IP address. It would also be helpful to match indicators from various sources such as Crowdstrike, RiskIQ, or ATT&CK-MISP to not only create redundancies that will support our analysis, but to enrich it with data that might not have been detected by VirusTotal.
Integrate Maltego with Your SIEM System and Enhance your Investigations Even More! 🔗︎
We have already shown you a sample of how the combined use of Maltego and VirusTotal can help you carry out your incident response process. Now imagine how much faster it would be by integrating your SIEM system with Maltego to be able to pull the data contained in your alerts directly into Maltego, instead of having to copy-paste and switch back and forth between platforms.
To learn more about integrating SIEM systems such as Splunk in to Maltego, please check out our integration brief. If you would like to integrate other SIEM systems, please get in touch with our Integration Specialists.
Don’t forget to follow us on Twitter and LinkedIn and subscribe to our email newsletter to always stay updated with new tutorials, use cases, and updates.
Happy investigating!



![To VirusTotal File [VirusTotal Public API]](/images/uploads/virustotal-use-case-001.png)
![To Filenames [VirusTotal Public API]](/images/uploads/virustotal-use-case-003.png)
![To DateTime [within Properties]](/images/uploads/virustotal-use-case-004.png)
![To Analysis Results [VirusTotal Premium API]](/images/uploads/virustotal-use-case-005.png)
![To Communicating Files [VirusTotal Public API]](/images/uploads/virustotal-use-case-006.png)
![To File Type [VirusTotal Public API]](/images/uploads/virustotal-use-case-007.png)