We are thrilled to announce our latest integration to the Maltego Transform Hub: The Splunk Enterprise Security Transforms! If you’re interested in integrating your Splunk data to Maltego, please reach out to Maltego using the contact form on our Splunk integration detail page.
If you work as a Cyber Security or Threat Analyst, chances are you are using Splunk ES as your day-to-day tool to oversee all the activity on your organization’s networks, endpoints, servers, applications, security solutions, databases and more, to find potential security threats and stop them as soon as possible.
What is Splunk? 🔗︎
Splunk ES was developed to help make sense of machine-generated log data, and has become a popular choice among Security Information and Event Management (SIEM) solutions for many organizations worldwide. It is primarily used for searching, monitoring, and examining Big Data through a web-style interface.
It has also become a popular tool used for business, web analytics, security, and compliance as it simplifies the task of searching for specific data that has been buried in massive amounts of more complex data.
What type of events can I query from Splunk? 🔗︎
Our Transforms take full advantage of the Splunk Common Information Model (CIM), which contains data models, documentation, and tools that support the consistent, normalized treatment of data. Below are the CIM data models that you can query using our Transforms.
Let’s check how the Splunk Enterprise Security Transforms can query the Authentication data model, thus allowing you to retrieve information from authentication sources such as Active Directory (AD) directly on Maltego.
With this new set of Transforms, you have multiple options to query the Authentication data model. We will start with an Alias Entity to represent an account, namely, LKhamal.
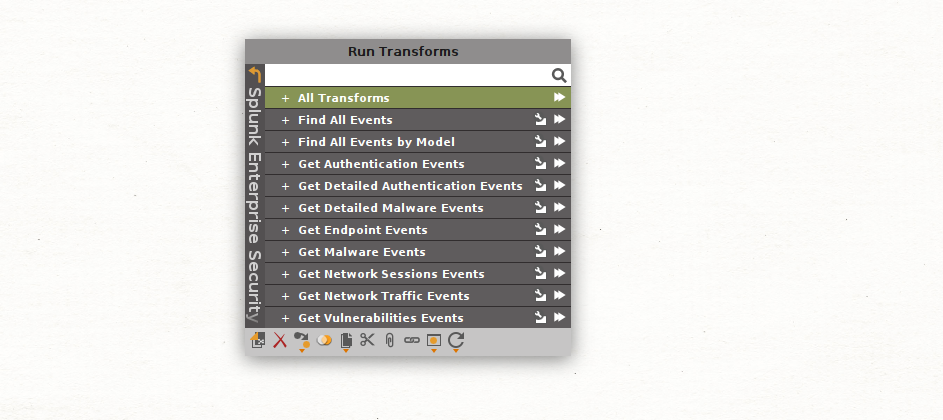
The Splunk Transforms menu presents us with a few Transform set options, each of them representing the different data models that we have made available with the Splunk Transforms.
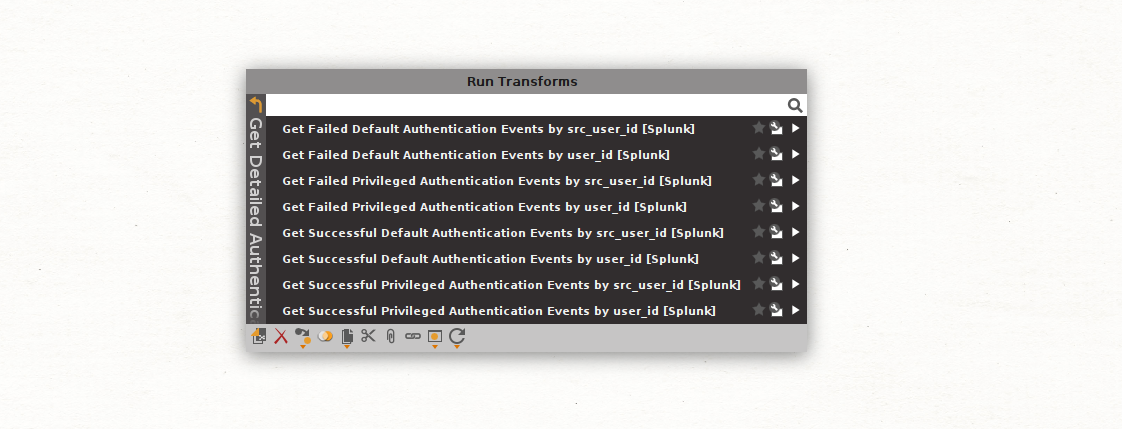
Since we are looking for authentication events, we will focus on the Get Authentication Events and the Get Detailed Authentication Events Transform sets.
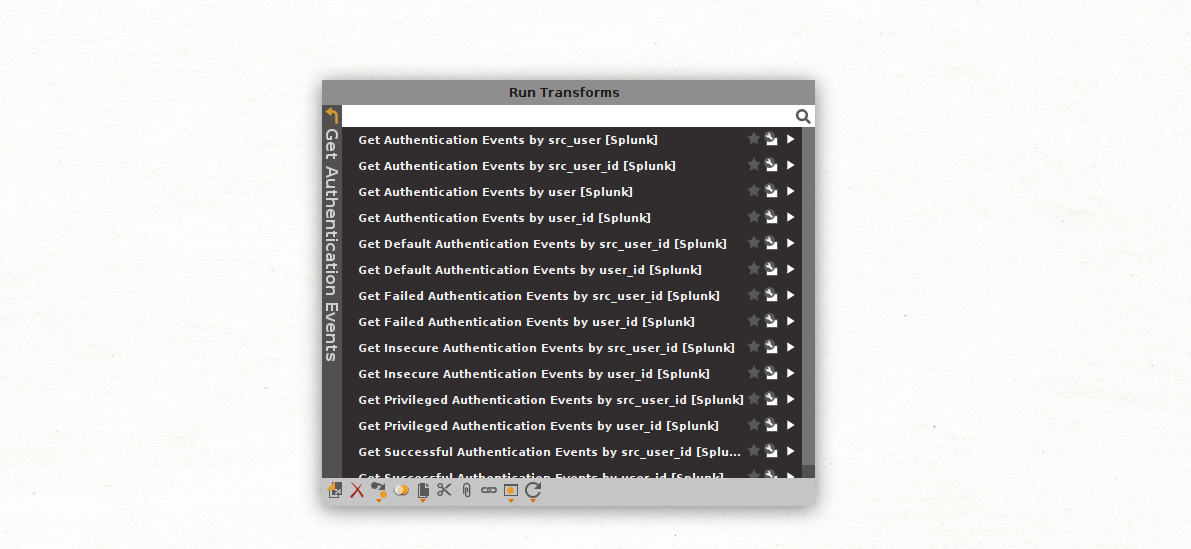
Let’s select the Get Authentication Events Transform set to retrieve information on the types of Transforms included in this set.
As we can see, we have multiple options to choose from, including general authentication events and more specific Privileged Authentication events.
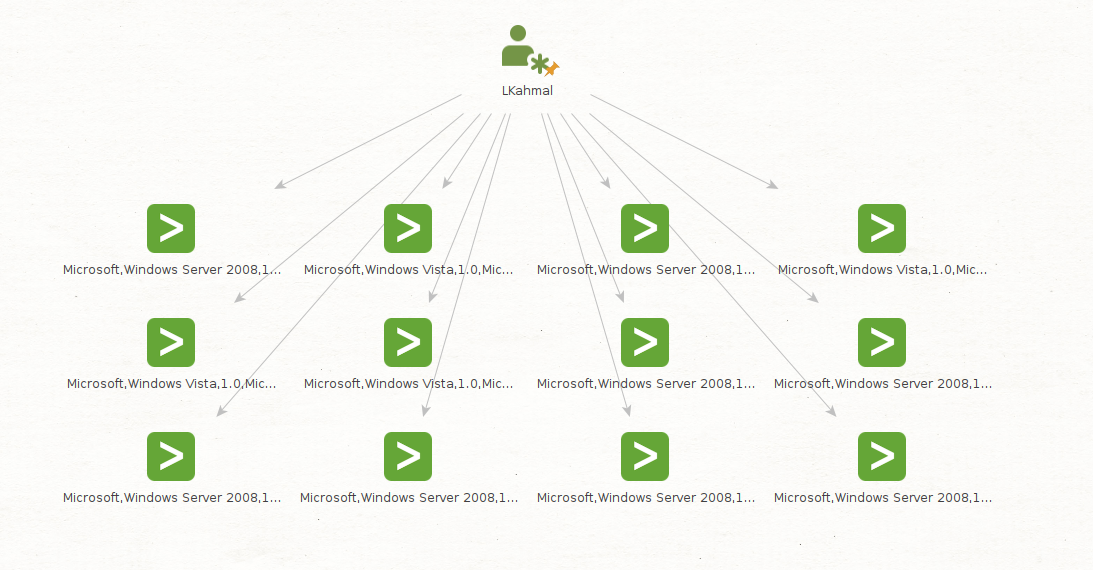
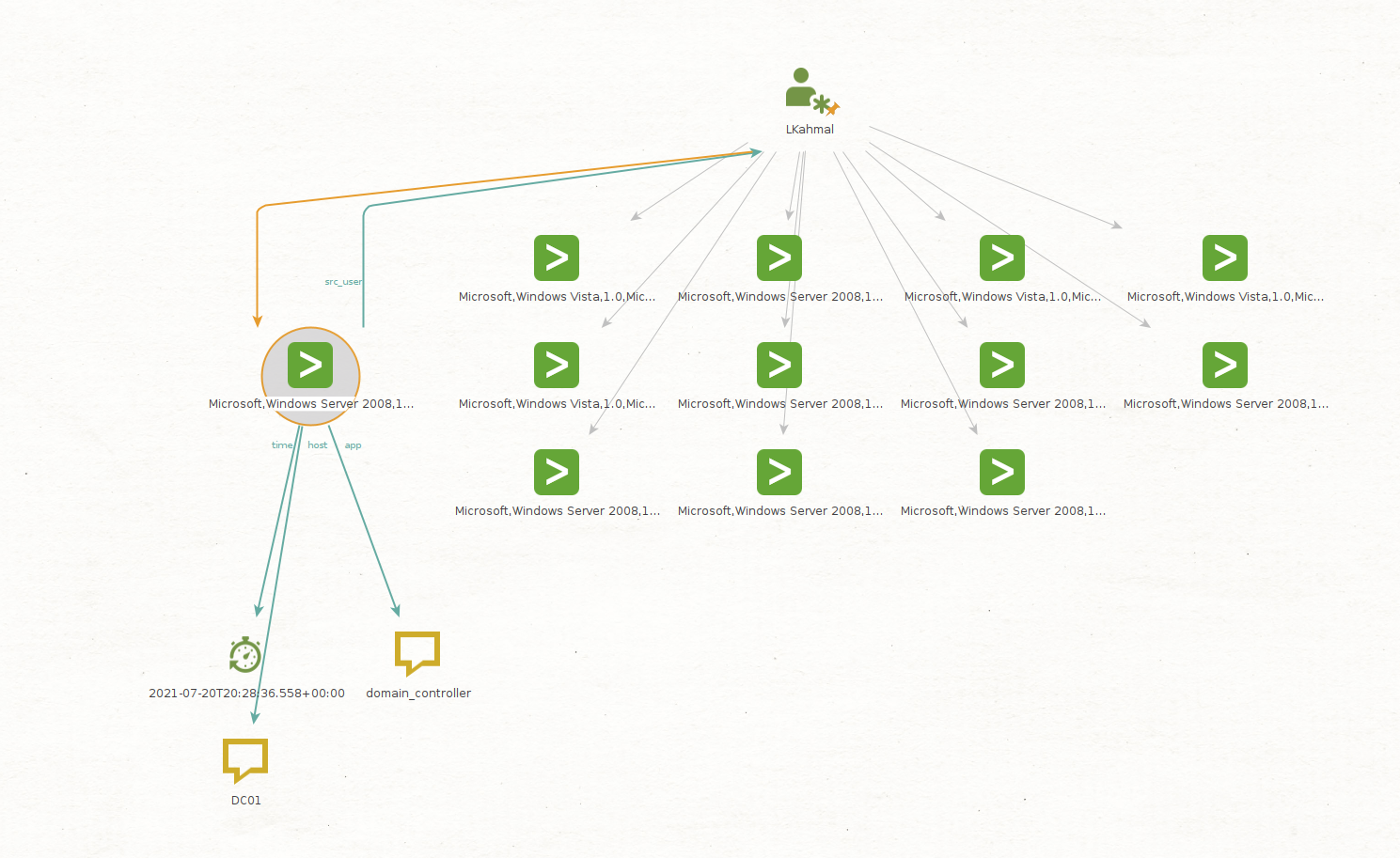
Let’s look at events where LKhamal’s account has been recorded as the src_user; we will use the Get Authentication Events by src_user [Splunk] Transform.
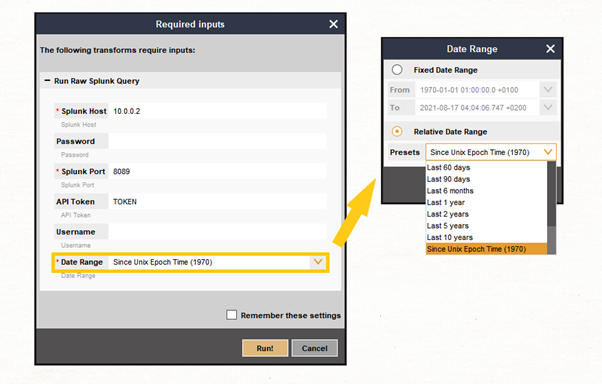
If this is the first time you’re running these Transforms, you will be asked to enter some information, and you will also be presented with the option to select a Date Range to narrow down your results to specific points in time.
We will leave the default option for now, which is the equivalent of “All Time” in Splunk; you can check the Remember these settings box if you do not want to be presented with this option every time you run this specific Transform.
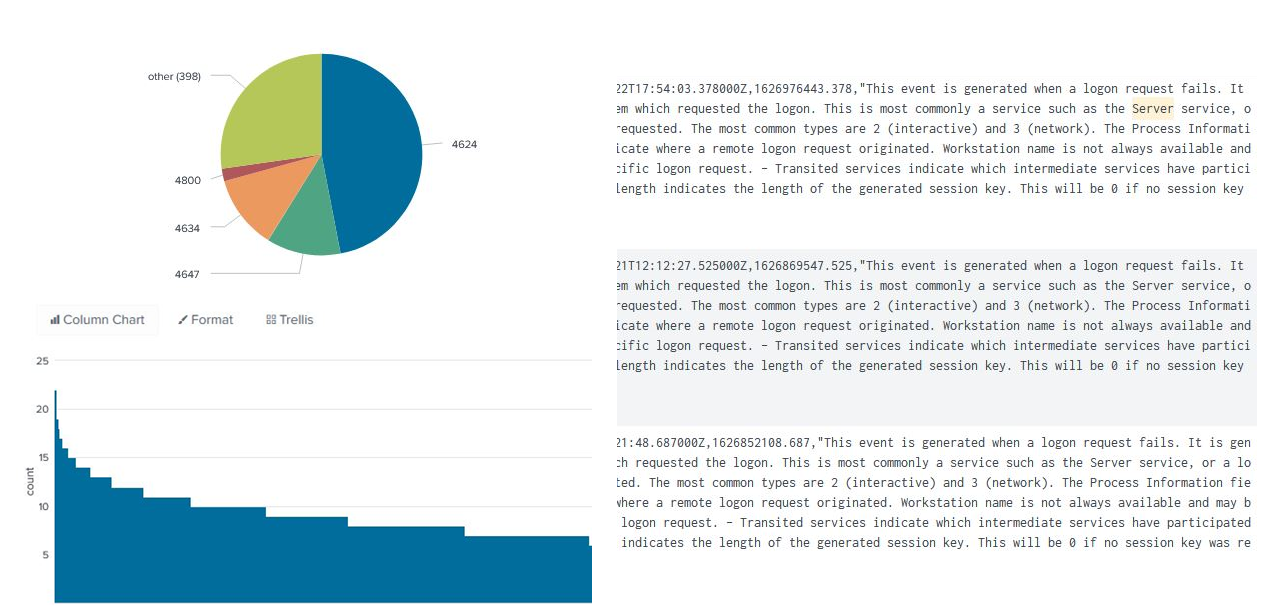
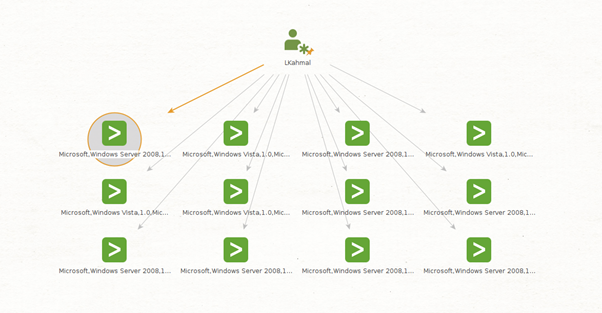
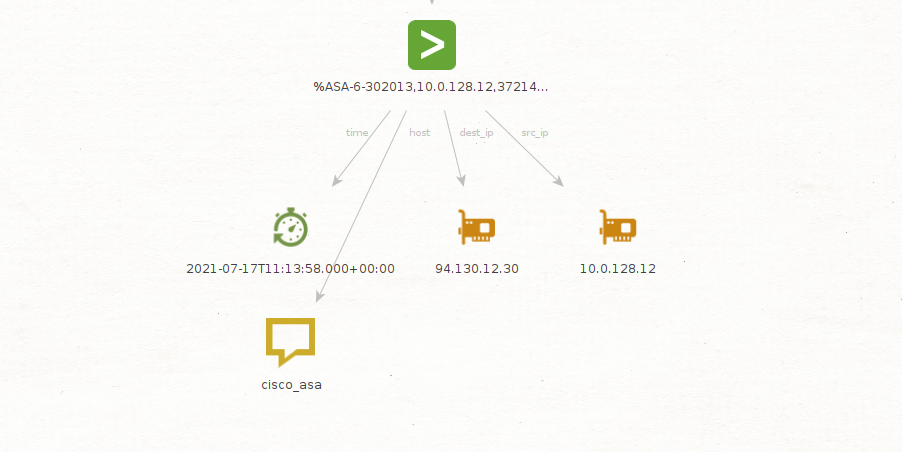
As we can see, Maltego returned 12 new Splunk Authentication Entities, which represent Splunk events where the LKhamal account was listed as the source user.
The main difference between these Transforms and the ones from the Get Detailed Authentication Events Transform Set is that you can query specific datasets from the Authentication data model with the detailed options, allowing you to choose between successful and failed events.
We will now run the Get Successful Default Authentication Events by src_user_id [Splunk] Transform and reduce our date range to only a few hours to see the difference in results.
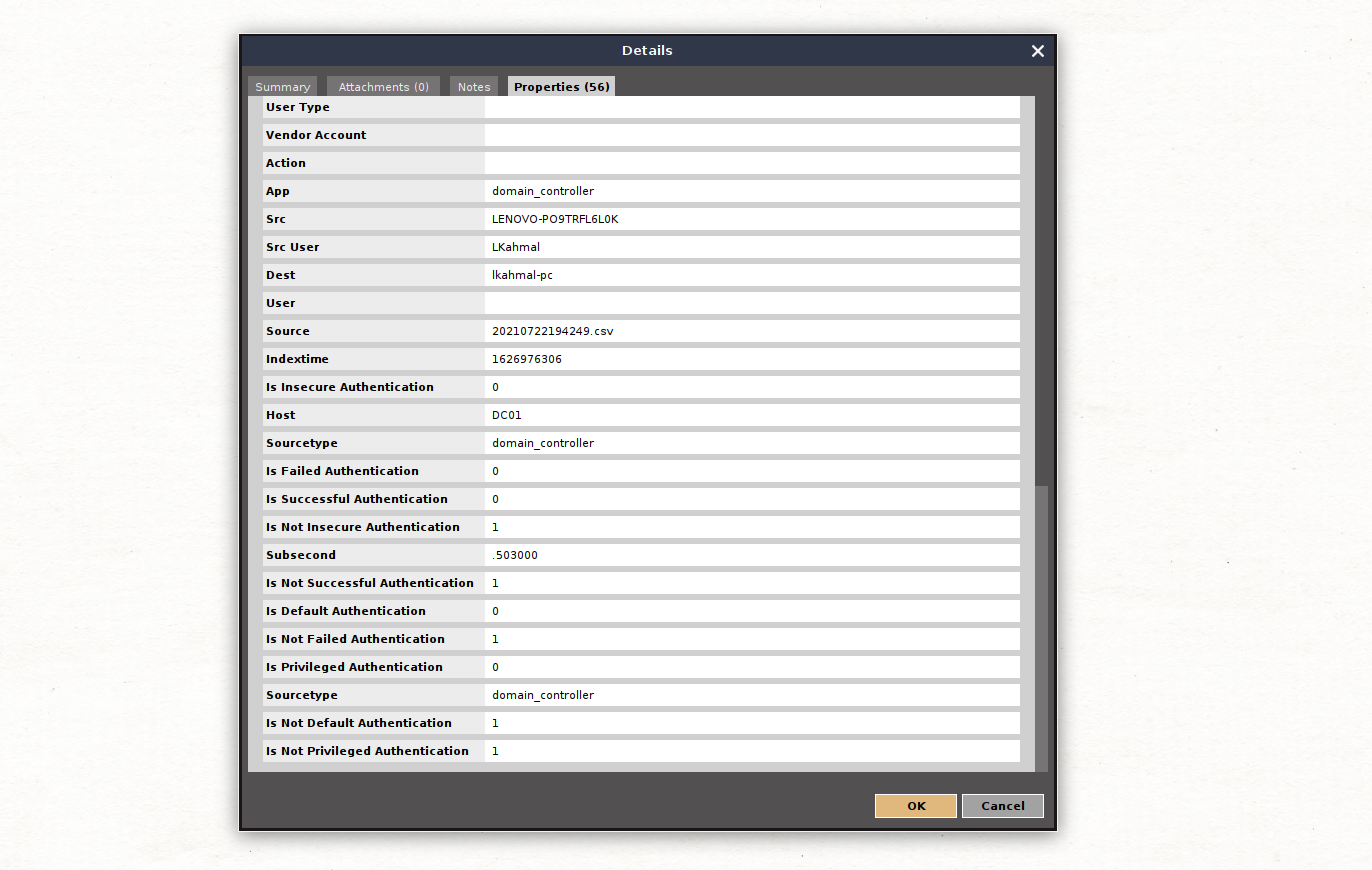
With this query, Maltego returned only one event that matches our logic; let’s open it and check the information that was returned.
As you might have guessed, the fields in the Detail View of the resulting Entity match those predefined in the Authentication data model as well as the raw event associated with this log; we can also extract some of these fields as Entities using the To Interesting Fields Transform set.
Let’s go back to the results from the Get Authentication Events by src_user [Splunk] Transform, select one of the events and right-click on it to navigate to the Splunk Transforms.
Maltego now presents us with the available Splunk Transform sets containing queries applicable to events, namely Transforms to extract interesting fields.
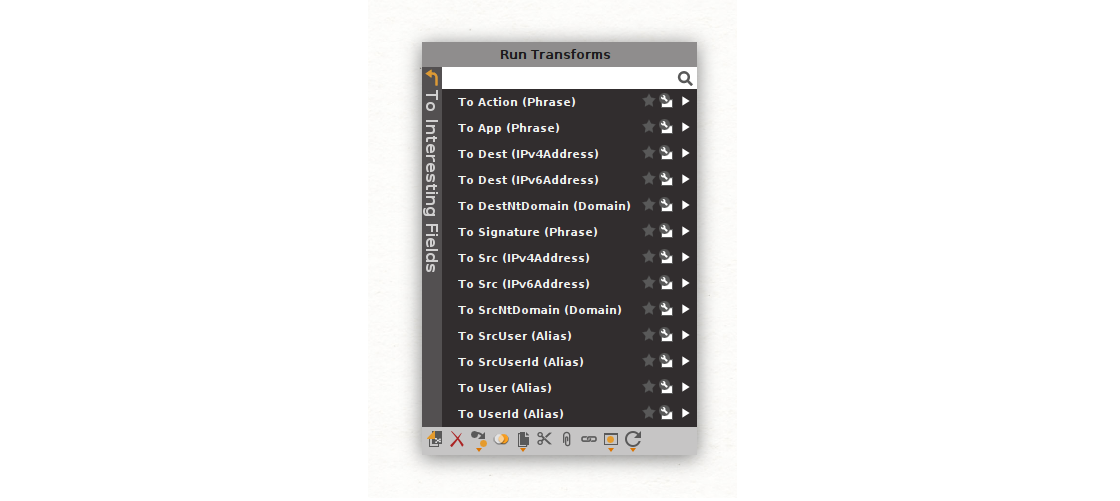
The To All Interesting Fields Transform set automatically extracts all the predefined lists of interesting fields present on the Entity. And the To Interesting Fields Transform set allows you to select specific fields to be extracted. We will now run the To All Interesting Fields Transform set, which contains the Transforms shown on the following image.
As you can see below, we now have details such as the timestamp for this event, the source type, the host that generated the logs, and the account associated with the event.
This was but a brief introduction to the Splunk Enterprise Security Transforms to show you how the CIM data models can be queried. We invite you to install the new Transforms and test this fantastic integration!
Can we perform Splunk Search Processing Language (SPL) searches with the new Transforms? 🔗︎
Yes, you can, we have included an option to perform raw searches, where you can use Splunk’s Search Processing Language (SPL) to retrieve other events that may not be part of the data models yet.
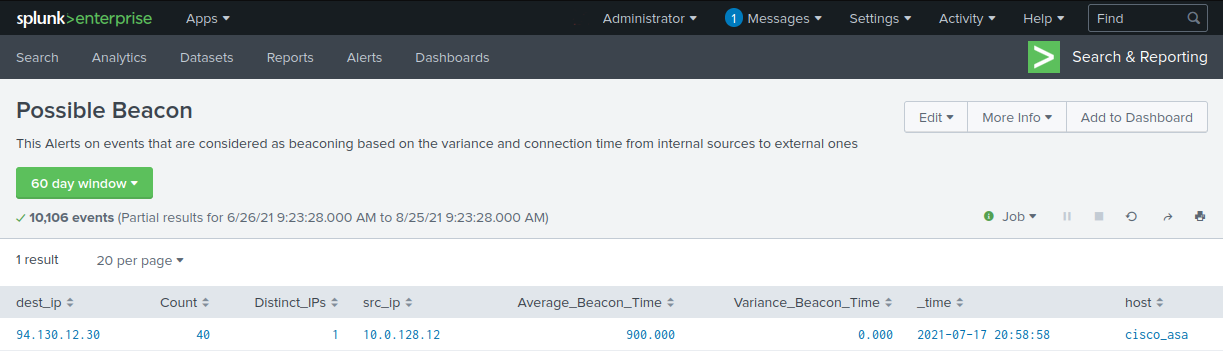
Let’s try this option to bring a specific Splunk event into Maltego. Let’s pretend you are a SOC L1 analyst and you are tasked with investigating a “Possible Beaconing” alert that was triggered by Splunk.
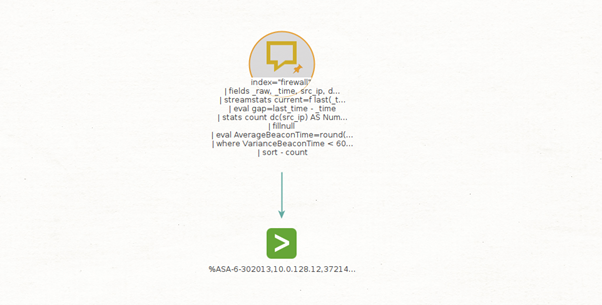
If you wanted to do a non-raw search on Maltego, you would take the external IP address, paste it into Maltego and use the Network Traffic Events Transform set to retrieve all the different events where that IP has been observed. But, since you are interested in testing the Raw Searches, you decide to take the query that triggered the alert and paste it into a Phrase Entity.
Now, you can run the Run Raw Splunk Query Transform, which gives you the option to select a specific time range for this type of search to narrow down the results.
Once you have the event in Maltego, you then decide to use the To Interesting Fields Transform to extract those bits of information that will help you throughout the investigation.
This time you will notice that you don’t have the choice to extract specific fields like you did before. This is because fields are based on different data models and, since this event is not linked to a specific model, it will extract all interesting fields instead.
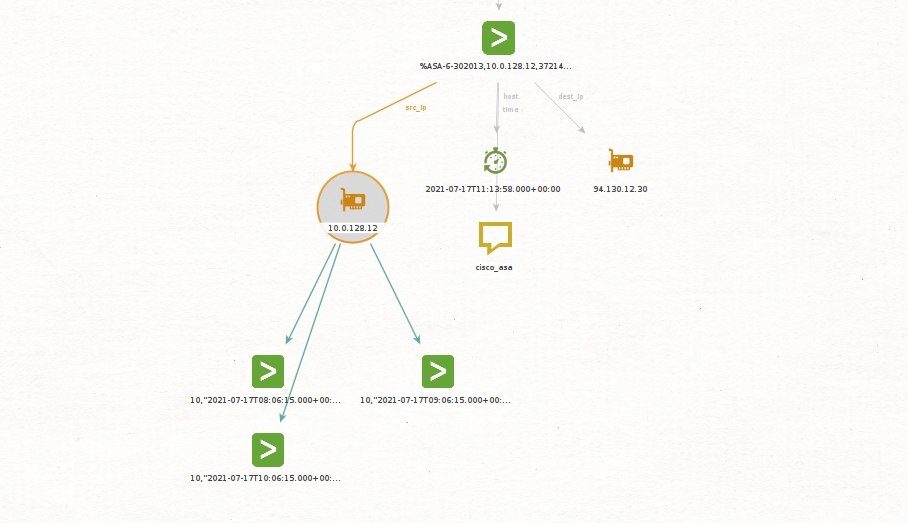
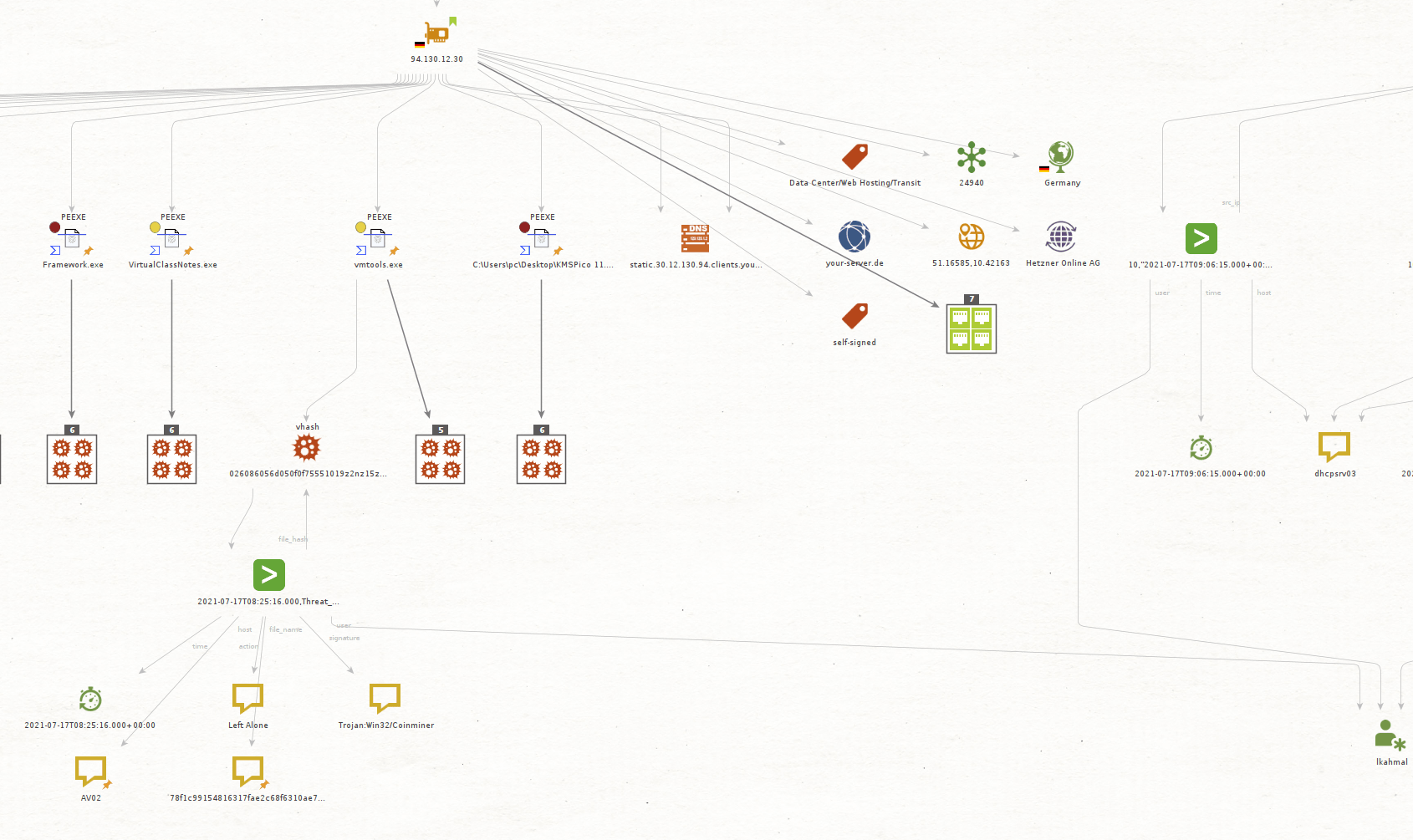
You then decide to get information on the internal IP, for which you can use the Get Network Sessions Events Transform set to check your DHCP logs around the time of the event.
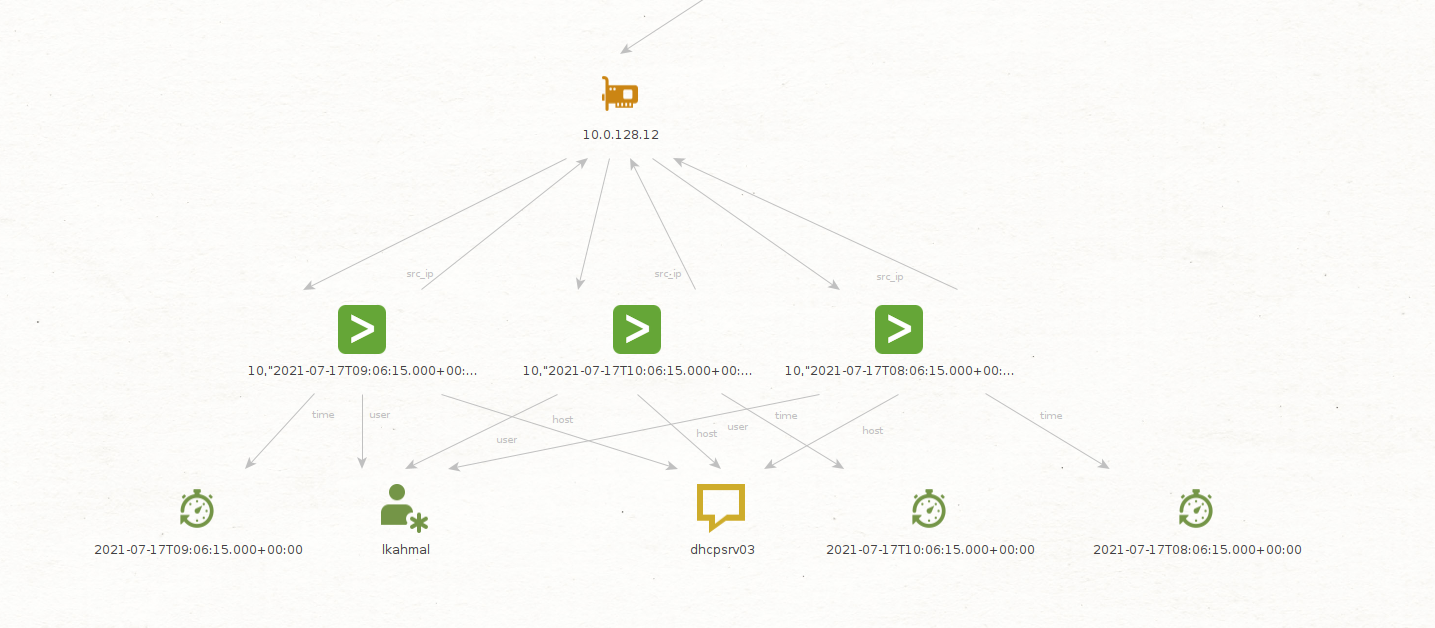
In this case, Maltego returned three events; let’s extract the interesting fields from them and check whether they are linked.
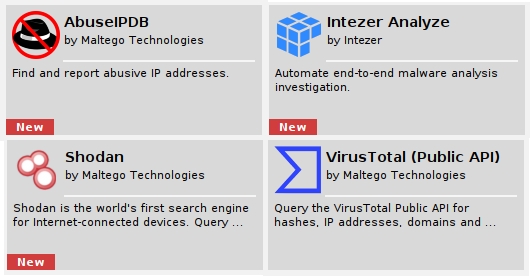
The results do in fact show that these events point back to our friend LKhamal, you then decide to check what is behind the external IP, and for that you will use the following Maltego Transforms:
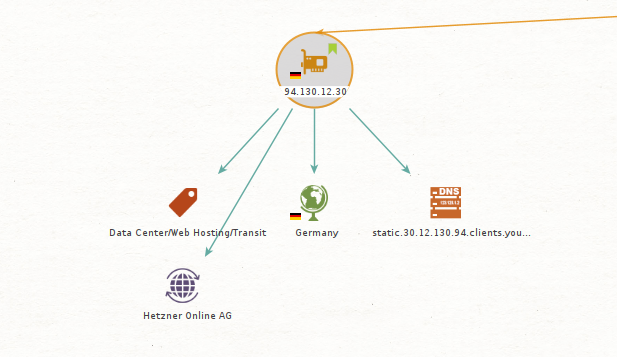
You decide to start by checking AbuseIPDB to find details associated with this IP, such as location, associated hostnames, ISP name as well as usage type.
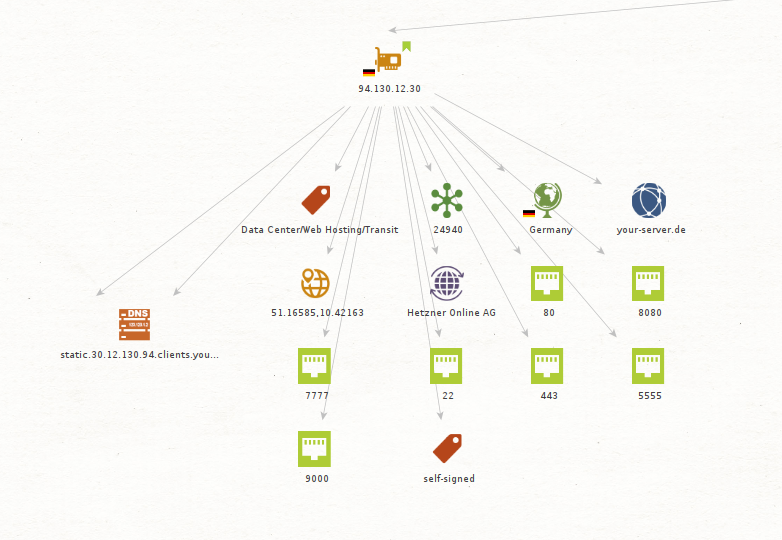
You then use Shodan to get more information related to this IP. In this case Shodan provided some relevant details such as ports that have been observed on the IP as well as a tag mentioning that a self-signed certificate was observed on the same.
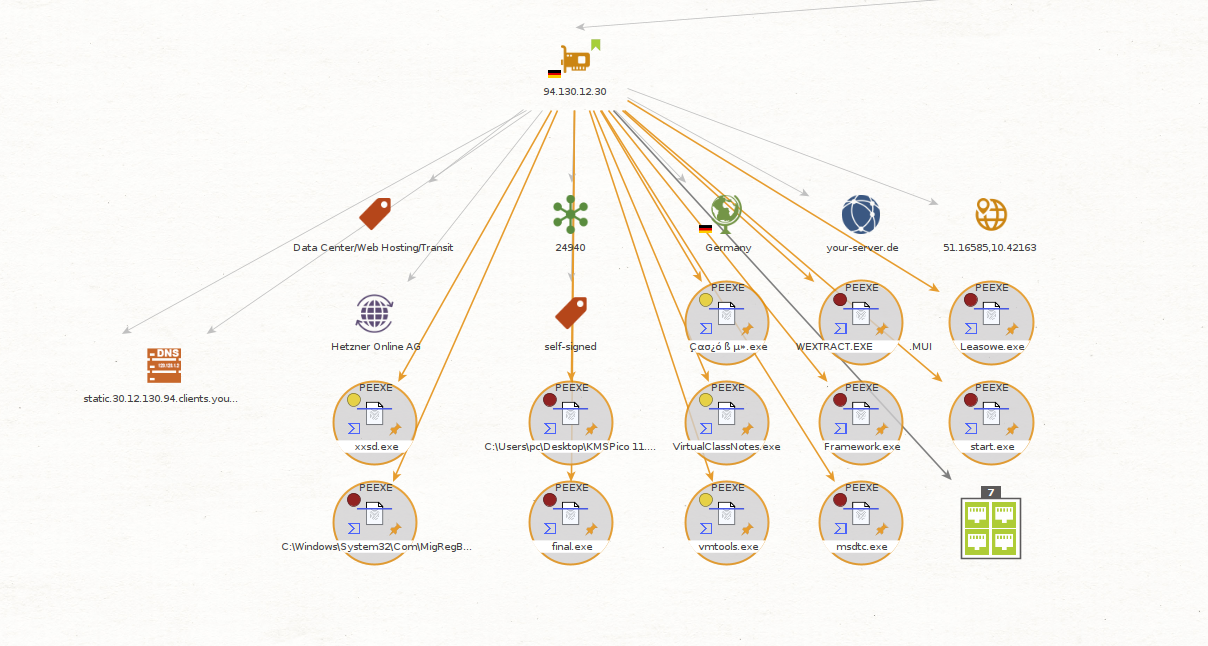
Next, you want to use VirusTotal to check whether there are any malicious files linked to the IP address, which in this case it seems like we have a few results that are not too great.
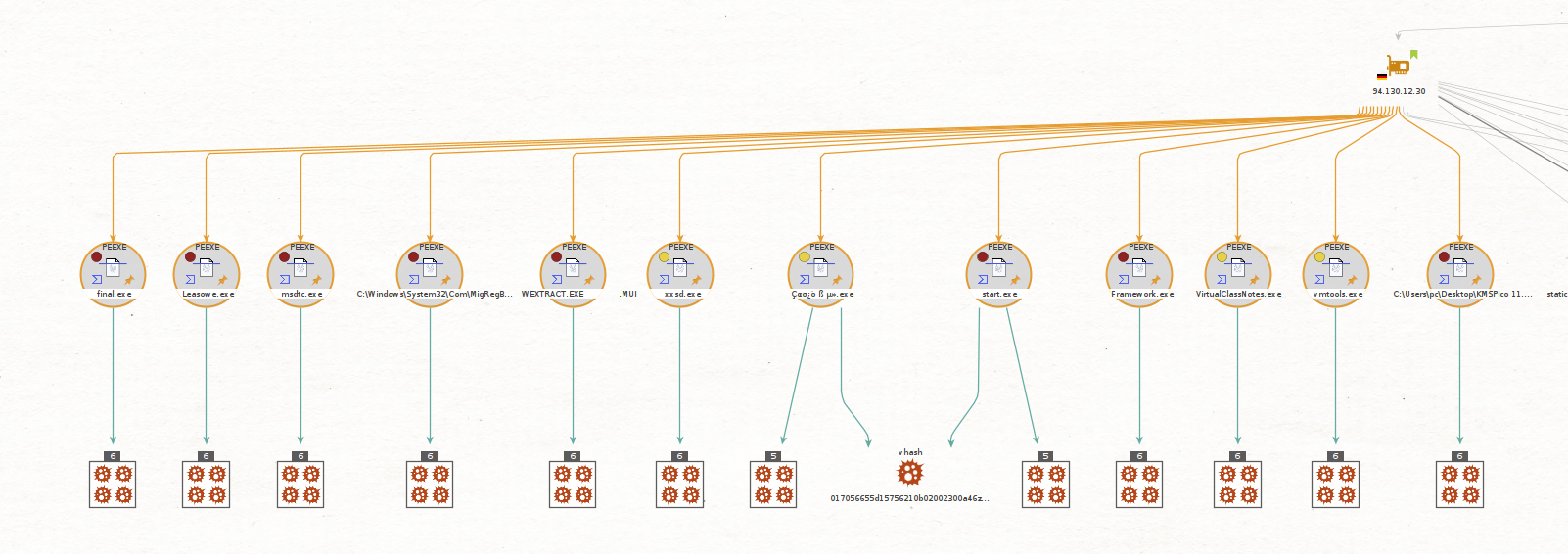
You are suspecting that LKhamal’s machine is infected with some type of malware, so you decide to extract the Hashes associated with these files using our VirusTotal Transforms.
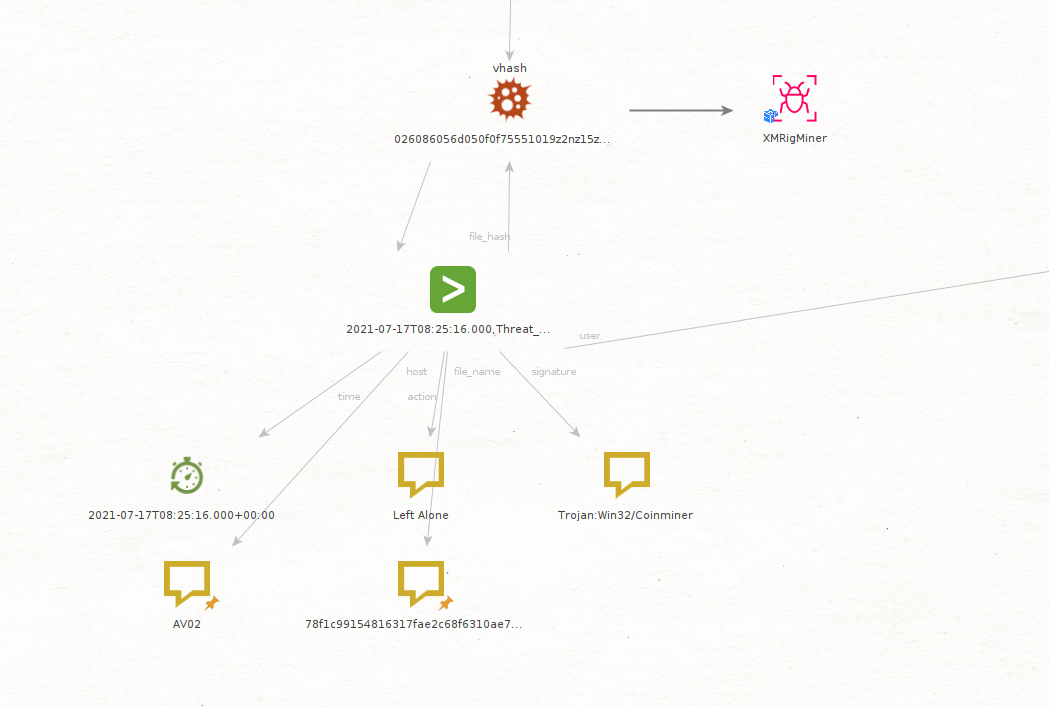
You then use our new Get Malware Events [Splunk] Transforms to check whether any of these have been observed on your network, in this case you were able to find one of these hashes in your logs, so you decide to extract the interesting fields from the new Entity.
It looks like LKhamal’s machine is in fact infected with malware, a coinminer in this case, and that your Antivirus Solution observed the file but decided not to take any actions on the same.
Now that you have confirmed that LKhamal’s machine is infected with malware and you have gathered other IOCs associated with said malware, you want to confirm its family type, so you use Intezer to get that information from the hash that was observed on your network.
Intezer confirms that the hash is in fact related with a type of coinminer malware called XMRigMiner.
With this information in hand, you can now create a security incident to start the remediation process for LKhamal’s machine.
But wait, there is more! 🔗︎
We have also created a new Malware Investigations [OSINT] Maltego Machine that automatically enriches the information associated with Hash Entities and checks for the associated IOCs in Splunk so you can minimize the time and effort required for these types of investigations.
This Machine leverages several Free and BYOK integrations to enrich Hashes, Files, IPs, Domains, and Splunk Events.
How can I use this integration? 🔗︎
To take full advantage of this integration, your company needs to set up the following CIM data models, and fields must have corresponding aliases to those specified for each data model.
It would be best to have an internal Transform Development Server (iTDS) with network access to your Splunk Search head.
If you’re interested in integrating your Splunk data to Maltego, please reach out to Maltego using the contact form on our Splunk integration detail page.
Don’t forget to follow us on Twitter and LinkedIn and sign up for our email newsletter to stay updated on the latest news, tutorials, and events.
Happy Threat Hunting!