Silobreaker is a SaaS platform that lets users monitor and research a wide variety of different topics, threats and incidents. Common customer use cases center around cyber and physical security, strategic and geopolitical risk, competitive intelligence, and vulnerability monitoring. The platform is fed with real-time data from approximately a million openly available sources, as well as deep & dark web content from leading intelligence providers. Silobreaker excels at minimizing the time taken for security and risk teams to understand and act on vast amounts of unstructured textual data, including news, blogs, reports, feeds, forum posts and tweets.
Gathering Intelligence Using Silobreaker and Maltego 🔗︎
Extensive use of machine learning and data fusion techniques help Silobreaker users extract intelligence at scale from noisy datasets. These core capabilities are supported in Silobreaker’s Maltego Transforms, including:
- Support for Silobreaker Entities and aliases
- Relevance sorting algorithms
- Evidence Transforms
Silobreaker Entities 🔗︎
To structure data effectively, Silobreaker operates a database of over 100 million Entities, broken into 36 different types. These include common classifications, like companies, people and geographic locations, as well as many types that are use-case specific, such as threat actors, malware, credit cards and products.
To help users search as efficiently as possible, most Silobreaker Entities also contain a variety of aliases. Aliases are other names for the same search term, often in different languages, and with casing and spelling variations. These are made available to Maltego users through the Matching or Related Entities Transforms.
Relevance Sorting 🔗︎
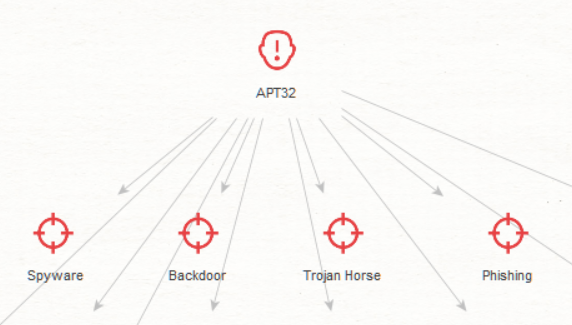
Silobreaker tries to find the most appropriate Entities and documents for a given query at the moment it’s made. To make this possible as new content is published, Silobreaker’s Transforms use a relevance sorting algorithm to rank results. The algorithm takes numerous factors into account, including the commonness of search terms, their frequency in the results set, and their position within the documents themselves. This allows Transforms to display changing relationships over time and show that Donald Trump, the Republican party and Newsmax are being discussed together, or that APT28, Russia and the Zebrocy malware are connected.
Evidence Transforms 🔗︎
Silobreaker is highly suited to strategic monitoring, and can quickly uncover trends and relationships across different datasets. It is important to note, however, that while Silobreaker’s Transforms can dramatically speed up investigations, they cannot replace the work of a trained analyst. To make the most of this Hub Item, it is vital not to jump to conclusions about the nature of a correlation: If the Transforms suggest that a specific threat actor is related to Russia, this does not mean it is suspected to be Russian. It could also be targeting Russian assets or be mentioned in the context of a Russian national.
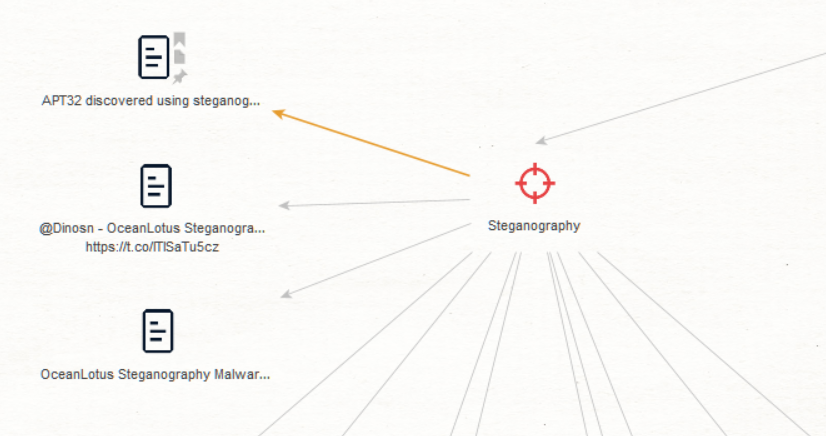
To aid in determining how a correlation has been established, users can run the [SB] Document evidence for link Transform, which will show the contextual evidence and source for any relationship.
The Silobreaker Transforms in Maltego 🔗︎
We have laid out examples and advice on how to make the most of Silobreaker in Maltego. The different Transform components of this Hub item are listed below, as well as guidance on how to use them.
Matching Entities 🔗︎
This Transform is normally the starting point for any investigation using Silobreaker: It allows a user to link a Maltego Entity from any Transform set to the equivalent Entity in Silobreaker, providing all the benefits of Silobreaker’s aliasing system.
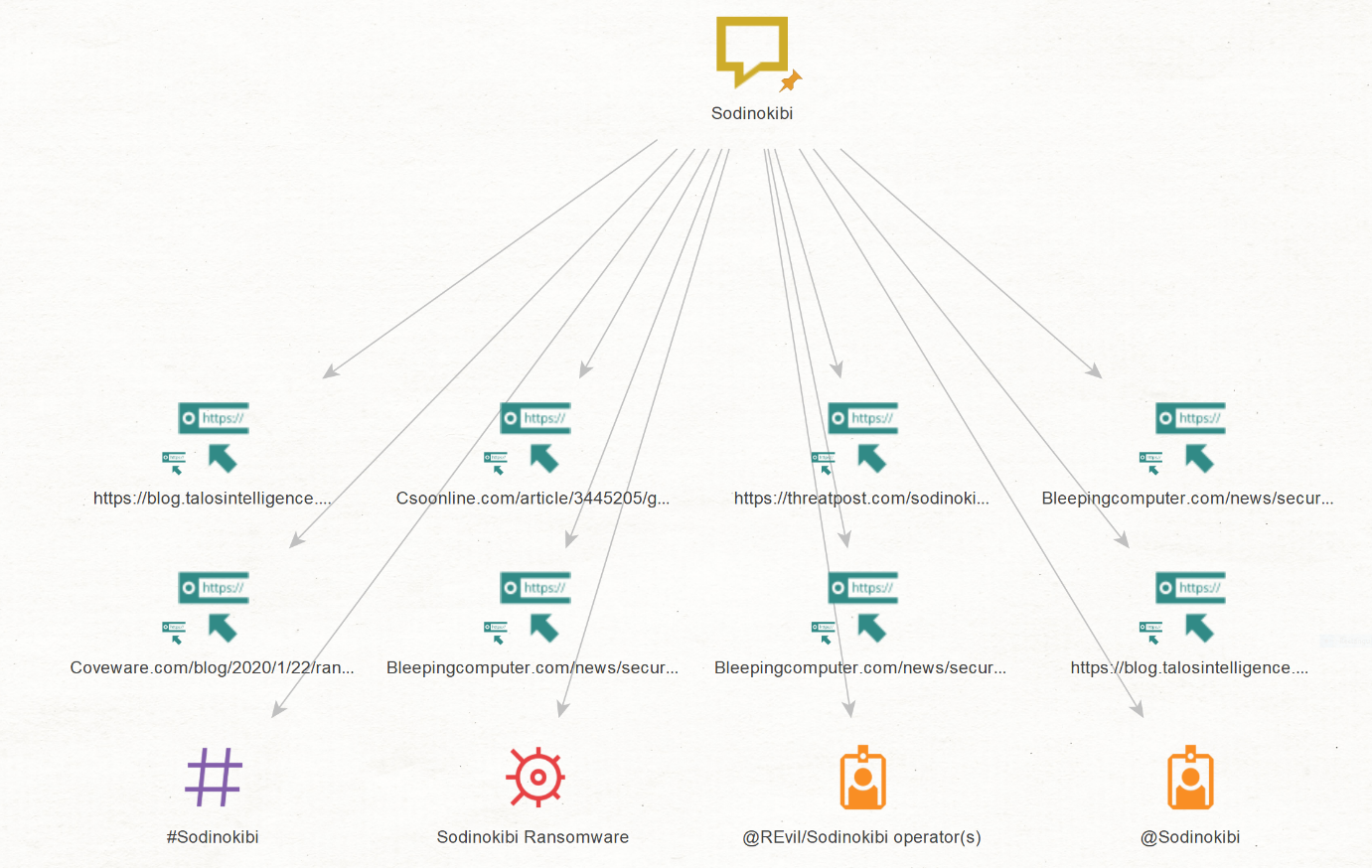
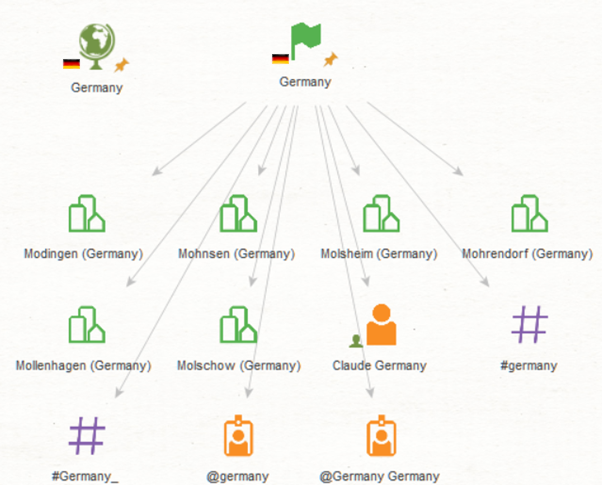
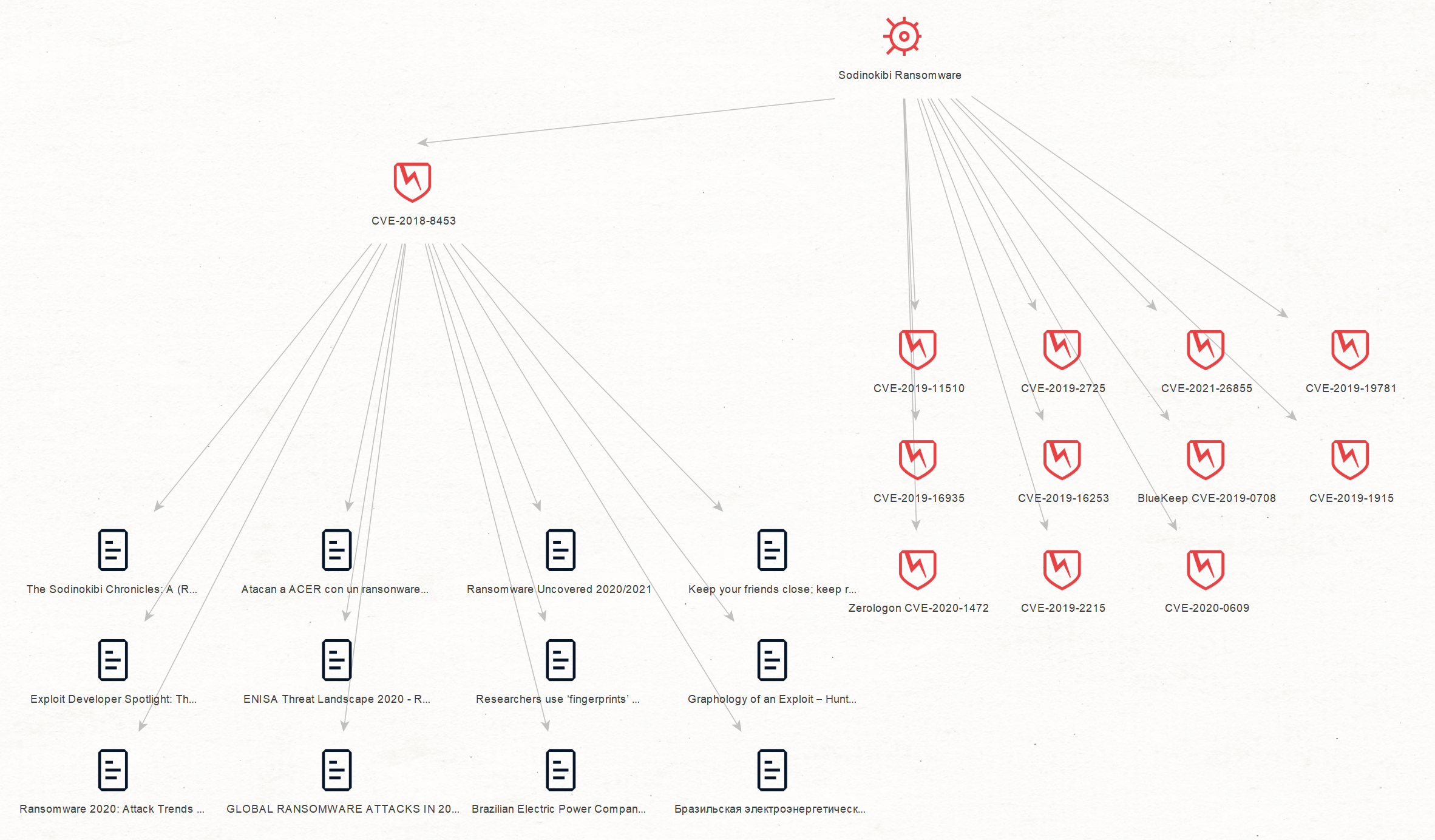
For example, to investigate the Sodinokibi ransomware, the first step would be to add any Entity and rename it “Sodinokibi”. Then you can run the [SB] Matching Entities Transform to retrieve Silobreaker Entities of any type that match this keyword. If you already know the appropriate Silobreaker Entity type (for example, malware), you can also run the [SB] Malware Transform to find malware Entities that are highly related to Sodinokibi.
Once matches have been found, it is up to the user to select the correct Entity to continue the investigation. In this example, the investigation focuses on the ransomware, not the threat actor using the Sodinokibi username, the hashtag, or any of the URLs.
Depending on the type of the Entity this Transform is run on, it is possible for properties to be directly added to your starting Entity instead of returning a matched Entity.
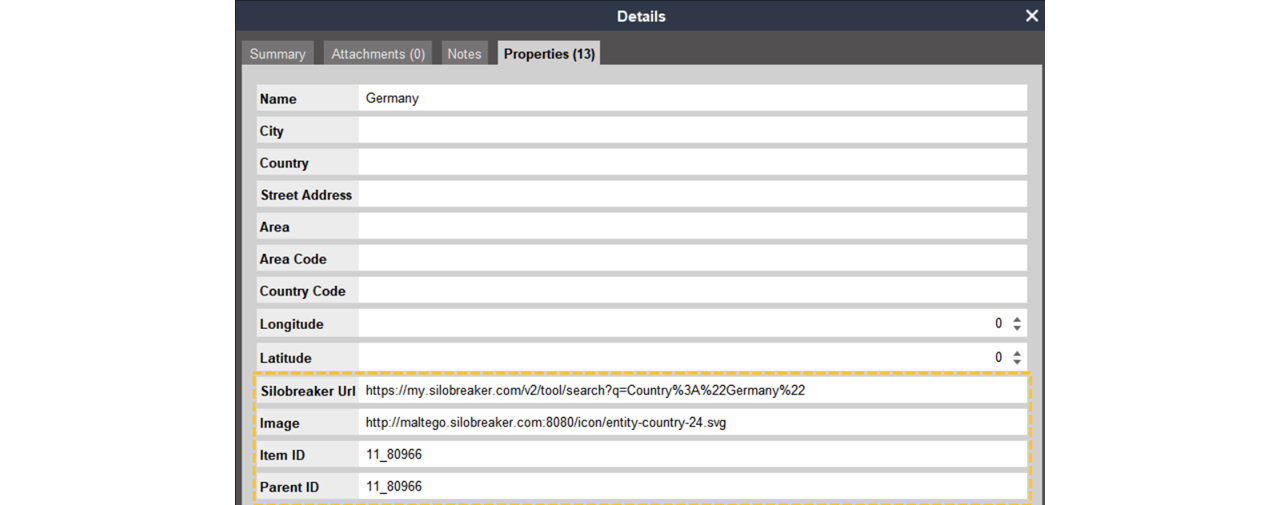
In the case above, the [SB] Matching Entities Transform was run on the Maltego Country Entity named “Germany” (an unmatched example is also shown to the left). In this case, only eleven results were returned instead of twelve during the matching process. Because the starting Entity was already a Country Entity, the Transform has changed the Entity’s icon and added Silobreaker properties to it, rather than adding a new Entity to the graph. These properties are displayed on the screenshot below.
Controlling the “Number of Results” Slider 🔗︎
Being aware of your results slider is very important when using Silobreaker’s Transforms in Maltego. Since the Transforms pull from a pool containing hundreds of millions of Entities, Transforms that act on large document sets will return many related Entities to the graph. This means that it is important to choose how wide a net you want to cast. The context of your investigation should help you make that decision.
Silobreaker always returns the most relevant Entities first, meaning that each Entity returned by these Transforms is likely to be less relevant to your investigation than the one before it. In many cases, you will need to consider your use case when deciding how many results to return.
For instance, when searching for malware related to the Android OS it is reasonable to expect more than twelve results to be relevant. In contrast, asking for more than 200 vulnerabilities related to a specific malware is unlikely to be useful.
Getting Related Entities 🔗︎
The majority of Silobreaker’s Transforms allow the user to find which other Entities are strongly correlated with an initial Entity of interest. These Transforms are organized into several categories:
- Cyber
- General
- Geo
Within each of these categories is a collection of Transforms that will find Entities of a specific type, by searching through documents that contain your starting Entity.
Using these categories is an easy way of narrowing down search results and focusing on a certain type of Entity. The cyber Entities category includes Transforms that return Entities such as Bitcoin wallet addresses, domains and email addresses, as well as threat actors and malware. The geo Entities category contains Transforms for geographical entities, such as cities, countries and places. The general category includes Transforms focused on Entities like persons, companies, and products.
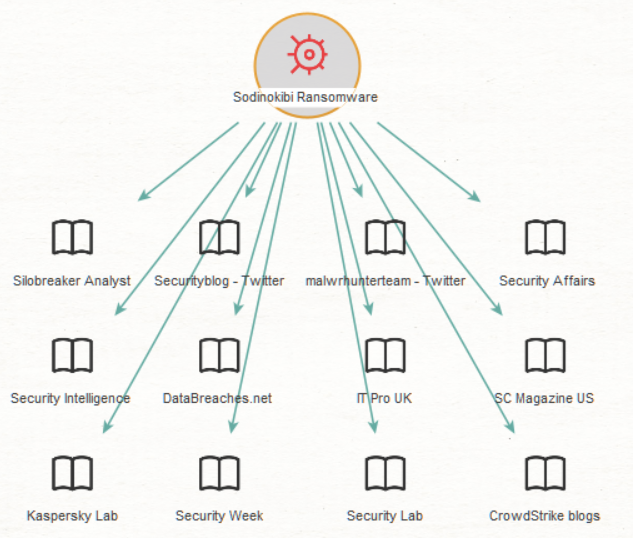
In order to gain general insight on any starting Entity, the [SB] Related Entities Transform will return a set of relevant Entities regardless of type. You can also search for sources that frequently discuss your starting Entity by using [SB] Related Publications. If you want to focus on cybersecurity news, you can also use [SB] Search Threat Publications to visualize industry publications that discuss your selected Entity. An example of these results is shown below.
Documenting The Evidence for A Link 🔗︎
Related Entities Transforms will add Entities to the graph if they are mentioned in the same documents as the starting Entity. Silobreaker also allows users to surface these documents (the evidence for the connection between two or more Entities) using [SB] Document Evidence for Link. To reduce the potential for noisy results, there are two versions of this Transform: One that includes pastes and one that excludes them.
The documents returned from these Transforms contain links to the original source (usually an external website) and to the relevant page in the Silobreaker platform. This facilitates the viewing of these documents even if the original publication is taken down.
Searching for Documents Mentioning An Entity 🔗︎
It is possible to search for documents mentioning a specific Entity directly, without going through the previously described process of finding related Entities and surfacing the evidence. Transforms like [SB] Search All Documents will simply search for documents mentioning a specific Entity. Eight other Transforms also perform a similar search with a scope that is limited certain types of documents. These can be used to drill down on news articles, blog posts, forum posts, pastes and so on.
Using Silobreaker Query Language 🔗︎
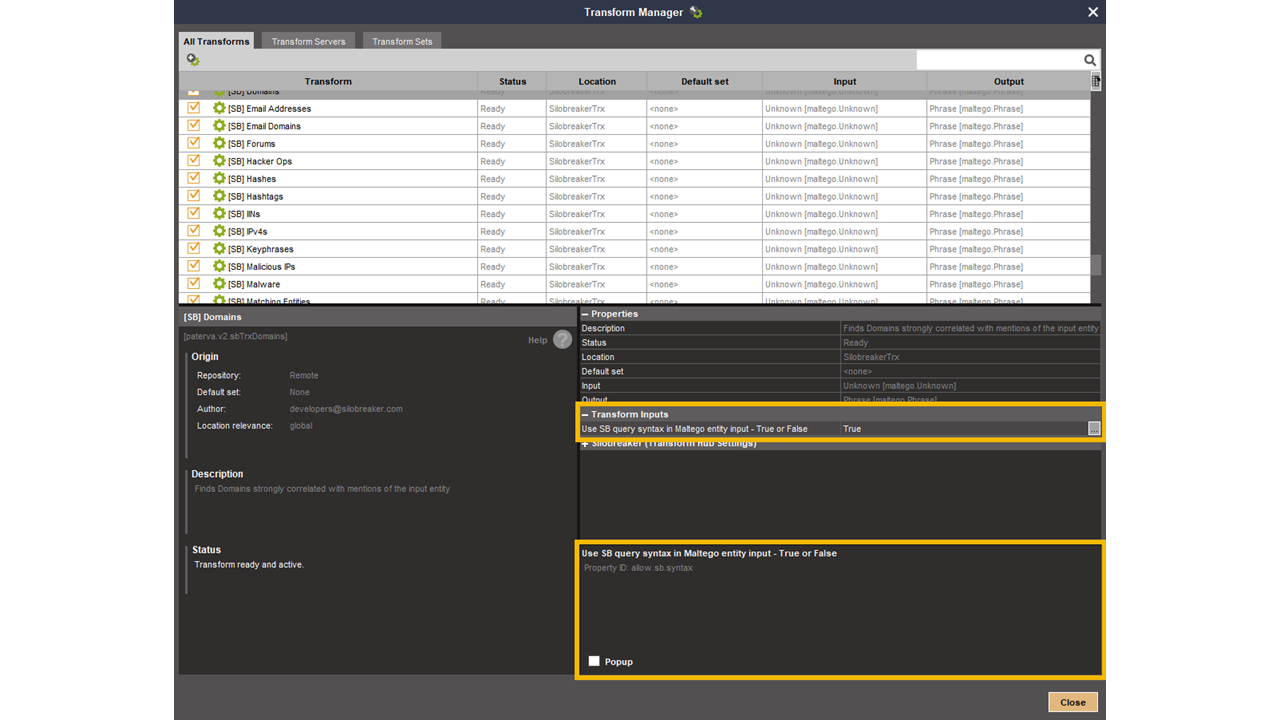
Silobreaker has a detailed query language to help find documents that suit precise criteria. A search can be narrowed down according to parameters such as the type of document, the source, the language, and the publication date. To use this feature, set the “Use SB query syntax” parameter to “True” in the Transform settings in the Transform Manager (see screenshot below) or choose to be asked every time you run the Transform by crossing the Popup checkbox. More information on syntax is available on Silobreaker’s website.
With a Silobreaker account, you can also take advantage of the platform’s List functionality: Instead of researching the same several topics or Entities, you can aggregate them into a list and run Transforms on all of them at once. A list created in Silobreaker can be used in Maltego by supplying the appropriate query language
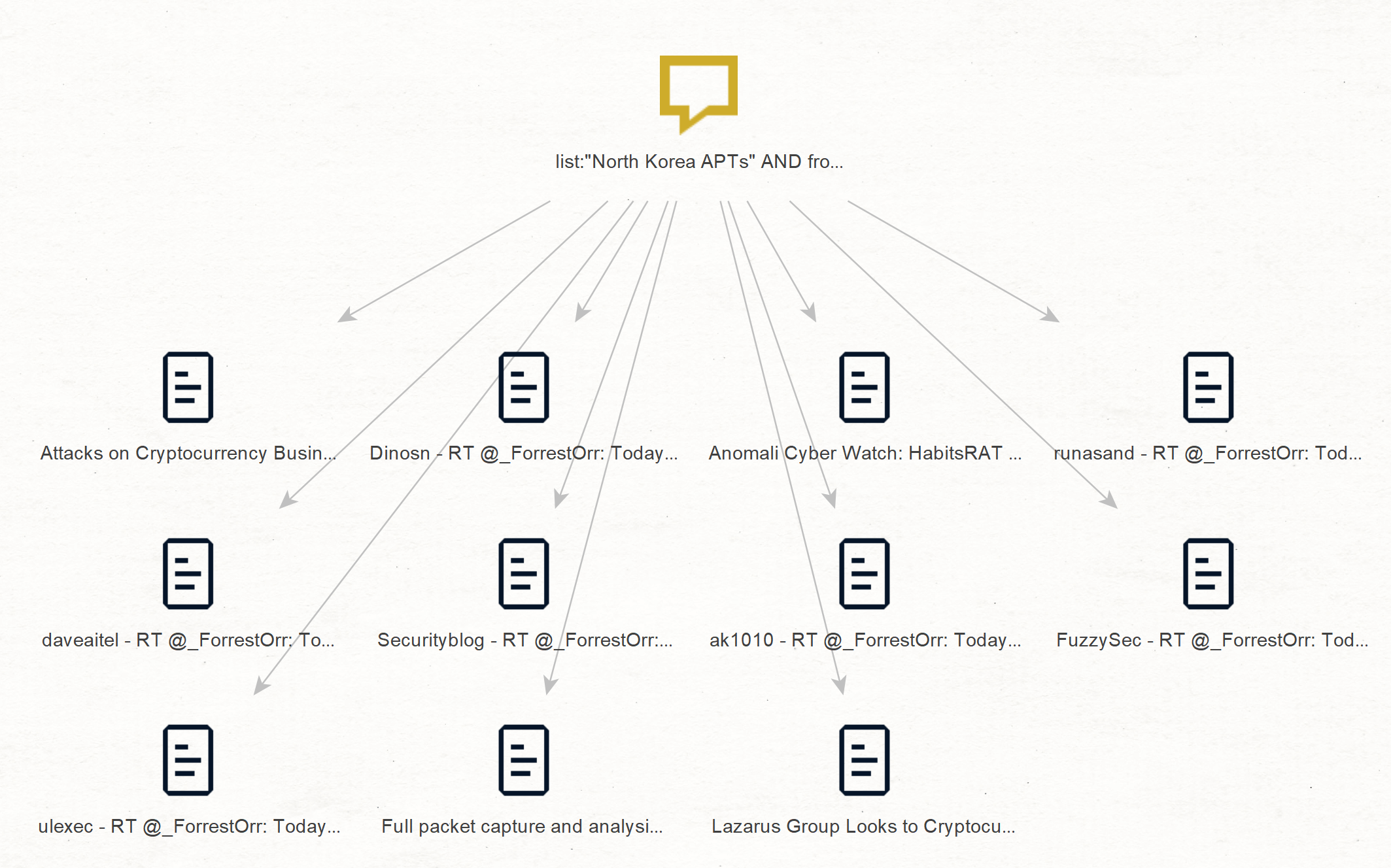
Below is an example of a graph containing documents from select cybersecurity publications in the past seven days. The results contain any mention of one or more of the North Korea APTs in the featured list. It has been produced using a Phrase Entity named list:“North Korea APTs” AND fromdate:-7 and the [SB] Search for Documents from Threat Publications Transform.
Using Additional Sources 🔗︎
Silobreaker data and publications can be seamlessly combined with other data sources such as Intel 471 and Flashpoint to further enrich results directly in Maltego using the Transform Hub.
Silobreaker in Action: Monitoring Banking Trojans Targeting LATAM Banks 🔗︎
To complete this introduction of the Silobreaker’s Transform set, let us look at a use case centered around threat monitoring. In this use case, a threat analyst working for a large bank from Latin America wants to list banking Trojans impacting the banking sector in the region.
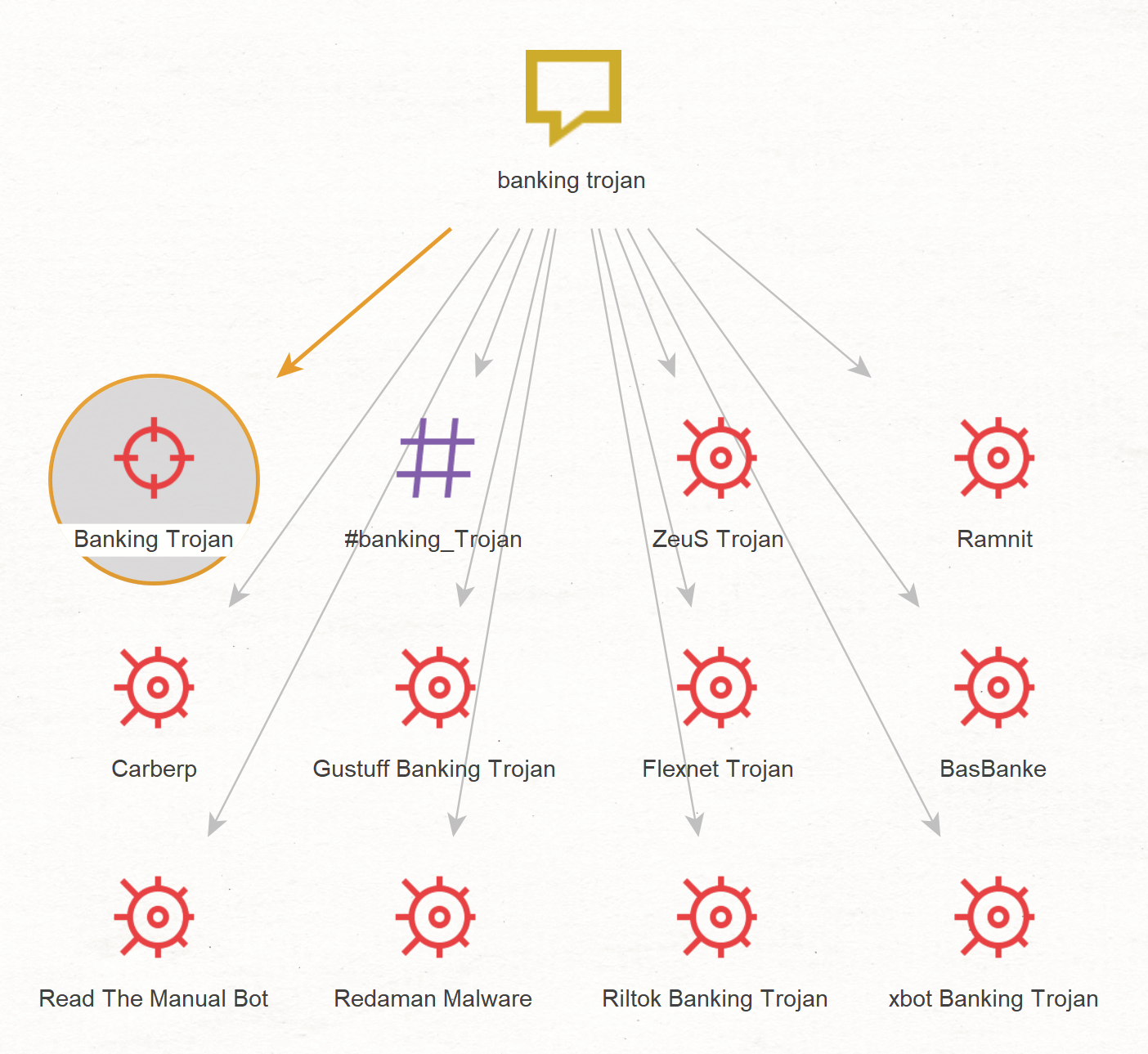
The first step of this investigation is to add relevant Silobreaker Entities to the graph, then search for malware related to them. Before anything else, make sure that the result slider is set to twelve and that collections are enabled. To begin, insert the phrase Entity “banking trojan” in the graph and run the [SB] Matching Entities Transform.
Select the AttackType Entity “Banking Trojan” and remove the other Entities on the graph.
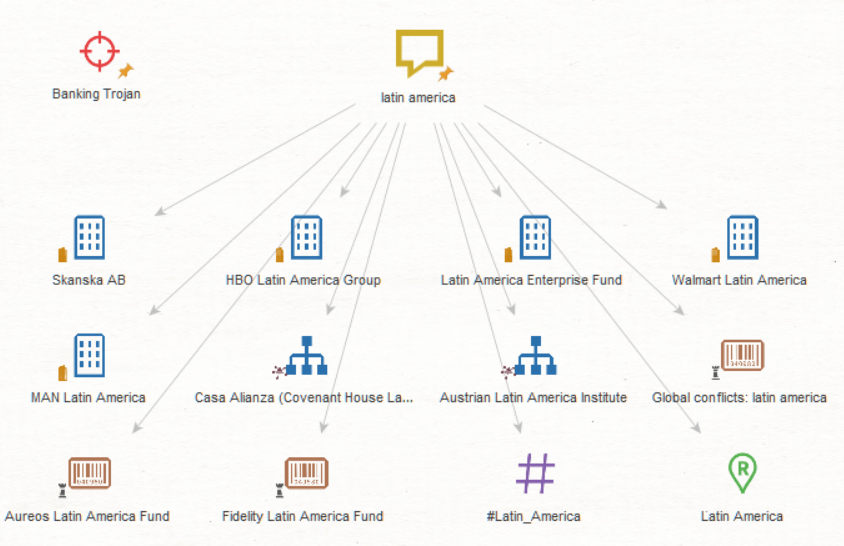
Apply the same method for the region: Add a phrase Entity and rename it “latin america”. Run the [SB] Matching Entities Transform and keep only the Region Entity.
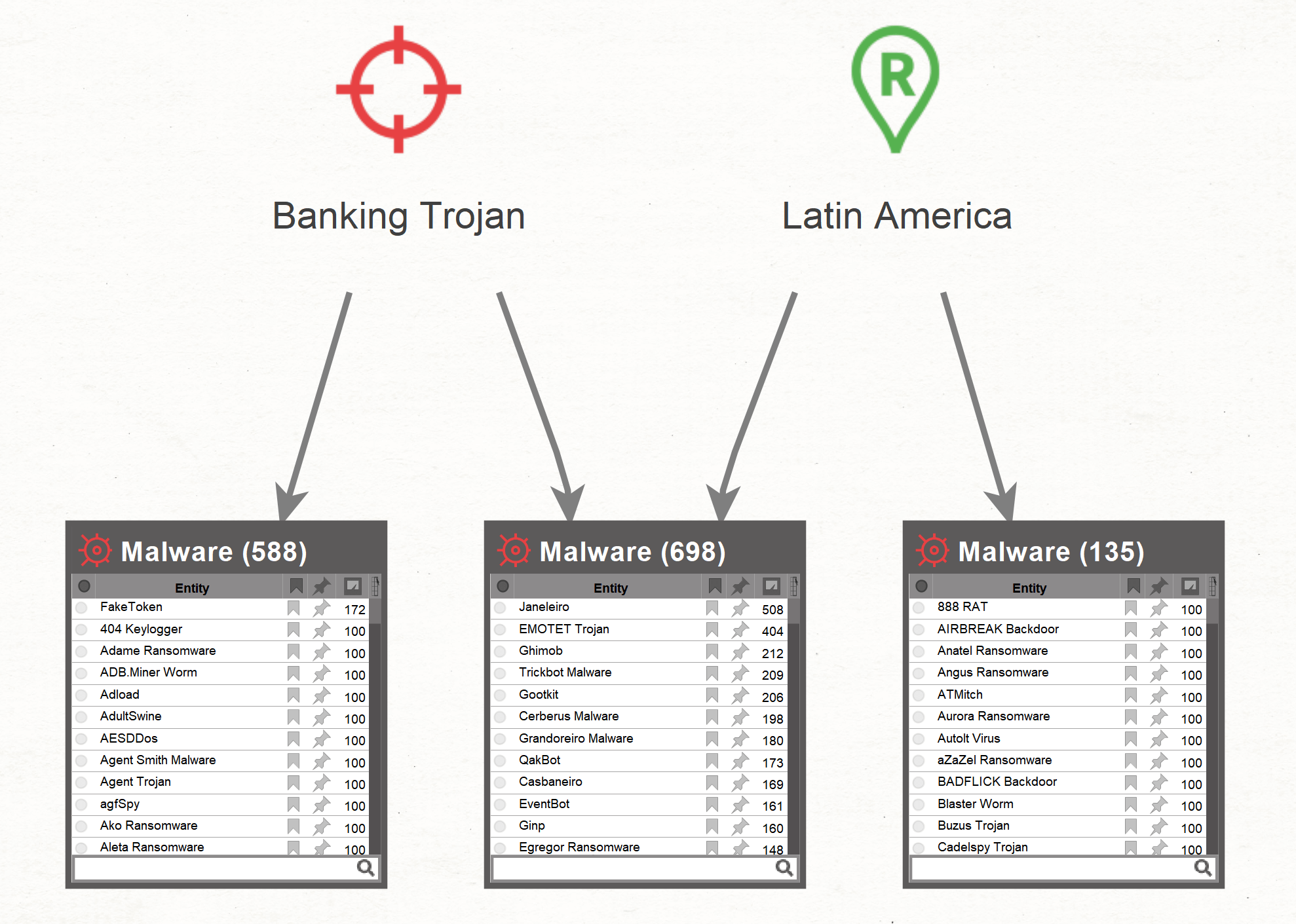
Set the result slider to 4,000 and run the [SB] Malware Transform on the two Entities on the graph.
Because the target of the investigation is banking trojans in Latin America, you can remove the malware not related to both. There is still a lot malware left to investigate (nearly seven hundred malware families!). To refine the results further, you can add important Latin American banking organizations to the graph. Copy and paste the following Entities in the graph:
- Banco del Estado de Chile
- Caixa Economica Federal
- BBVA Bancomer SA
- Banco Bradesco SA
- Banco do Brasil SA
- Grupo Financiero Banorte SAB de CV
- Itau Unibanco Holding SA
- Grupo Financiero Banamex SA de CV
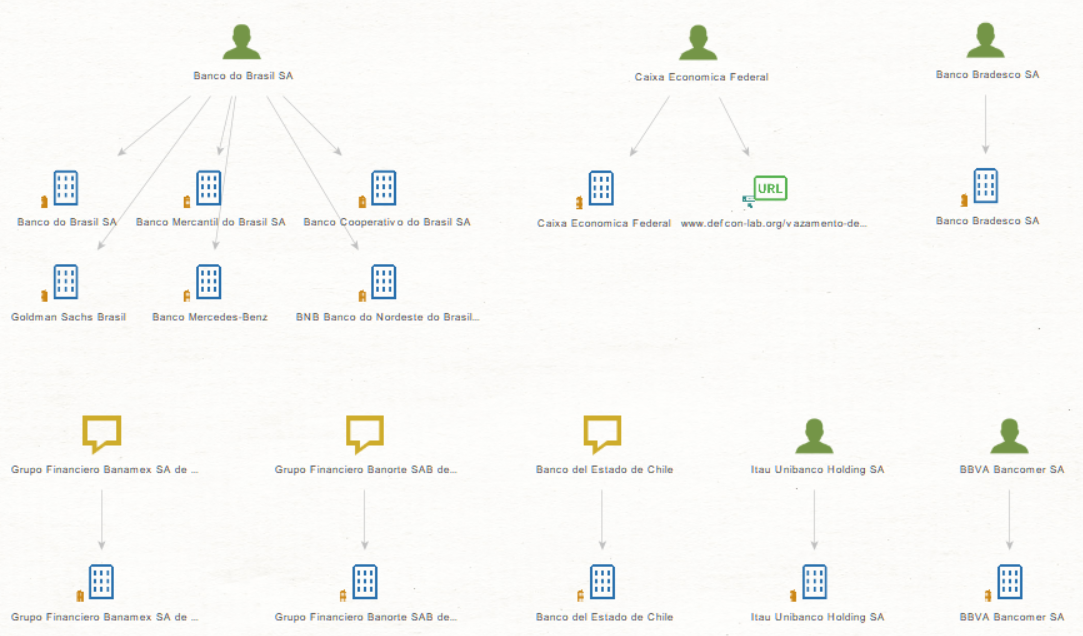
Set the slider result to twelve then run the [SB] Matching Entities Transform. Repeat the same approach as before and keep only the Company Entities.
Select the company Entities that were added and run the [SB] Malware Transform.
The next step will help narrow down the malware that merits further investigation. The goal is to isolate malware related to Latin America, to Banking Trojan and to at least one of the Company Entities on the graph.
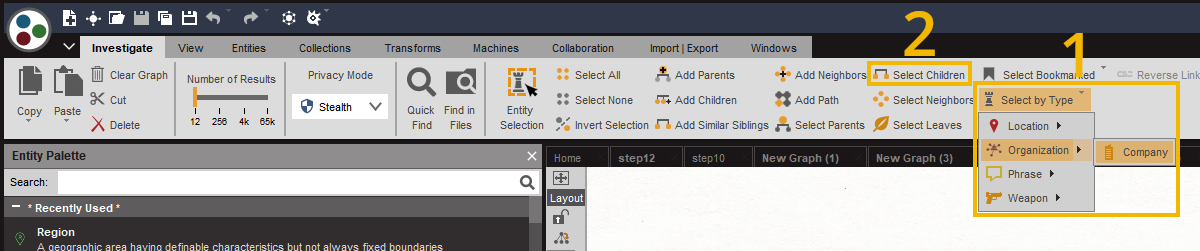
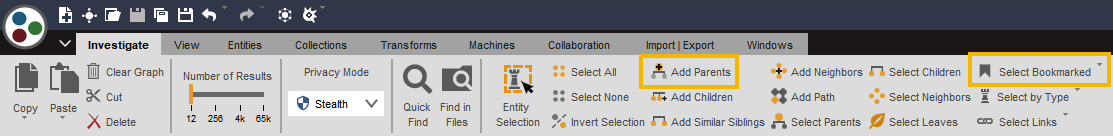
Select the companies on the graph using the Select by Type button (1) and select their children using the Select Children button (2).
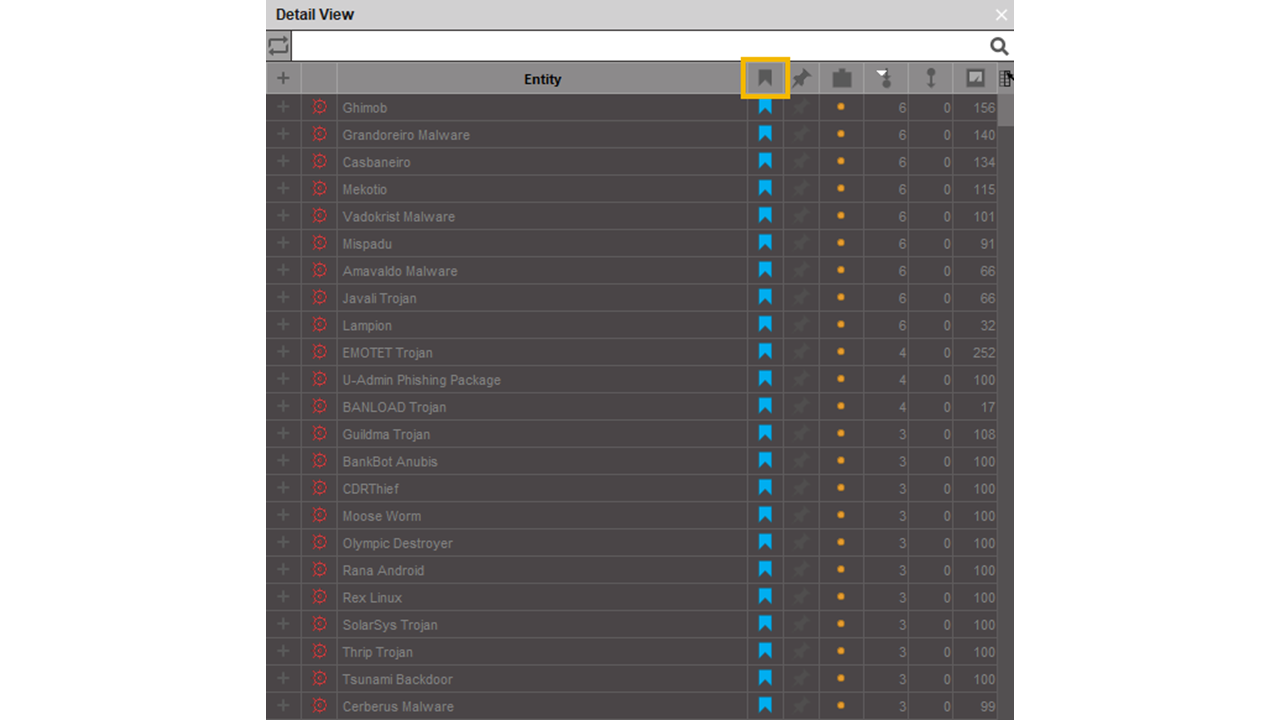
Bookmark the results blue using the Details View panel on the right-hand side of the screen: Click on any Entity in the panel and then use Ctrl+A to select all the Entities in this window. Click on the bookmark icon to set a bookmark color. Click several times to choose which color to set; for this investigation, set it to blue.
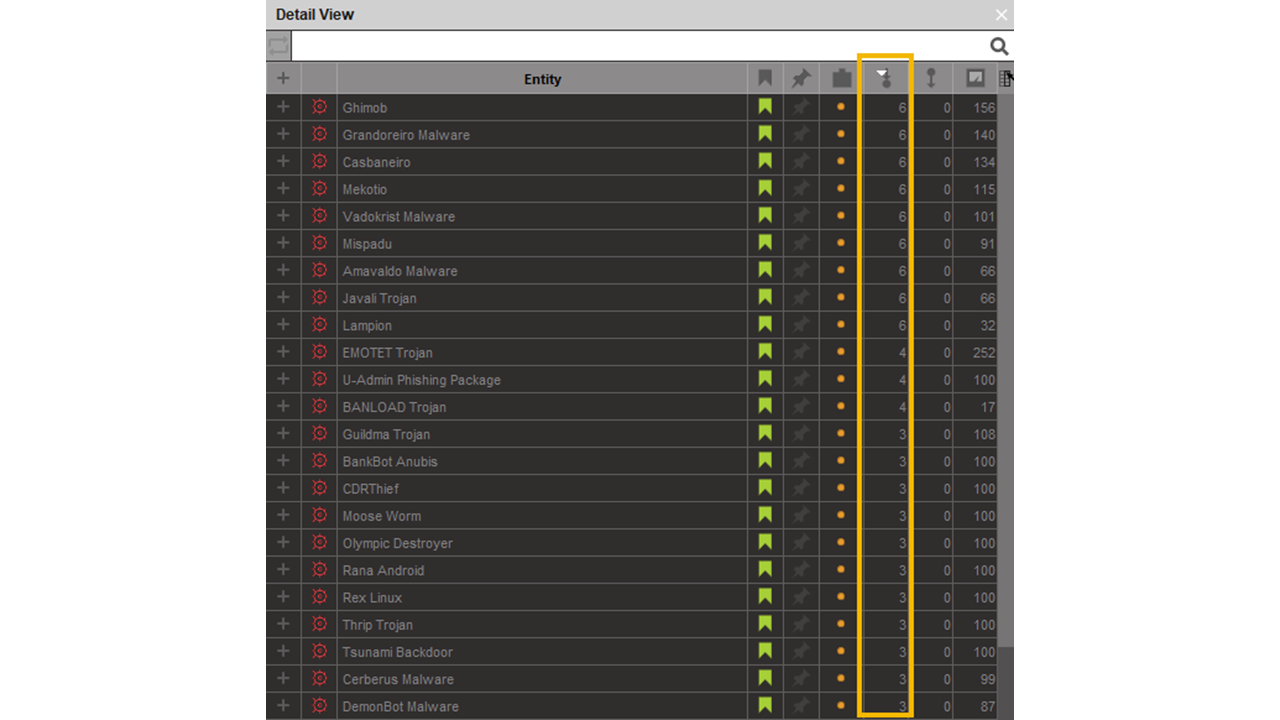
Then select the Latin America Entity and its children using the same button as before. Using the Detail View panel, sort them by bookmark color using the top row button (highlighted by the orange rectangle in the screenshot above). Select the Entities bookmarked as blue and bookmark them in green by clicking the bookmark icon. We now have isolated every malware on our graph related to Latin America, Banking Trojan and at least one Latin American bank. Because they are bookmarked, we have an easy way to select them.
Our next step is to clean up the graph so we can focus on which malware to investigate. Select the Entities bookmarked in green using the Select Bookmarked button above Select by Type. To select the Company, Banking Trojan and the Latin America Entities, add the bookmarked Entities parents to the selection using the Add Parents button.
After doing so, right-click on the graph and copy the selection to a new graph by using the Copy to New Graph button on the lower part of the menu.
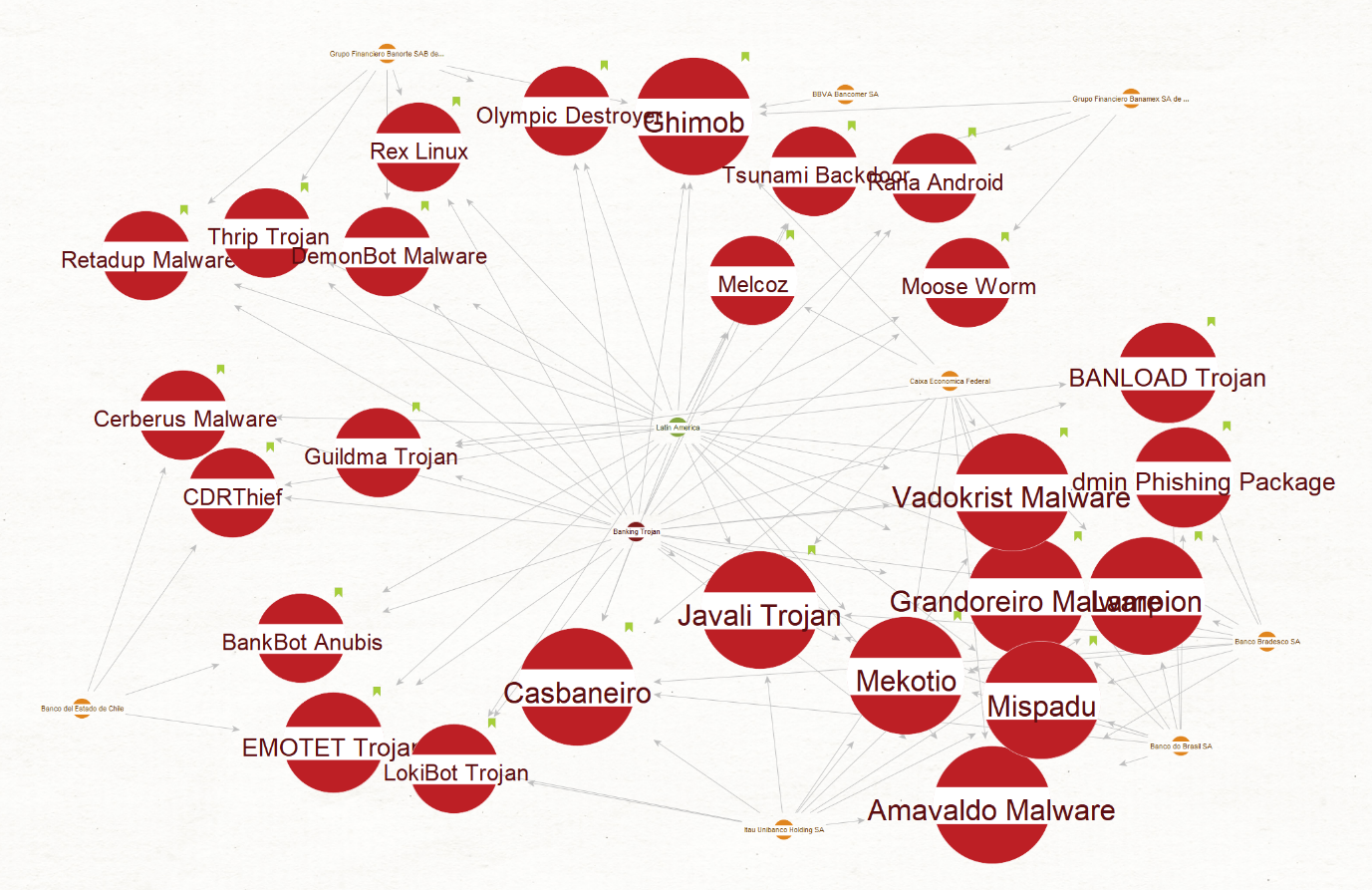
Now 35 malware Entities are left to investigate. To keep the investigation focused on banking Trojans, remove the ransomware results by searching “ransomware” in the search bar. Bring up the search bar by typing. After deleting the nine ransomware entities, the following graph is left:
To prioritize which malware to investigate first, select the Malware Entities in the graph and sort them by incoming link using the Detail View Window. Select the ones with 6 incoming links by pressing down control and clicking across the Detail View window.
From here, it is possible to continue investigating these Trojans by searching for documents using Silobreaker’s Transforms. To prioritize documents containing recent and concise information about malware behavior, origin and use, restrict the search to publications written by Silobreaker’s analysts. These are short summaries of larger publications that contain key information, allowing us to avoid reading through lengthy reports. To bring up these notes in the graph, run the [SB] Search Analyst Notes Transform on the Malware Entities. You can also use the [SB] Search Documents from Threat Publications Transform to search for industry reporting on these entities.
Start Using Silobreaker Transforms in Maltego! 🔗︎
The Silobreaker Transforms are available for purchase for both enterprise and individual investigators. To gain access to these Transforms or for more information, contact our team at support@maltego.com or refer to our Silobreaker Transform Hub page here .
We hope you’ve enjoyed this presentation of Silobreaker in Maltego. Follow us on Twitter and LinkedIn and subscribe to our email newsletter to stay updated on new use cases, tutorials, and product development!


 4.5 rating
4.5 rating