“Decoding Political Violence with OSINT and Lessons from the Frontline”

Get Started with Maltego
Please share your contact information for a personalized session.

Thank you!
We will contact you soon.
In the meantime, check out our product overview
to learn more about the Maltego platform.
Intel 471
By Intel 471 Inc.
Get Adversary, Malware, and Vulnerability Intelligence to support security operation teams.

Intel 471 Transforms for Maltego
Integrating Intel 471 intelligence with Maltego enables proactive security teams with the following industry-leading intelligence:
Adversary Intelligence
- Collections from the Deep and Dark Web (Intel 471 Pro Only)
- Tactical, Operational, and Strategic Adversary Reporting
Malware Intelligence
- Malware reports covering the adversary, detection and infrastructure components of the malware family
- Technical Intelligence
Vulnerability Intelligence
- Trending vulnerabilities within the threat actor ecosystem
Maltego’s ability to provide graphical link analyses allows for security teams to visualize threat profiles to support threat intelligence, threat hunting, patch management, Security Operations Centers, and Incident Response teams.
Typical Users of Intel 471 Data
- Threat Intelligence Teams
- Security Analysts
- SOCs and CERTs
- Fraud Analysts
- Law Enforcement
- Vulnerability and Patch Management
- Incident Response / Threat Hunting

Integration Benefits
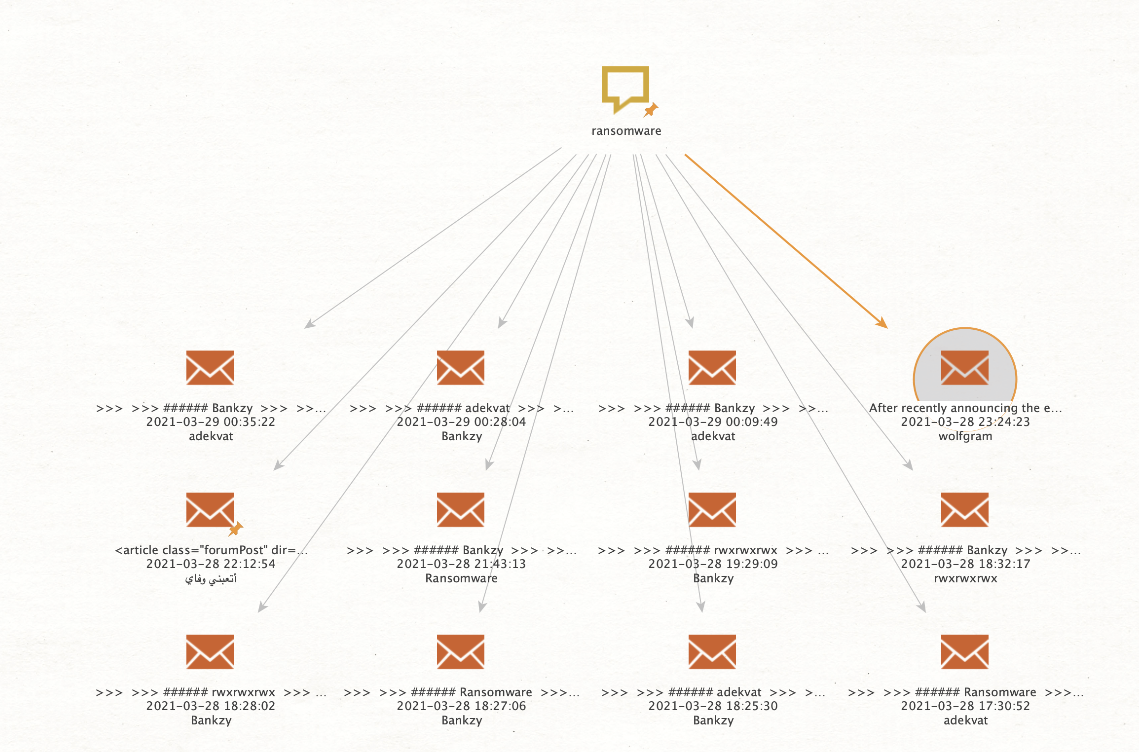
Cybercriminal Underground Insights
The Intel 471 Deep and Dark Web Collections data will enable you to gain an insight into the anatomy of the cybercriminal underground, broken down into three distinct areas:
- Products: Specific malware that is developed and sold to facilitate criminal activity
- Goods: Sensitive data exfiltrated from businesses across the globe
- Services: Bulletproof hosting services, enabling underground criminal activity to continue at an unprecedented rate
Additionally, the data provides you an opportunity to identify indicators and warnings such as the development of attack vectors and intended targets.
Adversary Intelligence
- Time-sensitive insight and operational knowledge of the tactics, techniques, and methodologies of cybercriminals
- Local human intelligence reporting from globally dispersed intelligence operators and native speakers who engage with top-tier cybercriminals on an ongoing basis
- Automated aggregation of relevant cybercriminal activity
Malware Intelligence
- Actively track weaponized and productionized threats that could cause security breaches, revenue loss, and customer harm.
- Gain real-time monitoring of malware activity and command and control infrastructures that’s paired with targeted human analysis.
- Tap Intel 471’s stream of technical indicators, campaign reporting and deep technical insights on top malware families to harden your defenses against the latest threats.
Vulnerability Intelligence
- A lifecycle view of vulnerabilities, including weaponized and productionized threats
- Ongoing monitoring and reporting of key vulnerabilities, prioritized by risk and impact
- Understand how threats are changing, prioritize patches, and reduce your risks over time
Leverage Intel 471 Data for

Threat Actor Interest Levels
Emerging Threat Actor Tools & Techniques
Threat Actor Modeling
Resources
Enrich Threat Intelligence and Criminal Investigations with Intel 471 Transforms and Data Subscriptions
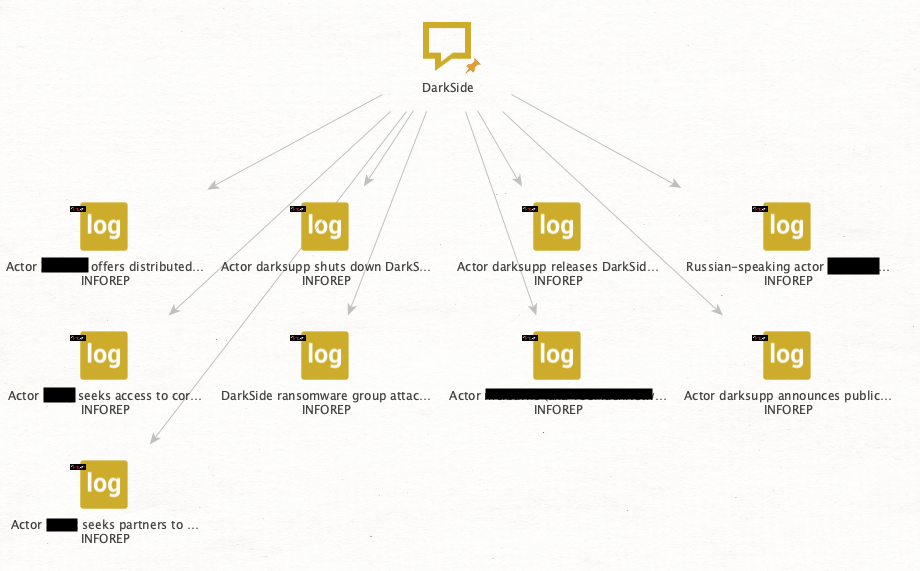
Chasing DarkSide Affiliates: Identifying Threat Actors Connected to Darkside Ransomware Using Maltego & Intel 471
Data subscriptions for Maltego
Simplified Data Access for Maltego Customers
1. Who is Intel 471?
2. What can I do with Intel 471 data?
3. Can I use it with the Community Edition of Maltego?
4. How can I access or purchase Intel 471 data to use in Maltego?
5. What is a Transform Run?
6. Are there any other requirements to get Intel 471 data access?
For Intel 471 data access, you will need:
- A valid commercial Maltego license edition (Maltego One, Classic or XL)
- An Intel 471 API key or a Maltego Intel 471 data subscription
In order to use Maltego data subscriptions, you must first agree to the following terms and conditions:
- Maltego Technologies License Agreement
- Maltego Technologies Data Integration Terms & Conditions
- Intel 471 Terms of Use
Furthermore, each data subscription purchase is subject to a Know Your Customer (KYC) vetting process according to the respective terms of use for the data in question. Due to the often-sensitive nature of data, access is generally reserved for vetted organizations with legitimate use cases commonly associated with organizations. Thus, after placing an order request in the web-shop or via our sales team, customers need to undergo a KYC vetting process before the purchase can be completed and they can make use of the data subscription.
7. Who can purchase the Intel 471 data subscriptions for “Internal Security” teams?
8. Who can purchase the Intel 471 data subscriptions for “Service Providers?”
Contact
Reach out to us to learn more about this data integration and how to access it.
About Intel 471
Intel 471’s Cybercrime Intelligence provides in-depth coverage and tracking of sophisticated, financially motivated cybercriminals, hacktivists, and other threats from across the globe that target organizations, their customers, employees, and suppliers. Intel 471 provides the intelligence to arm organizations with deep, actionable insights into these threat actors, their motivations, tools/malware, techniques, and alliances – and, ultimately, provides the information and context required to understand and stay ahead of the threat.
For more information, visit https://www.intel471.com.


 4.5 rating
4.5 rating