We are thrilled to announce two significant additions to our Transform Hub: utilities for working with STIX 2.1 and a STIX-powered integration for OpenCTI. These tools mark a crucial step for Maltego in our adoption of threat intelligence standards and our efforts to seamlessly integrate with the tools that threat intelligence researchers, SecOps analysts, and other Cybersecurity professionals rely on daily.
These integrations were created in close cooperation with ANSSI, the French National Cybersecurity Agency, who contributed a set of open-source Transforms, the development of which Maltego subsequently supported. Maltego’s contributions to this project are available under an open-source repository on Github, which you can access here: amr-cossi/maltego-stix2 and amr-cossi/opencti-maltego.
Understanding STIX 2.1 🔗︎
Developed by OASIS, STIX (Structured Threat Information eXpression) is a standardized language and serialization format used to exchange Cyber Threat Intelligence. Simply put, STIX tells you how to assemble the different pieces of information that your organization collects to create Intelligence documents.
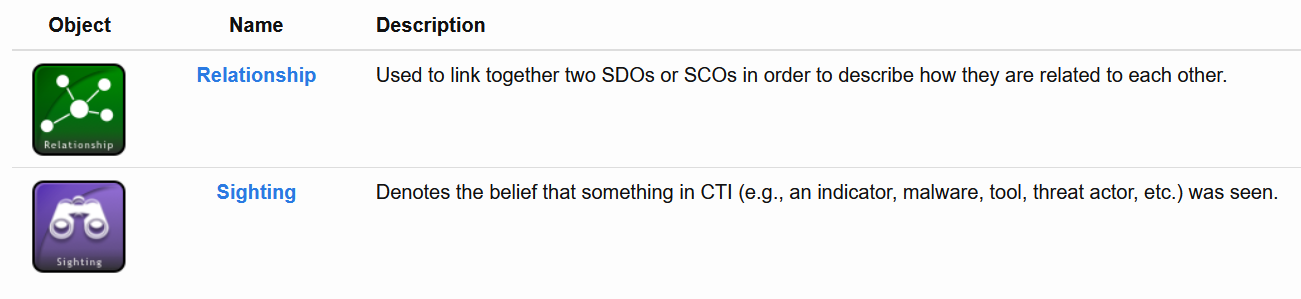
Most information in a typical threat intelligence feed/source can be expressed and serialized in a standardized and machine-readable format using STIX. Below are few examples of STIX2 Objects that have now been brought into Maltego.
STIX Domain Objects (SDOs) 🔗︎
STIX Relationship Objects (SROs) 🔗︎
Adapting STIX into Maltego 🔗︎
In total, we adapted 40 object types from STIX into the standard Maltego ontology, along with over 100 utility Transforms for converting standard Maltego Entities into STIX data and pivoting STIX objects into their property relationships.
The new STIX Entity types are effectively subsumed into our ontology of standard Entities, such that, for instance, a STIX 2 Vulnerability Entity can also be consumed by existing Maltego Transforms that operate on CVE Entities, or similarly, STIX Threat Actors can be interpreted as Organization Entities in other Transforms. In many cases, this mapping is straightforward: all standard observables like STIX IPv4 addresses, hashes, domains, URLs, etc., are also compatible with their direct Maltego counterparts.
Flagship STIX Support in OpenCTI 🔗︎
OpenCTI is a Threat Intelligence Platform (TIP) that was developed by the French national cybersecurity agency (ANSSI) and the CERT-EU (Computer Emergency Response Team of the European Union) to facilitate ANSSI’s interactions with its partners. Today, OpenCTI is developed and maintained by the non-profit organization Luatix (https://www.luatix.org/en/).
It was later released as an open-source tool aimed at helping organizations to structure, store, and organize information about Cyber Threats. OpenCTI enables you to go beyond only technical (TTPs and observables) and non-technical information (suggested attribution, victimology).
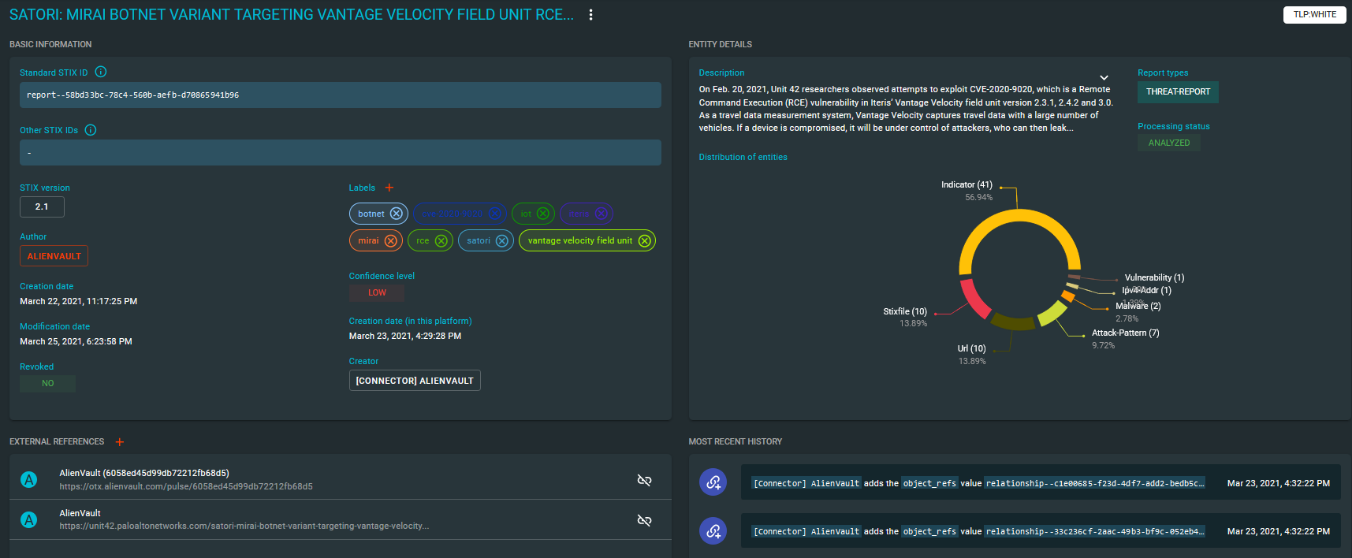
OpenCTI itself has connectors to many threat intelligence sources (AlienVault OTX, MITRE ATT&CK, custom integrations, etc.), which allow external threat intelligence data to be ingested into the platform automatically where it is structured according to the STIX specification. In effect, the result is a highly interconnected knowledge graph of threat intelligence that can be queried and explored in powerful ways by tools such as Maltego.
Our new integration for OpenCTI enables full access to this underlying graph of data, allowing you to query, explore and visualize it directly in Maltego, making full use of the newly introduced STIX 2.1 Entities.
Many organizations run their own deployment of OpenCTI, which our Transform Hub integration can connect to if these are internet-facing. However, more often than not, organizations may instead need to deploy these Transforms as an on-premise integration using the available open-source code. Get in touch with Maltego Support (support@maltego.com) if you would like us to help you get started.
The Importance of STIX 2 and OpenCTI 🔗︎
Threat Actors have been steadily improving their Techniques and Tactics; only by understanding their intent, capabilities, motivations and TTPs can we make sure to keep one step ahead of them.
The OpenCTI Transforms and STIX2 Utilities enable Maltego users to bring Threat Intelligence data from an OpenCTI instance into Maltego, allowing them not only to perform tailored investigations on advanced threats, exploits, and zero-day threats but to react against them more efficiently.
If you found this overview of STIX 2.1 and OpenCTI interesting, we hope you enjoy Part 2 of this announcement, where we will use these new tools to investigate a specific threat actor to build an understanding of their activities and footprint.