Are humans creatures of habit? When you observe the people around you, it becomes clear that each person develops a unique adult personality, characterized by distinctive habits and behaviors.
Viewed from a broader perspective, these behaviors often seem repetitive, highlighting our natural inclination toward certain activities, performed in specific ways. In the investigative world, these predictable patterns can be a valuable source of information and may be part of what is known as a pattern of life analysis.
In this blog, we will explore ways in which investigators can understand the habits or behaviors of their persons of interest, using the example of analyzing fitness-tracking device data in Maltego. For this investigation, we will focus on tracking data from the Strava application that have allegedly led to exposing the location of an assassinated Russian submarine commander, Stanislav Rzhitsky.
What Is Pattern of Life in OSINT? 🔗︎
Pattern of life analysis aids OSINT investigators in interpreting large quantities of data about a target to understand their habits and behaviors. This then helps discern patterns that help reach informed conclusions and complement person of interest investigations.
Alternatively, by noticing and then investigating unusual or curious behaviors, you can uncover the underlying causes that will lead to identifying the person involved in these actions.
If you want to know what data sources you can use for your pattern of life analysis, download the infographic below.
Why Use Pattern of Life in OSINT Investigations? 🔗︎
Regardless of the approach, there are several reasons why pattern of life analysis can be beneficial in investigative work.
1. Gaining insights into anonymized datasets: By applying open-source intelligence (OSINT) and signals intelligence (SIGINT) methodologies to metadata, investigators can generate intelligence from communications without needing access to the content of those communications.
INVESTIGATOR EXAMPLE Imagine you have access to a database of an online delivery service like Uber Eats that was leaked, and you see there is a pizza order every second Tuesday of the month to an address of a government building. This might give you a hint that there is a scheduled monthly meeting of a team. Imagine all those orders were made by the same phone number, which you can find within an OSINT database linked to an analysis department.
2. Identifying suspicious activities: Pattern of life analysis enables investigators to establish a baseline of “normal” or repeated activities. Once this baseline is set, it becomes easier to spot unusual activities.
INVESTIGATOR EXAMPLE There is an increase in social media posts about luxury items and vacations from a suspect usually posting about a modest lifestyle. This change coincides with large, unexplained bank transfers. By correlating these posts with financial data, you identify potential financial fraud, using the suspect’s deviation from normal behavior as a key indicator of suspicious activities.
3. Collecting predictive intelligence: If we know what the usual patterns of behavior of targets are, we can make pre-emptive operational decisions.
INVESTIGATOR EXAMPLE For instance, consider the analysis of airline ticket purchases made by known drug traffickers. By identifying specific patterns in their travel habits, border surveillance investigators can strategically decide which flights to monitor more closely or intercept.
How OSINT Investigators Can Use Data from Fitness-tracking Devices? 🔗︎
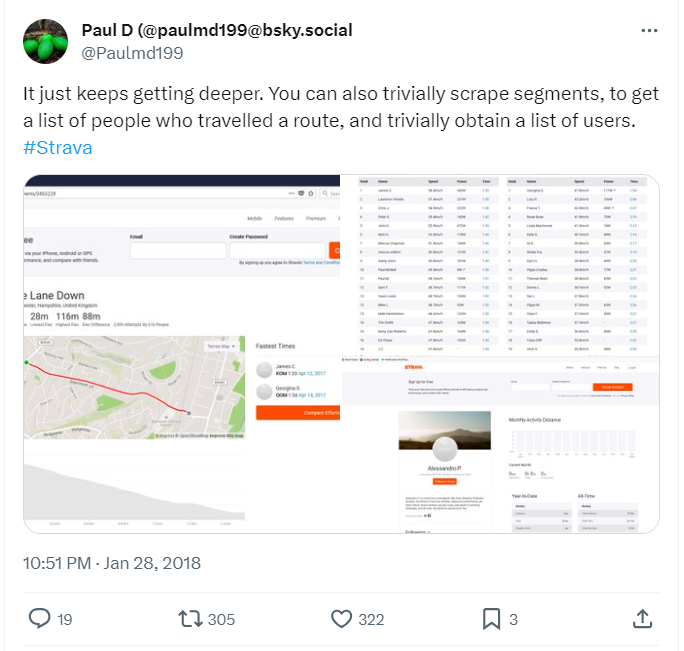
One example of a database that can be utilized for a pattern of life analysis is fitness-tracking devices. By exploring data shared via these applications, you may be able to track commonly used running routes and identify the frequency of their use, as well as discover connections between people using the same application.
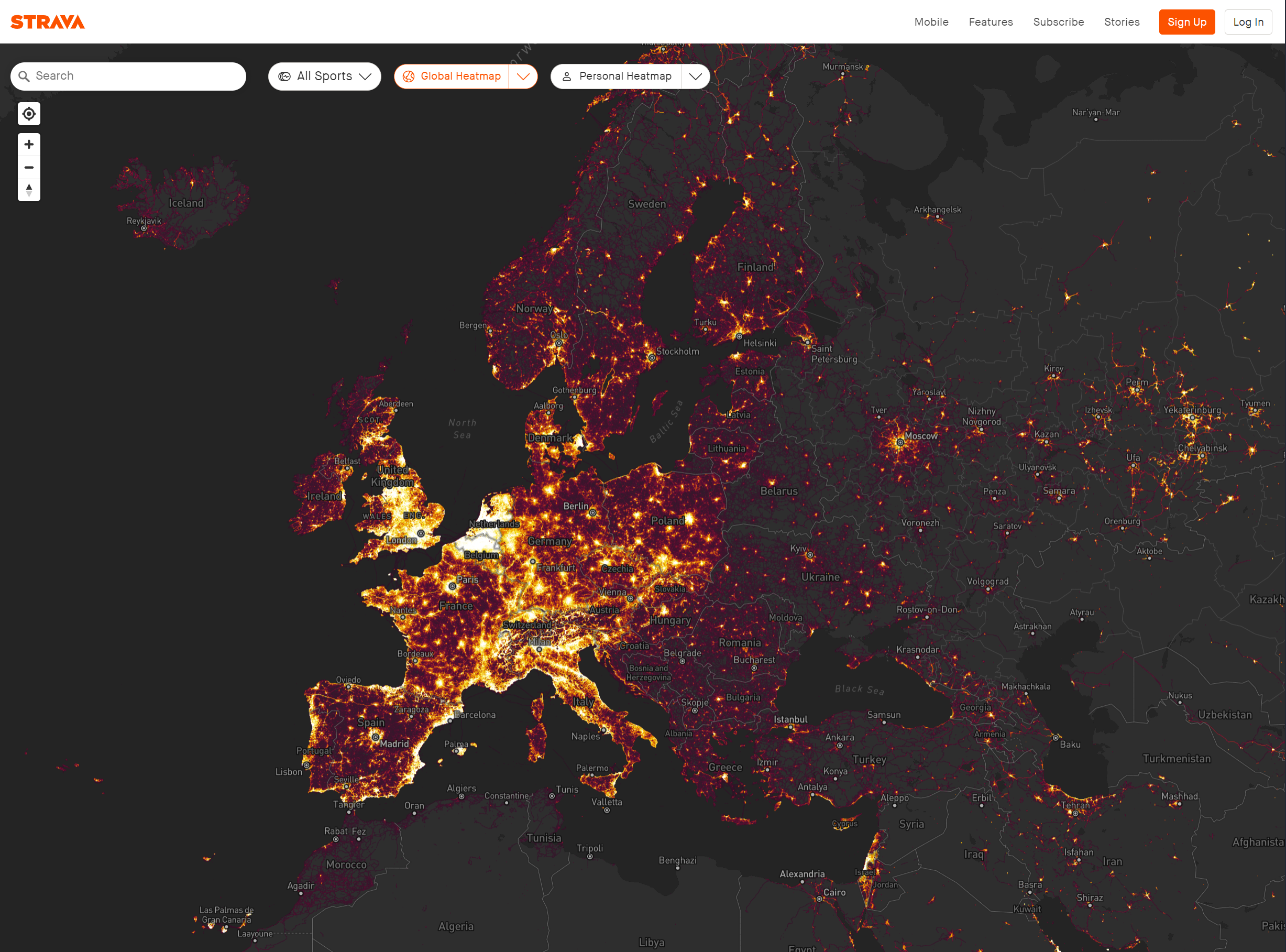
Source: Strava
Let’s consider the example of the heatmap feature in the Strava application, which tracks running and cycling routes and displays them on an online global heatmap.
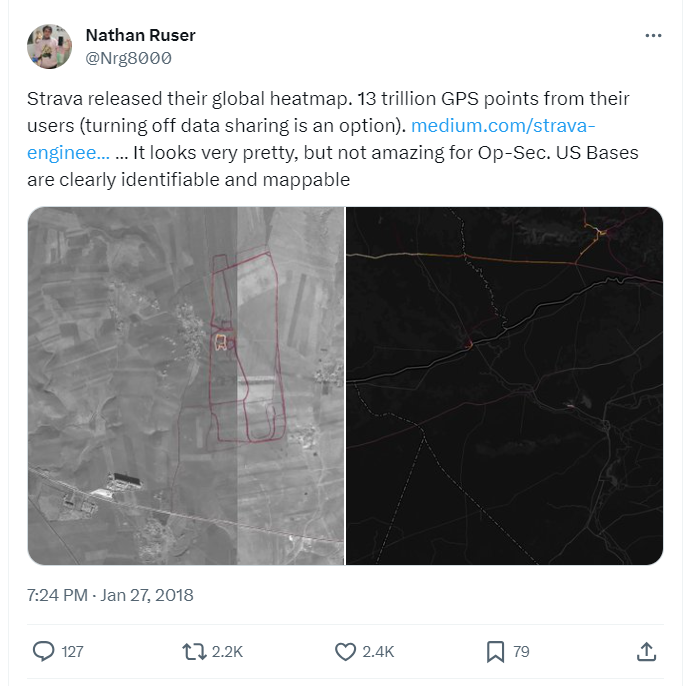
However, from an investigator’s perspective, what appears to be harmless and inquisitive behavior could actually help in uncovering patterns of user activity. Sometime after releasing this feature, press and social media commentators noted that Strava’s heatmap could have been used to identify military deployments.
Source: Wired
This occurred because the routes and performance of soldiers stationed at certain locations were tracked in the fitness application. Consequently, this incident inadvertently compromised their operational security (OPSEC), a topic widely commented on across popular social media channels and news websites.
How to Conduct a Pattern of Life Analysis in Maltego? 🔗︎
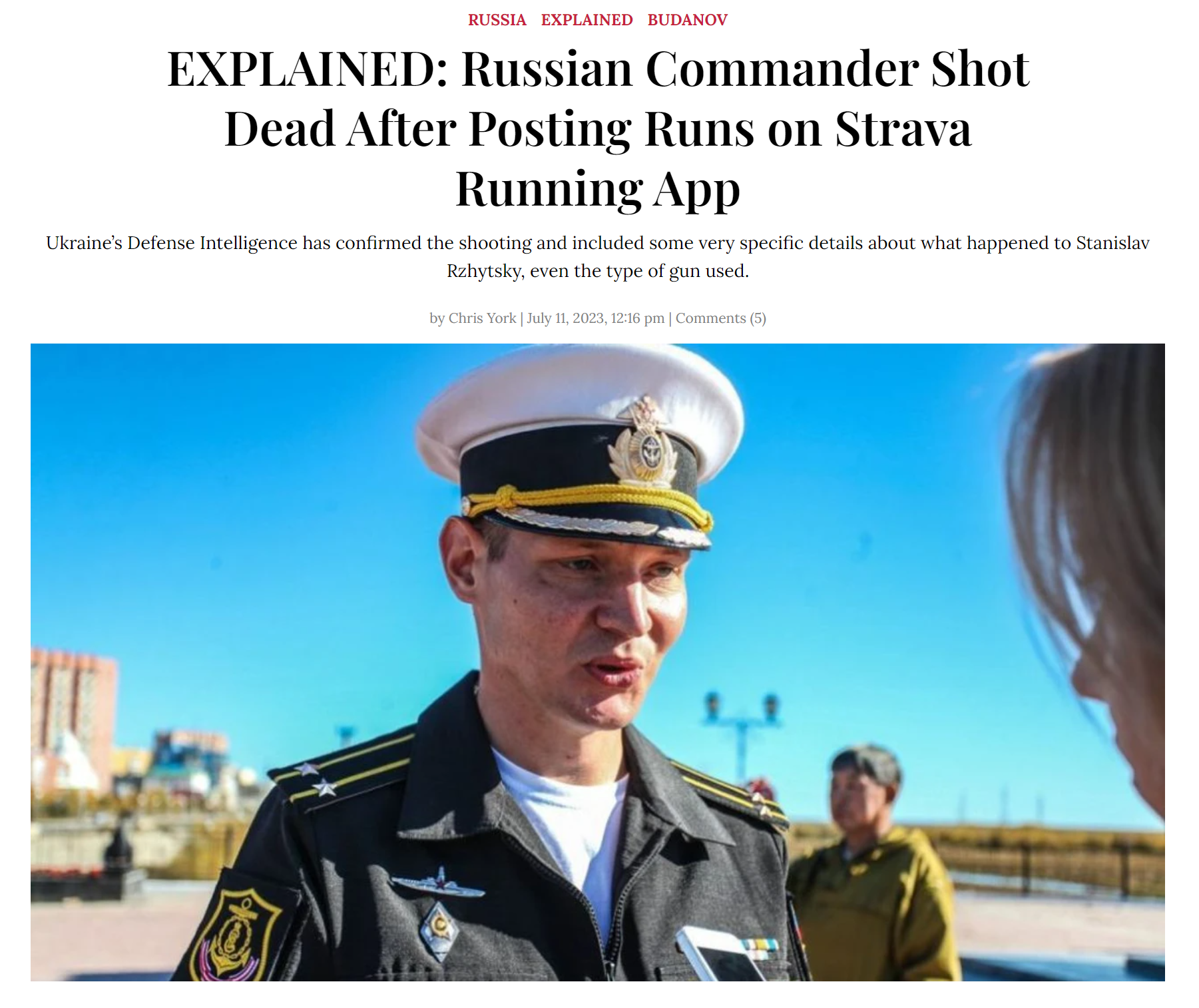
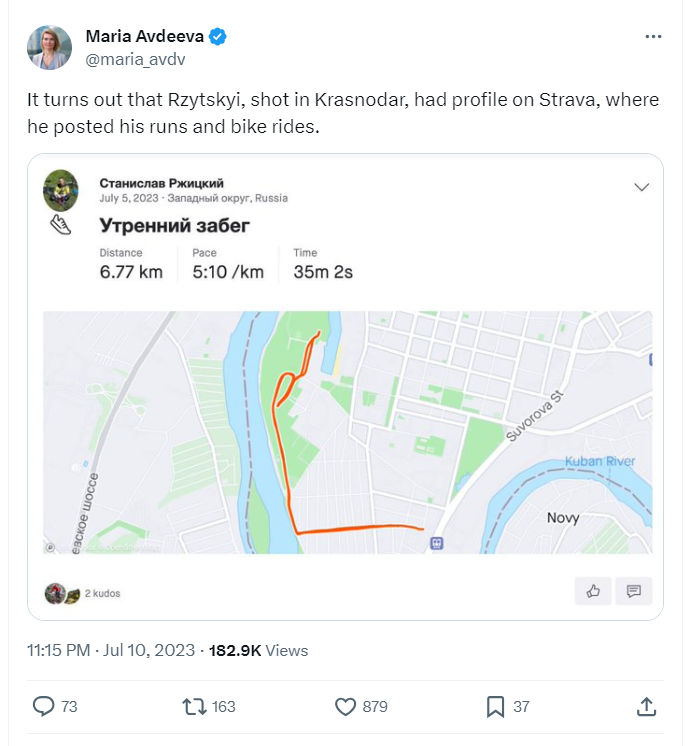
Similarly, the media reported that data from a fitness application could have compromised the whereabouts of a Russian submarine commander, Stanislav Rzhitsky, who was assassinated in 2023 while running. Allegedly, his assailant tracked his daily routes in the fitness application.
We will focus on this case in more detail in our whitepaper to illustrate how shared fitness tracking data can be utilized in an investigation.
Target Information 🔗︎
Stanislav Rzhitsky is believed to have been targeted in retaliation for a Kalibr missile strike in Vinnytsia, Ukraine. His death is thought to be linked to his use of a jogging application that uploaded data to the popular fitness platform Strava. His profile, which was left open to public view, detailed some of his frequently taken routes. Authorities suspect that the assassin used his fitness tracking data to locate him.
Source: Kyiv Post
Goal of the Analysis 🔗︎
The goal is to explore how the data shared by Stanislav Rzhitsky on his Strava app could have been leveraged by the assassin to locate him.
Source: Kyiv Post
Download Whitepaper 🔗︎
Our whitepaper will provide a demonstration of the initial discovery of our person of interest, followed by an illustration of a pattern of life analysis in Maltego.
With this guide, we aim to assist law enforcement agencies in their day-to-day investigations and raise awareness among other organizations about the importance of physically protecting their personnel by preventing the disclosure of sensitive information in public and enhancing their OPSEC. Such information could otherwise be used by individuals with illicit intentions to target them.
You can download the guide down below for a full pattern of life analysis in Maltego.
Download the resource
What Other Data Sources Can OSINT Investigators Use for Pattern of Life Analysis? 🔗︎
While fitness tracking data is one example you can use to complement your investigation of a person of interest with a pattern of life analysis, there are numerous other sources you should consider that may fit your use case.
Download the infographic to find out now.
Download Infographic 🔗︎
If you are interested in more guides on cybercrime investigations, you might want to explore our blog on person of interest investigations using OSINT and Maltego, which includes a ready-to-replicate workflow. Alternatively, you could watch a webinar on investigating FSB agents’ phone numbers to learn how to leverage breached data in your investigations.
Don’t forget to follow us on Twitter, LinkedIn, and Mastodon, and sign up to our email newsletter to stay updated on the latest tutorials, use cases, and webinars!
Happy Investigating!
References 🔗︎
About the Author 🔗︎
Carlos Fragoso
Carlos is the Principal Subject Matter Expert and Lead Instructor at Maltego with over 20 years of professional experience in information security: Incident response, digital forensics, threat intelligence, and threat hunting. A curious and passionate investigator working with big companies and LEAs to tackle cybercrime around the world (Europe, Middle East, LATAM) SANS Institute Instructor.


 4.5 rating
4.5 rating