The term Open-Source Intelligence (OSINT) has become so popular and marketable these days, chances are you have most definitely seen mentions of it somewhere. One might encounter it when comparing different data sources, when learning about investigative techniques, or as a category of data collection and analysis tools.
While all of its different connotations may be correct, at its core, OSINT is in fact a specific intelligence collection discipline used by the intelligence community. OSINT, HUMINT, SIGINT, and the other disciplines are often referred to as “INTs” as a shorthand for them sharing a common suffix.
In this article, we will explain what these different disciplines are and how they can be utilized. But first, we will build out a base to work from by exploring what intelligence means.
Table of Contents 🔗︎
What is Intelligence? 🔗︎
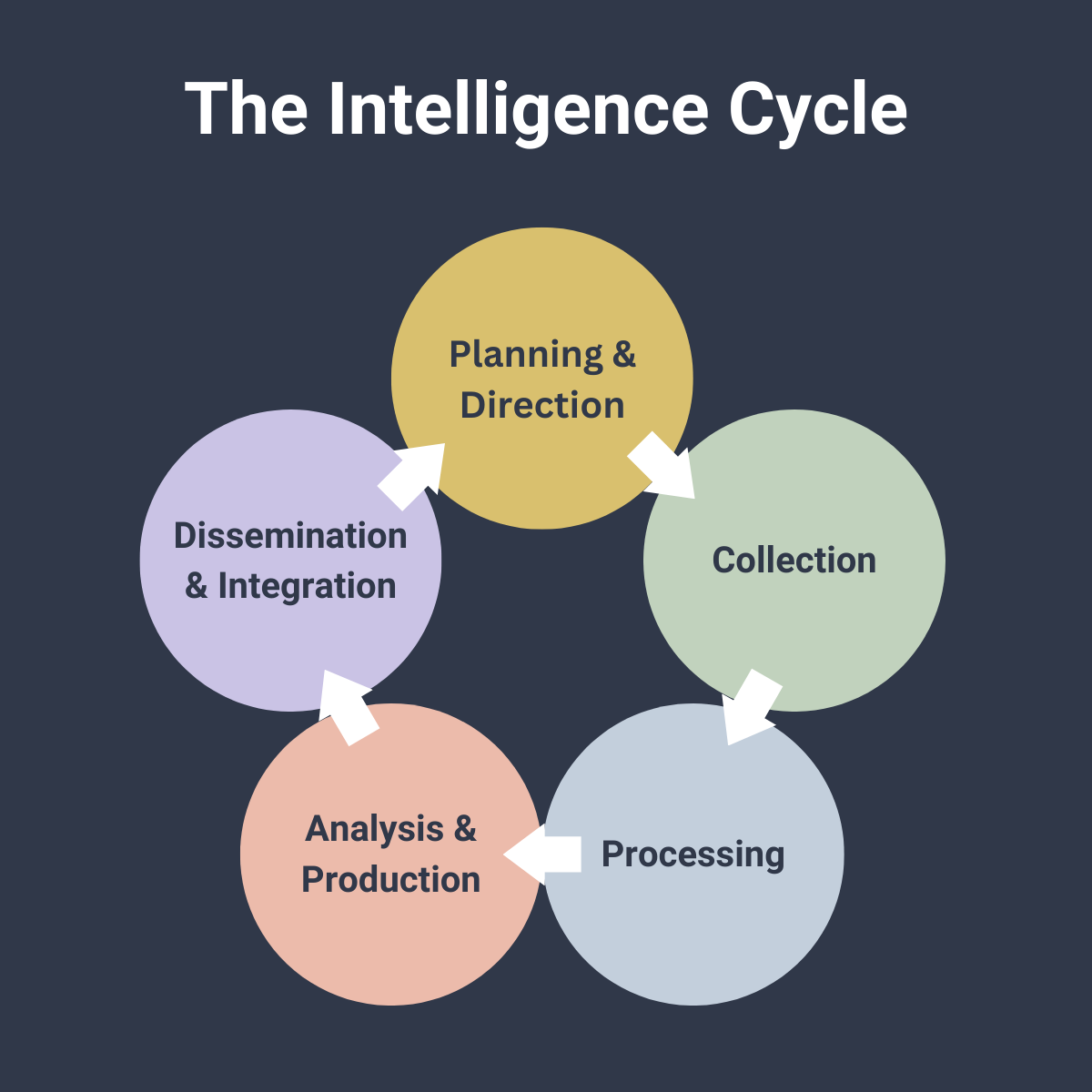
Intelligence is considered to be the product of the collection, processing, and analysis of raw information. As a product, intelligence is developed and made available using the intelligence cycle which, in its most standard model, is made up of 5 steps:
- Planning and Direction (also known as Requirements)
- Collection
- Processing
- Analysis and Production
- Dissemination and Integration
Even though this model is most often found in literature tied to governmental agencies, it describes a standard process that can be applied independently of the analyst’s individual context, be it civilian, law enforcement, or even military intelligence.
Once produced, intelligence is then consumed by “intelligence customers” to drive their decision-making. Typically, these customers are individuals in charge of, or supporting, ongoing actions such as incident and emergency response, strategy and policy making, and even national security decisions.
The Different Levels of Intelligence 🔗︎
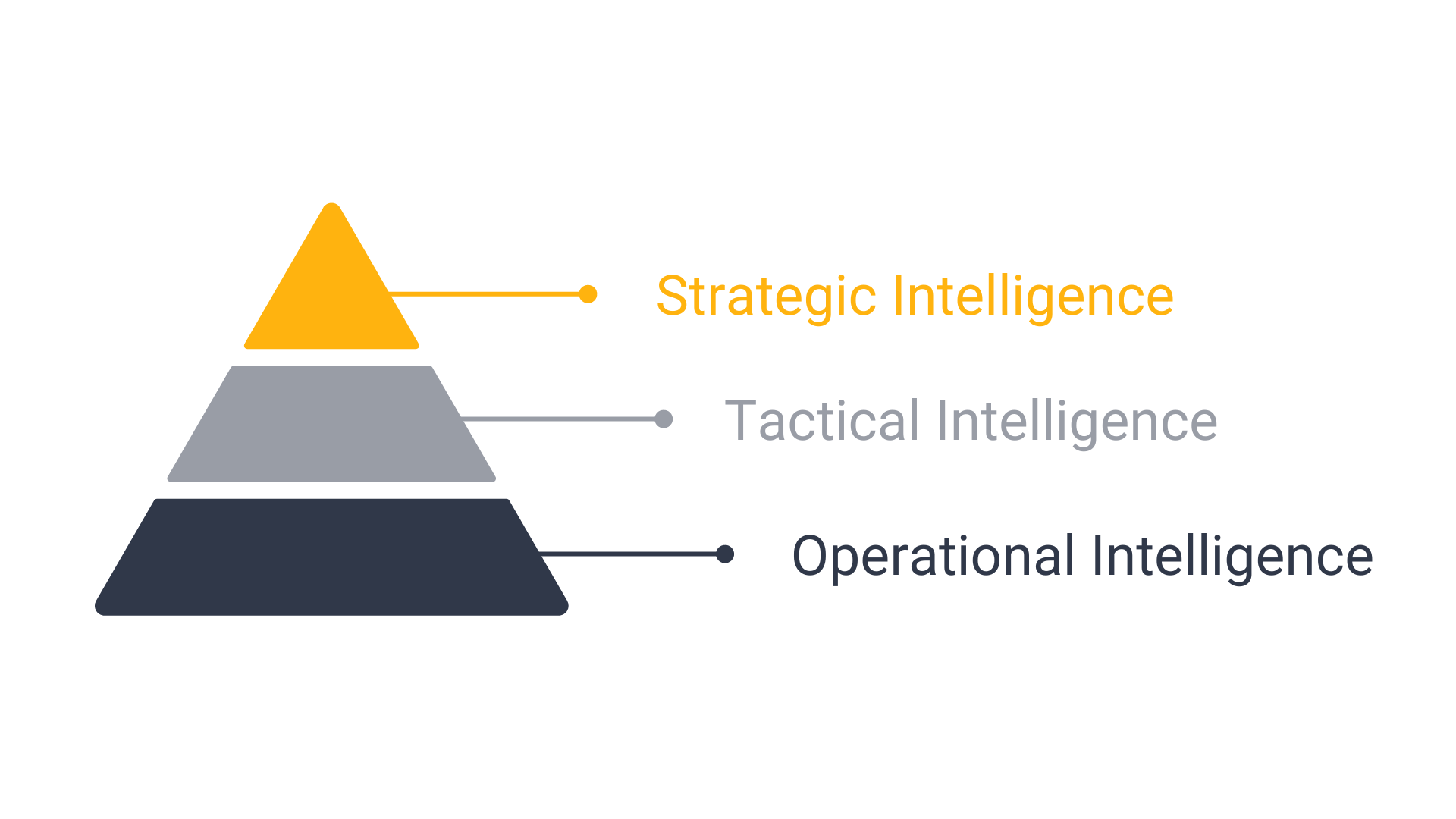
Because intelligence can serve different purposes and audiences, it has been classified into three different levels: Strategic, Tactical, and Operational. These levels have a hierarchical nature to them, with strategic intelligence situated at the top and operational intelligence at the bottom.
Strategic intelligence is forward thinking, heavily reliant upon estimations and is used to look at long-term trends. As such, it is often produced by analysts with profound subject-matter expertise and high adaptability.
Tactical intelligence provides an evaluation of a rival’s current capabilities, with a focus on their strengths, weaknesses, and intentions. This type of intelligence allows an effective allocation of resources, appropriate planning, and timely engagement with the adversary.
Operational intelligence requires real time, or near real-time information to be produced, for it is used in day-to-day activities and decision making. As such, it is mostly obtained from technical sources and has a short Time To Live (TTL).
Although knowing what level of intelligence is needed will help make it more relevant and actionable for the end user, their hierarchical nature allows them to feed off and impact each other. In fact, a comprehensive analysis will be comprised of intelligence from all levels.
Given that intelligence is used to drive decision-making, and decisions are only as good as the data that supports them, collection thus becomes one of the pillars of intelligence-led activities. As such, it is highly relevant to understand the scope and capabilities of each of the intelligence collection disciplines.
The Intelligence Collection Disciplines 🔗︎
As previously mentioned, OSINT is but one of the established intelligence collection disciplines. It’s worth mentioning that some of the disciplines – or their sub-disciplines – are of exclusive use for government institutions, particularly those within the military and special intelligence domains. There is no standard list of intelligence collection disciplines, however, there is consensus within the U.S. intelligence community about the existence of five main disciplines:
- OSINT
- HUMINT
- SIGINT
- GEOINT
- MASINT
Open-Source Intelligence (OSINT) 🔗︎
OSINT is produced from publicly available information that is acquired through legal means such as official requests, observation, and acquisition. Even though OSINT has gained popularity with the advent of internet and digital media, it can be produced from information found in a wide range of formats and sources including the internet, commercial or public databases, newspapers, radio, television, etc.
While it is an industry term developed to fuel further product segmentation, Social Media Intelligence (SOCMINT) can be considered as a sub-discipline of OSINT. SOCMINT allows the monitoring of social media platforms, such as Facebook and Instagram. This includes the monitoring of content, messages, and other relevant data.
If you wish to gain a deeper understanding of OSINT and its distinction from Web intelligence (WEBINT), consider reading our dedicated article which you can find here.
Human Intelligence (HUMINT) 🔗︎
HUMINT is derived from human sources. The public perception of this discipline is usually related to clandestine activities – think undercover missions and spies. Yet, the reality is that most of the sources used these days are less exciting and much more overt in nature. In fact, most of the raw information used to produce this intelligence is collected through interviews conducted with witnesses, suspects, and Persons Of Interest in an investigation, for example.
Interestingly, HUMINT is one of the oldest forms of data collection. It remained the primary intelligence source for governments until the technological revolution of the late 20th century.
Signals Intelligence (SIGINT) 🔗︎
SIGINT is produced from the interception and exploitation of signals. It is important to note that signals intelligence can be performed from different platforms, including ships, aircraft, and ground sites. These platforms or facilities can even monitor transmissions from terrestrial facilities and satellites. SIGINT is comprised of three sub-disciplines:
- Communications Intelligence (COMINT), which targets voice or text messages in their different formats, as well as teleprinter and Morse code traffic. In other words, it intercepts communication transmissions using cryptographic methods and device-to-device transmissions.
- Electronic Intelligence (ELINT), which intercepts and analyzes non-communication transmissions made by radars and other electromagnetic radiation. The instruments used are almost exclusively property of specific governments, making them highly classified and protected sources.
- Foreign Instrumentation Signals Intelligence (FISINT), which can intercept the telemetry of a weapons system or space vehicles. The intelligence produced allows the end user to determine the performance of said systems and vehicles.
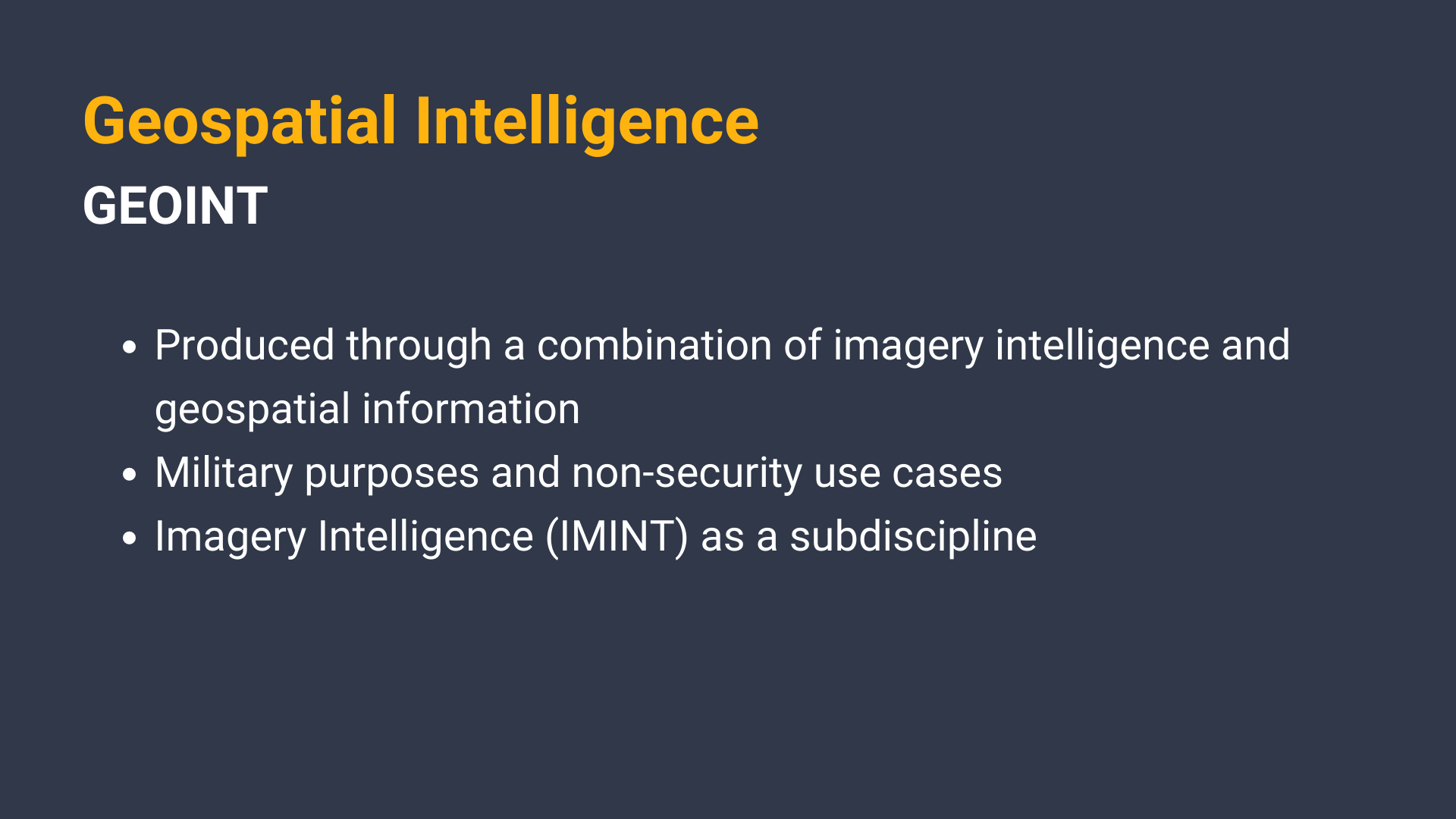
Geospatial Intelligence (GEOINT) 🔗︎
GEOINT is produced through a combination of imagery intelligence and geospatial information. In other words, it is information acquired through the analysis of images and data associated with a specific location. It can be used, not only for military purposes, but also for non-security use cases that track geographic changes and features (soil erosion, agricultural land usage, etc.).
While the Office of the Director of National Intelligence identifies Imagery Intelligence (IMINT) as a discipline, it is more often considered as a subdiscipline of GEOINT. IMINT can be derived from sources such as visual photography, infrared, radar sensors, lasers, and electro-optics, as well as imagery gathered via satellite.
Nowadays, more nations have access to IMINT due to the surge in space-based imagery systems. However, quality is a prevalent issue that can only be addressed with the use of highly sophisticated technology to combat the effects that natural phenomena such as adverse weather and light conditions may have on imagery products.
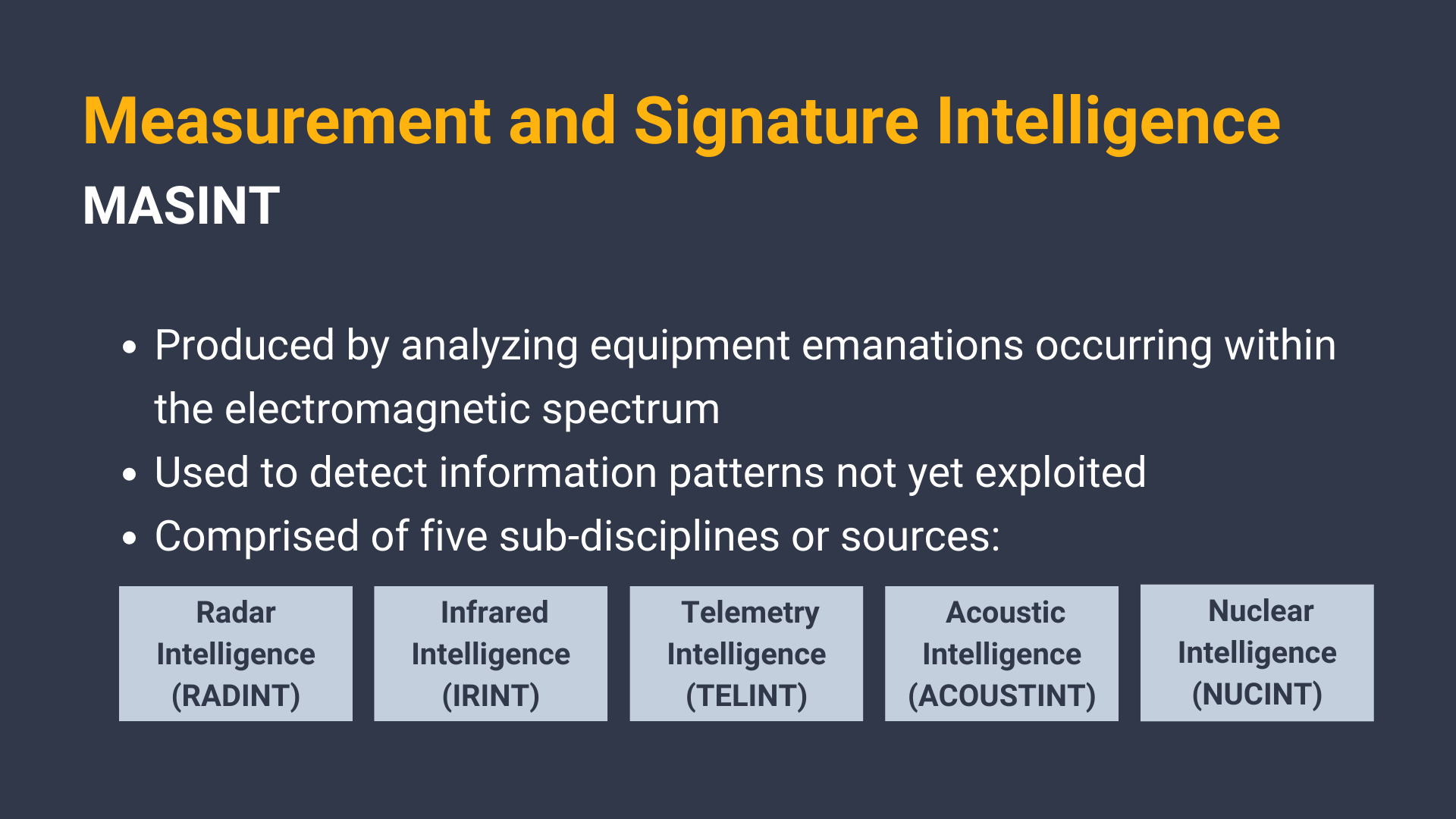
Measurement and Signature Intelligence (MASINT) 🔗︎
MASINT is produced by analyzing equipment emanations occurring within the electromagnetic spectrum. MASINT is used to detect information patterns not yet exploited by other systems and is comprised of five sub-disciplines or sources:
- RADINT, or Radar Intelligence
- IRINT, or Infrared Intelligence
- TELINT, or Telemetry Intelligence
- ACOUSTINT, or Acoustic Intelligence
- NUCINT, or Nuclear Intelligence
What is the Relevance? 🔗︎
There might be natural overlaps between the different types of intelligence collection disciplines, where one serves as an enabler for the others. And, while Maltego is an OSINT tool, our end users operating within the intelligence community are rarely conducting their analyses in a vacuum. Thus, their intelligence products often incorporate more than one type of collection discipline.
A better understanding of the fundamental pillars of intelligence will allow the intelligence community to better understand not only their needs as producers and consumers of intelligence, but what they as market consumers should pay attention to when considering a product or service.
If you wish to gain an even clearer picture of the different disciplines as well as their scope, limits, and practical uses, we recommend reading The 5 Disciplines of Intelligence Collection by Mark M. Lowenthal and Rober M. Clark.
We hope that this article proved useful and helped better your understanding of the different types of intelligence collection disciplines. If it has, please share this article with your colleagues and consider purchasing Maltego today.
From Information to Actionable Intelligence 🔗︎
If you want to gain even more insight into how intelligence is created and discover how analysts utilize intelligence collection disciplines to ensure high-quality intelligence, we encourage you to watch our deep dive on breaking down intelligence. Simply fill out the form below to watch it now!
Download the resource
Remember to follow us online via Twitter and LinkedIn. You are also welcomed to subscribe to our newsletter to stay updated on new product developments, tutorials, and cases. Happy learning with Maltego!
Sources 🔗︎
- https://www.dni.gov/index.php/what-we-do/what-is-intelligence
- https://irp.fas.org/threat/handbook/disciplines.pdf
- https://usnwc.libguides.com/c.php?g=494120&p=3381426
- https://en.wikipedia.org/wiki/List_of_intelligence_gathering_disciplines
- https://irp.fas.org/nsa/ioss/threat96/part02.htm
- https://www.mondaq.com/unitedstates/technology/898832/what-is-webint
- https://privacyinternational.org/explainer/55/social-media-intelligence#:~:text=Social%20media%20intelligence%20(SOCMINT)%20refers,such%20as%20Facebook%20or%20Twitter


 4.5 rating
4.5 rating