It’s another day operating as an open source intelligence (OSINT) analyst, engaging in digital exploration and online observation of a target person’s social media presence. Yes, there is a euphemism for endlessly scrolling in search of meaningful information for an investigation. And it can be all fun and games until you hit the “like” button under a post at 54 weeks deep. Your heart stops. Your palms are sweaty. Then you remember you’re using a sock puppet account, and the sky is blue again.
This is one of the most common scenarios that an OSINT analyst may face while gathering open source information for an investigation, and it would be terrible if that “like” came from any of our personal accounts.
The second worst-case scenario is that we are indeed using a sock puppet account, but that the target is a tricky one. Oftentimes, a target person may be overly cautious, and decide to look into the curious person behind our follow/friend request – and we, on the other side of the sock puppet, have zero friends, posts, or connections. This would be a large setback, and could set us far, far back.
In this article, we will share useful tips and tricks with all of you, our dear sock puppet accounts managers, on the appropriate operational security measures to take while gathering gated social media information. We also highlight the types of information that can be collected through sock puppet accounts while ensuring the safety of both the investigators and their organizations.
Where to Collect Social Media Information Must-Do Checklist Before Diving into Investigations Using Sock Puppet Accounts Stay Safe During SOCMINT Investigations with Sock Puppet AccountsTable of Content 🔗︎
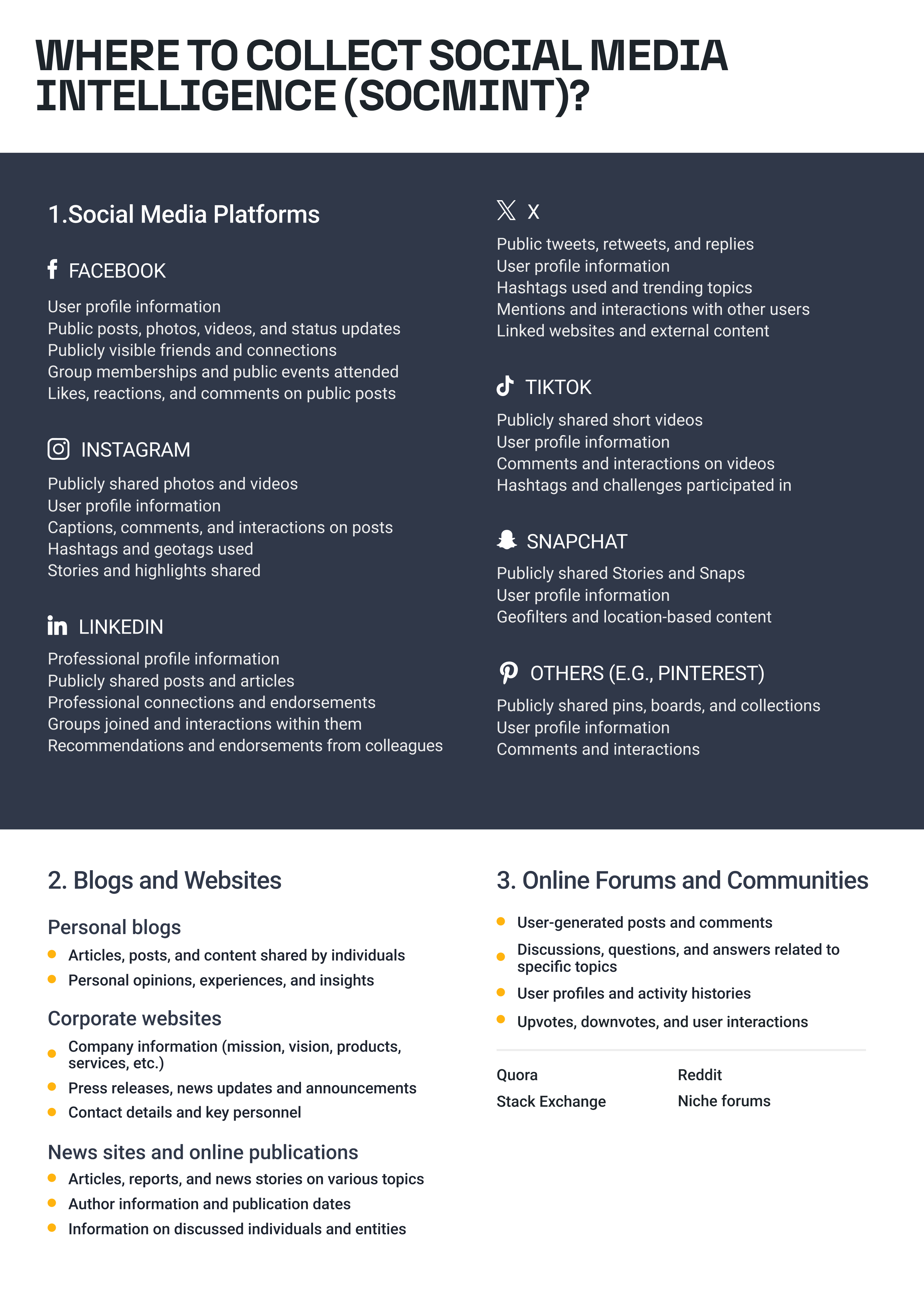
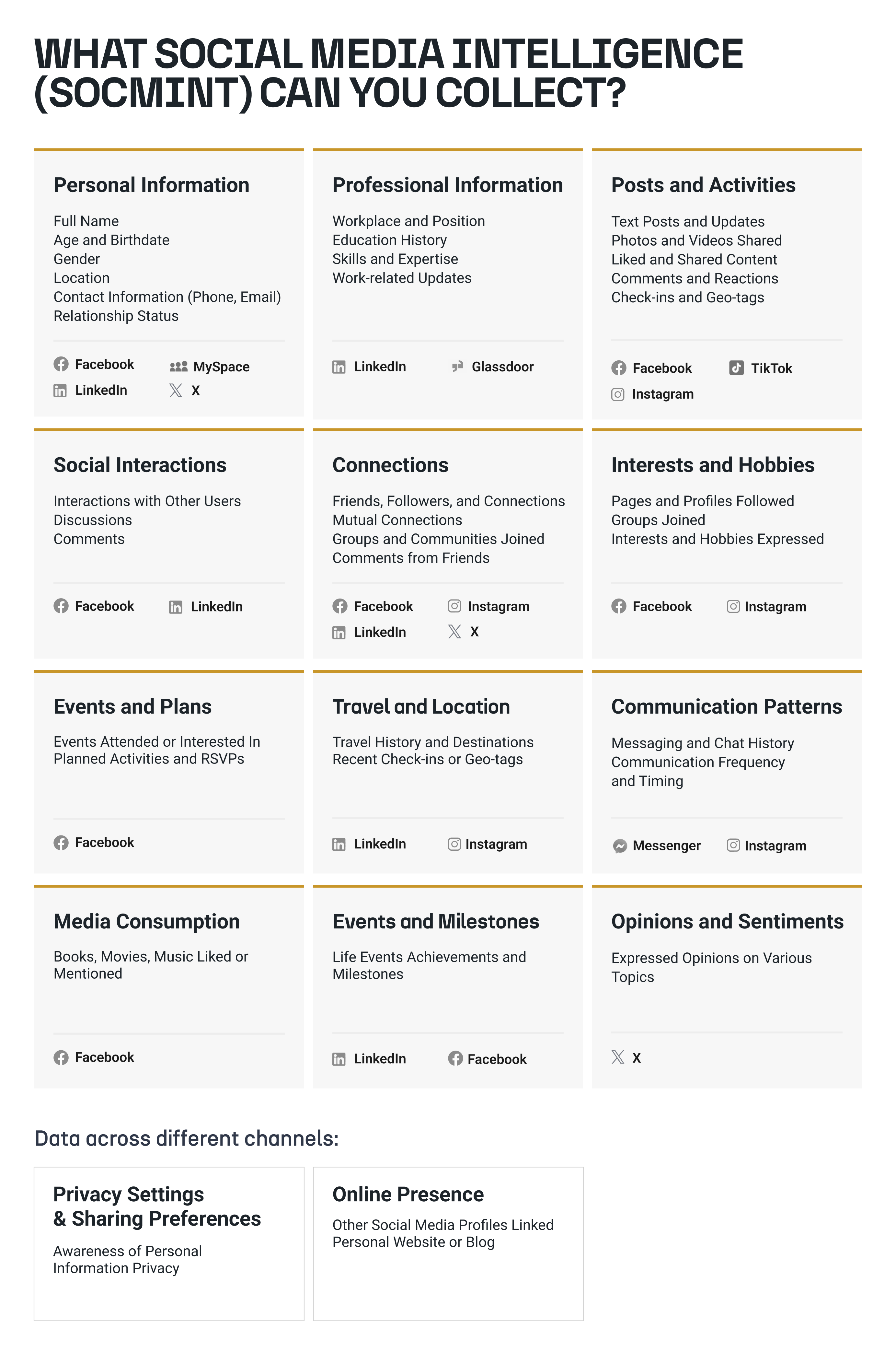
Where to Collect Social Media Information 🔗︎
To succeed in gathering social media intelligence (SOCMINT), start by identifying relevant information and objectives for your search. You should explore various platforms and public databases that aid comprehensive investigations. The key ones to focus on are:
Investing time to understand a social media platform may seem daunting, but it’s a worthwhile endeavor. Understanding the use of these social networks adds an extra layer of security to our operations.
The availability of this information may vary depending on individual privacy settings, platform policies, and the content users choose to share.
Passive SOCMINT 🔗︎
Some social media platforms allow users to see the target’s information and activities but will notify the target that someone has visited their profile (e.g. LinkedIn). This is one of the reasons why we need to have our sock puppet accounts from different social media platforms ready to go. Even if you are simply browsing for information, you need to make sure to do it without revealing your identity.
Active SOCMINT 🔗︎
On some social media platforms, the content we need–posts, stories, contacts–are not accessible due to the targets’ privacy settings. In the case where we must interact with the target in some way (for example, sending a friend request) to obtain access, we are employing the active SOCMINT technique.
Whether your chosen approach is passive or active, you should always navigate with the idea that all online activity can be monitored and identified. Understanding the functionalities and privacy settings of each platform gives us a huge advantage when using it for investigative purposes. Mastering the workings of these social media sites and platforms will optimize OSINT and SOCMINT investigations and provide optimal results.
Must-Do Checklist Before Diving into Investigations Using Sock Puppet Accounts 🔗︎
If you haven’t yet set up your sock puppet accounts, this article might be beneficial for you to read first, Creating Sock Puppets for Your Investigations. Now that you’re all set, let’s get started in the next steps to make your sock puppet accounts as safe and legitimate as possible:
1. Immediately review and set privacy settings for the platform to limit information visibility: 🔗︎
- Take the time to carefully work through each individual platform’s privacy settings, and configure these to restrict the amount of personal information visible to others.
- Carefully adjust who can see your posts, personal details, and contact information to minimize exposure to the public and potential adversaries.
2. For passive research, keep the account completely locked down and avoid making the profile public: 🔗︎
- If you’re conducting passive research and don’t intend to engage with others, it’s best to keep your account private and locked down.
- By limiting access to your profile, you reduce the risk of unwanted attention or intrusion while still being in a position to observe others’ public content.
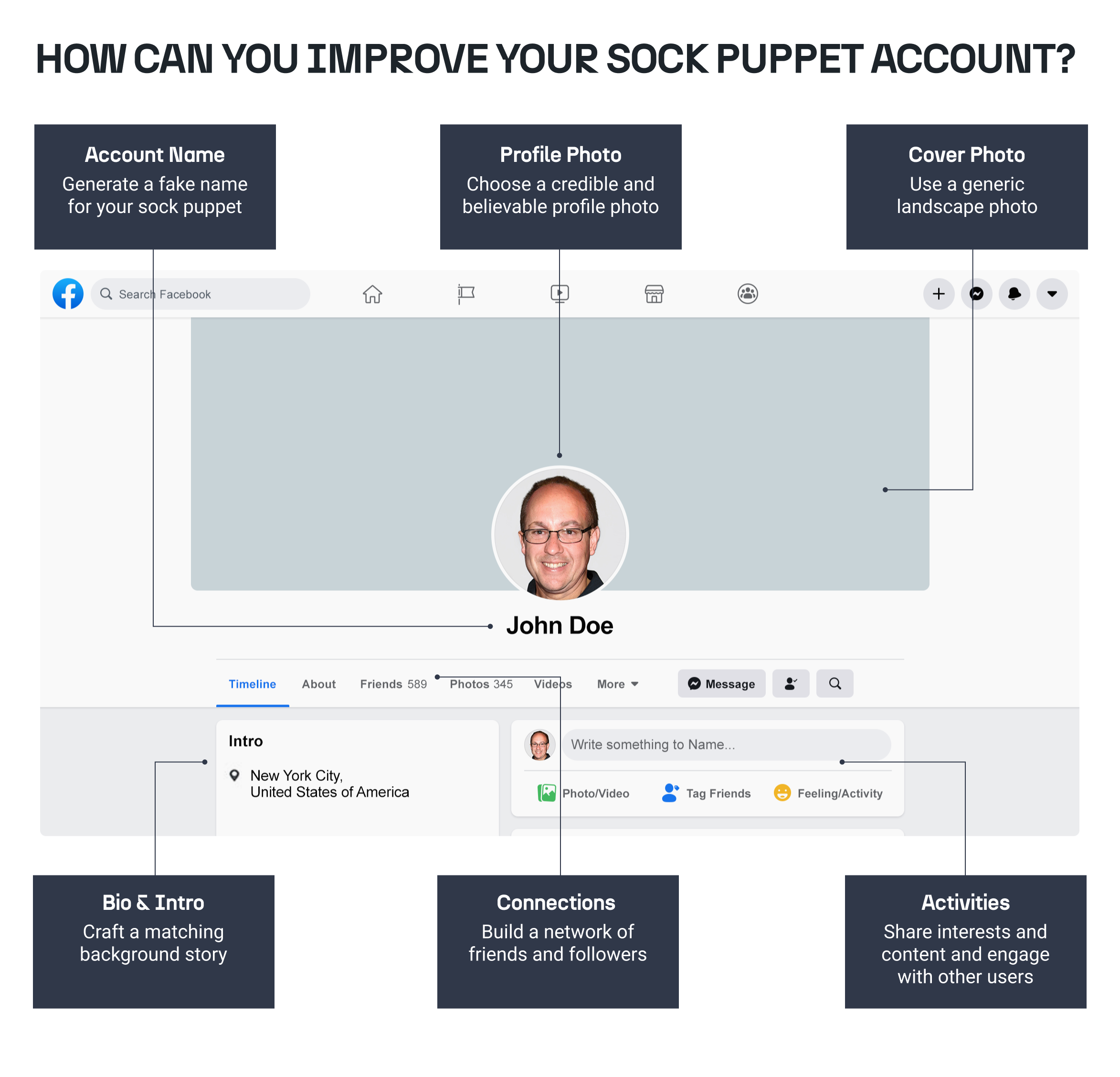
3. For active research, create a realistic profile with a suitable backstory, and ensure that it resembles that of a real person: 🔗︎
- When engaging in active research, such as interacting with subjects, it’s crucial to create a credible and believable profile.
- Craft a backstory for the profile that aligns with the persona you want to portray and ensure that it matches the platform’s user demographics.
- Ensure your profile has enough friends, followers, and activity to appear authentic, as sparse profiles may raise suspicion.
4. Use generic landscape photos rather than someone else’s identity, and be cautious with stock images: 🔗︎
- Avoid using pictures of real people, especially without their permission, as this can lead to identity theft concerns and legal issues.
- Opt for generic landscape photos or images that don’t reveal any specific personal details to safeguard your own privacy and respect others’ rights.
- Be cautious when using stock images as some social media algorithms can detect their use, potentially leading to account suspension or scrutiny.
5. Engage in natural activities like posting links and liking pages to mimic genuine user behavior: 🔗︎
- Once your profile is set up, engage in natural activities that reflect how a real person would use the platform.
- Post links to articles or content of interest, like pages related to your profile’s interests, and participate in discussions to appear authentic.
- Mimicking genuine user behavior will help convince the platform and other users that your account represents a legitimate user rather than a fake or malicious entity.
How to Use Maltego in Combination with Sock Puppet Accounts 🔗︎
Using Maltego in OSINT and SOCMINT investigations is a safe way to collect information.
Through the use of Maltego, we can gather a significant amount of the information we need in a discreet manner, without the need to directly visit social media sites. This is made possible by utilizing different connectors to consolidate data. However, there are times when delving deeper into social might require the use of proxy accounts, commonly referred to as sock puppet accounts.
In the Properties window of each returned Entity on the Maltego graph, you can find links to the source of the information retrieved, such as the original social media profiles. Visiting the original account may be beneficial and allow you to gather additional information about the target, or simply to verify if this account contains the data you are looking for.
It’s not a bad thing to be switching between Maltego and the browser of your preference. An instance of additional information that we might come across involves the target incorporating data or details about their presence on different social media platforms within their profile description.
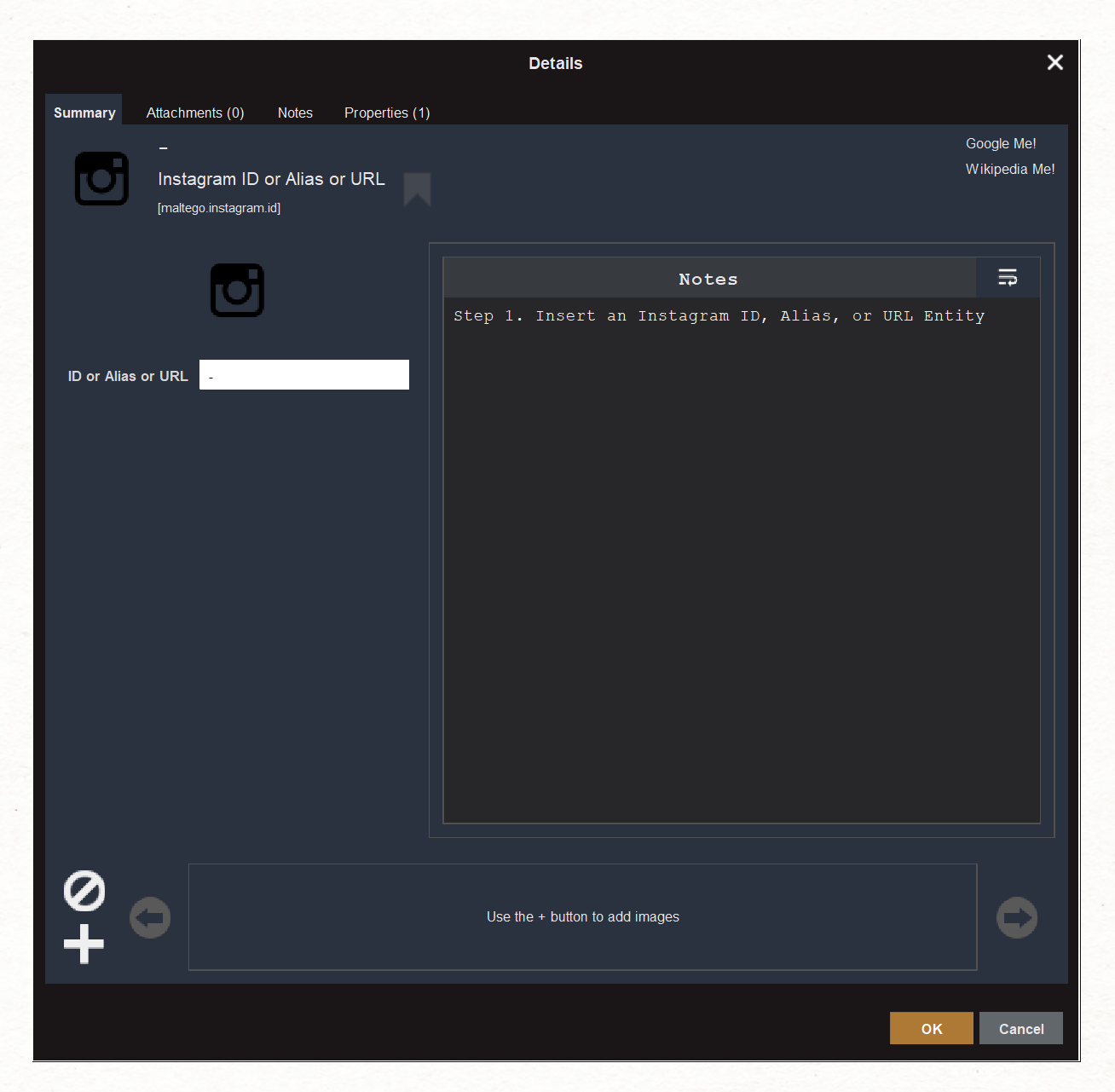
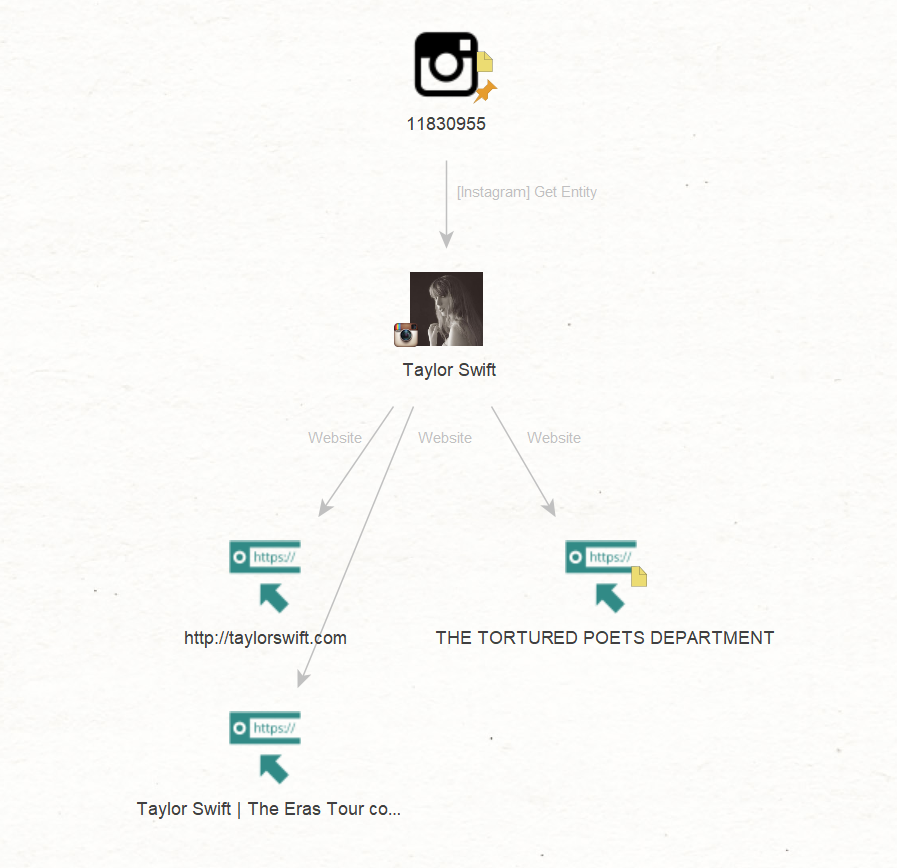
In our example, we will start with an Instagram Entity. Here, you can paste the complete ID, Alias, or URL of the Entity you want to investigate.
Now, you will be able to run a Transform to see the Name and Properties of the account of interest.
In this case, the Transform result tells us that this account belongs to Taylor Swift. From here, you may look into other details of the account in question and pivot further to Followers, Following, and other pieces of information that are pertinent to your investigation.
Stay Safe During SOCMINT Investigations with Sock Puppet Accounts 🔗︎
To help you conduct a thorough check on whether your sock puppet operation is properly set up and running, we put together a checklist that you can download. This checklist includes all the steps mentioned above and more tips and tricks to try out.
Download the checklist and share it with your team now!
Download the resource
Don’t forget to follow us on Twitter, LinkedIn, Mastodon, and sign up to our email newsletter, so you don’t miss out on updates and news!
Happy investigating!
About the Author 🔗︎
Daphnée Aguilar 🔗︎
Daphnée is a Criminologist with more than 10 years of experience as an Intelligence Officer. She specialized in developing actionable intelligence for identifying, preventing, and neutralizing threats and risks from Transnational Organized Crime. Driven by the feminist movement, her last research was on the Effects of Gender and Racial Bias on Gender-Based Violence Policies. She considers herself a professional taco taster.