Security within an Operation Starts with the Investigators 🔗︎
Sicherheit, securité, seguridad, ασφάλεια, sicurezza, veiligheids, safety. A word. A concept. It is a must in every aspect of our daily lives. It shouldn’t be different in the virtual realm.
The security of an operation starts with the investigator in charge. If the investigator does not have all their flanks covered with respect to their personal security, the other aspects (virtual, operational, strategic, and tactical) can be seriously compromised. One strategy to prevent this when we are performing OSINT investigations is by using a sock puppet.
Because prevention is the best protection, we at Maltego have made our Christmas list of must-have features for sock puppets when performing in-depth OSINT investigations. We want to share these with you and hope you can implement them to benefit your investigations in the near future.
Happy Holidays!
The 5 Levels and Types of Personal Data 🔗︎
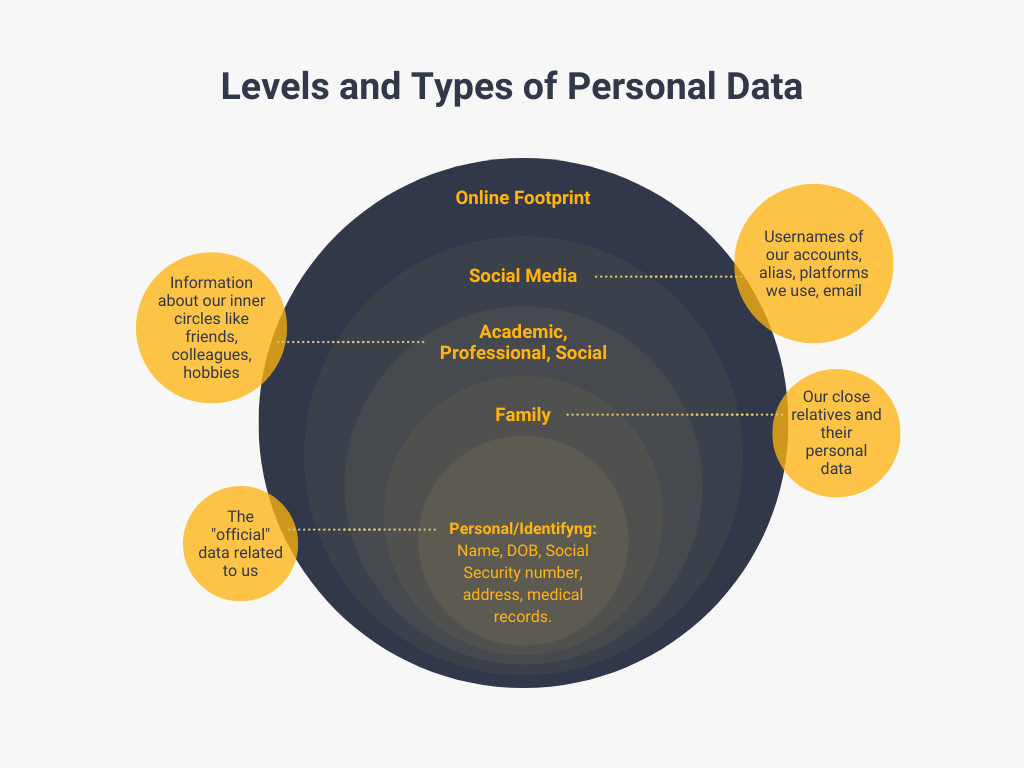
The personal safety of the investigator involves, among many other things, shielding all data associated with his or her private life. To better visualize the kind of information that we should be protecting, we can talk about “spheres” or areas of our daily lives that may be breached.
What is personal data? It is any information that allows us to identify a natural person or make a person identifiable. Data can be of different types:
- Personal Or Identifying Data: Name, surname, ID or NIE, social security number, address, telephone, date and place of birth, age, and marital status.
- Social: Properties, hobbies and lifestyles, membership in forums, clubs or associations.
- Family: Genealogical tree, names of parents, siblings, children, etc.
- Economic-financial: Bank details, income, income, credits, loans, guarantees, pension plan, and retirement.
- Medical or health: Medical history of the individual and health controls, among others.
- Administrative: Administrative procedures, claims and appeals, sanctions, records, applications, and concessions.
- Judicial: Judicial file or history, sanctions, and judicial procedures.
- Social Services: Aid or subsidies, receipt of social assistance benefits, subsidies, and pensions.
- Academic And Training: Academic record, training, and qualifications.
- Professional And Employment: Experience in the professional world, the professional record of the worker, and positions they’ve occupied.
The list above is not exhaustive, but it provides a general overview of the types of data that make it possible to identify a person.
Why is it important to be aware of the types of data that can identify us? Because it is a two-way street, and we must take these into account to set up our sock puppet.
DIY – Your Own Sock Puppet 🔗︎
In Internet terms, sock puppets are online identities used for disguised activity by the operator. A sock puppet is defined as a person whose actions are controlled by another. It is a reference to the manipulation of a simple hand puppet made from a sock and is often used to refer to alternative online identities or user accounts created for the purpose of deception and operational security.
First And Foremost, We Must Cover Our Virtual Tracks 🔗︎
Before thinking about what our sock puppet’s favorite color would be, we need to make sure that all the data we attribute to our sock puppet can’t be tracked back to us. How?
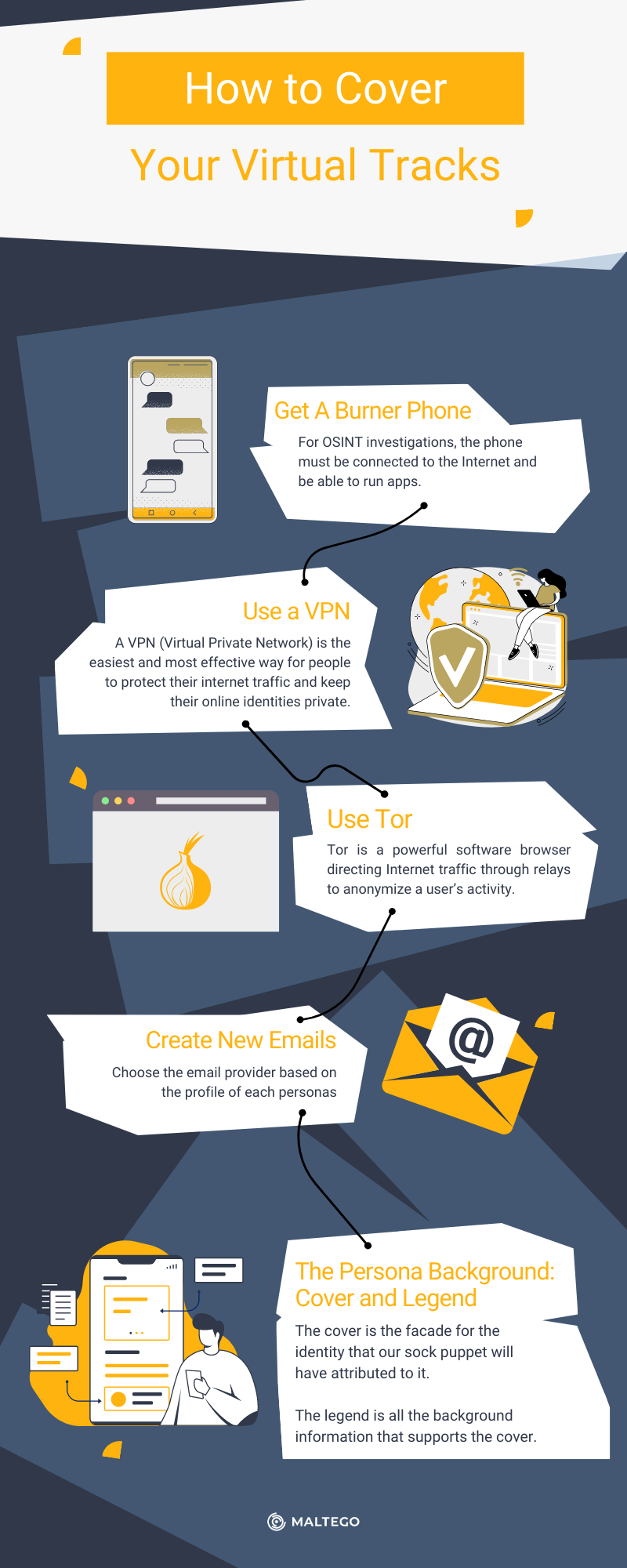
Get A Burner Phone 🔗︎
The basic definition of a burner phone is that it is a device very limited in terms of features. It is only intended to make and receive calls anonymously, and it is disconnected from all networks.
For OSINT investigations, the phone must be connected to the Internet and be able to run apps, so we need a smartphone, basically. But how can we make burner smartphones safe?
It may sound obvious and sometimes excessive, but in the small details lies the success or failure of security strategies.
- Purchase the phone in cash and in a physical store. Avoid any online shopping.
- When you turn it on for the first time and during the time you are using it, do not carry personal devices. This is in case you are tracked, the disposable phone and your personal or work phone do not share the same location. You never know who is watching.
- Do not enter email accounts related to your personal sphere.
- Do not store any data related to your personal sphere (phones, emails, calendars, photos).
- Use one gadget only per alias, preferably with an alternative operating system to the one you typically use.
Use a VPN 🔗︎
A VPN (Virtual Private Network) is the easiest and most effective way for people to protect their internet traffic and keep their online identities private. As you connect to a secure VPN server, your internet traffic goes through an encrypted tunnel that nobody can see into. Changing your IP address with a VPN helps shield your identity from websites, apps, and services that seek to track you. Good VPNs also prevent your internet provider, mobile carrier, and anyone else who may be listening from seeing your activity, thanks to a layer of strong encryption. Using a VPN changes your IP address (the unique number that identifies you and your location in the world). This new IP address will make you appear to be in the location you select when you connect: the UK, Germany, Canada, Japan, or virtually any country, provided the VPN service you choose hosts servers there.
Or… Use Tor 🔗︎
Short for the Onion Router, Tor is a powerful software browser that directs Internet traffic through thousands of relays to anonymize a user’s activity. It’s free to download and should be in conjunction with your alias.
Create New Emails 🔗︎
You’ll want a disposable email for each of your fake identities. Do you use Gmail or Proton? Choose the email provider based on the profile of the persona we are creating – whether it’s someone with extensive knowledge of online security or a simple commoner whose alias includes his birth year.
The Persona Background: Cover and Legend 🔗︎
Now that we have covered our online presence, we will delve into the intelligence jargon. We will have to apply two intelligence concepts that are essential in operational security when building an alternative identity for disguised activities: Cover and Legend.
The cover is the facade for the identity that our sock puppet will have attributed to it. Initially, it is composed of a name, an alias, a profile picture, and some of the data mentioned above.
The legend is all the background information that supports the cover. It is the heart of a cover and amounts to an entire artificial life history to “fool” even determined professionals. The legend describes who you are, why you are there, and what you are doing.
It is a very complex job to craft a good legend, but not impossible. Let’s look at how to build a legend that is suitably complex to outwit against even highly trained stalkers.
Drafting a Legend for Your Sock Puppet 🔗︎
You’ll need an alias – a false identity – to conceal a genuine one in the physical or digital worlds.
As prevention is the best protection, it is a matter of elaborating in detail the legend, the biography, and the new identity that the investigator assumes behind the sock puppet to protect it. That means spending a lot of time preparing the legend to support the cover.
- Avoid loose ends
- The whole story behind the identity we are creating must be coherent, and consistent, so as not to raise suspicions
Coverage includes having all these answers in mind.
Don’t use or reveal details about yourself. Even though it will be easier to remember by using our own data here and there, creating a sock puppet entails training our memory. Don’t ever use somebody else’s name. Instead, you can use a site like Fake Name Generator to get a new one according to your own settings.
The same goes for your profile picture. You might think, it will be very easy to use the photos from this person that I know a little bit about and we’re not friends at all. Don’t take that path. Instead, you can go to This Person Does Not Exist and refresh until an AI-created photo which aligns with your sock puppet profile pops up.
Delving Deeper into Shaping Our Social Media Profiles 🔗︎
The personality of our new persona will depend on the type of investigation which you will be using the sock puppet for. After a thorough analysis of your needs, you will first fill in the blanks on the personal data listed in the first part of the blog (like we said, two-way street).
We must be consistent in the accounts we use on our burner phone. The objective is that our persona does not raise suspicions about its authenticity, as well as the aliases, accounts and associated profiles.
If you are going to take the research a step further and interact with other users, we must be aware that building the profiles will take more time. A credible profile should have followers, publications, and previous interactions. This type of profile requires consistent teamwork and the combination of other disposable accounts.
In any case, there are some aspects that you must keep in mind:
- Don’t share your location
- Don’t use these accounts to follow your personal accounts, nor the personal accounts of people from your private or professional sphere
- Avoid posting photos of places you usually visit
Using your Sock Puppet 🔗︎
Your newly created profile is ready to use. Regardless of the type of OSINT we are going to perform (passive or active), it is extremely important that our puppet sock has some level of real activity in the virtual world. What kind of activity? How to manage multiple sock puppets at the same time? We will cover that in our next intel-delivery.
Attention to Detail is the Key to Safety 🔗︎
Some of the above points may seem exaggerated, or silly, but always remember that attention to detail is the key. Your safety is not only the safety of your colleagues and the operation, but includes protecting your family and friends.
We hope you find this article about creating sock puppets to ensure operational safety useful.
Don’t forget to follow us on Twitter and LinkedIn and sign up to our email newsletter, so you don’t miss out on updates and news!
Until the next one and happy investigating!
About the Author 🔗︎
Daphnée Aguilar
Daphnée is a Criminologist with more than 10 years of experience as an Intelligence Officer. She specialized in developing actionable intelligence for identifying, preventing, and neutralizing threats and risks from Transnational Organized Crime. Driven by the feminist movement, her last research was on the Effects of Gender and Racial Bias on Gender-Based Violence Policies. She considers herself a professional taco taster.