Born in and for the infosec community, Maltego has empowered over one million investigations in over 100 countries and markets. The result: a vast and vivid community that shares tricks and tips, use cases and demonstrations and tutorials.
For more than 10 years, users have incorporated Maltego into various investigations and inspired us to further develop, advance its capabilities and expand its potential. In this article, we will take a quick dive into some real-life use cases of Maltego and how specific types of investigators utilize the tool in their day-to-day operations.
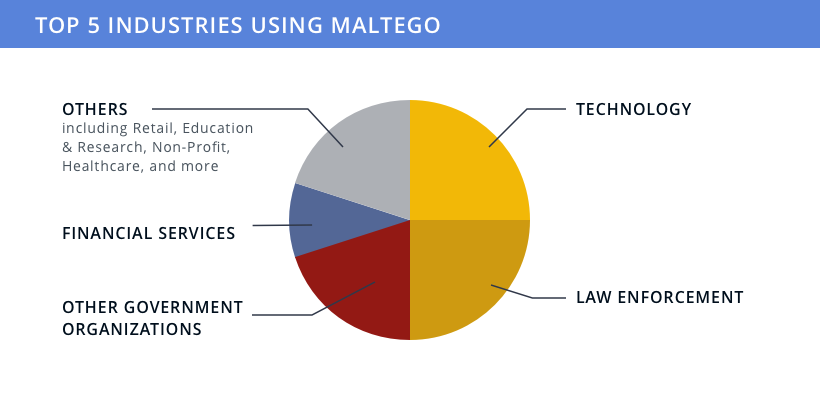
Infographic: Who Uses Maltego? 🔗︎
Maltego is used by professionals and experts in industries ranging from technology, law enforcement, financial services, and intelligence to retail.
Our primary users and use cases can be categorized into three groups: Cybersecurity, Law Enforcement, and Trust & Safety.

In Cybersecurity Operations: Reacting to and Hunting Threats 🔗︎
In cybersecurity operations or security operation centers, Maltego is often used by tier 2 incident response and tier 3 threat intelligence analysts.
Tier 2 Incident Response Analysts and Maltego 🔗︎
Incident responders identify the who, what, why, when, and how of attacks. Once an incident is verified, they analyze open vulnerabilities, initiate quick patches, and get down to the root causes of compromised systems.
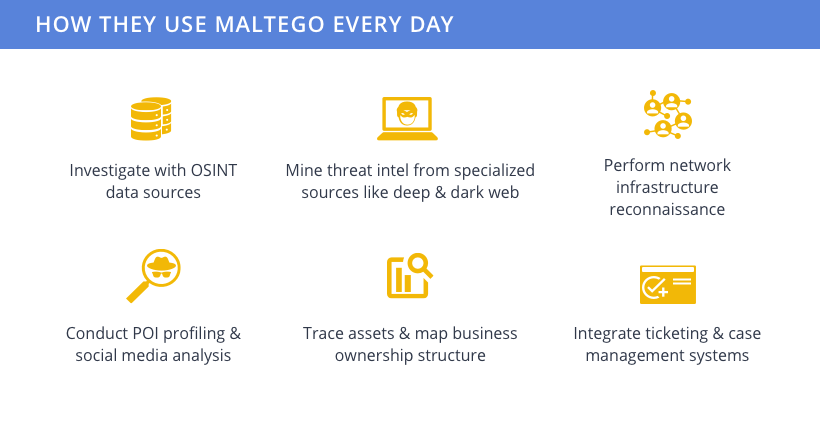
To streamline the process, they access log files in Maltego and conduct network traffic forensics, investigating unauthorized devices on the network, multiple logins from different locations, excessive connections to multiple hosts from a single host, and more. Afterwards, they can transfer these complicated information in an easily understandable Maltego graph or generate concrete reports for incident analysis reporting.
Tier 3 Threat Intelligence Team and Maltego 🔗︎
Threat hunters and threat analysts in a security operation center actively hunt for unknown threats, vulnerabilities, and security gaps in the network through vulnerability assessment and penetration testing. They use Maltego to assess vulnerabilities (CVEs), proactively look for undetected compromises with new indicators of compromises (IoCs), and support incident responders.
For example, using Maltego, threat analysts can identify vulnerable software or hardware architecture, outdated software or hardware with known vulnerabilities, open ports, attackable services, and more during pentesting.
Read more about cybersecurity use cases: 🔗︎
- How to Uncover Phishing Domains Using Maltego to Analyze Domain Infrastructure
- Network Footprinting with Machines in Maltego!
In Law Enforcement: Monitoring and Unmasking Criminals 🔗︎
Maltego is used by international, federal, and local law enforcement agencies around the world, including cybercrime investigators, cyber detectives, digital forensics units, and cyber criminologists. The German Federal Criminal Police Office (BKA), for example, uses Maltego in their investigations since 2016.
Maltego can help investigations into online fraud, cyber threats, cyberviolence, financial crime, and organized crime; where offenses can range from business fraud to identity theft, phishing to cybergrooming, money laundering to trafficking, and more.
Cybercrime Investigators and Maltego 🔗︎
Cybercrime investigators alike rely on Maltego for three operations: Monitoring, unmasking, and researching.
With Maltego, they visualize intel from high-valued deep and dark web sources to monitor threat actors. When suspects emerge, they conduct investigations to uncover information such as criminal attribution, email address, public records, profiling, and locations.
As part of a criminal investigation, they also use Maltego to understand the extent and nature of a criminal campaign, identify its infrastructure and servers, uncover company ownership structures, and conduct network mapping.
Read more about law enforcement use cases: 🔗︎
- Identifying Risky Bitcoin Transactions with Maltego and CipherTrace Blockchain Intelligence
- State of The German Police IT Infrastructure and The Importance of OSINT Capabilities
In Trust & Safety: Uncover Malicious Users and Prevent Insider Threats 🔗︎
Insider threat analysts, fraud investigators, and due diligence teams are all Maltego users in the trust and safety sector.
Insider Threats, Fraud, Abuse and Maltego 🔗︎
Insider threat analysts investigate product or data misuse by internal personnel, such as inventory theft, data exfiltration, and customer data leak. Fraud and abuse investigators look into external malicious users and activities like account takeover, fake news, spamming, catfishing, and more.
In these cases, Maltego is used for infrastructure mapping, social network analysis, social media data analysis, asset searching and tracing, and more.
Due Diligence and Maltego 🔗︎
The compliance and due diligence teams are responsible for a number of procedures including pre-transaction, third-party, customer, and employee checks, as well as politically exposed person (PEP) screening.
Maltego supports and allows them to conduct company ownership structure, asset searching and tracing, social network analysis, and identity resolution, effectively enhancing their due diligence accuracy.
Read more about trust & safety use cases: 🔗︎
- Investigating Insider Threats on Warehouses and E-Commerce Portals with Maltego
- Mapping Visual Disinformation Campaigns with Maltego and TinEye
Leverage Maltego to Tackle Your Analysis and Investigations 🔗︎
Why is Maltego, a single graphical link analysis software, able to help investigators perform such a wide variety of tasks and analysis? One of the biggest reasons lies in the extensive access to various data sources and flexibility for internal integrations.
External Data Sources and Internal Data Integration 🔗︎
Maltego features a variety of open source intelligence (OSINT) and third-party data sources in the Transform Hub, including deep and dark web, cryptocurrency, social media, person-of-interest, company intelligence, network, infrastructure, and many more.
These data integrations allow investigators to pivot from one Entity to another with powerful Transform queries to perform reverse image search, passive DNS lookups, and more. Companies and organizations can also seamlessly integrate internal data into Maltego, where they can securely and effectively collaborate on sensitive or confidential investigations.
On top of that, Maltego is designed with the flexibility to integrate with other systems. For instance, cybersecurity experts can integrate their SIEM and ticketing systems—like Splunk and ServiceNow— into Maltego, while law enforcement agencies can seamlessly integrate it with their case management, evidence systems, or digital forensics tools.
What Do Our Customers Say About Maltego? 🔗︎
Keith Gilbert, Malformity Labs, says:
“A great strength of Maltego is the ease of gaining insights from multiple, disparate data sets. In the past couple of years, Maltego has been increasingly developed towards a relevant market place for data and I am excited to see how this will evolve in the future.”
Make Maltego Your Own 🔗︎
If you want to learn more about how Maltego can help your teams and organizations conduct effective investigations, schedule a demo with our experts today!
For the latest use cases, product updates and news, follow Maltego on Twitter and LinkedIn or subscribe to our newsletter!
Download this infographic here to share with your friends, family, and colleagues!


 4.5 rating
4.5 rating