In times of crisis, our vulnerabilities at a national, organizational and individual level may be exposed. And while it is heartening to see people coming together to form voluntary initiatives e.g. the exceptional efforts by the Cyber Threat Coalition and Cyber Volunteers 19 to fight COVID-19 challenges, we also see a sharp spike in exploitations by malicious actors preying on these vulnerabilities. This has occurred in many forms using topics related to COVID-19 as a hook for phishing attacks, fake apps claiming to distribute information from the WHO on the spread of the disease and ploys to extract user credentials from high on-demand products and services, a recent example being the outcry against Zoom, a hugely popular video conferencing platform.
A phishing attack is when a threat actor sends out a seemingly innocent message or email designed to mislead people into downloading malware, logging into a fake service and providing personal data, or attempting to blackmail for financial gain, etc. In addition to being alert and practicing safe behaviors such as steering clear of suspicious links and not clicking on download files from unknown senders, and reporting suspicious emails (all great weapons against phishing attacks) but, if you want to delve deeper and carry out a specific investigation, there are also some smart steps you can take to analyze phishing infrastructure.
In this post, we outline a quick and easy process in Maltego that can provide additional insight into suspicious or phishing domains.
Returning to fraudsters taking advantage of the Covid-19 crisis, on the 2nd of April 2020, the Bundesagentur für Arbeit in Germany warned on its website and Twitter account about an ongoing phishing attack using the email account kurzarbeitergeld[at]arbeitsagentur-service[.]de.
The phishing message was targeted at German companies and demanded information about the entity, its legal representatives and its employees. It claimed that this information would be used to perform an online application for the company to obtain “Kurzarbeitergeld”, directly translating into “short-term pay”, a German government scheme that allows companies to retain employees even if they are asked to work fewer than usual hours by sponsoring part of the wages.
So, how do we find out more information about this phishing domain? 🔗︎
For this example, we will be using the Transforms by Recorded Future. You will need an API or current subscription for this. Other useful data integrations you can use in the Transform Hub are providers such as Passive Total (e.g. to check if digital artifacts have been detected and by which systems) , Domain Tools (e.g. to get historical data on domains), and Shodan (e.g. to see if there are different services running on a domain) to name only a few.
Note: The results on the specific artifacts (Domain, ISP) are no longer available in the exact manner presented in this investigation, possibly because action was taken quickly to redirect users to the official website of the German Arbeitsagentur. However, you can still follow the steps presented here to discover the structure of any other suspicious domains.
Let’s run some Transforms! 🔗︎
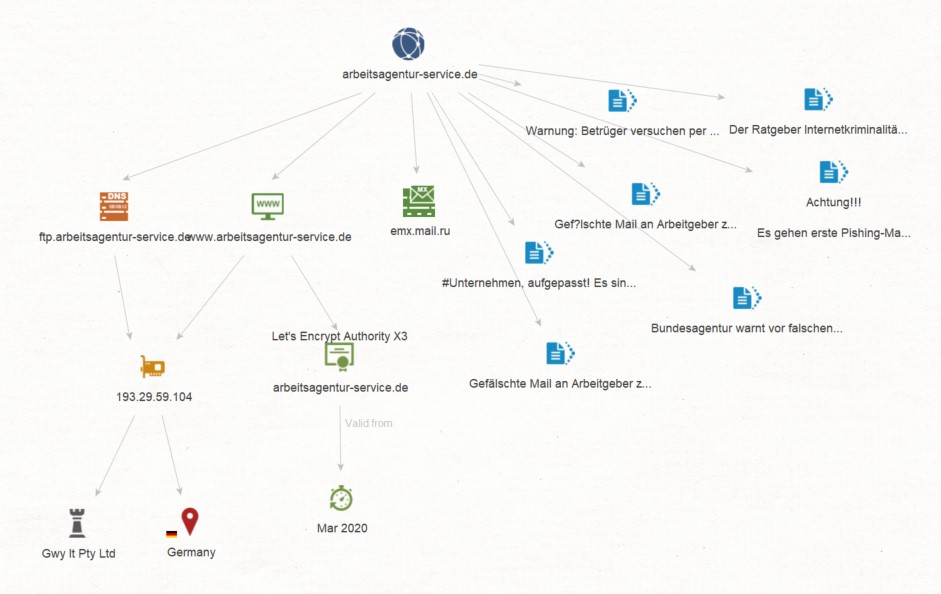
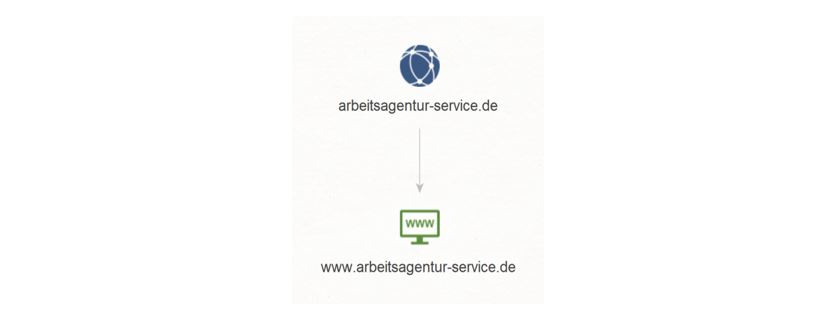
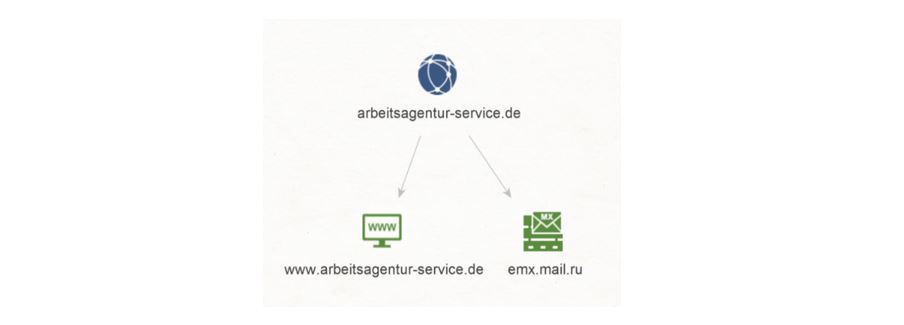
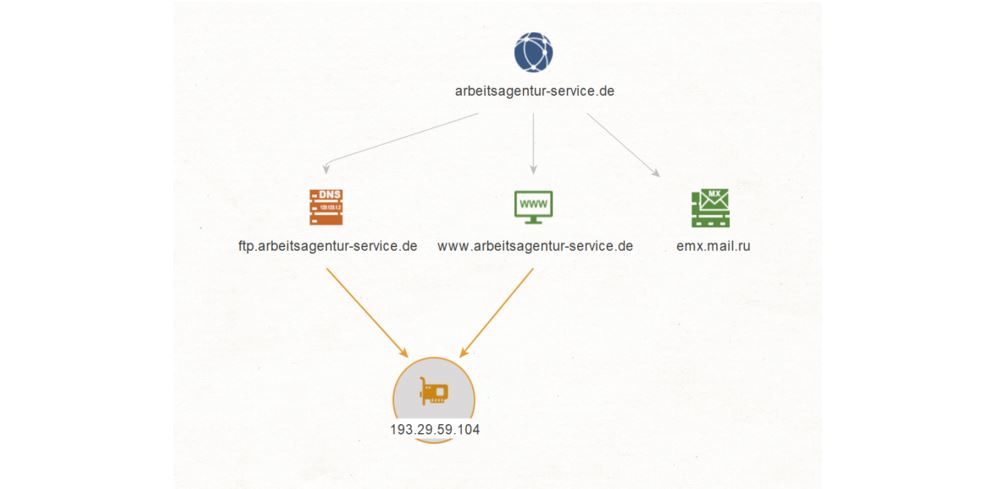
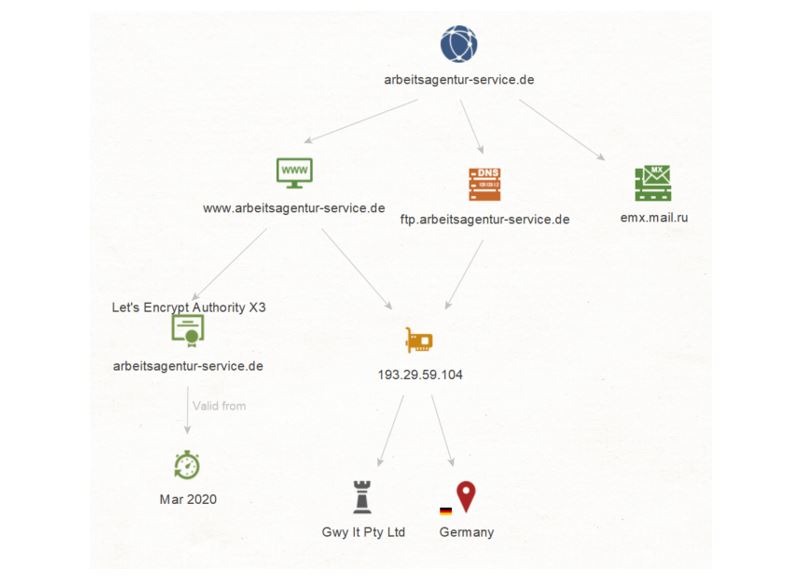
We copy the Domain arbeitsagentur-service.de to Maltego and run a To Website mentioning domain [Bing] Transform on it. This query results in a Website named www[.]arbeitsagentur-service[.]de.
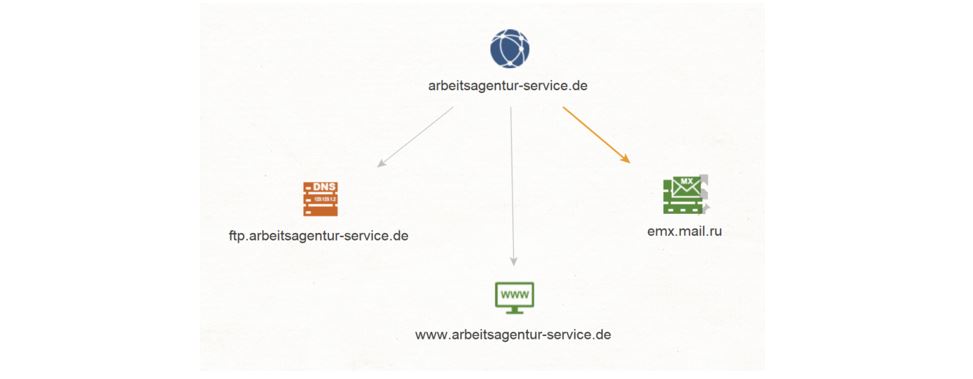
Let’s go back to the Domain arbeitsagentur-service[.]de and run a To DNS Name - MX (mail server) Transform on it. We see that this resolves to a Russian MX Record named emx.mail.ru.
We select the Domain arbeitsagentur-service[.]de Entity and run a To DNS Name [Find common DNS names] Transform on it. This query results in one DNS Name: ftp[.]arbeitsagentur-service[.]de.
Now, we want to find out if there is an IP Address linking this domain and DNS Name. In order to do so, we select the Website www[.]arbeitsagentur-service[.]de and the DNS Name ftp[.]arbeitsagentur-service[.]de, and run a To IP Address [DNS] Transform on them. We find that there is one IPv4 Address 193[.]29[.]59[.]104 linking both the Website and the Name Entities together.
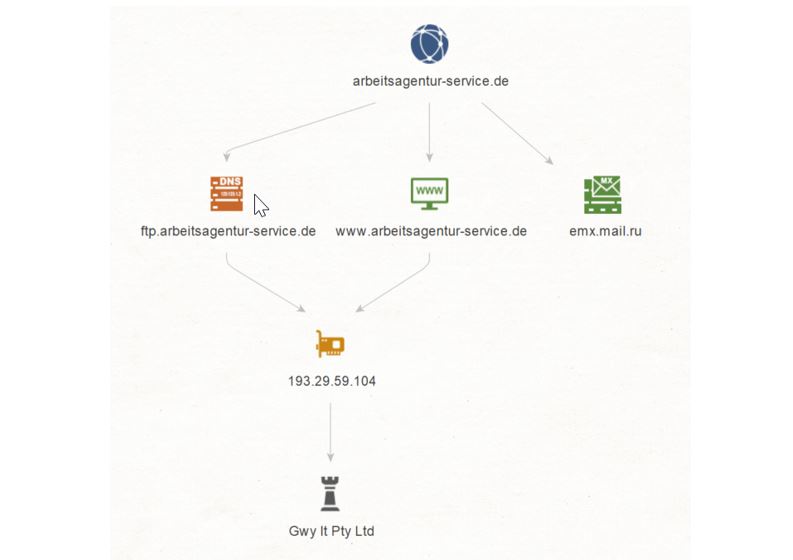
Let’s see if we can dig a bit deeper and get the ISP (or Internet Service Provider) of this IP Address. We select the IP Address 193[.]29[.]59[.]104 and run a To ISP [Shodan] Transform. This returns an ISP named Gwy lt Pty Ltd.
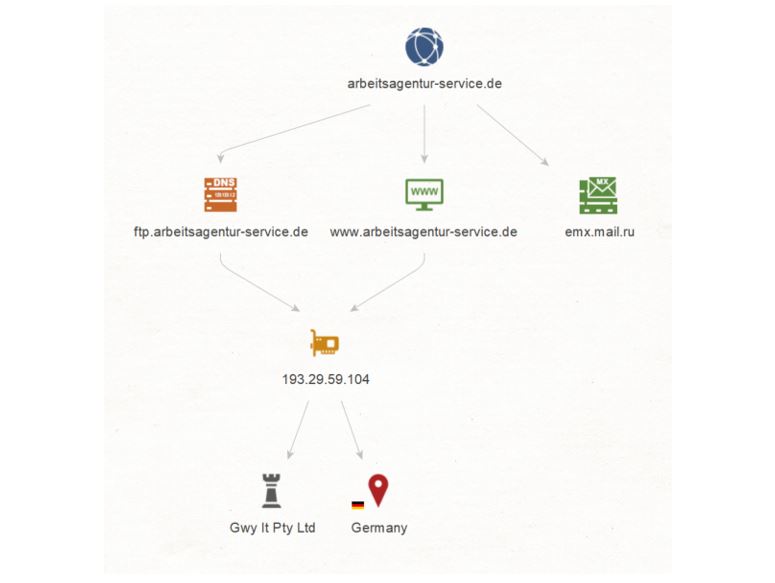
But we’re not done with the IP Address just yet. We select it again and run a To Location [Country] Transform on it, which traces the location of the IP to Germany.
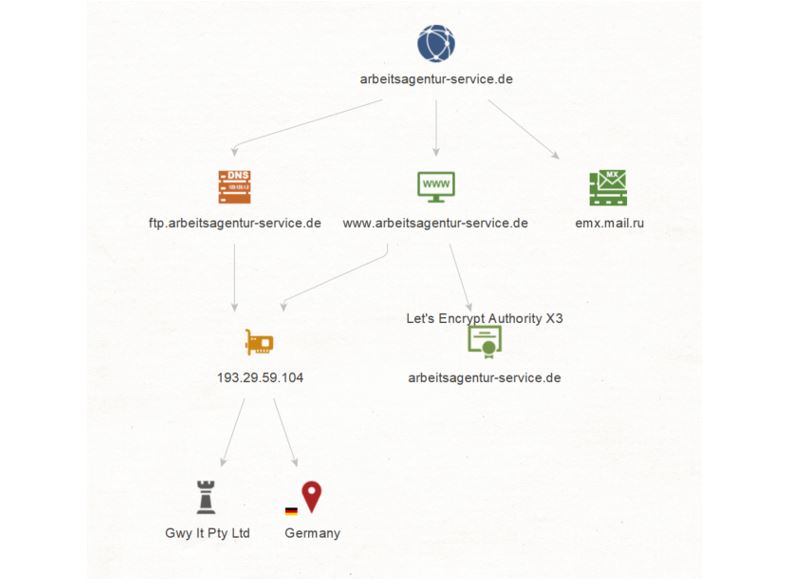
So far so good, but let’s go back to the Website www[.]arbeitsagentur-service[.]de and try to get some information on its certificate by running a To Certificate Transform on it. We obtain a Certificate for arbeitsagentur-service[.]de from Let’s Encrypt Authority X3.
Side note here: Let’s Encrypt is a non-profit certificate authority run by Internet Security Research Group (ISRG). It provides X.509 certificates for Transport Layer Security encryption at no charge. The certificates are valid for 90 days, and renewals can take place at any time during that period. These certificates are believed to be as safe as paid certificates.
Let’s take a look at the certificate date information. Select Certificate arbeitsagentur-service[.]de and run a To Valid From Transform on it. The information returned tells us that this certificate was registered in March 2020 - the timing around which the German Government decided to ease conditions on Kurzarbeit. This helps us further validate this artifact as part of a phishing infrastructure!
This is looking pretty good so far but let’s see if we can find some concrete information for our investigation by querying data from one of our Data Hub members, Recorded Future. By using Recorded Future’s Transforms, we seek to find evidence on whether the domain we have used for the investigation has been detected as an Indicator of Compromise (IOC). Make sure you have a valid RF API with you for the next step!
We select the Domain Entity arbeitsagentur-service[.]de and run a Recorded Future [RF] Domain to RFDoc Transform on it, which results on 7 RFDoc Entities, meaning 7 sources which cite this domain as part of a campaign (all of them in German). By clicking on each of the resulting documents, it’s possible to read the content - or a summary thereof - and learn more about this phishing campaign.
And this is how with the use of just a few Maltego Transforms we’re able to pivot from a Domain to a Website, from the Website to its IP address and Certificate - including data on the Certificate - from the IP to an ISP and Location, and finally from the domain to related articles and mentions of it as part of a phishing campaign!
We hope this tutorial has revealed some of the possibilities within Maltego to keep yourselves and your organizations safe from malicious actors.
Follow us on Twitter and LinkedIn or subscribe to our RSS feed and stay tuned for more interesting use cases!