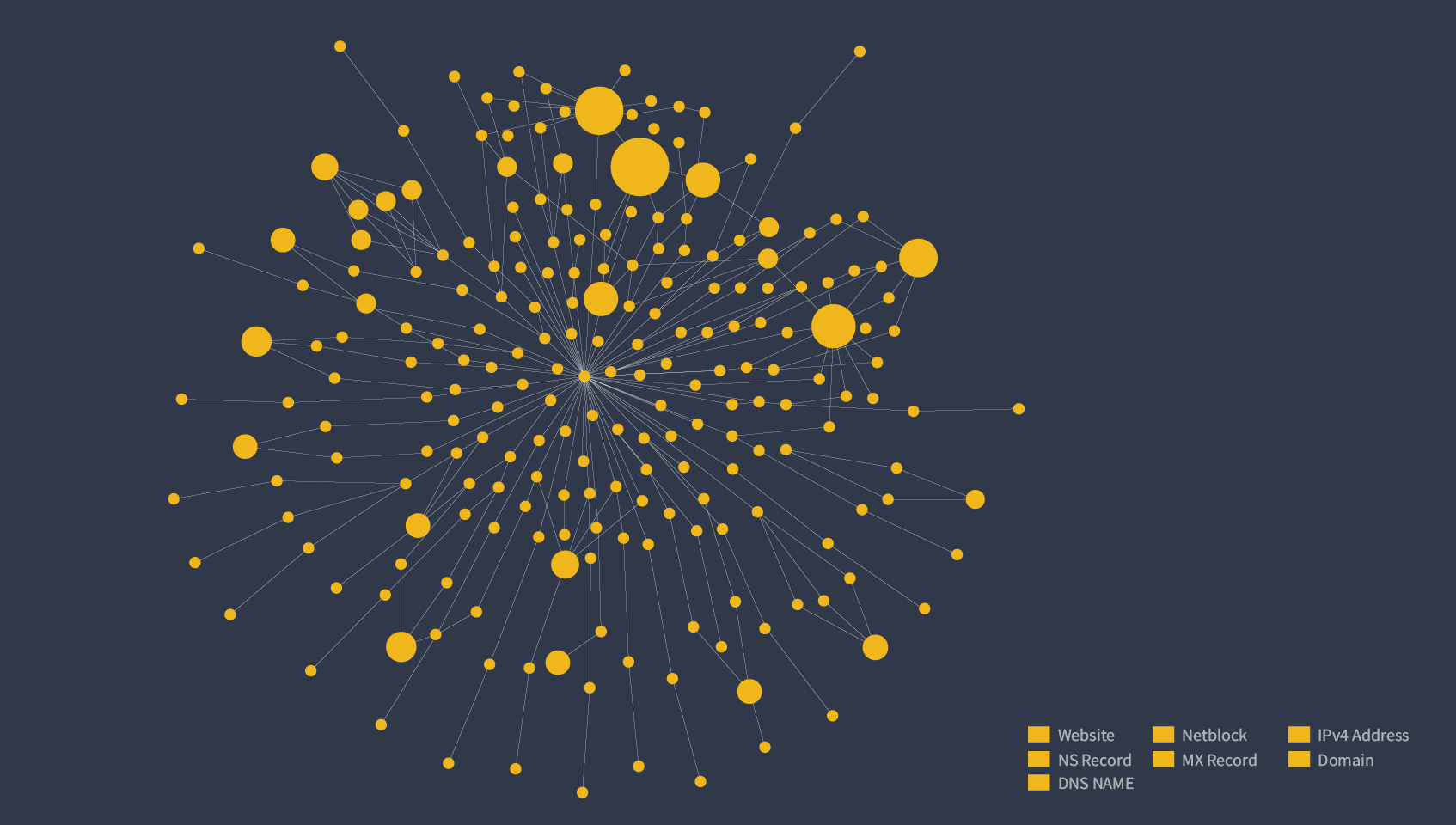
Maltego is a widely known a visualization tool for performing noteworthy external tasks. And indeed, it does perform powerfully by using external Transforms to gather information that is visualized in a target-oriented process.
However, based on its Transform architecture, Maltego can also be used as part of the daily routine of Admin or Security Officers in ways that people are not aware of, including internal visualizations for internal hosts, systems, weaknesses and services.
Metasploit Data Integration in Maltego: Easily Visualize A Bulging Database 🔗︎
Let’s use Metasploit for example. Most are aware of Metasploit’s powerful functions, especially when used in conjunction with a database and db_nmap. Very quickly though, you could find yourself lost in a bulging database which may not be easily visualized afterward without performing some tricks using tools like Armitage.
You may not be aware that with Maltego, visualization of the output is possible, and putting it into practice is actually quite simple. For starters, everything you need can be found on the web and can be done in very little time.
Let’s take a look at it, but let’s start almost from scratch. Let’s assume you have neither Maltego, nor Metasploit installed. In fact, let’s just assume you have nothing to begin with at all.
If you have already set up Metasploit and Maltego, dive into Part 2 to see how Metasploit is visualized in Matlego!
Setting Up Metasploit in Maltego 🔗︎
In this example we’re going to use VMware Fusion on a Mac and a Kali Linux VM, but you can replicate this on any setup you prefer. We begin by grabbing the latest 2020-1 VMware Kali 64Bit image at https://www.offensive-security.com/kali-linux-vm-vmware-virtualbox-image-download/ and start it up in Fusion.
Login with the kali/kali (remember the latest images don’t have the usual root/toor applied). If you prefer to simply play around in your testlab, you could set your root password with ‘sudo passwd root’ and use that. For this example, I’m going to be lazy and use the last method.
First, update everything using ‘apt-get update && apt-get dist-upgrade’ to ensure that we’re using the latest toolset. At the time of writing this article (March, 08th, 2020), we needed to download about a Gig (and pair it with at least two cups of coffee, because honestly, this can take 15 minutes even on fast machines).
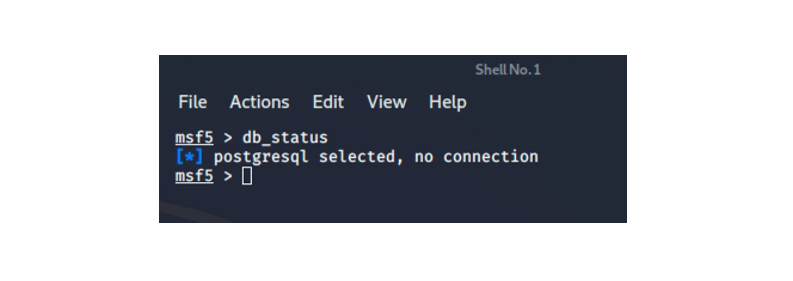
We have Maltego in place and we have Metasploit’s latest version on Kali, but we don’t have the Metasploit database support in place yet. We verify this by launching msfconsole and doing a db_status as shown in the image below.
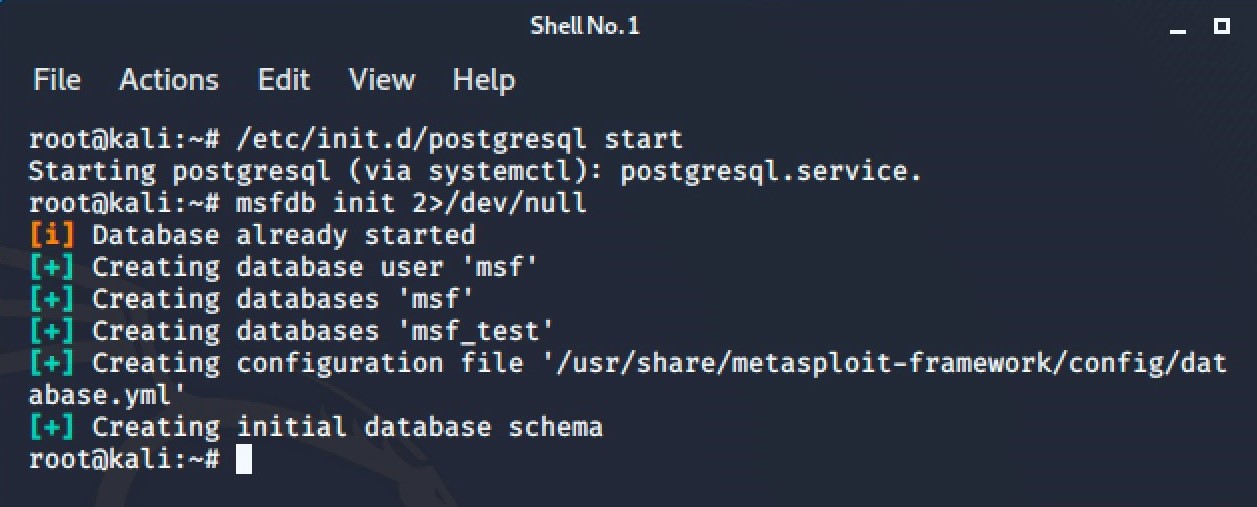
Let’s enable it now by opening a fresh console and entering ‘/etc/init.d/postgresql start‘ to start up the database, and ‘msfdb init 2>/dev/null‘ to create the database user ‘msf’, and the ‘msf’ and ‘msf_test’ databases.
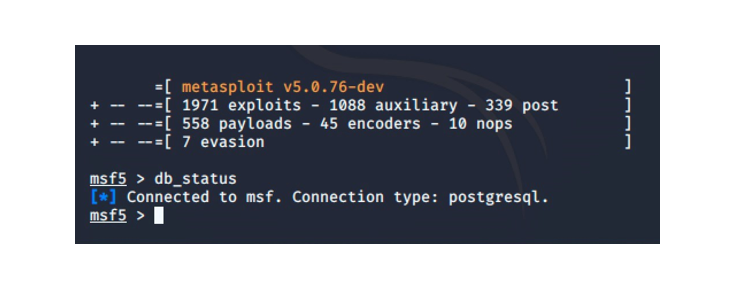
Let’s verify whether db_status is satisfied. Launch msfconsole again and query with the command ‘db_status’.
That looks better!
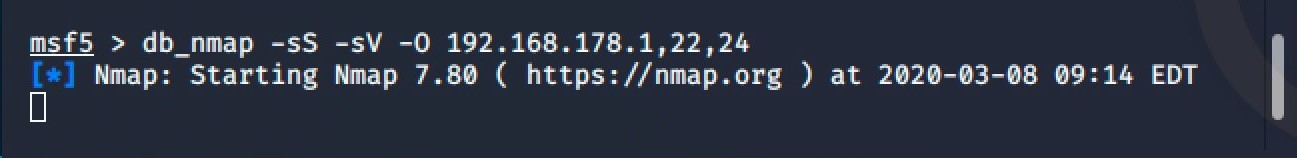
Next, let’s get db_nmap populated to get an idea of how it can be used on a larger scale. To keep it short, I launched a quick db_nmap on a private, home network. I used the msf command ‘db_nmap’ targeting three devices: a fritzbox home router, a TV and a network printer.
If you have multiple networks to examine, you could create Metasploit workspaces and manage each network in its corresponding space. You can find a great write-up with this method on the offsec website (https://www.offensive-security.com/metasploit-unleashed/using-databases/). Otherwise, the ‘default’ workspace is always selected and used.
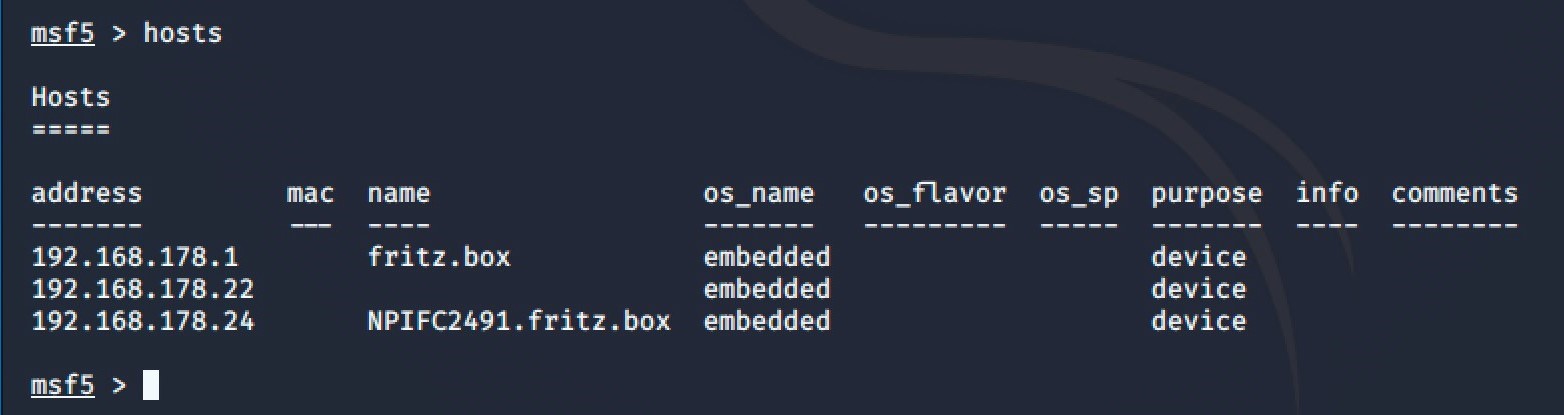
When the db_nmap command has finished, we verify whether actual content lies in the database using the ‘Hosts’ command inside msfconsole.
Now we’re getting somewhere: there is something in our msf database! Imagine that Maltego could connect directly to this very same database, access its content and produce a visualization. Except you don’t need to imagine it because it can be done, and it’s actually quite simple!
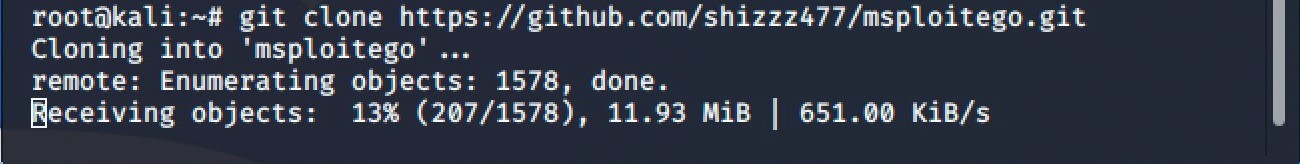
There are many different options, but why complicate it when everything we need is on GitHub. For example, msploitego by shizzz477 (https://github.com/shizzz477/msploitego) is an easy way to get the database opened inside of Maltego. Let’s grab it using git clone command. This is considered a beta feature of msploitego but why not give it a try.
git clone https://github.com/shizzz477/msploitego.git
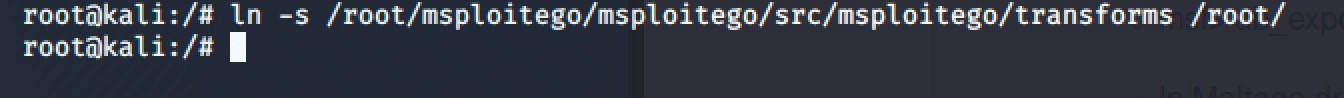
Some configuration and installation of pre-requisites is necessary to get things running. First, the Transforms path should be in ‘root’ because that is the way this GitHub defaults. Alternatively, you could also enter the ‘Transforms Manager’ in Maltego and change the paths manually.
ln -s /root/msploitego/msploitego/src/msploitego/transforms /root/
But, this little stunt requires some installations so first go with python-pip to install some python bits and pieces.
apt-get install python-pip
Launch ‘pip install deprecated’ to get them installed.
pip install deprecated
Get python-libnmap and don’t be confused when the GitHub project site shows something else. The name has simply changed.
pip install python-libnmap
Now launch ‘pip install NmapParser’.
pip install NmapParser
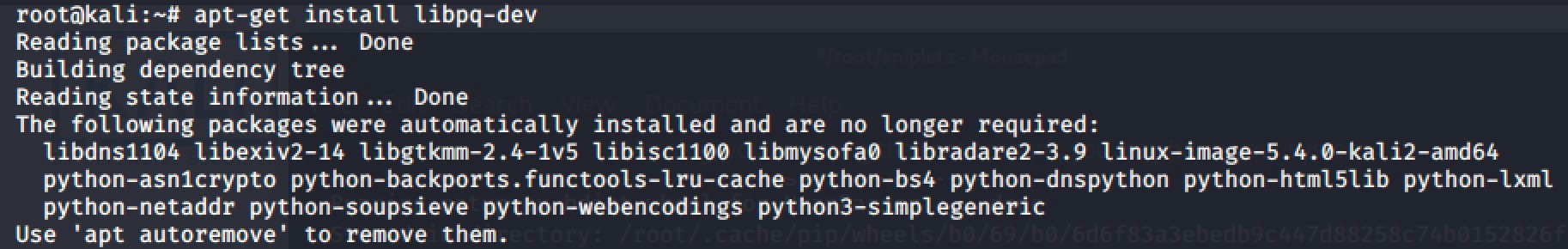
We install libpq-dev.
apt-get install libpq-dev
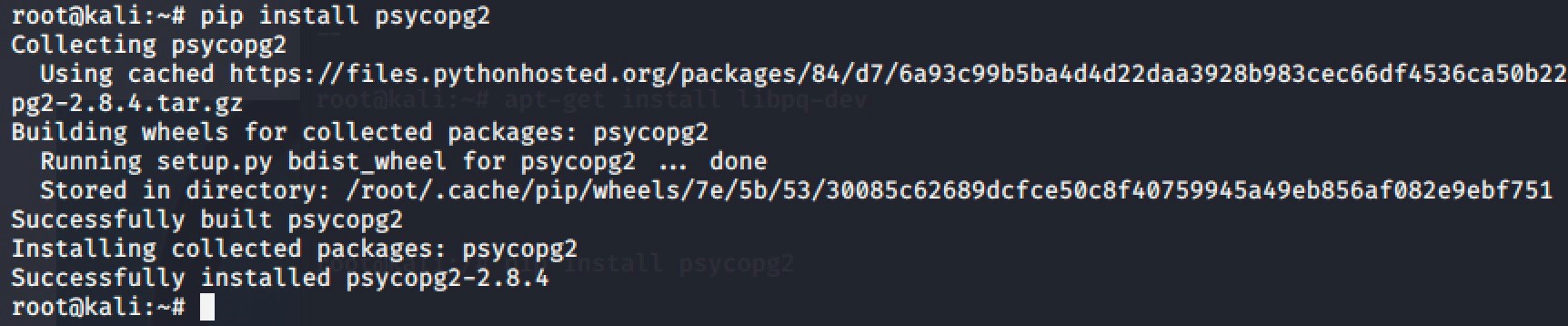
And finally we install psycopg2.
pip install psycopg2
Yes, this was the tedious part of our exercise, but in Part 2 we focus on the fun part and we’ll use Maltego to start visualizing!
About the author
Joerg Riether specializes in the fields of information security, high availability, storage and virtualization. During the last 20 years he has developed numerous projects and wrote publications in said fields.