About Incident Response 🔗︎
The threats to companies are increasing despite growing expertise and investments in IT security. Companies can no longer protect themselves effectively through prevention alone. It shows that most organizations can’t detect initial intrusions (Attivo Survey, 2020) . Nearly two-thirds (64%) of respondents indicated that 100 days of dwell time . They must therefore be in a position to react correctly to events in IT systems. As soon as a company detect violation of their security policy and a raise a security incident , since those events mostly compromise sensitive personal & business data they needs to respond quickly (before major damage occurs). To be able to do this, the methodology of incident handling helps.
While focusing on incident response capabilities, the incident response methodology also underlies processes and procedures that can be applied to any security incident.
As we observe a rise in the number of security incidents, the IR handling processes helps with the use of attack categories to faster identify and scope the problem and apply different response strategies.
For example, the National Institute of Standards and Technology (NIST) categorizes the types of attack incidents as follows:
- External/Removable Media: An attack executed from removable media (e.g. flash drive or CD) or a peripheral device.
- Attrition: An attack that employs brute force methods to compromise, degrade, or destroy systems, networks, or services.
- Improper Usage: Any incident resulting from violation of an organization’s acceptable usage policies by an authorized user, excluding means from the above categories.
- Loss or Theft of Equipment: The loss or theft of a computing device or media used by the organization, such as a laptop or smartphone.
- Other: An attack that does not fit into any of the other categories.
Handling the given incidents is essentially the task of Computer Emergency Response Teams or Computer Security Incident Response Teams, also commonly known as CERT or CSIRT.
After an initial assessment of the situation, it is typically necessary to determine whether there is an imminent danger to life and limb (such as in the case of manufacturing and industrial plants), but also a risk of manipulation, sabotage, or exfiltration of sensitive data. If necessary, such a danger can be contained with immediate measures, whereby the attacker should not be made aware of the existence of the incident response activities if possible. The incident response team then attempts to identify the attacker’s current and past activities to a sufficient extent and observe them over a period of time to gain a picture of their capabilities, procedures and possible motives.
Information gathering is essential to tracing the activities of an incident. It ensures sufficient evidence identification and IOC development that will enable the IR team to assess and define the extent of compromise. In this critical stage of the incident response process, Maltego supports IR teams to gather intelligence from both public and paid data sources.
Typical Incident Response Processes 🔗︎
Incident response is the process designed to manage, contain, and—when possible—reduce the consequences of a cyberattack in a fast-paced and efficient manner. Maltego can help incident response teams carry out rapid analyses of digital artifacts that have triggered such a response protocol, align your operations with the best common practices, and shape your existing playbooks.
NIST Cybersecurity & Incident Response Frameworks 🔗︎
The National Institute of Standards and Technology (NIST) is an agency operated by the United States’ Department of Commerce which provides standards and recommendations for many technology sectors. These standards and recommendations are usually voluntary for industry but mandatory for government agencies.
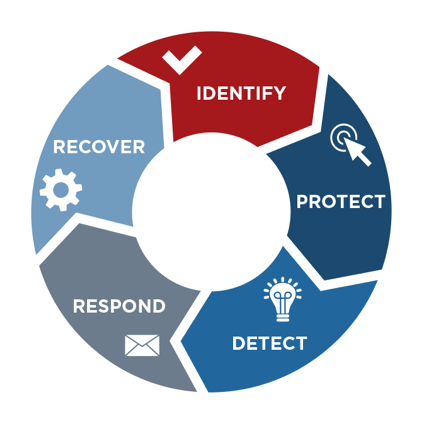
NIST created a high-level cybersecurity framework based on existing standards, guidelines, and practices for organizations to better manage and reduce cybersecurity risk and communications amongst both internal and external organizational stakeholders. The Framework consists of five key functions that provides a comprehensive view of the lifecycle for cybersecurity management:
The NIST Information Technology Laboratory (ITL) developed one of the most extended models for incident response (IR): The Computer Security Incident Handling Guide (Special Publication 800-61 ). The NIST incident response process is a cyclical activity featuring ongoing learning and advancements to discover how to best protect the organization. It includes the following stage:
The core of everything is the Incident Response Plan (IRP) which is a set of documented procedures detailing the steps that should be taken in each phase of incident response, including roles and responsibilities, communication plans, and standardized response actions.
MITRE ATT&CK & D3FEND Matrixes 🔗︎
During the last years, incident response teams have been overwhelmed as they have not been able to properly manage the growing landscape of threats that were impacting organizations in a persistently and impactful way. In the past, it was common to define some standard operational procedures (SOPs) aligned with the common types of triggers that detection teams were potentially detecting and handling. These observations were handed over to the response teams(IR-Teams). This approach was however not sufficient, so the discipline shifted towards actively using threat intelligence for a better understanding of the threat landscape: Enumerating threat actors, their tactics, techniques and procedures (TTPs), and tracking their ongoing campaigns mapped to specific indicators of compromise (IoCs) used in every single cyberattack.
In order to properly structure all the adversary information, MITRE ATT&CK Framework was born. The MITRE ATT&CK Framework is a globally accessible knowledge base of adversary tactics and techniques based on real-world observations. The knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community.
Most stakeholders in the industry follow this framework in order to align the generation of threat intelligence information (exchanged in well-known TIP platforms such as MISP or OpenIOC), detection signatures using standardized languages such as YARA, response capabilities such as the ones available in Security Orchestration Platforms (SOARs), and investigative OSINT/DFIR tools pivoting in digital online/offline evidence such as Maltego.
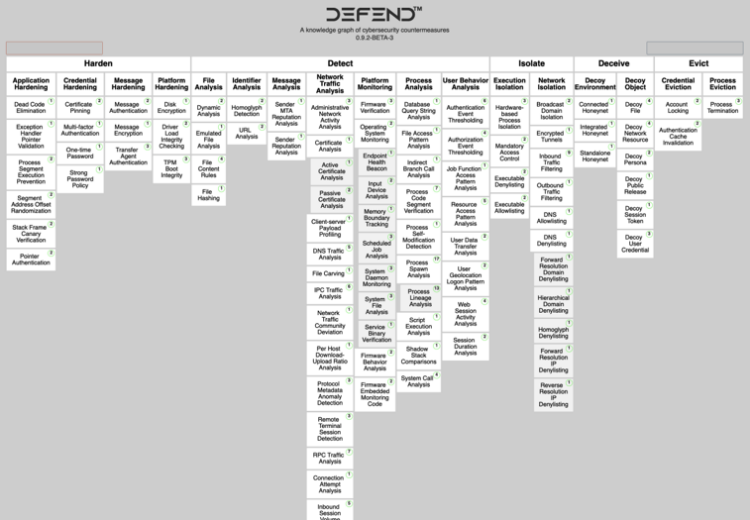
During the last year, a new complementary framework known as D3FEND was born to support defenders in order to encode countermeasures in a knowledge graph. It contains types and relations that define both the key concepts in the cybersecurity countermeasure domain and the relations necessary to link those concepts to each other.
Accelerating Your Incident Response Workflows from Hours to Minutes with Maltego 🔗︎
With Maltego, analysts will not need to spend valuable time switching between multiple tools or writing a report detailing their findings for other teams and decision makers to act upon. Instead, they can carry out their analysis with all available data within one interface in Maltego and present their results directly on the graph, which will help them reduce time during the triage and analysis phase.
This handbook is meant to serve as an example of how Maltego could be utilized in standard incident response workflows to streamline investigative efforts. It is not meant to replace any established practices or tools, but to present a solution to challenges some investigators might face.
Don’t forget to follow us on Twitter and LinkedIn and sign up to our email newsletter, so you don’t miss out on updates and news!
Happy investigating!