In our previous IPQualityScore article, we announced the launch of a small number of Transforms within the Maltego Standard Transforms that investigators can use to verify whether an email address exists, and return basic fraud indicators.
This time around, we will introduce you to one more set of IPQualityScore Transforms. This small batch is powered by IPQualityScore’s (IPQS) proxy & VPN detection API, and can help investigators identify if a given IP address possesses indicators of malicious intent such as fraud, as well as basic details about its provenance.
Using IPQualityScore Transforms to Investigate IP Addresses 🔗︎
Using the proxy & VPN detection API from IPQualityScore, investigators can gain precise and detailed information on a given IP address, such as the following:
- Is the IP address tied to fraudulent activity?
- Has the IP address been spoofed or anonymized?
- Basic footprint of the target IP address
- Pivoting from IPQS basic footprint on the IP address to advanced footprinting
Is the IP Address Tied to Fraudulent Activity? 🔗︎
These new IPQS Transforms allow analysts to obtain actionable information on an IP address for quick and effective decision-making on whether or not to block or flag traffic from a given IP address.
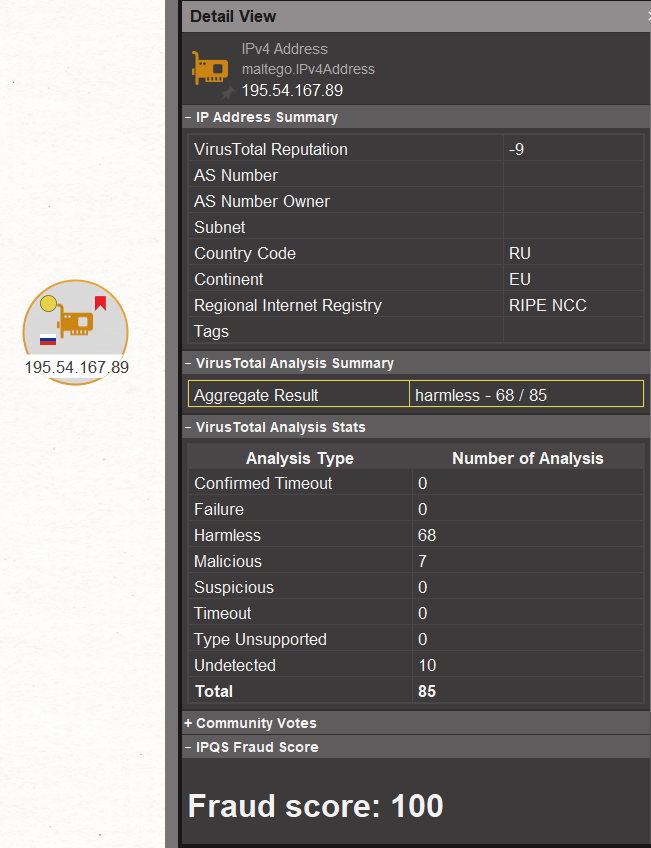
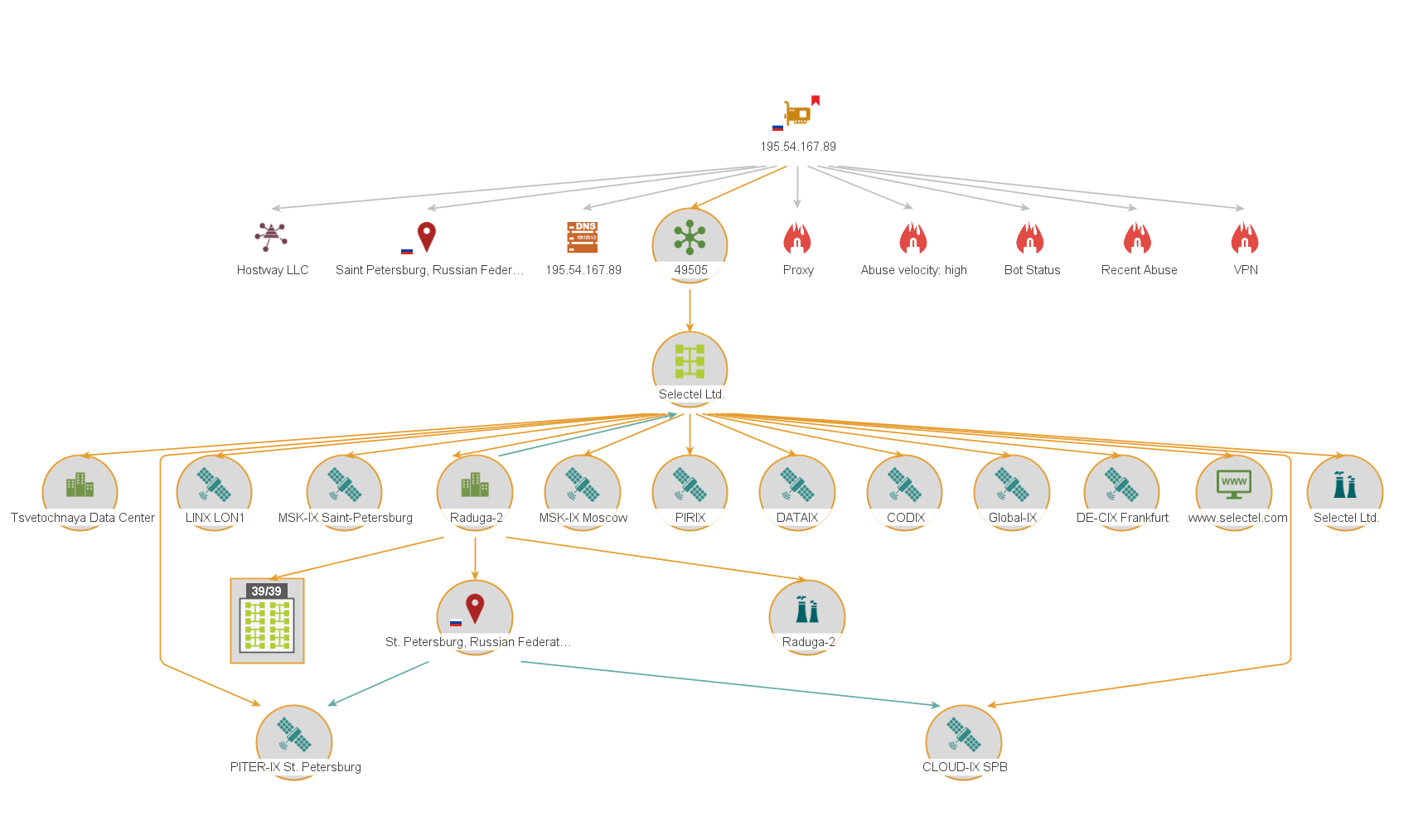
All you need to do is select an IP address and run the Fraud-check IP address [IPQS] Transform. This will retrieve the IP’s fraud score information from IPQS and add it to the Detail View in Maltego. It will also add a red bookmark on the upper-right corner of the IP Address Entity when the score is equal to or higher than 75.
Keep in mind that according to IPQS, while an IP address with a score >=75 is considered suspicious, it is also often a proxy, VPN, or Tor connection, but not necessarily tied to fraudulent activity. A high-risk IP address would have a score >=85 with abusive behavior presented in the previous 24-48 hours.
If, as on the image above, you encounter a potentially suspicious or high-risk IP address, pivoting to Transforms such as Annotate Ipv4 Address [VirusTotal Public API] from the VirusTotal Public API Hub item will help you better evaluate the potential risk. This Transform will pull in additional malware-specific information relating to the target IP into Maltego’s Detail View. It will also add a colored overlay on the upper-left corner of the Entity to inform us about the IP’s reputation score.
Digging Deeper: Has the IP Address Been Spoofed or Anonymized? 🔗︎
Conducting a rapid query to verify whether a given IP address is suspicious or high-risk has its advantages, particularly for SOC teams. However, an analyst often needs to dig deeper to understand the elements behind the score and to fully discard false positives that may impact the business.
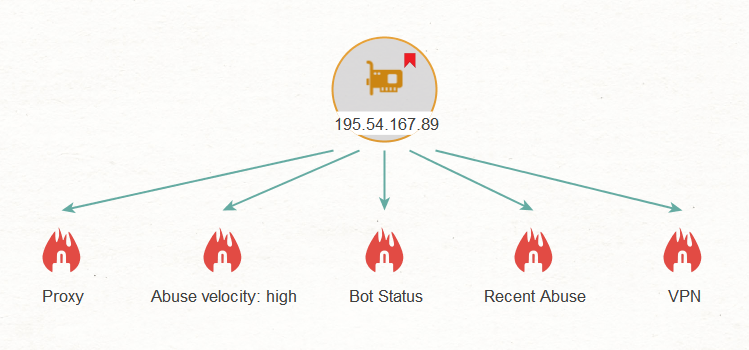
This is where the Get tags and indicators (VPN, Tor, Proxy, etc.) [IPQS] Transform comes in handy. As stated in its name, this Transform returns indicators (Tag Entities) on whether an IP address has been spoofed or anonymized, how often it has been abused, and how.
The tags are based on IPQS analysis and they include:
- Proxy: The IP is suspected to be a proxy (VPN, Tor, etc.)
- VPN: The IP is suspected of being part of a VPN, including data center ranges that may become active VPNs at any time
- Active VPN: Identification of active VPN connections used by popular VPN services and private VPN servers
- Abuse Velocity (none, low, medium, high): Indicates frequent abusive behavior over the past 24-48 hours
- Recent Abuse: Verified instances of abuse (e.g. chargeback, compromised device, fake app install, etc.)
- Bot Status: Recent use of the IP by bots or non-human traffic for automated fraudulent behavior
Running a Small Infrastructure Footprint 🔗︎
Lastly, the IPQS proxy & VPN detection API also allows analysts to access information on a given IP address such as geographical location, internet provider, and ASN. This data may help analysts with attribution for an exploit or allow them to pivot to different Transform Sets to continue enhancing their investigation.
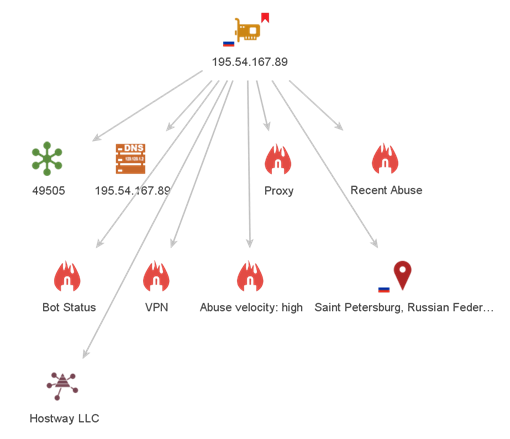
All the available information can be retrieved by running a single Transform: to Details (Location, DNS, ASN, Company] [IPQS]. As you can see below, now the IP Address Entity features a flag overlay on the lower-left corner which corresponds to the Location Entity on the lower-right side of the Maltego graph pictured below.
The Transform has also returned AS (Autonomous System) Number, DNS, and Organization Entities. The Organization Entity may represent the parent company or subsidiary of the listed service provider. Additionally, the Location Entity retrieves a clickable link for Google Maps which appears in the Detail View.
The insights gained with these new IPQS Transforms will help analysts to carry out investigations involving duplicate and fake users, click and advertisement fraud, payment and transaction fraud, and account takeover. They may also ultimately help update the rules and policies for the different tools used by SOC, as well as Trust and Safety teams, thus improving the organizational cyber resiliency.
Pivoting to Other Hub Items to Further Enhance the Investigation 🔗︎
As already stated, the IP Address Entity could be used to better assess with Transforms such as those from VirusTotal, the risk presented by a suspicious or high-risk IPQS fraud score.
Moreover, an AS number Entity would allow investigators to pivot to Transforms from different Hub items such as PeeringDB in order to continue the investigation.
For example, by selecting the AS Entity and running the To Network [PeeringDB] Transform, we can start running an advanced footprint.
And so, following the steps presented in the PeeringDB article, you would end up with a graph similar to the one above, which presents the related infrastructure and connections.
Access and Usage Limits of Maltego’s IPQS Transforms 🔗︎
As we mentioned in the previous IPQualityScore Transforms, these new IPQS Transforms are also included in the Maltego Standard Transforms Hub item and are free to use for both Community Edition (CE) and commercial Maltego users.
CE users will be able to run up to 50 Transforms per month for free, while commercial Maltego users can run up to 500 Transforms. Note that the requests will count towards the same usage as that of the IPQS Email Transforms.
If you need more Transform runs for IPQS, you can register for an IPQS account and plug in your own API key using the corresponding Transform settings in Maltego. Note that you may need to click the “Refresh” button on the Standard Transforms Hub item to make sure that these new Transforms are installed on your Maltego Desktop Client.
We hope you enjoyed this brief walkthrough of the new IPQS Transforms.
Don’t forget to follow us on Twitter and LinkedIn or subscribe to our email newsletter to stay tuned to more such product updates.



![Fraud-check IP address [IPQS] Transform](/images/uploads/ipqs001.png)