With the rise of crypto millionaires flooding social media feeds and the global adoption of cryptocurrencies, a new form of scamming prevails - fake cryptocurrency exchanges - luring new investors looking to be part of the winnings.
Below are some examples of the most common ways investors lose their money to scammers.
- Pig Butchering: Refers to how a target is “fattened up” before being butchered or slaughtered.
- Romance: People meet on social media, show their gains to others, and then convince them to “invest.”
- Rug Pull: A startup or influencer promotes a crypto token, solicits public investment, then vanishes with the cash or stops updating the project.
- Pump and dump: Artificially inflating a coin’s value by misleading statements and misrepresenting investor demand.
We have observed a current trend involving combining all four techniques, so how does it work?
Stage 1 🔗︎
It usually starts with the romance scam: Someone contacts a target via social media and pretends they were looking for someone else, but they establish a conversation that often results in an online relationship. The scammer takes time to build trust with their target. Throughout that process, the scammer also shows off their luxurious life and mentions that it is all thanks to “crypto investments.”
Once the trust is built, the scammer introduces their victim to the “Fake Crypto Exchange” where their target is guided on how to create an account and transfer money for the investment. The scammer does this in order to create a false sense of trust and control.
Stage 2 🔗︎
Here is where the pig butchering scam starts, although not all the victims of these “fake exchanges” go through stage 1, since some individuals find the sites by searching online and proceed to sign up and transfer funds to their own account.
These fake exchanges usually have dashboards where the victims will be progressively shown increasing “fake” gains over their investments, which further encourages the victims to continue adding more and more funds to their portfolio.
Stage 3 🔗︎
Rug pulls. At this stage, the fake sites will be shut down without a trace, leaving the victims empty-handed. Often, one final attempt will be made to extort even more money from the now frazzled investors. The scammers will reach out and promise to pay out the victim’s funds and winnings once an additional deposit is made for “taxes owed”.
Unfortunately, the victim will often comply, and the organization will shut down and disappear with all their victim’s money.
Finding the Domains behind Fake Cryptocurrency Investment Platforms 🔗︎
I began my investigation by using Reddit as a crowdsourcing tool to find possible scam sites posing as legitimate crypto exchanges. For this investigation, I will focus on Free integrations so that anyone can follow along.
I am going to leverage the subreddit known as r/Scams which is a room or board used by people to discuss/get help on different scams.
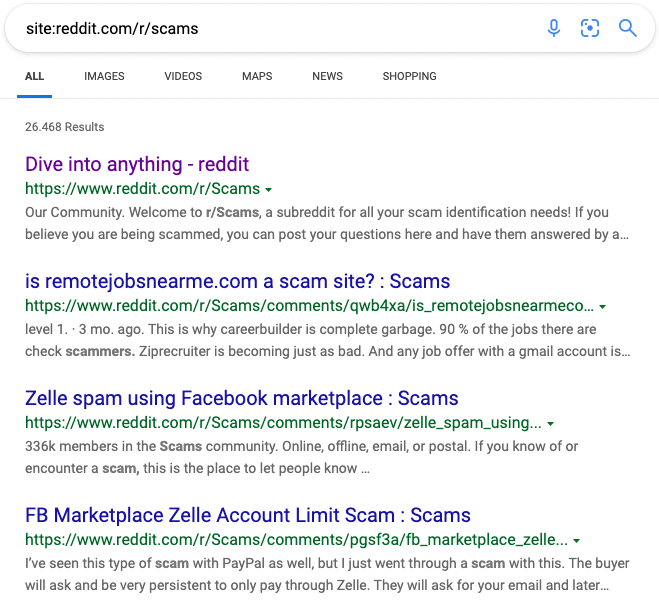
Let’s take a look at how this subreddit looks like.
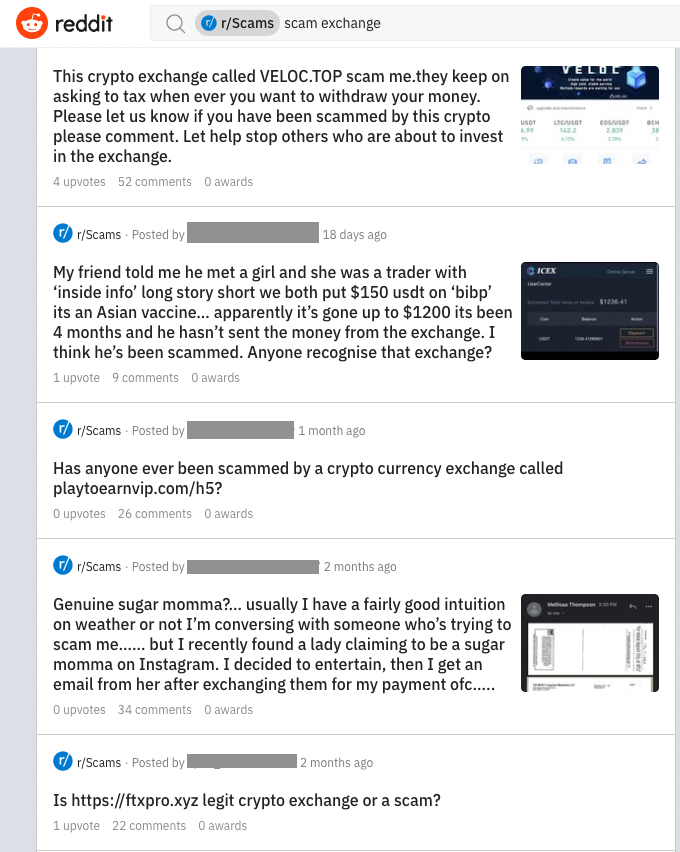
Let’s now add a couple of keywords to the search box to narrow the results.
As we can see, the results are more related to mentions of fake crypto sites, but we still need to extract all the domains and analyze them to separate the legitimate ones from the bad ones.
Ok, let’s start from the beginning; let’s extract all the different posts from Reddit and import them into Maltego for analysis.
I’m going to start by using a technique known as “Search Engine Dorking,” a way to interrogate a web browser for specific information.
To replicate our search inside Reddit, I will ask my browser to return results only for the r/Scams Subreddit.
site:reddit.com/r/scams
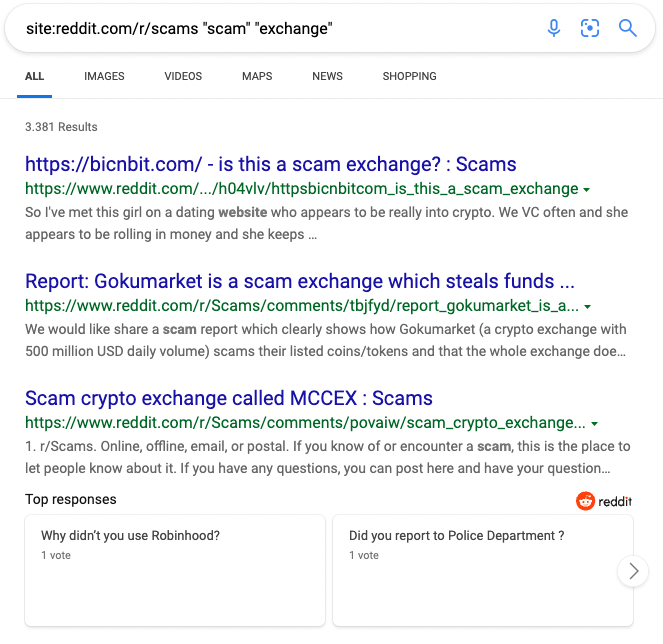
Great, now let’s add the keywords “scam” “exchange” to retrieve only results that mention those words.
Fantastic, now that we understand how to get the posts that we want directly on the browser, we can use the Bing Search Transforms in Maltego to move on to the analysis
I will add a new Phrase Entity to the graph, enter site:reddit.com/r/scams “scam” “exchange” and run the To Website [using Search Engine] Transform. You can read more about Dorking in our blogpost Maltego Dorking with Search Engine Transforms Using Bing
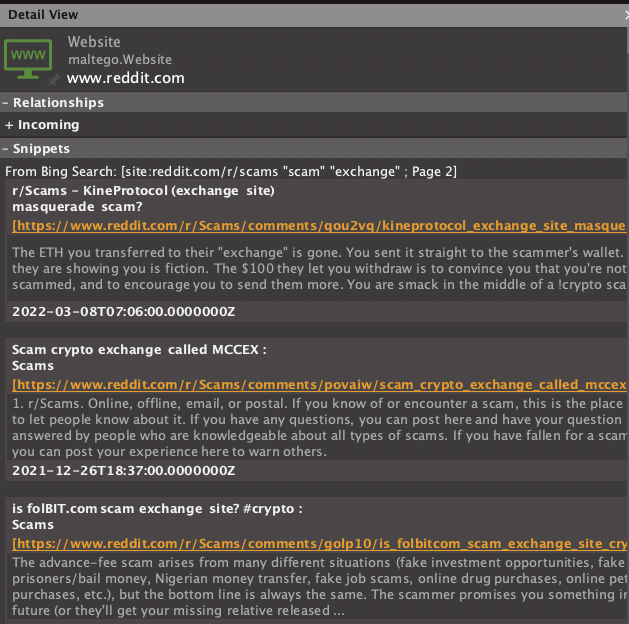
We can see that running this Transform created only one website Entity, but that does not mean Maltego could not find all the different pages associated with our search. If we look under the Detail View window in Maltego, we will see all the other posts retrieved and their URLs.
For the next step, I will extract the URLs from the website Entity by running the To URLs [show Search Engine results] Transform. Maltego returned 135 URL Entities, so let’s take a quick look at some of them.
Great, we are almost there. Now, I need to extract the Domains mentioned on the posts so that we can review them. The To Regex Matches [Found on web page] Transform can help us extract information from URLs based on Regular Expressions.
Regular expressions are particular types of strings used for describing a search pattern. Read this article if you want to learn more about Regex. You can think of regular expressions like wildcards on steroids.
I will use the following string to search for domains:
([a-zA-Z0-9-_]+\.)*[a-zA-Z0-9][a-zA-Z0-9-_]+\.[a-zA-Z]{2,10}
This Transform created 242 new Entities (Purple circles) based on the Regex expression that we defined. Let’s zoom into a section of the results to see what the new Entities look like.
We can see some legitimate domains mixed with the suspicious ones, as well as domains mentioned on multiple posts.
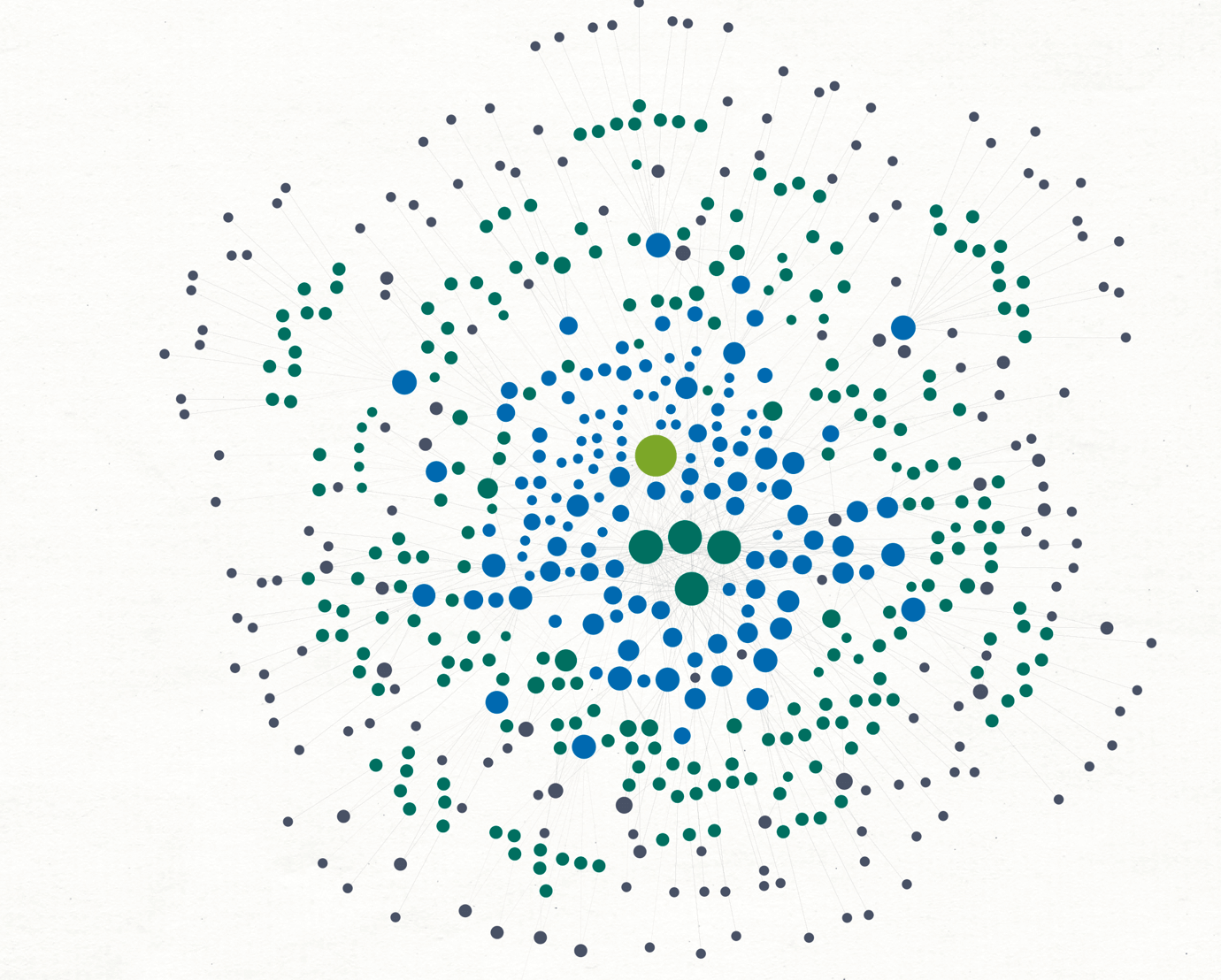
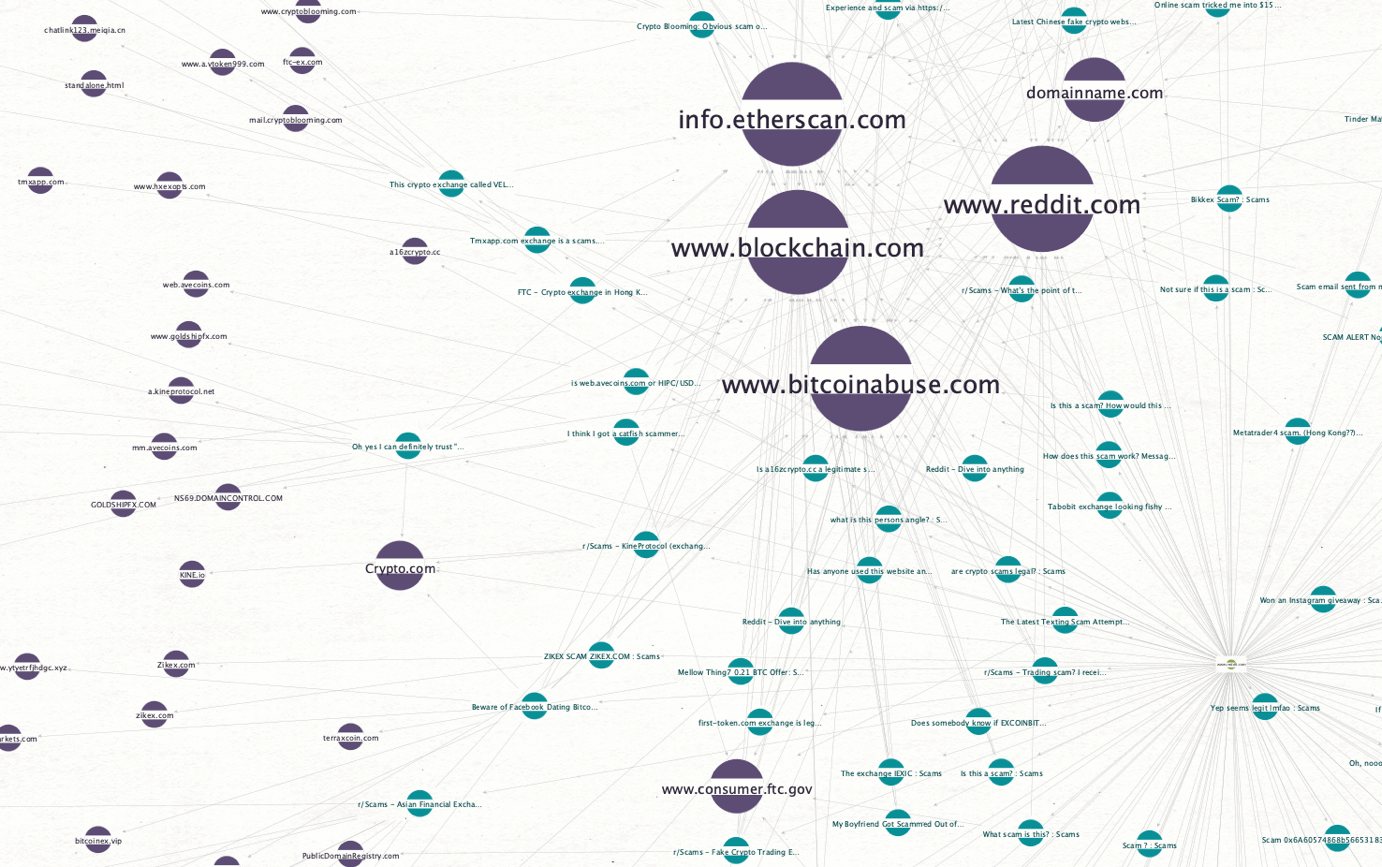
We can use the Views and Layouts to understand which results are mentioned the most. Let’s change the view to Ball Size by Links (Incoming) and the layout to Organic.
We can see right in the middle that 4 Entities are far more prominent than the others:
These are all legitimate domains: Etherscan and Blockchain are used for tracking Ethereum and Bitcoin transactions, respectively. Bitcoinabuse follows Bitcoin addresses reported for different reasons, and Reddit is connected to all the posts since that’s our source.
As we mentioned before, there are legitimate domains mixed with the different reports, so we will use Scamadviser to help us differentiate between the legitimate and the scam sites.
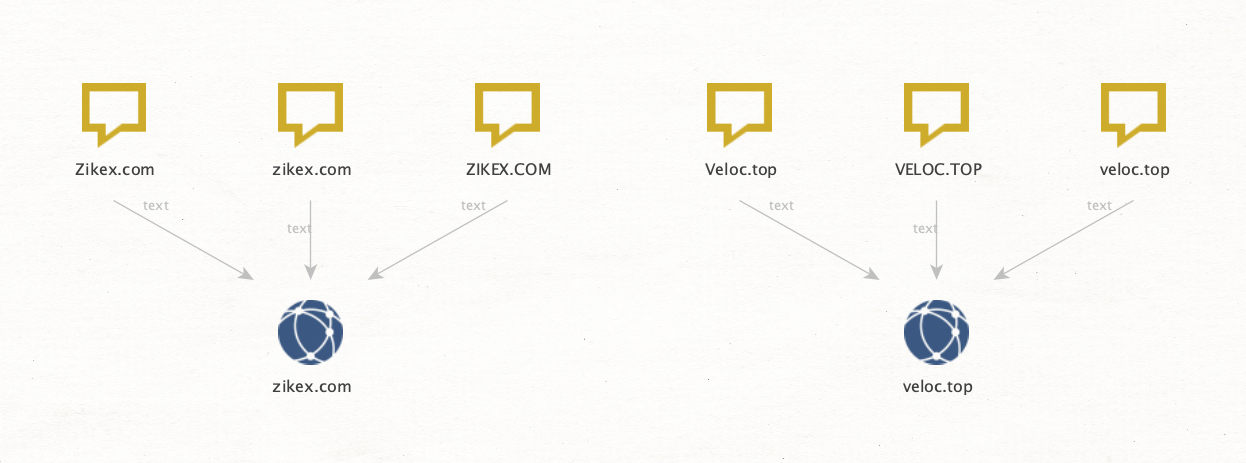
But first, I need to convert the Phrase Entities into Domains. Let’s select all the Phrase Entities and run the To Domains [within Properties] Transform. This will allow us to use Scamadviser to get information on risk scores associated with the domains.
This is a subset of the results, but you can see how Maltego extracted the domain names from the Phrase Entities. It also helped us remove duplicates created by the different spellings used for some domains on the Reddit posts. Below are a couple of excellent examples.
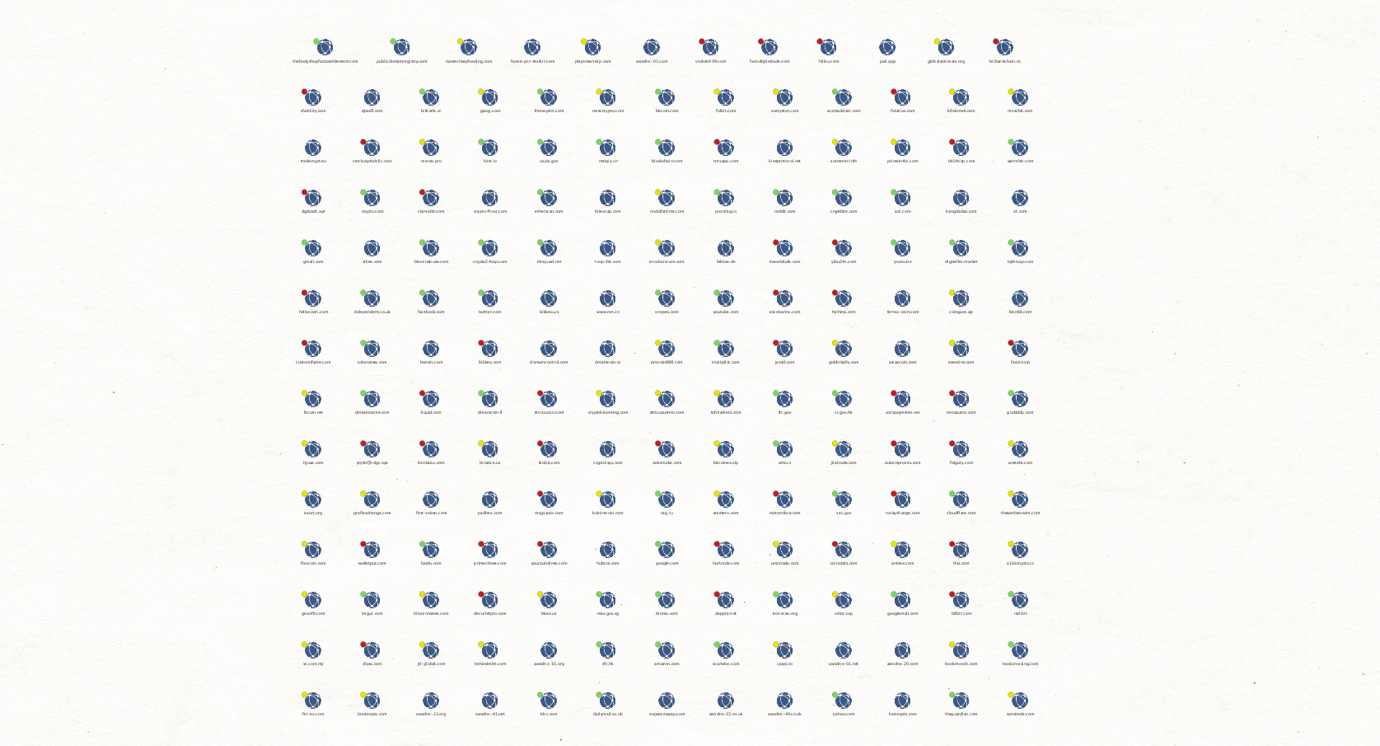
Now that we have all the Domain Entities in the graph, we can run the Annotate Domain (Live Scan) [Scamadviser] Transform to get the latest details from Scamadviser, such as the website’s title, description, SSL Certificate information, and the risk scores assigned to each domain.
Scamadviser also adds a small Overlay to the Domains with a color that reflects its score (Red=Low/Bad, Yellow=Medium/Suspicious, Green=High/Good).
Let’s focus on the ones with the lowest scores for now. We can select the ones with the red overlays and move them to a new graph for the next step.
As mentioned at the beginning of this article, the websites used for these scams tend to have short lifespans. I wouldn’t be surprised if a significant portion of these have already moved onto another domain and websites. An easy way to check whether any of these domains are still serving any content is by looking for websites associated with them. Let’s select all the domains and run To Website [Quick lookup] Transform.
In this case, we can see that most of the domains returned websites associated with them. I would like to know where these sites are located, and which service providers are most commonly used by these scammers to host their websites.
Let’s select all the website Entities and run the To IP Address [DNS] Transform to get the IPs connected to the websites, and we will run a couple of Transforms to get the information on ISP and Location from these IPs.
And now, let’s select the IP Addresses and run the To ISP [AbuseIPDB] and To Country [AbuseIPDB] Transforms.
Most of the sites are being protected by Cloudflare and are based out of the US. Some websites are being served from more unique ISPs such as OVH and Digital Ocean.
Let’s see if we can find other websites connected with the current ones. As I mentioned before, some of these sites will eventually be shut down by the scammers, but they usually have a new domain/website ready for the next victim.
Let’s take the websites to a new graph and run the To Relationships [BuiltWith] Transform. This will query BuiltWith for information such as IP Addresses and Tracking Codes used by these sites.
We can see many results from these websites, but we are interested in the tracking codes at this stage. Web admins use these codes to track their site’s visitors and track their activities on different pages. Often times, these administrators will reuse these codes on other websites which can then be linked back to them thanks to the Tracking codes.
Let’s remove the “ip” results so that we can run the next Transforms on the tracking codes only.
Now that we have only the tracking codes, let’s select the BuiltWith Entities and run the To Websites [BuiltWith] Transform on these.
The Transform returns many results. If we look closely, we will see that some of these sites are variations of the names from the original website, some of them have entirely different names but their logos (favicons) confirm these are probably used for the same purpose as the original ones, and some other don’t look anything like the original website, likely because the scammers were diversifying their scams.
What we were able to find during our investigation 🔗︎
- 135 Reddit posts mentioning both scams and exchanges.
- 181 Domains extracted from the posts.
- 102 Websites connected to 29 high-risk domains.
- 81 Medium to High-Risk domains according to Scamadviser.
- 16 Unique Tracking Codes (Google Analytics, Alexa, Facebook, etc.)
- Cloudflare and Namecheap are among the most used ISPs by this subset of scammers.
- United States infrastructure is used heavily by these groups.
Maltego was fundamental in finding, extracting, parsing, and analyzing the data from Reddit and it helped to reduce the noise presented by false positives (legitimate domains) while drawing connections between the high-risk domains and their associated infrastructure (websites, IP addresses, Internet Service Providers).
Don’t forget to follow us on Twitter and LinkedIn and sign up for our email newsletter to stay updated on the latest news, tutorials, and events.
Happy Threat Hunting!




![Add a new Phrase Entity, enter enter site:reddit.com/r/scams “scam” “exchange,” and run the To Website [using Search Engine] Transform](/images/uploads/fake-crypto-exchanges_6.png)
![Run the To URLs [show Search Engine results] Transform](/images/uploads/fake-crypto-exchanges_8.png)
![Run The To Regex Matches [Found on web page] Transform](/images/uploads/fake-crypto-exchanges_9.png)

![Select all the Phrase Entities and run the To Domains [within Properties] Transform](/images/uploads/fake-crypto-exchanges_13.png)
![Run the Annotate Domain (Live Scan) [Scamadviser] Transform](/images/uploads/fake-crypto-exchanges_15.png)
![Run To Website [Quick lookup] Transform](/images/uploads/fake-crypto-exchanges_17.png)
![Select all the website Entities and run the To IP Address [DNS] Transform](/images/uploads/fake-crypto-exchanges_18.png)
![Select the IP Addresses and run the To ISP [AbuseIPDB] and To Country [AbuseIPDB] Transforms](/images/uploads/fake-crypto-exchanges_19.png)
![Take the websites to a new graph and run the To Relationships [BuiltWith] Transform](/images/uploads/fake-crypto-exchanges_20.png)

![Select the BuiltWith Entities and run the To Websites [BuiltWith] Transform](/images/uploads/fake-crypto-exchanges_22.png)