Project Hades, the brainchild of the Anti-Human Trafficking Intelligence Initiative (ATII), provides researchers with a wealth of information related to darkweb onion sites.
The Project Hades dataset includes information on the existence of various onion sites as well as critical information those sites may contain, such as email addresses, cryptocurrency addresses, SSH keys, favicons, and other identifiers that can allow investigators to build connections. The sites that Project Hades monitors cover an assortment of illicit activity, ranging from weapons sales to document fraud to CSAM (Child Sexual Abuse Material).
Using Project Hades data in Maltego allows investigators to create compelling visualizations of connections between darkweb sites. And, by facilitating easy access to a wide arrangement of data sources in a single UI, Maltego also allows Project Hades data to be combined with information on cryptocurrency movements, domain registrations, social media profiles, and more.
WannaBuy Investigation with Project Hades 🔗︎
Let’s take a look at the Russian- and English-language underground shop WannaBuy. WannaBuy is dedicated to the sale of compromised remote desktop protocol (RDP) servers which can be used for a variety of cybercriminal schemes, ranging from ransomware operations to tax fraud. WannaBuy exists only on the darkweb.
Image 1: Screenshot from the WannaBuy home page.
The homepage for WannaBuy is located at wannab666qqm2nhtkqmwwps3x2wu2bv—————[.]onion. Let’s put that into the Maltego as a Tor Onion Website Entity.
To learn more about this site, let’s run the Transform [PH] Fetch Website Title.
The information returned indicates that this site brands itself as the WannaBuy homepage, which checks out with our understanding of this site.
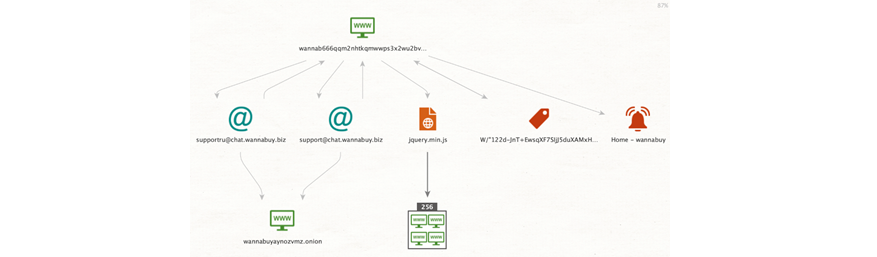
Now let’s try to get more insights on the site by running the Transform [PH] Fetch Selectors. This Transform returns information that appears on the site, such as cryptocurrency addresses, emails, Google Tags, SSH Keys, and more.
In this case, the Transform returns a few results: an eTag, a JavaScript file, and two email addresses. The email addresses are:
- supportru@chat[.]wannabuy[.]biz
- support@chat[.]wannabuy[.]biz
We know that WannaBuy is a Russian- and English-language shop, and from the emails it appears that the site has also dedicated support channels for English and Russian speakers (the “ru” in one of the email addresses stands for Russian).
The returned Entities may provide us with interesting connections to other darkweb sites. Let’s select the four Entities (the two email addresses, the JavaScript file, and the eTag) and click the double play button on the top level of the Transform Menu to run all the Transforms from the Project Hades Hub item that can be run against these Entities. Those Transforms are:
- [PH] Search by Email
- [PH] Search by ETags
- [PH] Search by JavaScript
After running these Transforms, we discover that the ETag only appears one time within the Project Hades dataset, on the WannaBuy site.
We also find that the JavaScript file appears across hundreds of sites. The screenshot above shows 256 results returned, but this is because the Maltego client used for the investigation had capped Transform results at 256. This limit can be adjusted using the Results Slider under the Investigate Tab. Given the considerable number of results as well as the generic name of the JavaScript file (jquery[.]min[.]js), this selector and the results that we found connected to it are likely not critical to our investigation into WannaBuy.
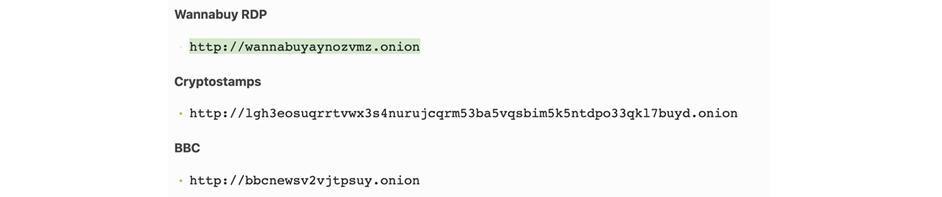
However, both email addresses appeared on another site: wannabuyaynozvmz[.]onion.
Hey, that site looks familiar! In the onion URL, we can see the name “WannaBuy” appear again. When we check the site, it seems to be offline.
It is possible that this WannaBuy website we just discovered is an older and disused URL.
WannaBuy Investigation with Wayback Machine 🔗︎
We can check this hypothesis by checking cached results for the popular onion directory site dark[.]fail. Many threat actors and researchers alike reference dark[.]fail to stay on top of the latest onion addresses for popular onion sites ranging from the official darkweb version of Facebook to criminal markets.
Let’s open a new Maltego graph with a website Entity for dark[.]fail.
The Maltego Standard Transforms include Transforms that allow users to access historical snapshots of different websites via information from the Wayback Machine. The associated Transforms are:
- To Snapshots [Wayback Machine]
- To Snapshots between Dates [Wayback Machine]
As their names suggest, the first Transform searches across all time, while the second can have a specific date range input. In this case, we don’t have a strong sense of when this old WannaBuy URL might have been used, so we will run To Snapshots [Wayback Machine].
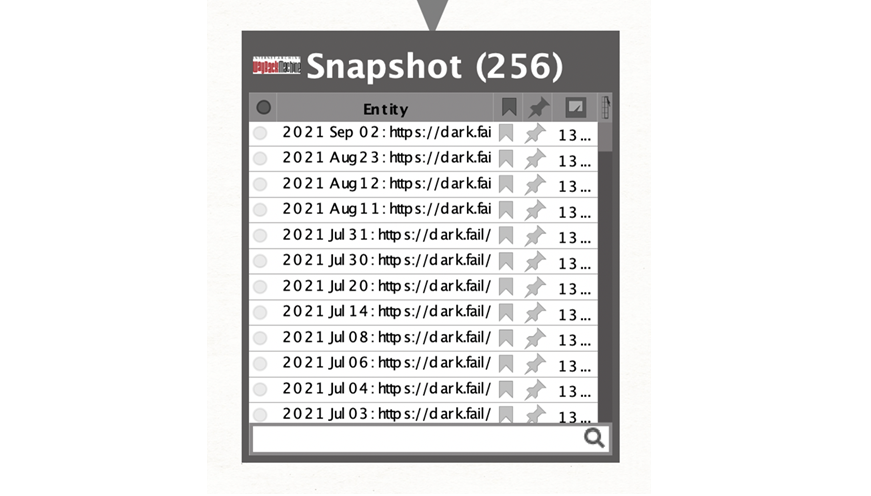
Note: We received 256 results, due to the restrictions set in the results slider. When we zoom into our graph, we can see more details about the individual results. The most important detail for this investigation is the dates.
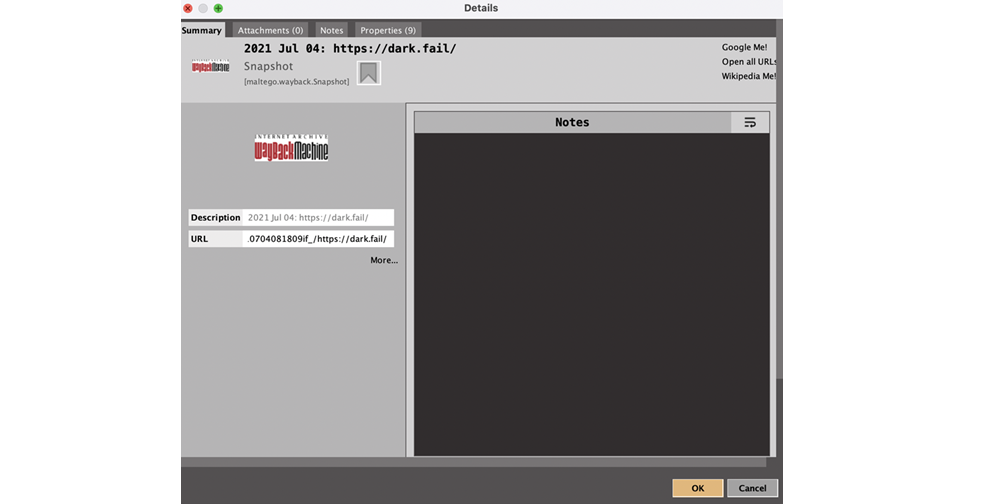
Now, we enter the manual part of our investigation, where we check the different results one by one to see if we can find a Wayback Machine result for dark[.]fail that includes information on the old WannaBuy URL. Lucky for you, I’ve already done that! Let’s examine the result from July 4, 2021. Double click on the entry for July 4, 2021, to pull up the Details View.
We are interested in the URL that appears in the Details View: hxxps://web[.]archive[.]org/web/20210704081809if_/hxxps://dark[.]fail/
Let’s copy that and paste it into our browser. If we search for WannaBuy on the list, we will eventually find it…
It’s the WannaBuy URL that we found earlier! Now we can confirm that this URL is indeed an old URL used by WannaBuy.
Don’t forget to follow us on Twitter and LinkedIn and sign up for our email newsletter to stay updated on the latest news, tutorials, and events.
Happy investigating!


 4.5 rating
4.5 rating





![Run the Transform [PH] Fetch Website Title in Maltego](/images/uploads/heads-atii_003.png)
![Run the Transform [PH] Fetch Selectors in Maltego](/images/uploads/heads-atii_004.png)

![Run To Snapshots [Wayback Machine] Transform in Maltego](/images/uploads/heads-atii_008.png)