We originally presented this case study at the Digital Experience Nordic 2025 event earlier in April. Given the positive feedback from the audience and requests from the customers, we decided to share it with our broader network and community. This article reflects on the role of OSINT in incidents like the Örebro school shooting, focusing on incident response and how tools like Maltego can assist in high-risk public safety scenarios. Before we begin, our thoughts are with the victims and all those suffering their loss.
The Role of OSINT in Responding to Hybrid Threats 🔗︎
Open Source Intelligence (OSINT) is not a silver bullet; it won’t solve an incident on its own, nor can it replace traditional investigative methods or frontline policing. However, with the rise of emerging hybrid threats, which often span both the digital and physical realms, relying solely on conventional approaches is no longer sufficient. These threats blend cyberattacks, disinformation campaigns, and online radicalization with real-world violence, infrastructure sabotage, or coordinated unrest, requiring a systematic and adaptive response.
This is where OSINT plays a crucial role. By integrating OSINT into investigative workflows, law enforcement and security professionals can respond more swiftly and effectively. OSINT helps identify and profile suspects, map their digital footprints, uncover their networks, and gather corroborating evidence across open sources, all in near real-time. When used alongside traditional methods, OSINT strengthens situational awareness, shortens investigative timelines, and enhances the ability to anticipate and mitigate complex threats. In rapidly evolving situations that threaten public safety, it’s critical for law enforcement agencies to respond with speed and broad intelligence coverage. Let’s explore in detail how OSINT helps them to act fast.
How OSINT Helps LEAs 🔗︎
Law enforcement agencies worldwide are increasingly leveraging OSINT, especially during high-profile incidents that pose risks to public safety. OSINT plays a vital role in enhancing real-time decision-making, improving situational awareness, and supporting post-incident investigations. For example, since the start of the Russian invasion of Ukraine, OSINT has been key in tracking troop movements, verifying missile strikes, and uncovering war crimes, including widespread cyberattacks. Let’s dive into how real-time situational awareness—before, during, and after incidents—can make all the difference. To learn how the Ukrainian Cyber Police use OSINT and Maltego to protect their citizens, click here.
Real-Time Situational Awareness: Before, During, and After the Incident:
-
Before the Incident: Proactive monitoring of open sources can alert LEAs to emerging threats. By analyzing patterns in online chatter, event planning posts, or suspicious activity in forums and social platforms, investigators can detect potential risks before they escalate. Keyword alerts, geospatial data, sentiment analysis, and features like Echo—the AI case assistant in Maltego Monitor— enable agencies to anticipate incidents and prepare appropriate responses in advance.
-
During the Incident: In the midst of crises, such as terrorist attacks, natural disasters, or mass shootings, OSINT delivers critical, real-time information to LEAs. Social media posts, live-streamed videos, and geotagged images from eyewitnesses on the ground often provide faster, more granular insight than traditional intelligence channels. For example, monitoring keywords like “breaking,” “first visuals,” or “shooter spotted” can help surface first-person views and footage, offering immediate situational awareness.
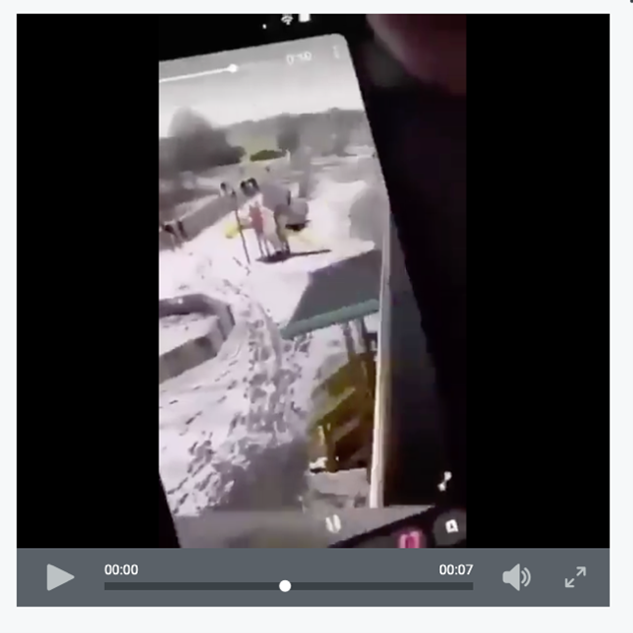
OSINT can also support the geolocation of visual content to confirm the location of events, validate reports, and track movement patterns. In parallel, LEAs can use OSINT to detect and counter disinformation campaigns or harmful narratives, such as deepfakes or fake news, that can spread quickly during the chaotic events and heighten public panic. For example, within the first 20 minutes of an incident, Maltego Monitor surfaced the first visuals of the shooter, captured by a bystander through their window. This provided critical intelligence, including the type of weapon used and the potential direction of movement, helping agencies respond faster and more effectively. -
After the Incident: Following an event, OSINT becomes vital in the investigative phase. LEAs use it to identify suspects, uncover motivations, and trace digital footprints. It aids in verifying alibis, mapping relationships between individuals or groups, and understanding whether the incident is part of a broader organized effort. OSINT also plays a key role in gathering legally defensible evidence, helping agencies build stronger cases that can stand in court. By preserving and contextualizing digital traces, investigators can establish timelines and corroborate findings with other sources.
Post-incident OSINT investigations also help analyze the long-term impact of events. Agencies can monitor signs of online radicalization or community polarization that may increase the likelihood of future incidents. Understanding how narratives evolve after an attack enables authorities to address root causes and prevent recurrence.
In the demonstration below, we’ll walk you through how this type of post-incident investigation unfolds, showing how one piece of a clue can lead to a wider network of insight. A single thread may spark the weave, but only a full tapestry tells the whole story. With Maltego, that first lead can unravel a broader truth. Keep reading!
Integrating Maltego into Hybrid Threat Response 🔗︎
So, how does Maltego fit into this, and how does it enhance real-time situational awareness at every stage of an incident?
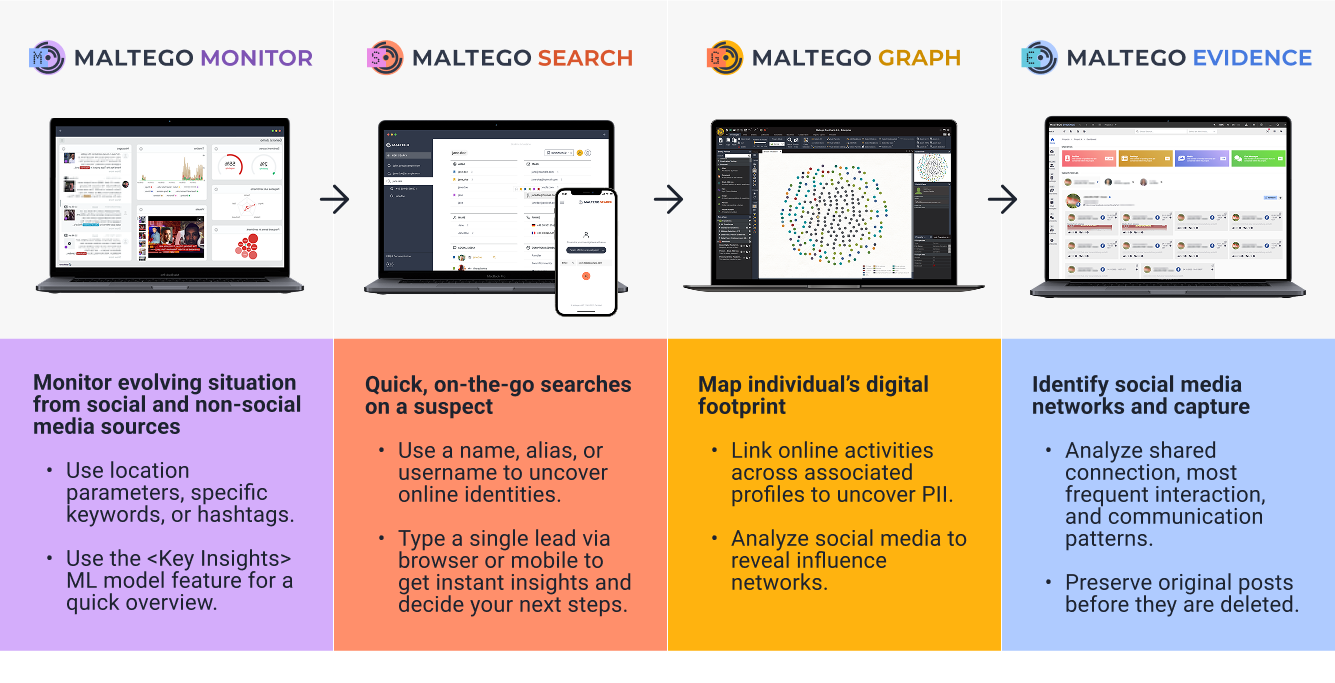
To start off, you can use Maltego Monitor to mine information from social and non-social media sources about the evolving situation. Based on location parameters or specific keywords and hashtags, LEAs can gather first-person accounts of the incident to crowdsource critical information. Using Key Insights ML models, such as those trained on physical attacks, analysts don’t need to spend hours deriving actionable intel. They can receive summaries of key developments within seconds, effectively gaining those crucial few minutes to focus on higher-priority tasks. Ongoing monitoring capabilities also enable LEAs to stay alert to emerging threats, such as a rogue shooter elsewhere or online chatter about similar incidents developing in other locations.
Simultaneously, you can use our Search and Graph capabilities to quickly deanonymize or map the digital footprint of an individual. Despite being online, a surprising amount can be uncovered, revealing someone’s activities and potential motivations. In the case of Taleb Amhedousen, who drove his car into a Christmas market crowd in Magdeburg, Germany, on December 20, 2024, within minutes of identifying his name, investigators were able to access forums he participated in, websites he had registered, and threats he had been making for months. This also opens the door to identifying influence networks—both what may have motivated the attacker and whether they’re connected to groups that could pose future risks.
To further expand the picture, it’s often essential to understand the attacker’s immediate environment—who they were in contact with, and what their online social network reveals. Maltego Evidence supports this by identifying shared connections, most frequent interactions, and communication patterns, helping investigators trace relationships that might otherwise remain hidden.
Investigating the Örebro School Shooting with Maltego 🔗︎
Now that you’ve read how Maltego’s all-in-one platform supports LEAs at every stage of an incident, let’s take a closer look at how it can be applied to post-incident analysis of the Örebro school shooting.
As law enforcement officials, in the aftermath of the incident, your focus shifts to identifying the perpetrator and understanding their network and motivation. You will work to address key questions such as: Who is the shooter? What might have motivated them? Are there any ideological drivers behind the attack? Could others be involved? What networks are linked to the perpetrator? Are there signs of threats, manifestos, or attempts to preserve evidence?
This is where Maltego’s investigative capabilities become especially valuable. It is well known for its strength in Person of Interest investigations and has supported many high-profile and sensitive cases for governments around the world. Starting from a single breadcrumb—such as a name, email address, or limited digital footprint—Maltego helps uncover hidden connections and build a full context of the case.
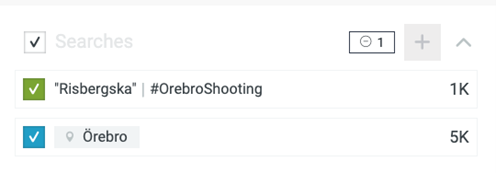
With those key questions in mind, we immediately initiated a monitoring case as soon as the shooting was reported. Using just two basic parameters, a geographic location block and a few targeted keywords, we began tracking real-time developments as thousands of messages started flooding in from various platforms on Maltego Monitor.
We quickly observed videos and images through applied filters and began identifying first-person accounts of the incident. For law enforcement agencies, this kind of direct insight from individuals on the ground offers immediate operational value.
Once the shooter’s name was made public through media reports, we pivoted to Maltego Graph to investigate his digital footprint. Starting with the name, Maltego Graph identified associated social media profiles and potential indicators such as email addresses and phone numbers linked to the target. One notable finding was a series of runs logged on Strava in Örebro, near the location of the shooting. However, in a classic OSINT pitfall, we soon realized that we had misidentified the individual. There was another person with the same name—Rickard Andersson. This is where the investigator’s skillset becomes critical: knowing how to stay focused on the objective and avoid getting lost in rabbit holes. Without a clear investigative direction, following misleading leads can result in significant time lost and potentially delay actionable outcomes.
As more details emerged in media reports, it became clear that the actual perpetrator led a reclusive life, making a direct investigation into his digital presence less fruitful. This led us to redirect our efforts toward his immediate network and family. Using Publicly Available Information (PAI), we identified several family members, some of whom had already begun scrubbing their digital footprints, likely to avoid public scrutiny or further association with the case.
Due to the sensitivity of the investigation and privacy considerations, we cannot share many of the specific findings presented during the event. However, we hope this gives you a clear sense of how OSINT supports high-stakes investigations, particularly in post-incident person of interest cases, and how Maltego enables you to uncover the full story starting from a single lead. This case illustrates both the power and the caution required in OSINT investigations and how Maltego’s tools enable flexible, multi-angle investigative workflows.
Happy investigating!
About the Author 🔗︎
Nitish Chandan
Nitish is a Senior Subject Matter Expert at Maltego with a background in trust and safety, product risk and compliance, and investigative work. At Maltego, he works closely with customers to understand their challenges and demonstrate how the platform supports their investigative goals. He helps teams unlock their full potential by developing tailored use cases and end-to-end workflows. His interests include the dark web, CSAM, cryptocurrency, and cyber threat intelligence. He also conducts investigations in response to emerging incidents. Follow him on LinkedIn to learn more.