In today’s rapidly evolving cyber landscape, security operations must stay ahead of increasingly sophisticated threats and manage vast amounts of data from diverse sources. Relying solely on a single tool or manual process is no longer sufficient. So, what should you consider when choosing a threat intelligence integration and analysis platform?
In this blog, we will highlight Maltego’s strategic approach to empowering cyber threat intelligence (CTI) teams, showcasing our holistic platform and benefits. Let’s first dive into what are the key trends shaping the field of CTI and the challenges that CTI professionals go through.
Essential Capabilities of a Holistic Data Integration and Analysis Platform for CTI Teams Benefits of a Holistic Data Integration and Analysis Platform for CTI Teams Table of Contents 🔗︎
Future of the CTI Landscape 🔗︎
In a world where significant advancements in technologies like artificial intelligence and machine learning dominate our everyday lives, it is evident that they will shape the landscape and future of cyber threat intelligence (CTI) over the next decade. These technologies will enable sophisticated, real-time threat detection, allowing organizations to predict and mitigate cyber threats before they materialize. However, they also pose new challenges, such as the cybersecurity workload created by the vast amounts of information generated by both humans and machines and high-level social engineering cyber-attacks that leverage these advanced technologies.
Although we recognize the importance and value of advanced technologies, especially as they pertain to the future for all practitioners in the CTI space, how can you facilitate more robust defense strategies and improve overall cybersecurity resilience at this time? There is a growing need to manage the full lifecycle of threat intelligence within a single platform. Such a platform should seamlessly integrate vast amounts of data from diverse sources, providing comprehensive insights into the threat landscape and threat actors’ behaviors. Additionally, as cyber threats become more complex, real-time collaboration and information sharing among organizations, industries, and governments globally will become essential. By efficiently working with data, organizations can enhance their defense mechanisms and stay ahead of evolving threats.
Challenges in CTI investigations 🔗︎
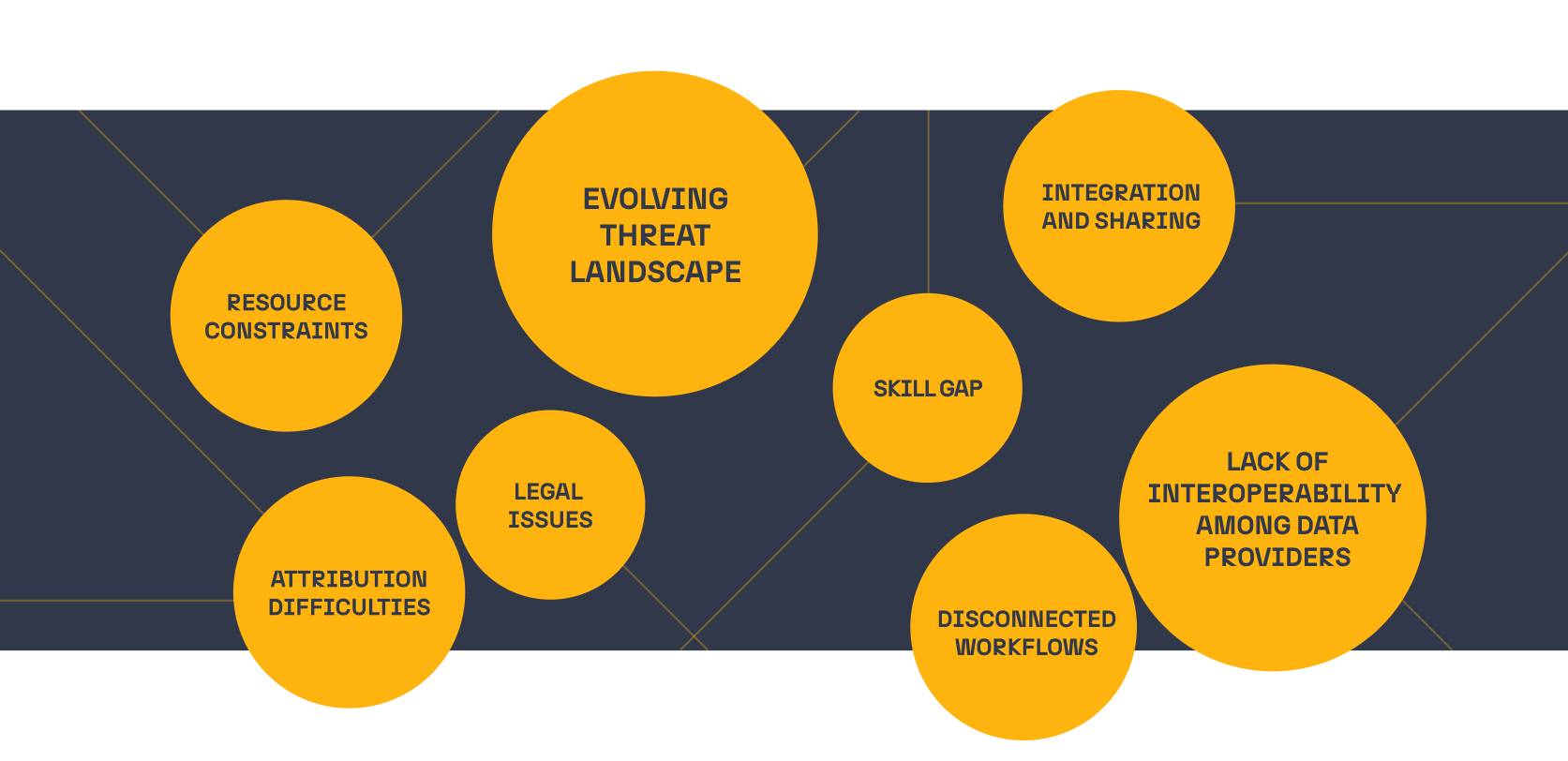
Despite the clear benefits technological advancements offer, they will simultaneously intensify the challenges in CTI investigations. Let’s explore several of the current challenges in CTI investigations.
CTI investigations encounter numerous challenges. Given the vast amount of data produced by various networks, devices, and sources, analysts require a platform to consolidate and visualize their data in an easily consumable manner. Threat analysts are forced to juggle several tools and platforms, each with myriad data sources, to cross-reference results. This process is further impeded by differences in pricing, plans, and licenses. All these aspects complicate and disconnect their workflows, making it difficult to efficiently sift through information and identify meaningful connections, regardless of their level of training. This slowdown is particularly critical in SOC operations, where time is of the essence.
Furthermore, as threat actors continuously develop new tactics, techniques, and procedures (TTPs), it becomes challenging for analysts to accurately attribute cyber-attacks to specific actors or groups. They need to acquire or purchase the most relevant tools and data for each effective investigation.
Additionally, resource constraints, including the need for skilled personnel, advanced tools, and continuous monitoring, can limit the ability of threat intelligence teams to conduct thorough CTI investigations. Integrating data from various sources seamlessly and ensuring the sharing of intelligence across different organizations and platforms is complex. Legal and ethical considerations, such as privacy laws and regulations, must be also navigated carefully to ensure compliance while gathering and using intelligence.
Finally, there is a persistent skill gap, with a shortage of cybersecurity professionals specializing in CTI. This makes it difficult for organizations to train and retain talent in this specialized field, not to mention fully leveraging each acquired tool to address new and specific challenges.
Essential Capabilities of a Holistic Data Integration and Analysis Platform for CTI Teams 🔗︎
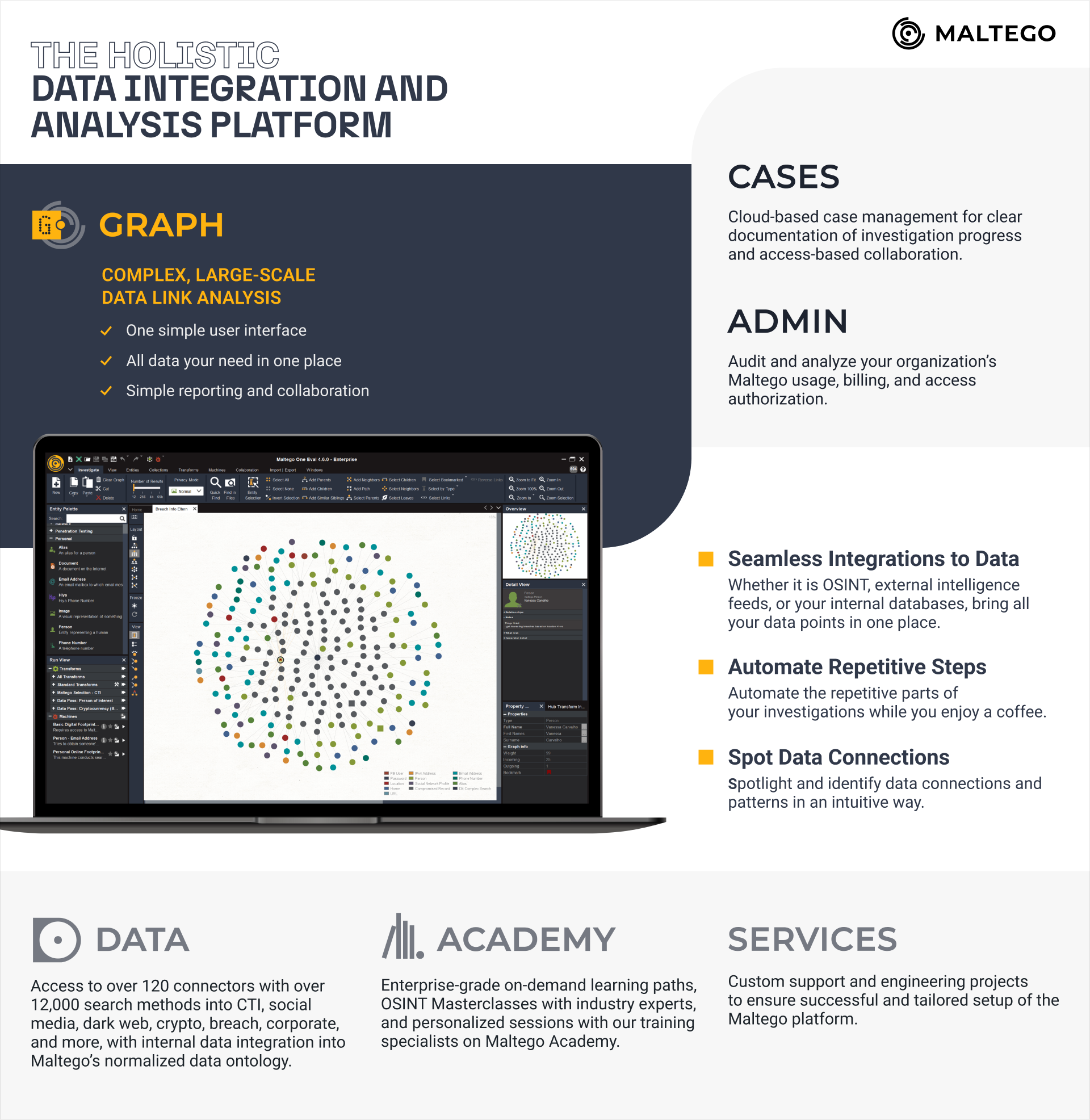
Maltego constantly evolves to enhance product capabilities with a user-centric approach. As introduced in our product roadmap, we truly focus on an intuitive, but holistic way for CTI professionals to centralize intelligence and manage data-led workflows in a single platform. Dive deeper into what Maltego has to offer for CTI teams.
Maltego Graph 🔗︎
Maltego Graph enables analysts to visualize and comprehend key information and connections in large and complex datasets via a straightforward user interface. Additionally, Maltego Graph can significantly cut down the time spent on investigations—from hours to minutes—by automating manual and repetitive tasks with Maltego Machines.
Maltego Data 🔗︎
The entire platform is powered by Maltego’s unique data, offering you access to all the data you need. It integrates over 120 different data providers and more than 12,000 search methods into CTI investigations, including data sources and tools like OpenCTI, Anomali, Splunk, and more. Our focus has been on streamlining workflow integrations, enabling you to centralize all relevant data from SIEM, TIPs, SOAR, OSINT, and internal databases into Maltego’s standardized data ontology.
Maltego Academy and Services 🔗︎
World-class experts offer both pre-recorded and custom live training sessions tailored to teams of any skill level, ensuring they make the most of Maltego. Additionally, custom support and engineering projects are available to guarantee a successful and personalized setup of the Maltego platform.
Maltego Cases and Admin 🔗︎
The team can store and collect all investigations in a single location and cross-correlate all data in a unified format to enhance collaboration. With administrative controls, the manager can audit and centralize your organization’s Maltego usage, billing, and access authorization, eliminating the need to manage these aspects separately for each tool.
Benefits of a Holistic Data Integration & Analysis Platform for CTI Teams 🔗︎
These essential capabilities translate into three main benefits:
Supercharge your Analysts 🔗︎
Empower your analysts with real-time intelligence and seamless internal and external data integration to enhance their efficiency and precision. By helping them bring up-to-the-minute threat data in one interface and ensuring smooth data integration across various sources, you enable them to perform their tasks more swiftly and accurately. This empowerment not only improves their effectiveness but also boosts their confidence and decision-making process, leading to a more robust security posture for your organization.
Identify Threats Faster 🔗︎
Achieve incident readiness and respond to incidents with unprecedented speed. By leveraging advanced threat detection and real-time intelligence with Maltego, your organization can rapidly identify potential threats and vulnerabilities. For example, Maltego allows you to directly take indicators from third-party sources and link them to your internal environment. This process helps identify previously undetected incidents, enabling swift incident response and minimizing the impact of security breaches. In doing so, you can ensure your systems and data remain secure. With faster threat identification, you can stay ahead of cyber adversaries and protect your assets more effectively!
Increase Return on Investment 🔗︎
Save time and money with an unparalleled intelligence analysis experience. By optimizing your CTI processes and tools, you can reduce the time spent on manual data analysis and streamline your threat detection workflows. This efficiency translates to significant cost savings, as your team can focus on high-priority tasks and strategic initiatives. Additionally, preventing business interruptions and potential financial setbacks caused by cyber incidents further reduces overall costs, ensuring your organization remains resilient and profitable in the face of evolving cyber threats.
Achieving Incident Readiness with Maltego 🔗︎
It all sounds promising, but you might wonder how to achieve these benefits. Below, you’ll see how your organization can proactively prepare for and respond to cyber threats by leveraging the power of threat intelligence. You’ll find resources to help you explore the full capabilities of Maltego, perfectly suited for a corporate environment.
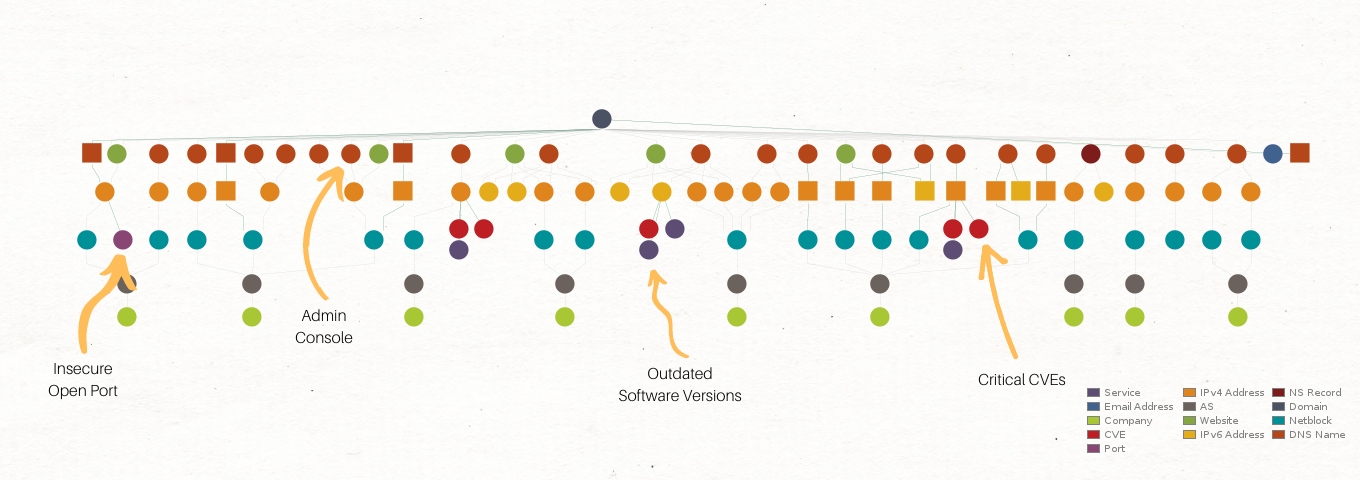
Identifying Exposure 🔗︎
Maltego enables teams to identify the exposure of digital assets or individuals who could be targeted through surface threat assessments and analysis of personal footprints. This enables organizations to understand and mitigate potential vulnerabilities before they are exploited. For example, your team can learn how to use Maltego for attack surface assessments here, or check out the playbook for vulnerability and attack surface assessment in use case 3 of this handbook.
Collecting and Disseminating Threat Intelligence 🔗︎
Maltego allows users to collect threat intelligence on potential threat actors from various data providers and disseminate this information to detection engineering and hunting teams. This process facilitates better detection and aids in the early identification of attempts or the early stages of attacks, enhancing the ability to preemptively counter threats. For example, you can refer to this white paper on cyber threat profiling of the known threat actor “Scattered Spider,” which introduces various methods for collecting and analyzing IoCs using Maltego.
Investigating Insider Threats 🔗︎
With Maltego, organizations can effectively investigate insider threats that may pose risks to the company. You can uncover and analyze behavioral patterns that indicate malicious activities within the organization, allowing timely interventions. By harnessing Maltego’s dark web integrations, the organization can proactively search for mentions of the company or sensitive data on hidden forums and marketplaces. For example, you can check out a step-by-step playbook for investigating insider threats here, which allows your team to replicate the same process.
Additionally, all investigations conducted on Maltego platforms are guided by three key principles. Maltego ensures the security of investigators’ identities and the data acquired, maintains compliant and transparent data collection and storage, and finally provides expert support for tool training, deployment, and individual setup tailored for your organization.
In conclusion, the rapidly evolving landscape and challenges of CTI demand innovative and comprehensive solutions. Our discussion has underscored the necessity of an all-in-one platform to effectively address these issues and showcased how Maltego’s strategic approach and product capabilities can empower CTI teams to meet the emerging demands of advanced investigations.
We hope this overview has provided a clear understanding of how Maltego enables your team to centralize data access, visualize vast amounts of information, and interpret it to uncover hidden truths. As a result, your team can respond to threats faster and reduce risks effectively. Having a holistic threat intelligence integration and analysis platform is invaluable and essential for successful CTI operations. Stay ahead of the curve with Maltego and ensure your organization is equipped to tackle the ever-changing threat landscape with confidence.
Stay connected with us on X and LinkedIn, and subscribe to our email newsletter to get updated with the latest news and developments.
Enjoy exploring all our resources!


 4.5 rating
4.5 rating