OAuth is an open standard for authorization which allows a resource provider (RP) to request access to a user’s resources from an identity provider (IDP) subject to the user’s approval. It is useful when a service needs to utilize the resources of another service. For example, the Maltego Standard Transforms read a user’s LinkedIn feed on their behalf without sharing login credentials with Maltego.
In Maltego, we use OAuth to allow our users to log into third-party providers with their credentials and have an access token returned to the tool. This access token can then be sent to the Transform Server, which in turn can request information from the provider on behalf of the Maltego user.
OAuth in Maltego is mostly used by clients who use or develop custom Maltego Transform integrations and would like to add user authorization functionality to their Transforms.
Currently, Maltego supports OAuth 2.0. However, OAuth 1.0a is still supported for backward compatibility purposes. There are different grant types which change the OAuth flow. Maltego natively supports the Authorization Code Grant flow.
Let’s have a look at how we can use OAuth in Maltego.
Integrating OAuth in Maltego 🔗︎
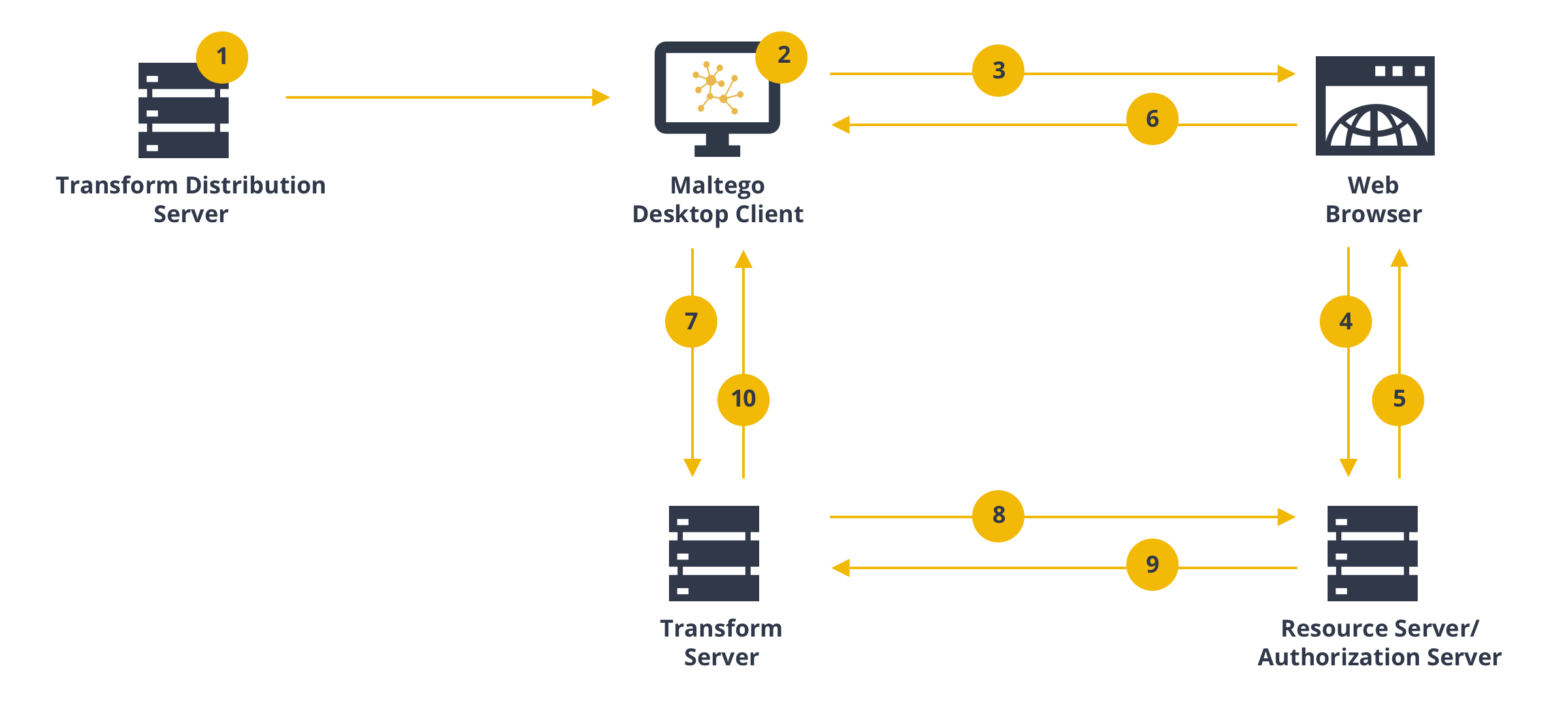
Initially, users must develop Transforms which use OAuth. This way, the Maltego Desktop Client will acquire the OAuth token on behalf of the user, encrypt it using the customer defined public key, and send it to the Transforms for further use. The diagram below illustrates the process.
Steps to Integrating OAuth in Maltego 🔗︎
-
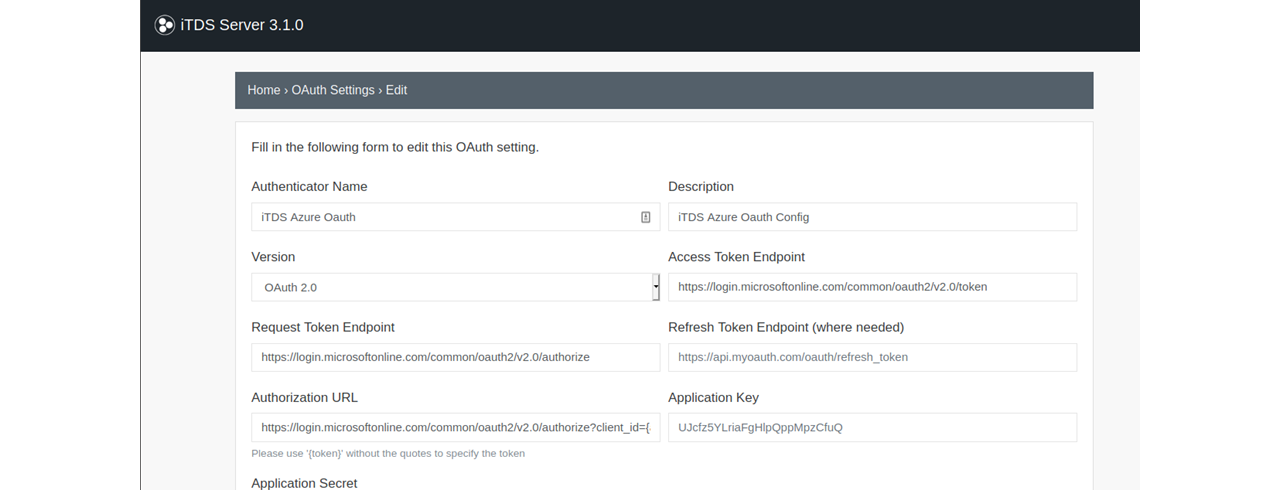
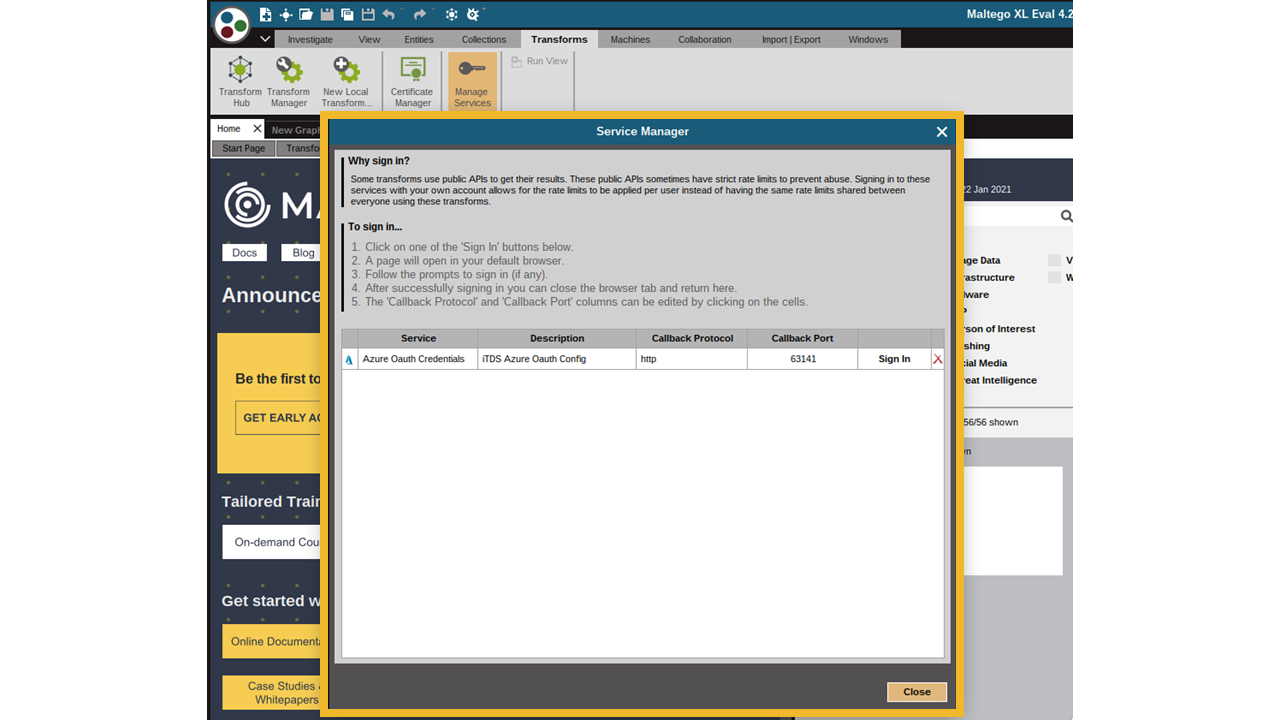
Configure the required OAuth Setup (App Develop Credentials) on the Resource Provider service such as LinkedIn, Okta or Azure, and configure the OAuth Settings in the Maltego Transform Distribution Server (TDS)
-
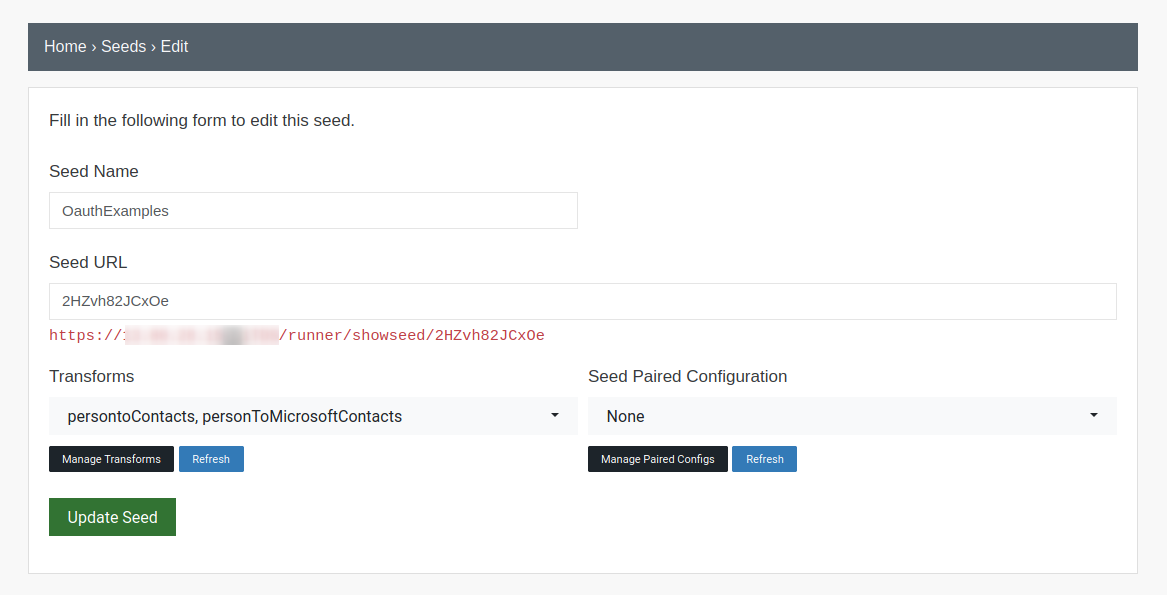
Install the Transform Seed from Step 1 in the Maltego Desktop Client
-
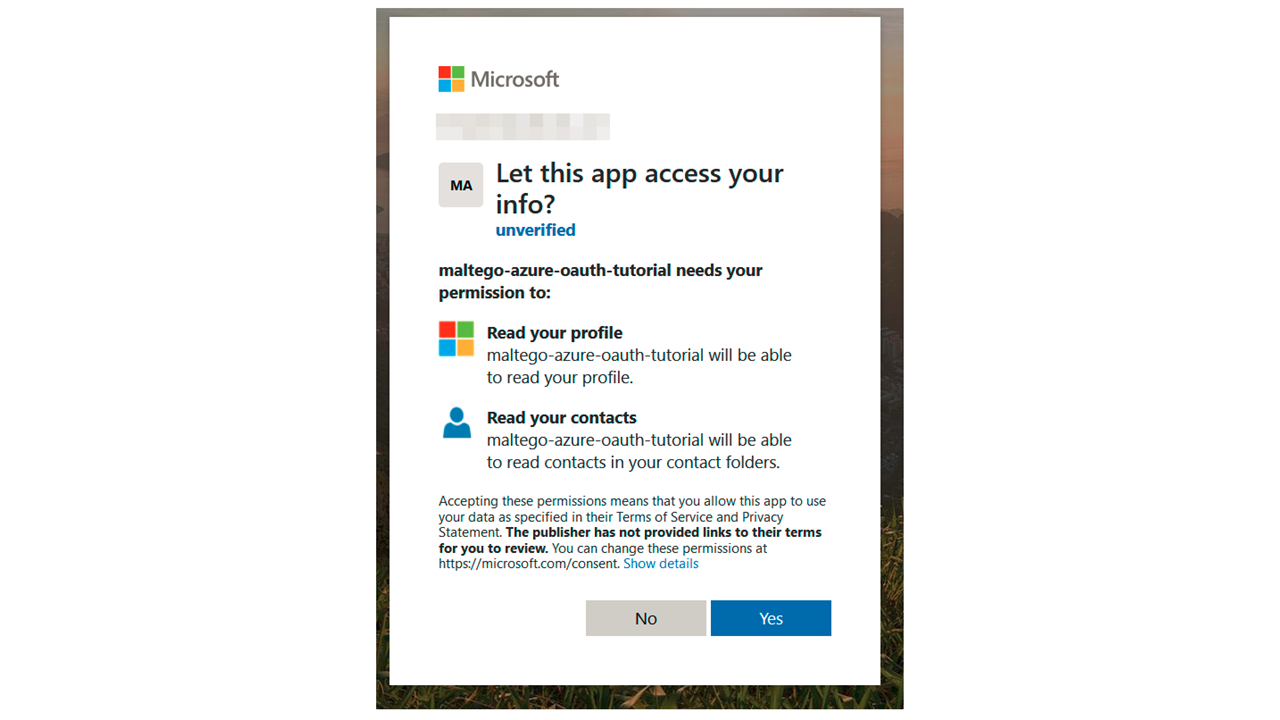
Log in to the resource provider’s web portal and authorize permissions
-
Request authorization token from the identity provider (IDP)
-
The IDP responds with authorization token
-
The web browser sends the token to the Maltego Desktop Client call-back URL and the Client then encrypts the token
-
The Maltego Desktop Client encrypts the token using the public key configured in Step1 and sends the encrypted token as part of a Transform request
-
The Transform code decrypts the ciphered token using private key from Step 1. Next, the decrypted token can be sent to the resource provider (RP) and get permitted resources or to check token validity
-
Return requested resources
-
Return Transform results
Token Encryption in Maltego 🔗︎
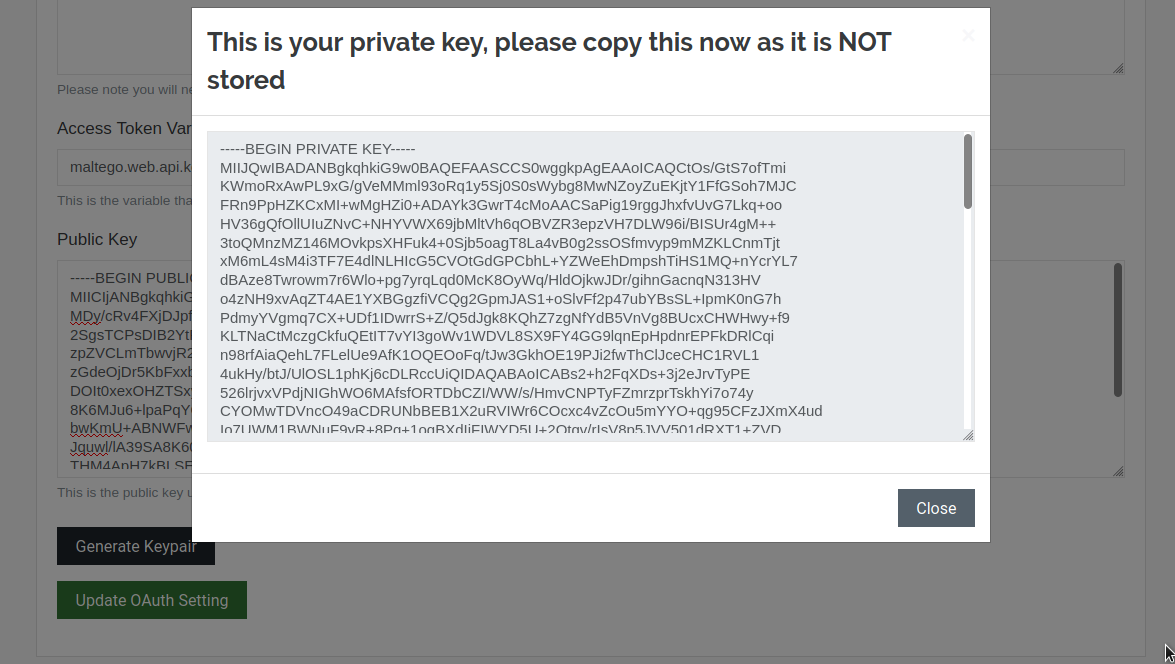
The OAuth Token is encrypted as soon as it is received from the IDP through the browser redirect. During OAuth settings configuration in the ITDS (Step 1 above), the customer is required to generate a public cryptography key pair.
The public key is added as a configuration setting and is used by the Maltego Desktop Client to encrypt the token acquired from the browser redirect once a user completes the authorization process on the resource provider’s authorization web page. The encrypted token is sent to the Transform Server, and the Transform code owned by the customer can then decrypt it and use the resulting code to retrieve resources from a resource server.
For technical guides, please refer to the following detailed examples in our online documentation:
OAuth may appear to be a complicated topic, but we at Maltego strive to simplify configuration and integration with numerous OAuth providers. We also provide both technical support for OAuth integrations as well as bespoke Transform development services.
For more interesting tutorials, case studies and updates, follow us on Twitter and LinkedIn and subscribe to our email newsletter.


 4.5 rating
4.5 rating