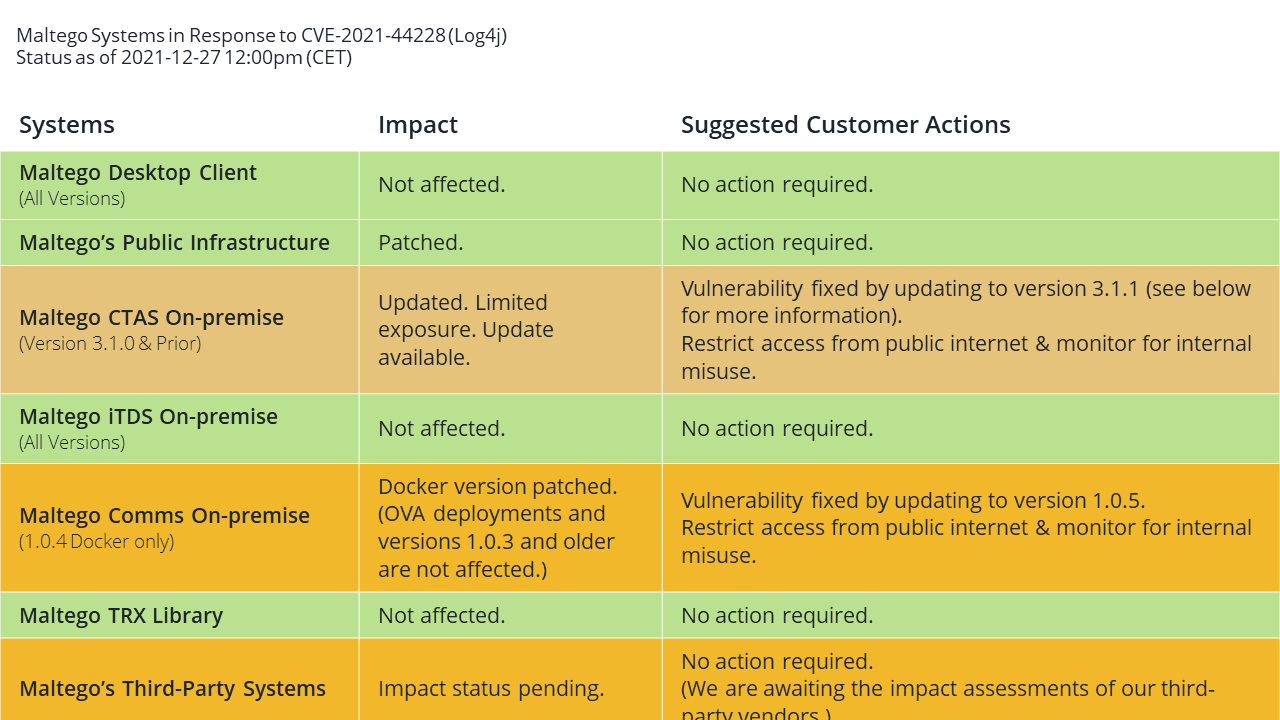
Update on Dec 27 2021, at 12.00pm CET 🔗︎
The vulnerable Docker version of our Comms server (Version 1.0.4) released in July 2021 is now patched. Users running a Docker-deployed Comms server on-premise are advised to update to the newest version 1.0.5. Deployments of the Comms Server via OVA and versions prior to 1.0.4 are not vulnerable to CVE-2021-44228.
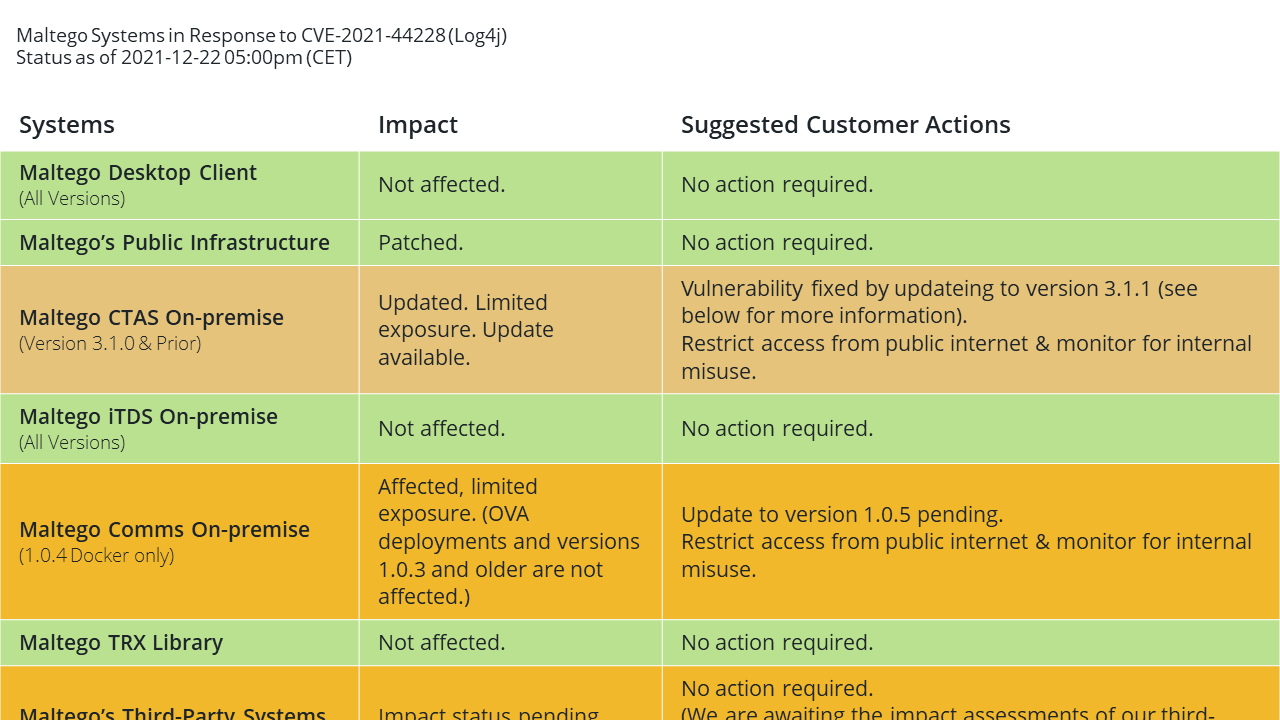
Update on Dec 22nd 2021, at 5.00pm CET 🔗︎
We have learnt that the latest Docker version of our Comms server (Version 1.0.4) released in July 2021 is still vulnerable to Log4shell attacks. Users running a Docker-deployed Comms server on-premise are advised to shut it down until we have released an update. Deployments of the Comms Server via OVA and versions prior to 1.0.4 are not vulnerable to CVE-2021-44228. The team is currently working on a fix.
Update on Dec 16, 2021 at 10:00am CET 🔗︎
On Tuesday, Dec. 14, we learned about CVE 2021-45046, a second Log4j vulnerability in certain non-default configurations. To exploit this new vulnerability, Maltego would have to be using non-default/non-standard Context Lookup or Thread Context Map to be at risk of exploit.
After additional analysis, we came to conclude that Maltego is not using non-default configurations and therefore not vulnerable to CVE 2021-45046. Therefore, we will not be issuing any emergency patches for this vulnerability, but will address CVE 2021-45046 as part of our standard vulnerability management program.
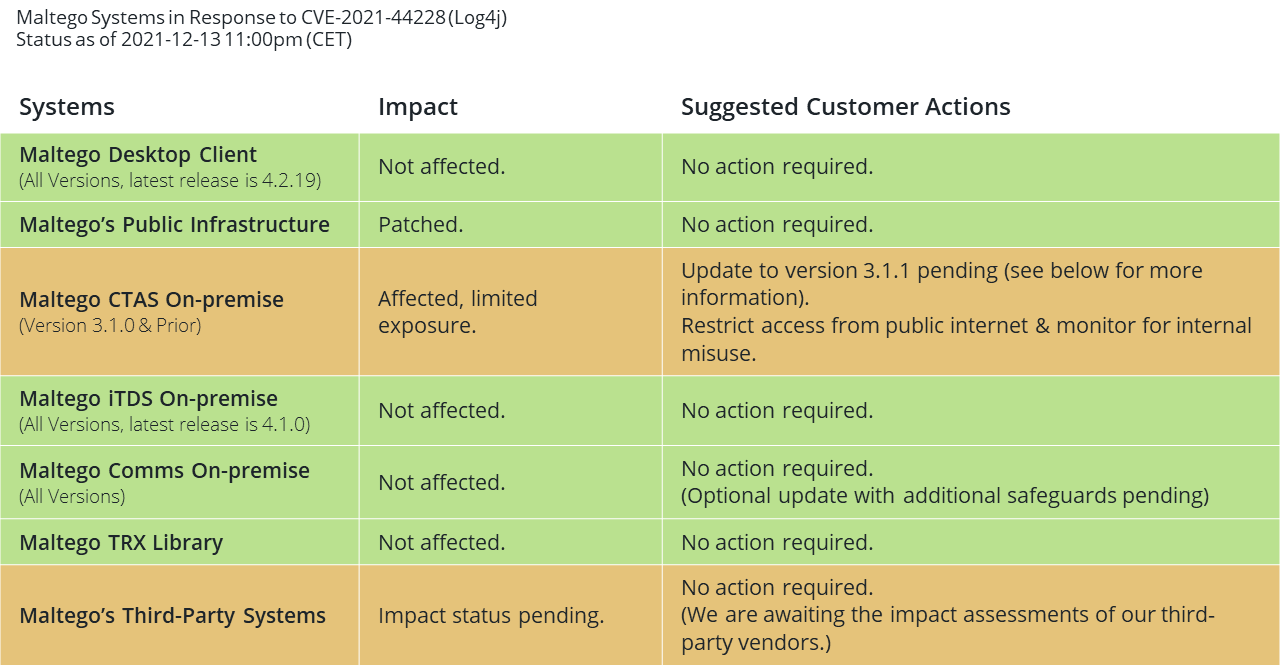
Update on Dec. 13, 2021 at 8:00pm CET 🔗︎
We have released version 3.1.1 of our “Maltego Standard Transforms On-premise (CTAS).” On-premise customers have been informed to update to this version to fix CVE-2021-44228.
At this point in time and to our current knowledge, all Maltego systems have been fixed (if required) and patches have been made available to customers. We will continue to provide updates should new information become available.
Update on Dec. 13, 2021 at 04:30pm CET 🔗︎
We have concluded the initial remediation of our systems affected by the Apache Log4j vulnerability. At this point in time, we have determined the impact of CVE-2021-44228 on our systems as follows:
Initial remediation: Since Sunday Dec. 12, 2am CET, Maltego’s public infrastructure has been patched, where required. We have also determined that the Maltego Desktop Client, Internal Transform Deployment Server (iTDS), Collaboration Server (Comms), as well as the trx Transform library are not affected by CVE-2021-44228.
Affected systems: Users of our Maltego Standard Transforms on-premise (CTAS) are affected, but exposure is limited under our standard suggestions for deployment. We are working on an update to version 3.1.1 which will become available to customers over the course of this week. Until then, customers are advised to ensure that their CTAS installation is not accessible from the public internet. In addition, although highly unlikely, customers are advised to restrict internal access and usage of the CTAS server to avoid potential attacks from internal users.
What happened since the initial update: We are working on releasing an update to our Maltego Standard Transforms on-premise (CTAS) for on-premise customers.
We are also bringing the Scamadviser Transforms back online in the next couple of hours.
What will happen next 🔗︎
We will continue to provide updates as we have them and appreciate everyone’s patience as we work through the impacts of these events.
Update on Dec. 13, 2021 at 11:00am CET 🔗︎
As with many other companies across the globe, Maltego utilizes the Apache Log4j Java library that was revealed to be vulnerable to a Remote Code Execution (RCE) exploit (see CVE-2021-44228).
What we did so far 🔗︎
Maltego quickly took action over the course of the weekend to identify what of its applications and servers was vulnerable and remediate.
- Maltego-hosted Infrastructure: Maltego has remediated all of its hosted infrastructure by patching to the recommended Log4j version and tested its infrastructure to confirm.
- Maltego Desktop Client: At this point in time, we have found the Maltego Desktop Client to be not vulnerable due to not utilizing the affected Log4j library.
- On-premise Systems: For enterprise customers that use our on-premise solutions, the Standard Transforms hosted on-premise (CTAS) continue to be vulnerable until we have released an update. However, at this point in time, we consider these systems to be at lower risk as they are both containerized with restricted permissions as well as typically firewall restricted. Maltego will be releasing an update this week to patch this system as well.
- Other Affected Systems: As a precautionary measure we have shut down access to the Scamadviser Transforms until our data partner acknowledges that no issue is present.
What will happen next 🔗︎
We will continue to provide updates as we have them and appreciate everyone’s patience as we work through the impacts of these events. In particular, we will reach out to our customers with more information on how to update their systems should they be affected.