At Maltego, we are constantly working on bringing you the best tools for your investigations. That is why we are happy to announce our new integration for URLhaus by Abuse.ch.
This article will walk you through the URLhaus data and how to use our new Maltego Transforms to speed up your malware investigations.
What is URLhaus? 🔗︎
URLhaus is a project operated by Abuse.ch to share intelligence on malicious URLs that are being used for malware distribution. The community-driven project collects, tracks, and shares malware URLs, helping network administrators and security analysts to protect their network and customers from cyber threats.
By bringing URLhaus data into Maltego, you can reduce the time required to confirm malicious URLs and their payloads.
You can also seamlessly fuse information obtained from URLhaus with that of other Maltego integrations; For example, you could pivot from a hash found in URLhaus to find detailed malware behavior analysis using VirusTotal, or explore relevant internal network traffic and events for a malicious URL using Splunk.
What Do I Need to Start Using the URLhaus Transforms in Maltego? 🔗︎
All you need to start leveraging URLhaus Transforms is to go to the Maltego Transform Hub, look for Abuse.ch URLhaus, and click Install.
You don’t need an API key for this integration, so you can start exploring the URLhaus data as soon as the installation is finalized.
What Type of Information Can I Get from URLhaus? 🔗︎
You can use our URLhaus Transforms to gather information on Entities such as Domains, URLs, DNS Names, IPv4 Addresses and Hashes.
This is a summary on what you can get from URLhaus.
- Entity Details: Enrich your Entities with additional information from their URLhaus database.
- Blacklist Status: Confirm whether one of your Entities is currently part of a blacklist.
- Payloads: An excellent feature for investigations–Get the payload (malware file) associated with specific URLs or Hashes.
- Payload Details: Pivot from payloads to other Entities such as md5 and sha256 Hashes, Host, Signature, URLs, Tags, and Reporter Details.
Can We See These URLhaus Transforms in Action? 🔗︎
Absolutely, let us take you through a short demo.
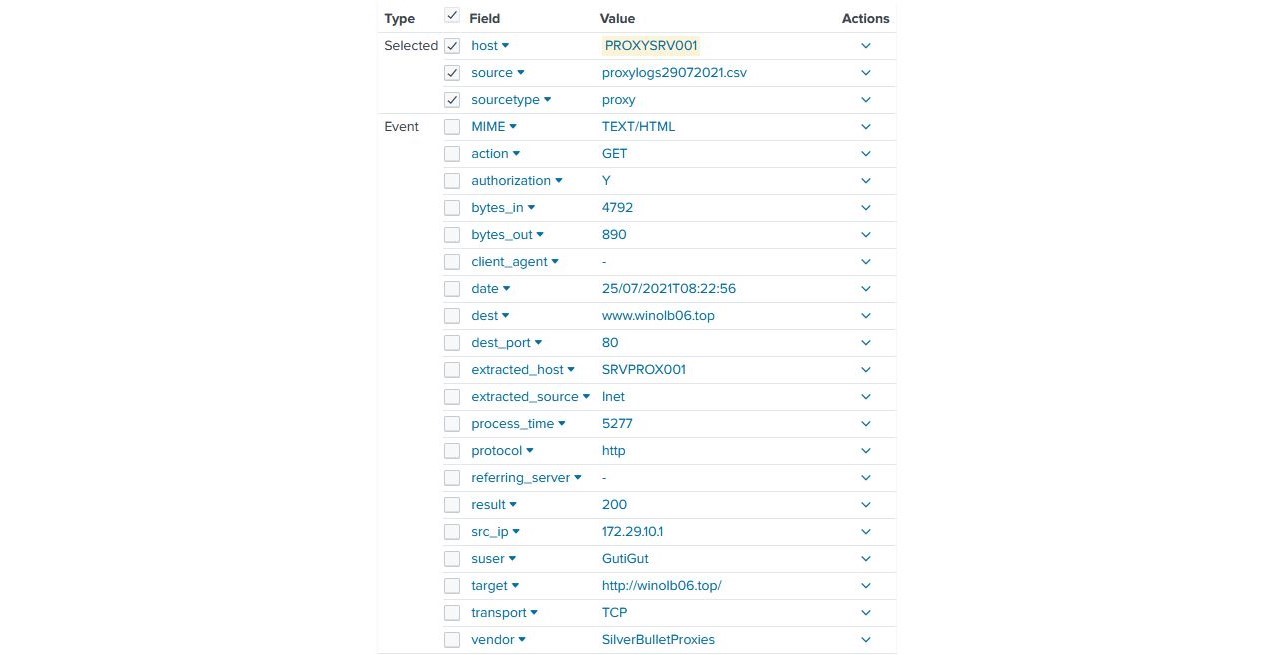
Let’s say you are a security analyst or a network administrator and you come across an interesting entry in your proxy logs in Splunk that caught your eye. You want to confirm whether this is a malicious site.
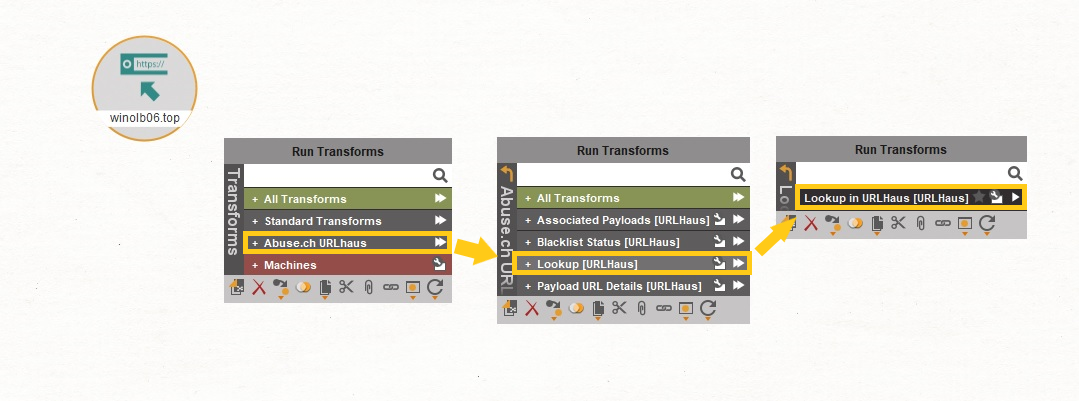
Let’s take the target URL and paste it into Maltego.
Select the URL Entity and right-click anywhere on the graph to open the Transforms menu. We will start by checking if URLhaus has any information about this UR by running the Lookup in URLHaus [URLHaus] Transform.
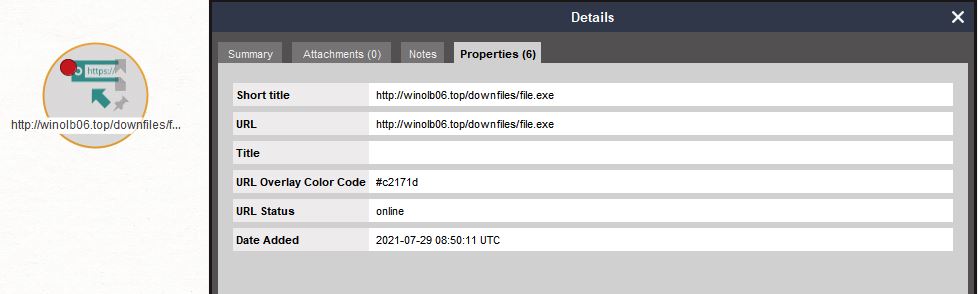
We can immediately see that our Entity has changed, as there is now a red dot on the upper left corner of the Entity. We can also open the Entity details to find out what else has changed.
The URL status is online for this URL, meaning it is still accessible. We also obtained the date when this entry was added to the URLhaus database.
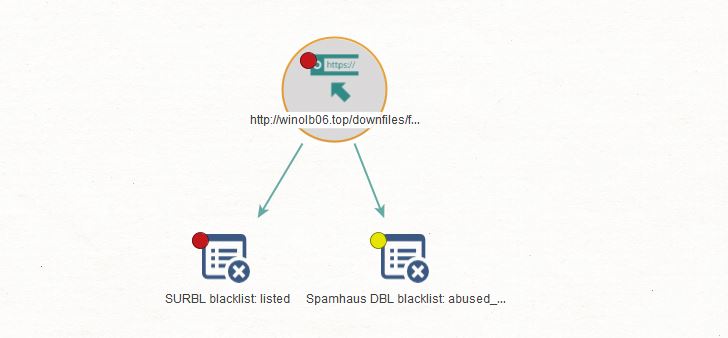
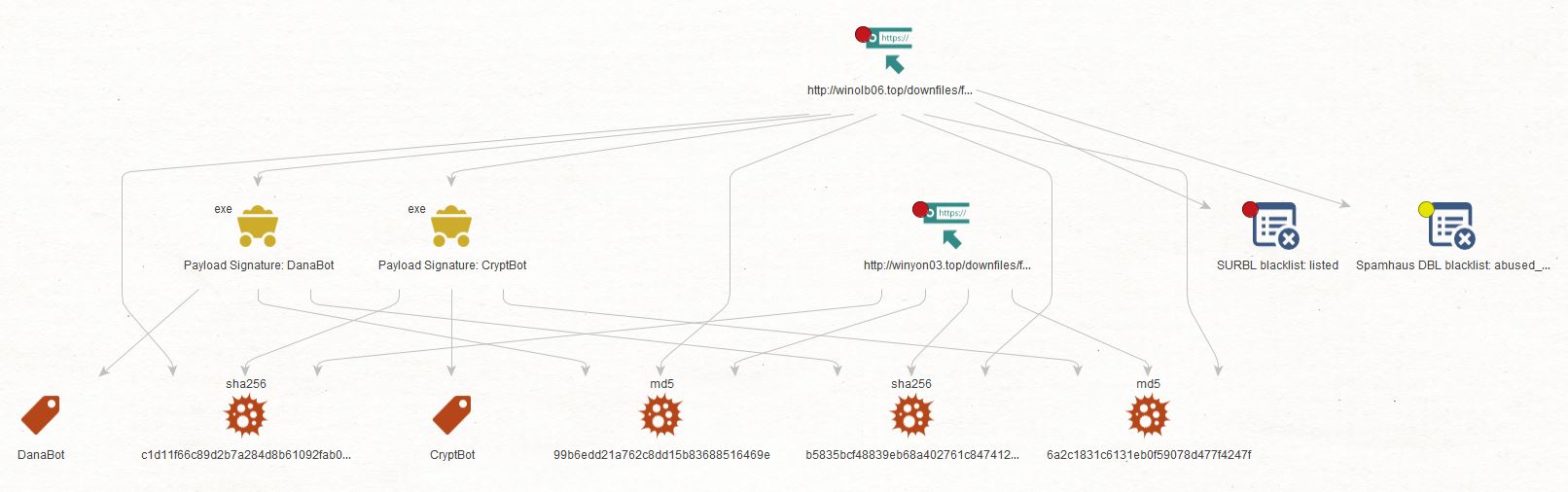
Next, we validate whether this URL has been added to a blacklist by running the To Blacklists Status [URLHaus] Transform. In this case, we received confirmation that this URL has been added to SURBL and Spamhaus DBL.
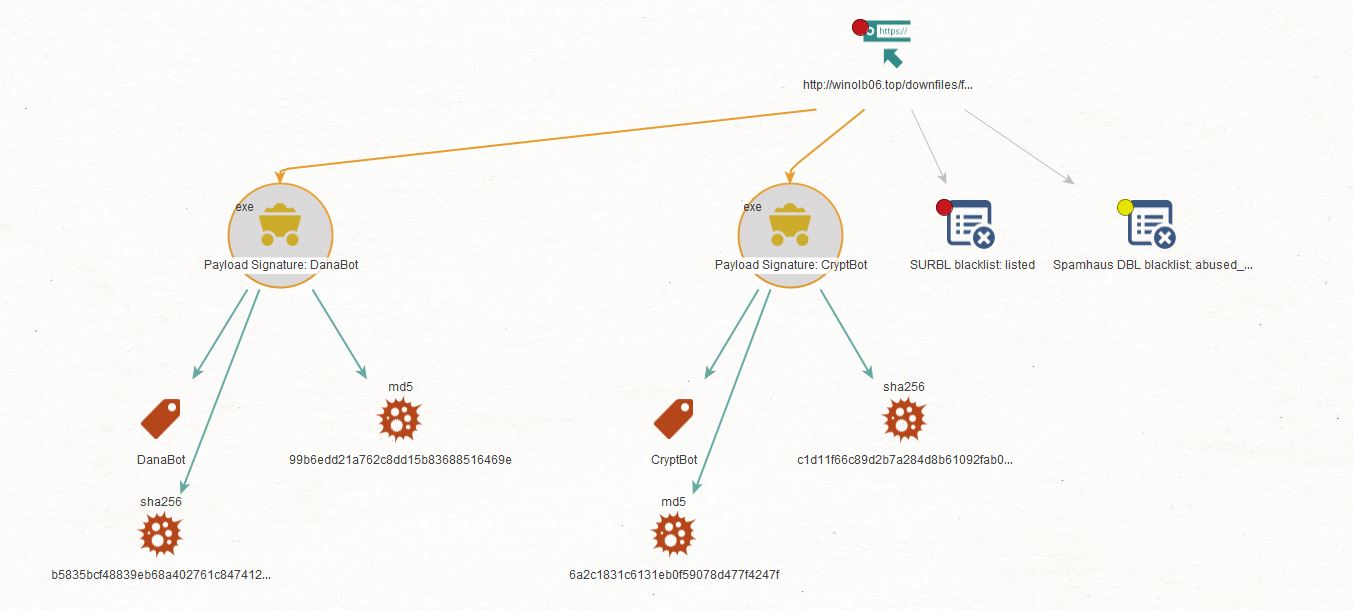
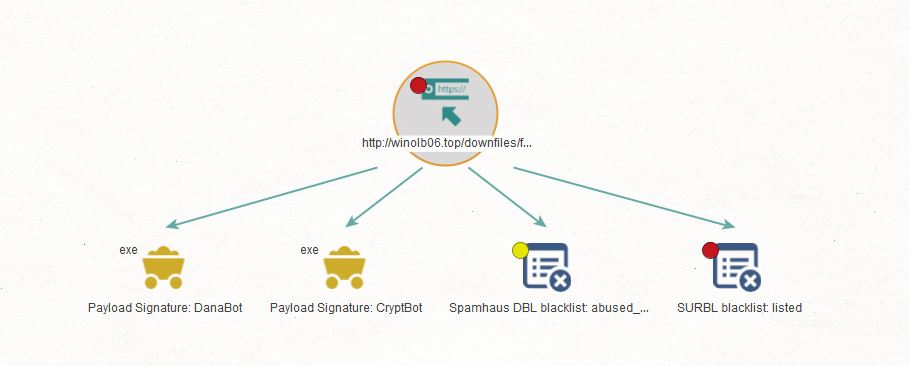
Now that we have confirmation that this URL is malicious, let’s check if we can find the payloads that are being served by the URL. We will run the To Payloads [URLHaus] Transform on the URL Entity.
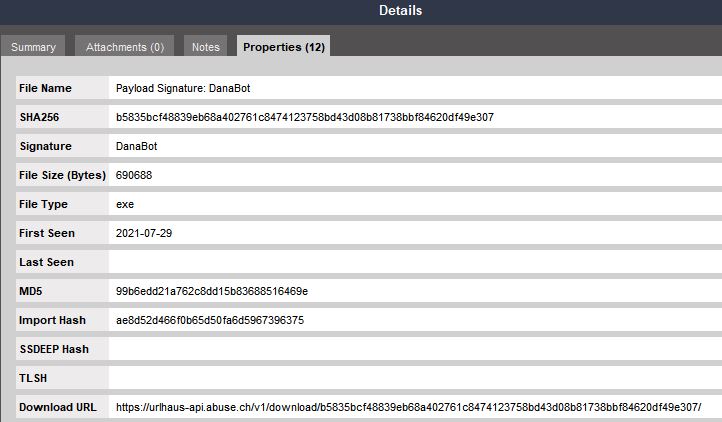
As we can see, Maltego returned a couple of abusech.Payload Entities. If we open the details for one of these, we will see information such as signature, file type, file size, md5 and sha256 hashes, and the first seen date, among other details.
We can bring the relevant pieces of information into Maltego by selecting the Payload Entity and running the Payload Details [URLHaus] Transform Set.
Let’s now take the newly added Hashes and run the To Payload URLs [URLHaus] Transform to identify additional URLs serving the same Payloads. As we can see, we could identify another URL serving the same payload.
We have now confirmed that the URL that was accessed is a malicious one and is currently live and serving malware. With this confirmation and the additional details such as file names, hashes, malware family, and URLs, you can move to the next phase in your incident response process.
We hope you enjoyed the release of the URLhaus data integration for Maltego.
Don’t forget to follow us on Twitter and LinkedIn and sign up for our email newsletter to stay updated on the latest news, tutorials, and events.
Happy Threat Hunting!