This guide shows how a basic (Level 1) network footprint of an organization can be derived. In Maltego, we use “levels” to indicate how deep such footprints go. For example, a Level 1 footprint is all the infrastructure directly observable without having to pivot backwards to discover additional resources.
Level 1 Network Footprint in Maltego 🔗︎
A basic Level 1 network footprint contains:
- DNS names currently or previously used by the organization;
- Mail exchange servers used by the organization;
- Email addresses of the organization’s network administrators;
- The netblocks that these IP address belong to; and
- The companies owning these netblocks.
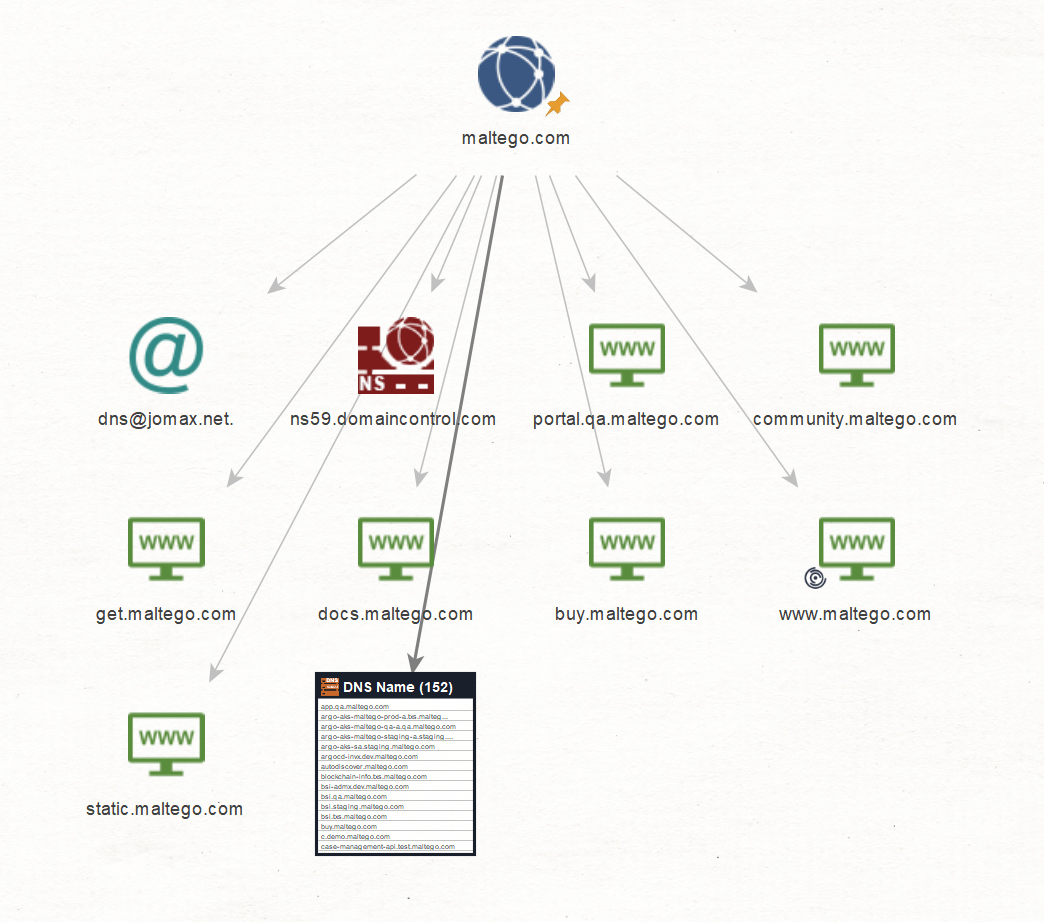
In Part 1 of this series, we focus on deriving the DNS names and mail exchange servers used by the organization, as well as their administrative email addresses. In Part 2, we will explore the next step in mapping the Level 1 network footprint
For Complete Maltego Beginners 🔗︎
If you are new to Maltego, please visit Beginners Guide to Maltego: Charting my first Maltego Graph for a brief introduction to Maltego concepts, such as creating a graph, what an Entity is, and running your first Transform.
Maltego Transforms for Level 1 Network Footprint 🔗︎
The next section of this post will focus on how to derive the IP addresses of the DNS names and mail exchanges.
Given an organization’s domain, we can extract the DNS names under that domain by querying DNS resolvers on the Internet. There are also passive DNS databases which keep a historical record of DNS names. Using Maltego, we can query both the current DNS resolvers and passive DNS databases to derive the DNS names. Additionally, we can use the Bing search engine to find DNS names that end with the given name. The following are the Transforms that derive DNS names from a domain.
To Website [Quicklookup] 🔗︎
This Transform performs a DNS lookup for the DNS name derived by prefixing “www.” to the given domain. Upon successful lookup, that DNS name is returned.
To DNS Name [Find common DNS Names] 🔗︎
This Transform will try to discover various common DNS Names in a domain. The common DNS names are tested by prefixing domains with the following names:
mail, mx, ns, ftp, webmail, web, gateway, secure, intranet, extranet, smtp, pop, ns1, mx1, email, admin, dmz, blog, dns, forum, ntp, pub, route, sql, ssh, webaccess, xml, imap
To DNS Name [Attempt Zone Transfer] 🔗︎
This Transform sends a zone transfer request to the Name Server of the given domain. If the request succeeds, the DNS server will give information about all the DNS names in the domain. The Transform then returns DNS names for all the A and CNAME records in the zone.
Note that DNS servers generally do not respond to zone transfer request. Nevertheless, we may get lucky with an old or an ill-configured one.
To DNS Name – SOA (Start of Authority) 🔗︎
This Transform returns the NS record and the email address of the administrative contact of the given domain.
To websites using domain [Bing] 🔗︎
This Transform queries the Bing search engine and returns all the websites with hostnames that end in the given domain. For example: jobs.
To DNS Name [SecurityTrails] 🔗︎
This Transform searches the SecurityTrails passive DNS database for any DNS names that contain the given domain.
To DNS Name (interesting) [SecurityTrails] 🔗︎
This Transform is similar to the previous one, but searches for DNS names containing the given domain and any of the following terms:
- VPN
- Webmail
- Firewall
- Test
- Scada
- Intranet
- Secure
- SSH
- Database
Starting Off: Run the Transforms on a Domain Entity 🔗︎
Right click on the Domain Entity on the graph. In the context menu, you can search for the Transform by typing its name. Once the desired Transform is found you can click on the Transform to run it.
Run the above Transforms on the Domain Entity in any order. What you have on the graph are the DNS names that we can find for the given domain.
Note that the SecurityTrails and the Bing Transforms may return historical DNS names which may or may not be currently available.
As an example, here is the result of running the above Transforms on maltego.com domain:
In our next part of Beginners Guide to Maltego: Mapping a Basic (Level 1) Network Footprint – Part 2, we will show you how to derive the IP addresses from these DNS names, their netblocks and the companies that own them.
Follow us on Twitter and Linkedin or subscribe to our email newsletter to make sure you don’t miss out on any updates.


 4.5 rating
4.5 rating