Get Started with Maltego
Please share your contact information for a personalized session.

Thank you!
We will contact you soon.
In the meantime, check out our product overview
to learn more about the Maltego platform.
IBM QRadar
By Maltego Technologies
Extract and map context of IOCs from event logs and offenses.

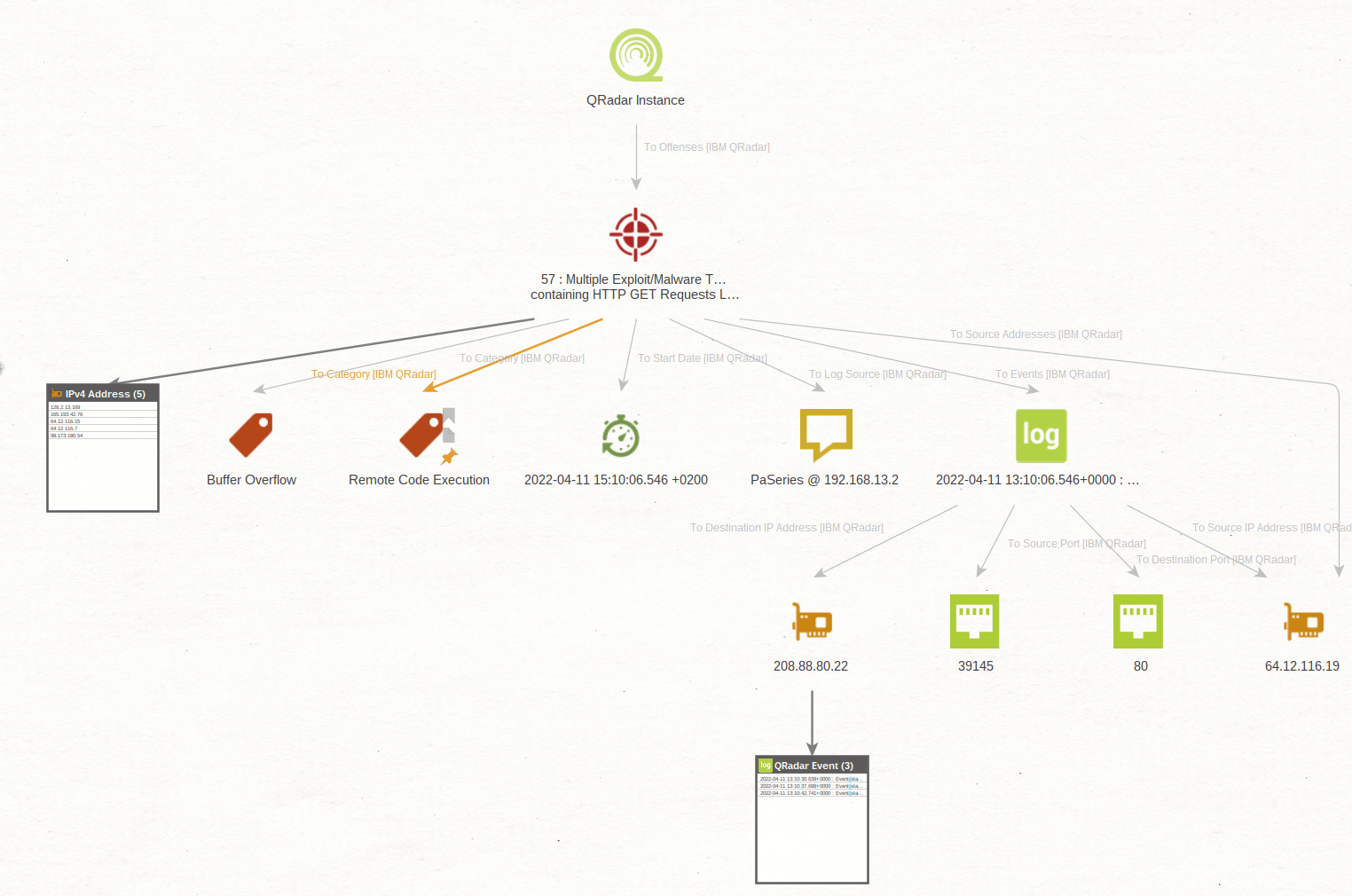
IBM QRadar Transforms for Maltego
QRadar uses rules to monitor information security events and network flows to detect security threats. When events and flows meet the test criteria that are defined in the ruleset, an offense is created to show that a security attack or policy breach is suspected.
The IBM QRadar integration for Maltego provides context for events and offenses helping improve investigations by mapping the complex relationships. The IBM QRadar Enterprise integration for Maltego enable security teams to extract and map host assets, IP addresses, hashes, operating systems, vulnerabilities and other IOCs from event logs and offenses.
Using the Transforms, investigators and analysts can query offenses from a given QRadar Instance, find the related events for those offenses, bring in the IOCs into Maltego, and leverage our wide variety of data sources to augment and enrich their investigations.
Typical Users of IBM QRadar Data
- Threat Intelligence Teams
- Threat Hunting Teams
- Incident Response Teams
- Security Operation Centers

Integration Benefits
Seamlessly start investigations in a simple, visualized graph
Exploring offenses and performing deep dive investigations
Combine QRadar with other threat intelligence feeds
Map IT assets and related events and offenses
Enabling incident response, hunting, and digital forensic investigations
Leverage IBM QRadar Data for
Incident Response
Threat Hunting
Threat Assessment
Contact
Reach out to us to learn more about this data integration and how to access it.
About IBM QRadar
IBM QRadar is an enterprise security information and event management (SIEM) product. It collects log data from an enterprise, its network devices, host assets and operating systems, applications, vulnerabilities, and user activities and behaviors to then perform real-time analysis of the log data and network flows to identify malicious activity so it can be stopped quickly, preventing, or minimizing damage to the organization.
For more information, visit https://www.ibm.com/uk-en/qradar.



 4.5 rating
4.5 rating