 Maltego Monitor
Maltego Monitor
 Maltego Monitor
Maltego Monitor
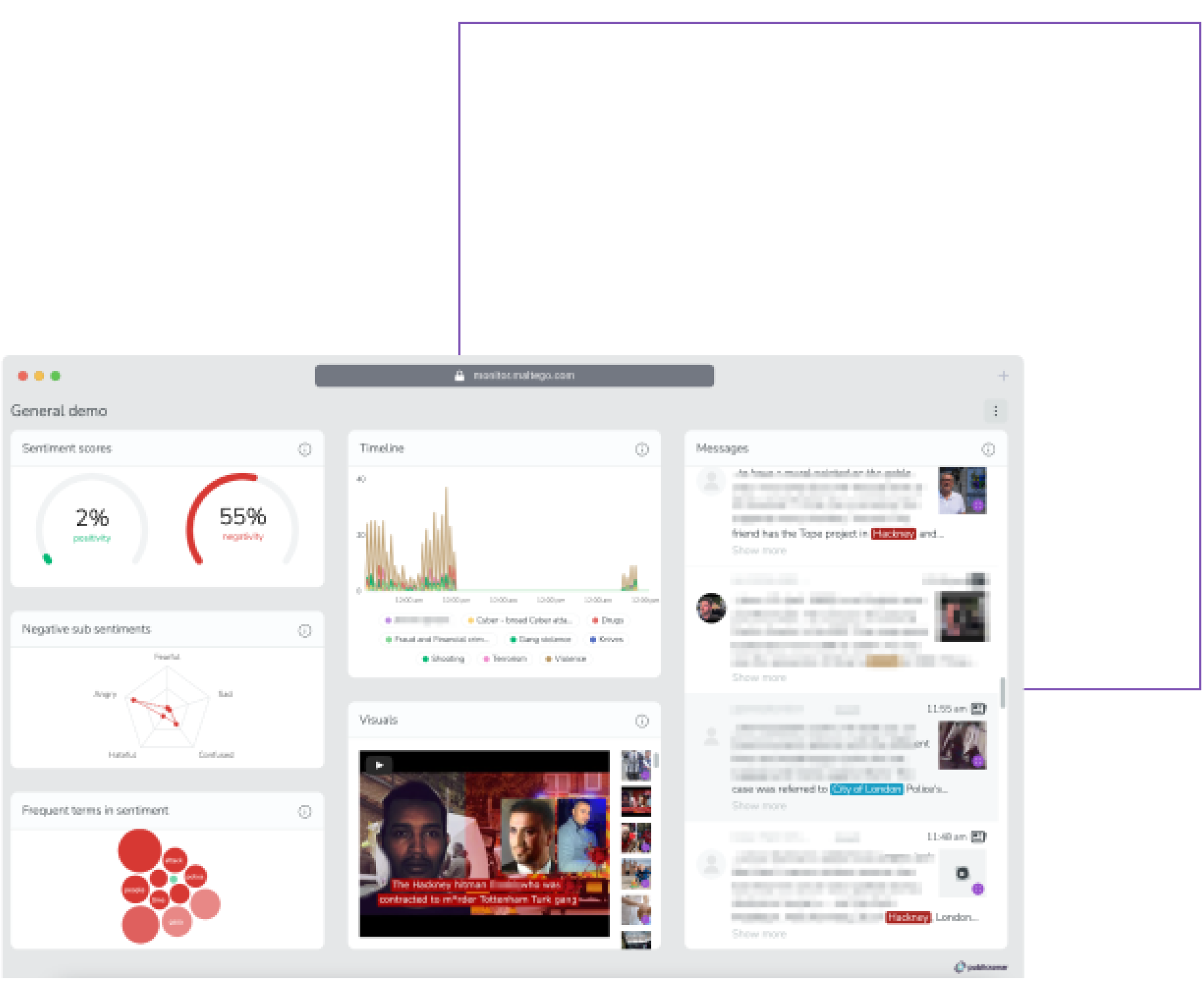
Gain situational awareness to protect public safety and businesses, and respond swiftly to crises with real-time social media intelligence
-
 Large-scale OSINT monitoring
Large-scale OSINT monitoring
-
 Intuitive interface for complex analysis
Intuitive interface for complex analysis
-
 AI-powered capabilities
AI-powered capabilities
Without Maltego Monitor
-
Dispersed & Massive OSINT Data
You have multiple data sources and platforms, and it is time-consuming to monitor and analyze every single channel activity manually.
-
Being in the Reactive Role
It is hard to stay ahead of the situation without the ability to ingest and digest information about ongoing threats, emergencies, and disruptions in real time.
-
Lack of Situational Awareness
Without a bird’s-eye view analysis on-site, maintaining situational awareness is challenging, increasing the risk when the full scale of the danger is unknown.
With Maltego Monitor
-
Access to Real-Time OSINT Data
Access and monitor real-time public sentiments and activities across multiple social media platforms, news sites, and live blogs.
-
Stay Event- and Region-Focused
Set up customized monitoring dashboards for specific events, regions, topics, and occasions for the most focused and relevant insights.
-
AI-Powered Analysis
Accelerate decision-making and gain context rapidly through AI-powered analysis of images, videos, and large volumes of text.
When investigators need fast and accurate results, they get them with Maltego.
Maltego Monitor helps prevent incidents and detect threats to the public and businesses through continuous monitoring and analysis.
How does the Maltego platform support organizations worldwide?

Simply smart, powerful and efficient tool! As a seconded researcher of Trend Micro to INTERPOL and some of my co-researchers, Maltego is essential in our day to day cybercrime investigation for the purpose of chasing down the threat actors and revealing their modus operandi and infrastructure.

Maltego is the first tool I'd install on any researchers laptop, and the first I open any time I'm starting a new investigation. From the ability to access many different data sources through one tool, to the advanced visualisations, its an absolutely essential part of modern cybercrime research

Maltego’s strength lies in its capacity to visualize relationships among Entities, even when dealing with large volumes of data. Ultimately, Maltego enables us to quickly obtain information about the subject from the surface web and the deep and dark web.

A great strength of Maltego is the ease of gaining insights from multiple, disparate data sets. In the past couple of years, Maltego has been increasingly developed towards a relevant market place for data and I am excited to see how this will evolve in the future.

Maltego allows us to quickly pull data from profiles, posts, and comments into one graph, where we can conduct text searches and see connections. In just a few minutes, we can narrow initial research to a handful individuals using variations of aliases connected to suspected local traffickers. We would not have been able to do that without Maltego.

I have been an avid user and advocate of Maltego for many years, using it especially for internet infrastructure mapping. However, its automated search and graphing capabilities make it perfectly suited for creating cryptocurrency transaction maps. If you are looking for a low cost entry into address identification, I highly recommend it.

Maltego is a wonderful aggregator of interfaces to various OSINT databases. The company behind Maltego has even formed its own OSINT ecosystem. Maltego can scan a target website, but then it lets its users effortlessly apply what it calls “Transforms” from its ecosystem to connect the web information to various databases. I’ve been blogging about infosec for years, and even I’m nervous about Maltego’s capabilities. With OSINT, knowledge is truly power.

Maltego is simply limitless in the options that it provides us. We see great potential in the default options available in Maltego, from graphing capabilities to the different entities to data integrations. It allows us to extend its capabilities and customize it to our investigative needs.
Maltego Monitor is part of the Maltego platform! Have you explored the other tools and services?
Discover all capabilities of the all-in-one investigation platform!
Monitor real-time data and use AI-powered sentiment analysis to detect and assess potential and ongoing public safety disruptions and cyber threats
Quickly uncover new leads by identifying and tracking the activities of suspects and potential threats

Run quick OSINT searches on suspects and threat actors with data from social media, the dark web, identity databases, and breach data
Run quick OSINT searches on suspects and threat actors with data from social media, the dark web, identity databases, and breach data
Monitor real-time data and use AI-powered sentiment analysis to detect and assess potential and ongoing public safety disruptions and cyber threats
Conduct deep investigations into complex OSINT cases and cyber threats with access to all external and internal data
Conduct deep investigations into complex OSINT cases and cyber threats with access to all external and internal data
Uncover hidden truths in large social media datasets with customized crawling profiles


Advisory Services
Leverage expert guidance for workflow optimization, new use case development to elevate your organization's capabilities




technical Services
Custom engineering for specialized Maltego deployment and integrations to suit your organization's investigative and compliance needs
technical Services
Custom engineering for specialized Maltego deployment and integrations to suit your organization's investigative and compliance needs


custom Training
Empower your investigative team with custom training sessions for investigators and developers


Administrative tools
Audit and analyze your organization's Maltego usage, billing, and access authorization
• Long-time requested by our customers • Secure & modern environmentOn-demand learning resources and live group trainings to help you succeed in your investigations
• Best way to learn Maltego • Up-to-date contentDiscover the capabilities used by thousands of customers, including half of the Dow Jones companies and major governments.
Unlock the full capabilities of the Maltego platform!
Experience firsthand how Maltego helps teams like yours centralize data analysis and adopt a unified approach to every investigation.
A company email works better. Want to switch?
The Maltego platform is designed for organizations. Using a company email means you'll get faster response times and access to features built specifically for business use.
For personal use, we recommend the free Community Edition (CE)!




