We are excited to announce the release of several improvements to the Maltego Standard Transforms with the latest updates to the PGP, BuiltWith and Wikipedia Transforms.
With over 170 Transforms, the Maltego Standard Transforms, available out-of-the-box, enable investigators to perform a vast range of standard OSINT investigations, and are available to all commercial Maltego users as well as CE users.
The Standard Transforms are useful for different kinds of investigations commonly conducted in Maltego, including both specialized and generic Transforms to supplement the functionality of other Hub items.
For more detailed information on each Transform as well as different use cases, please refer to our online documentation.
Table of Content 🔗︎
PGP Transforms 🔗︎
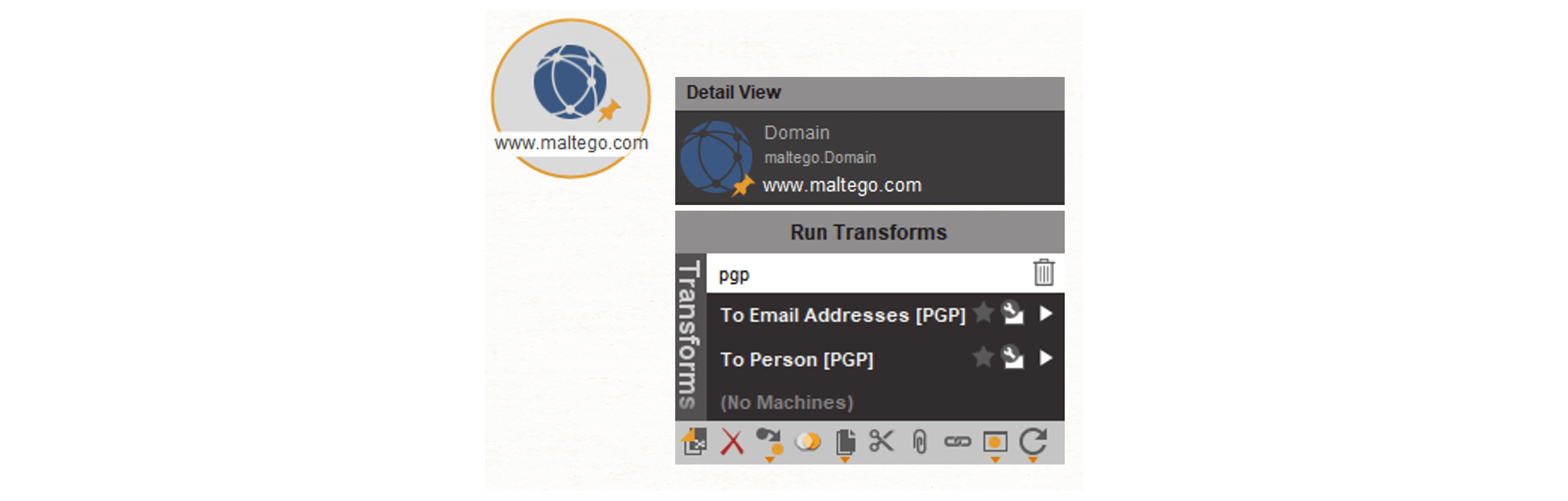
Using the Maltego PGP Transforms, investigators can query PGP key servers and investigate relationships between PGP keys, email addresses and people.
Researching usernames and email addresses is a very common OSINT investigation task. However, PGP keys can offer additional information to help identify links between different Entities in a way that other research methods might miss.
Public PGP keys are primarily used by people who seek to protect their online identity for purposes such as document encryption, digital signing of documents and verifying a username or email address. Whatever their purpose, PGP keys are always tied to a username or an email address. Wherever PGP keys are present, there may also exist bits of information that are useful for OSINT investigations.
For this reason, PGP Transforms can assist investigators in uncovering email addresses where previous search techniques have failed.
BuiltWith Transforms 🔗︎
The Maltego BuiltWith Transforms provide information on the current and historic technologies which websites are built with.
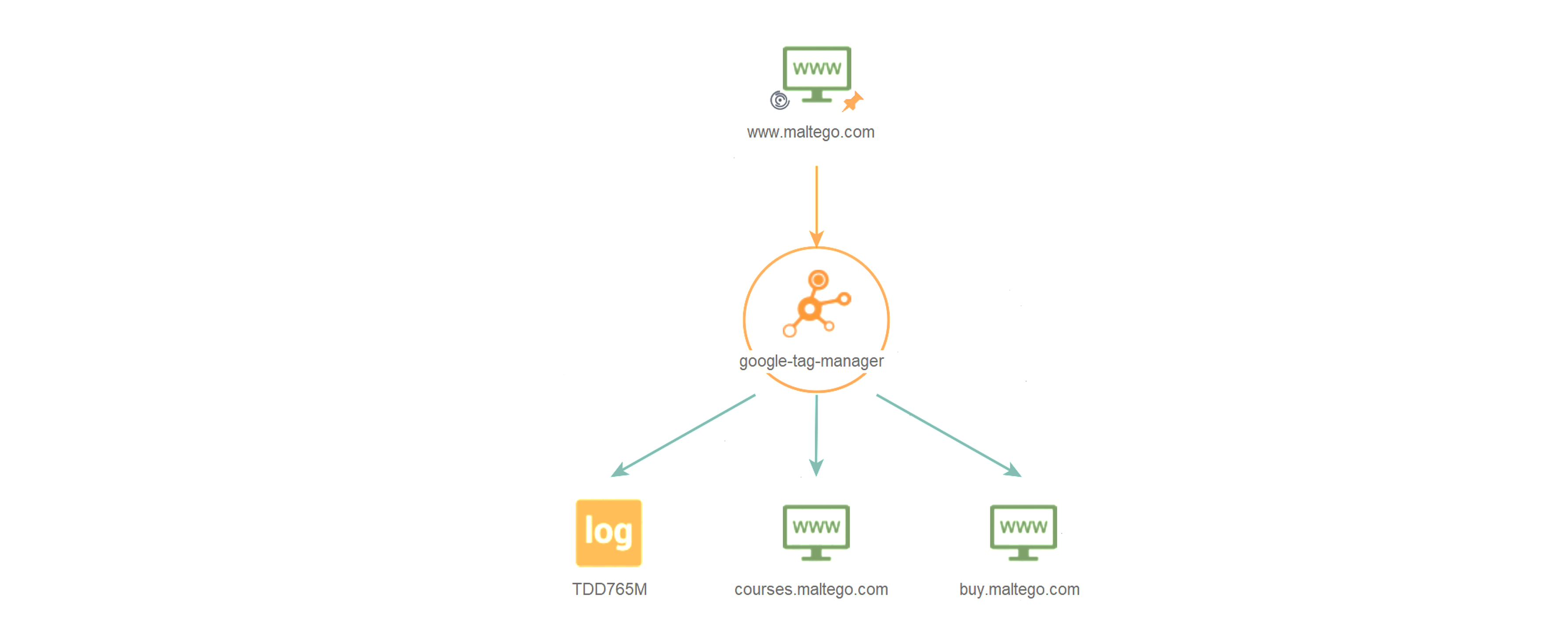
These Transforms are particularly useful for discovering relationships between websites and for retrieving the details on how these are related, as well as the duration of the relation (e.g., IP’s and tracking codes).
BuiltWith Transforms make it easy for investigators to detect which technologies are being used on any website on the internet. This includes detailed information about content management systems in use, as well as JavaScript and CSS libraries, web server types, SSL providers and even web hosting providers used.
A noteworthy addition to this Transform set is the new “To Identifier [BuiltWith]” Transform which returns from a BuiltWith relationship, the identifier on which this relationship is based, such as IPs and tracking codes, allowing users to pivot further into an investigation based on these results.
The recent updates to Maltego’s BuiltWith Transforms enable users to pivot from a BuiltWith Relationship Entity to discover related website technologies and website relationships. We have also re-named some of the Transforms and Transform sets from Server Technologies to Website Technologies to better describe the output from these Transforms, which include detailed website technologies in addition to server-based information.
Please note that if you have created any Machines that make use of these Transforms, some of the Transform names may need to be replaced.
Wikipedia Transforms 🔗︎
Using the Wikipedia Transforms, investigators can identify which users, IPs, and netblocks have made edits to Wikipedia pages and what those edits were.
These Transforms are particularly useful for uncovering misinformation campaigns and for enriching infrastructure information.
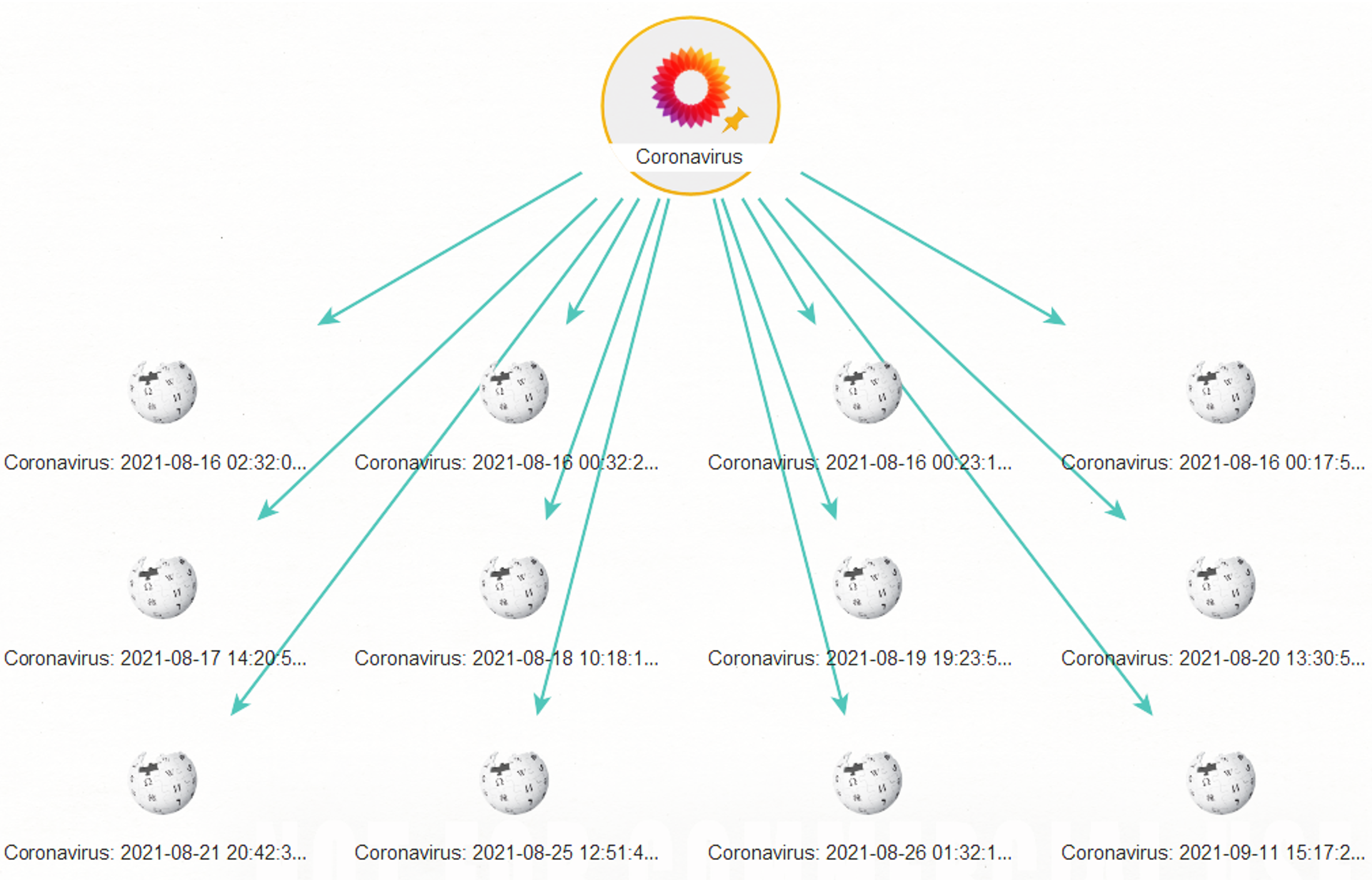
The example below is centered around Wikipedia’s “Coronavirus” page, where Wikipedia “editor wars” have been rampant since the virus emerged. Wikipedia contributors have been battle-locked, particularly around a contentious question, “Where did the virus come from?”.
As a result, Wikipedia users have been caught using multiple accounts to push their own personal views, as Wikipedia contends with conspiracy theories and speculation.
Below, we will make use of Maltego’s recently updated Wikipedia Transforms to conduct a basic investigation illustrating how these Transforms can be used and what type of information can be gathered.
Please note that IPs will only be returned in instances where the page editor is not using a Wikipedia account to make the edits.
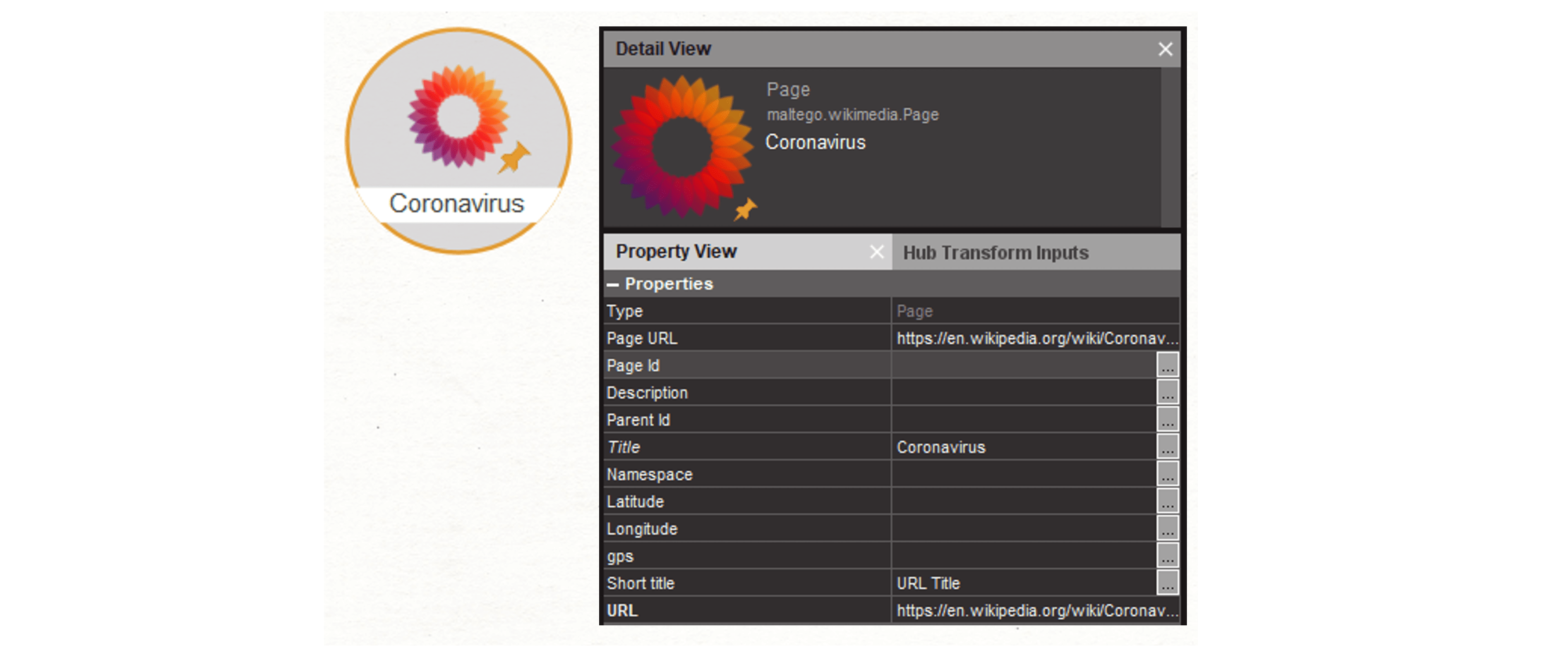
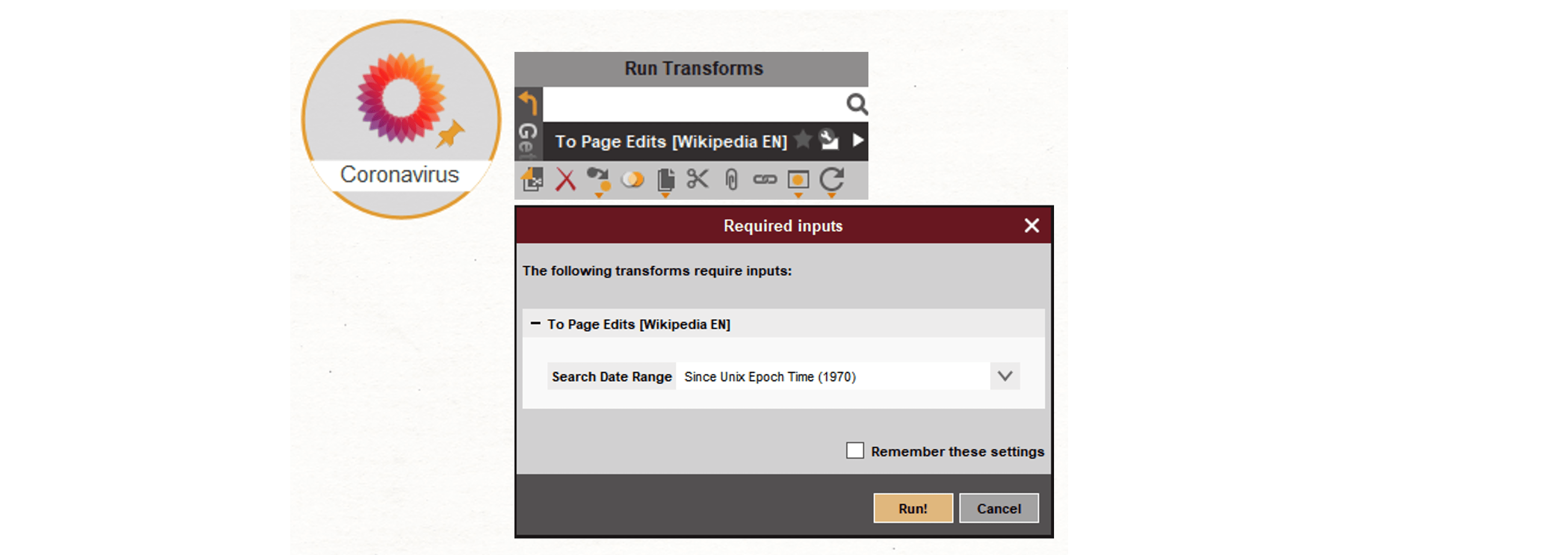
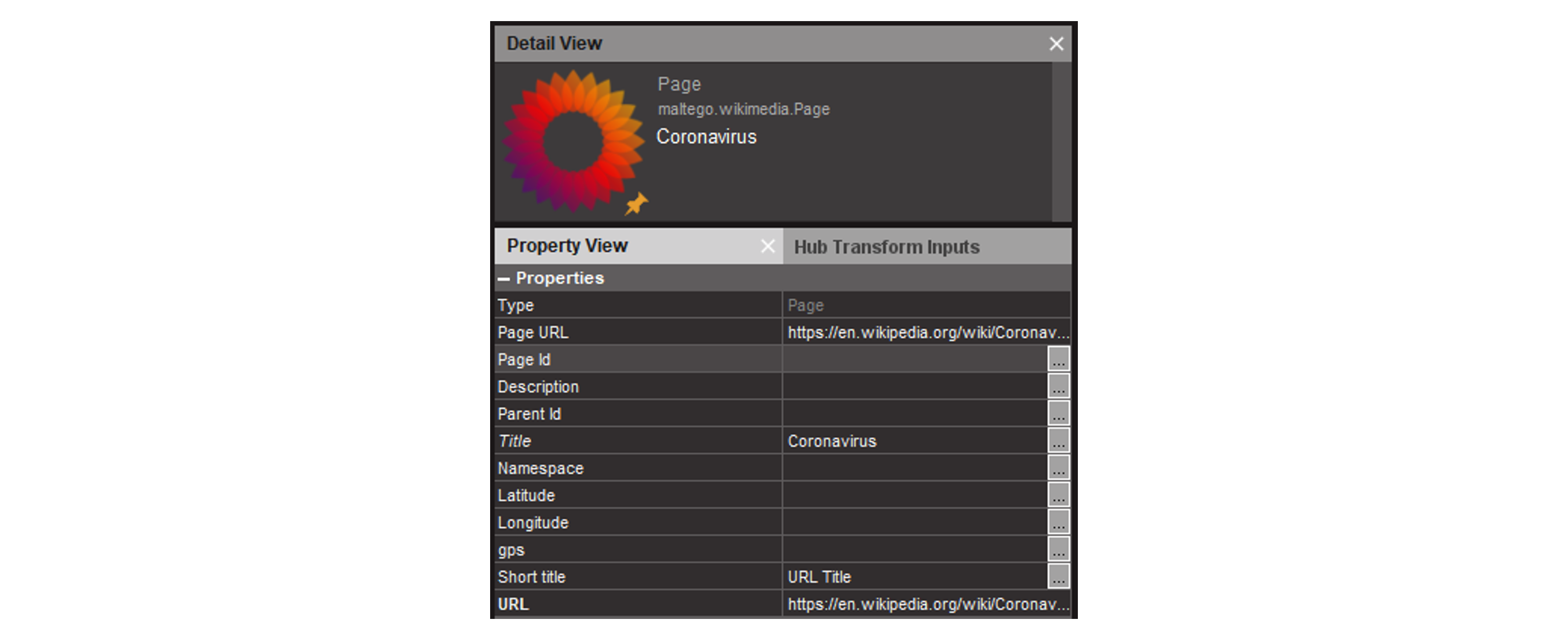
We begin by dragging a Page [Wikimedia Page Entity] onto a new graph. We enter the page URL and the page title into the Property View.
Next, we attempt to discover the edits that have been made to this page by running the To Page Edits [Wikipedia EN] Transform.
Upon running this Transform, we will be prompted to enter a date range in the Required Inputs window. For this example, we will run the Transform with the date range set to Since Epoch time, which by default, will return all edits found for this page since 1970.
For your own investigations, however, you might find that the date range window allows for better efficiency in narrowing down revisions made within a certain time frame. Please note that the exact time stamp needs to be input into the Required Inputs window.
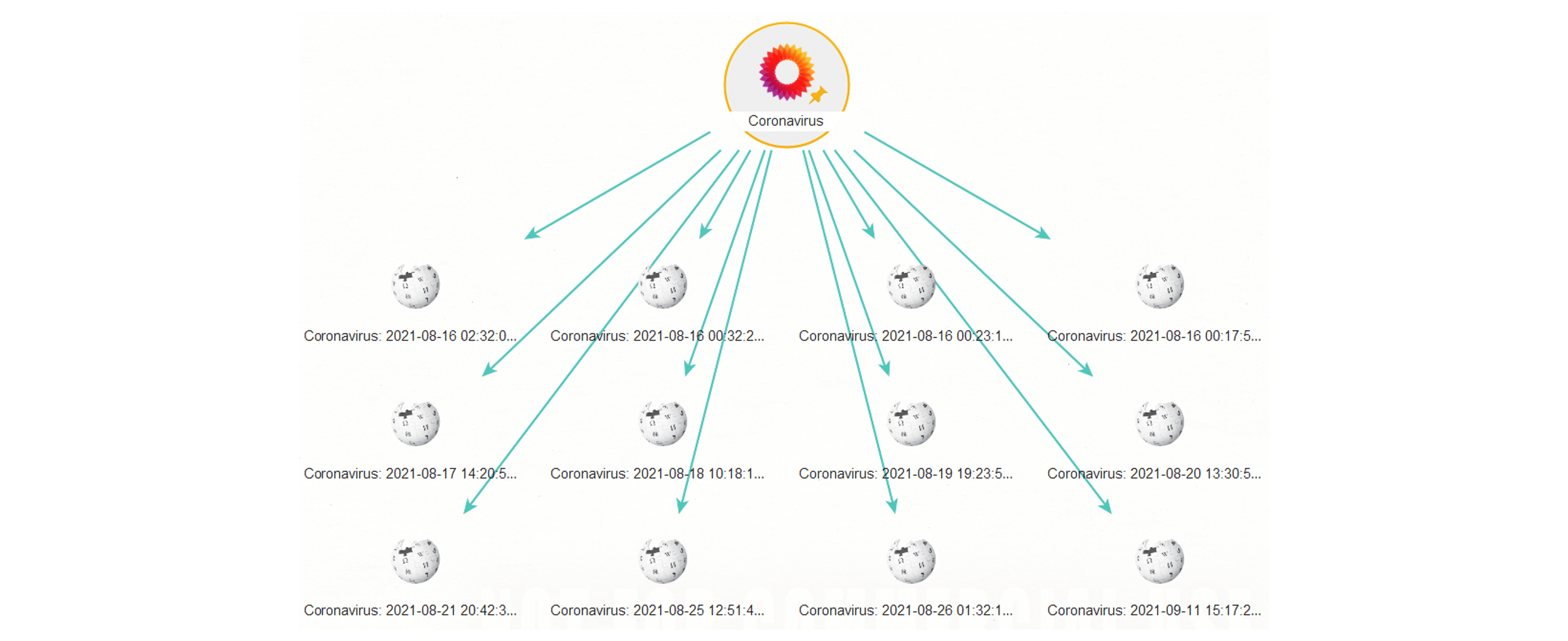
Let’s take a closer look at the Wikipedia Edit Entities returned to our graph.
Selecting one of the Edit Entities, we can discover details such as the name or alias of the page editor or their IP address, the date of the edit, time stamp, user ID, page ID, as well as the editor’s comment.
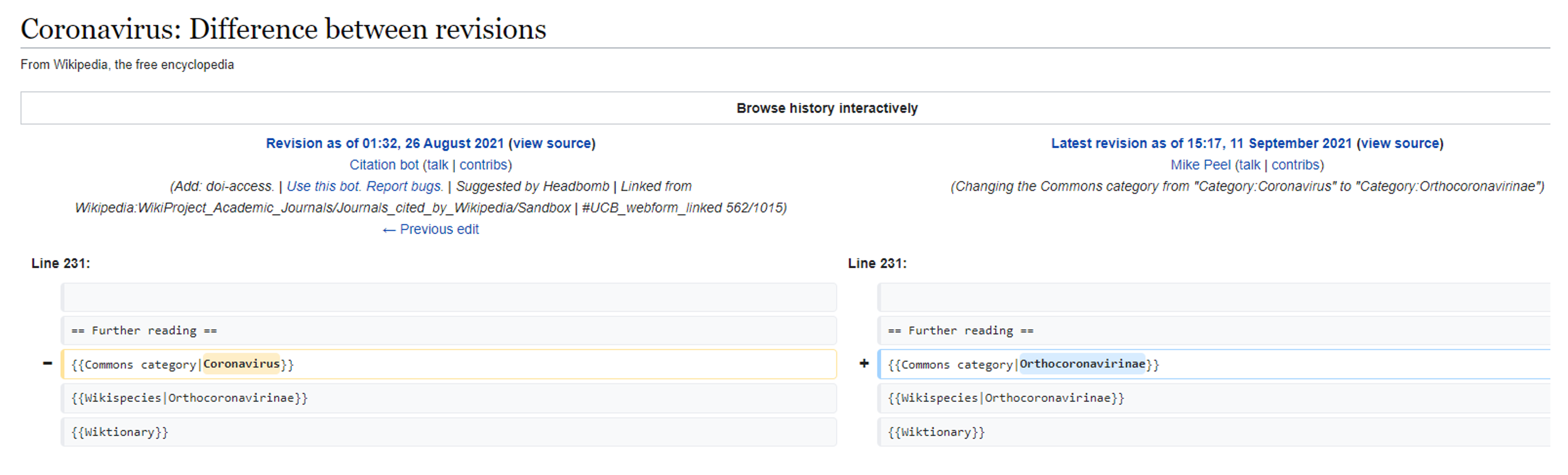
Clicking “revision” will open a URL in your browser showing what was revised/changed for this edit.
Pivoting from an edit, we can also retrieve the editors’ details by running the Get Page Editors [Wikipedia EN] Transform. If the edits were made by a person logged into a Wikipedia account, their name or alias will be retrieved. If the page editor was not logged into a Wikipedia account, we will be able to retrieve their IPv4/6 address.
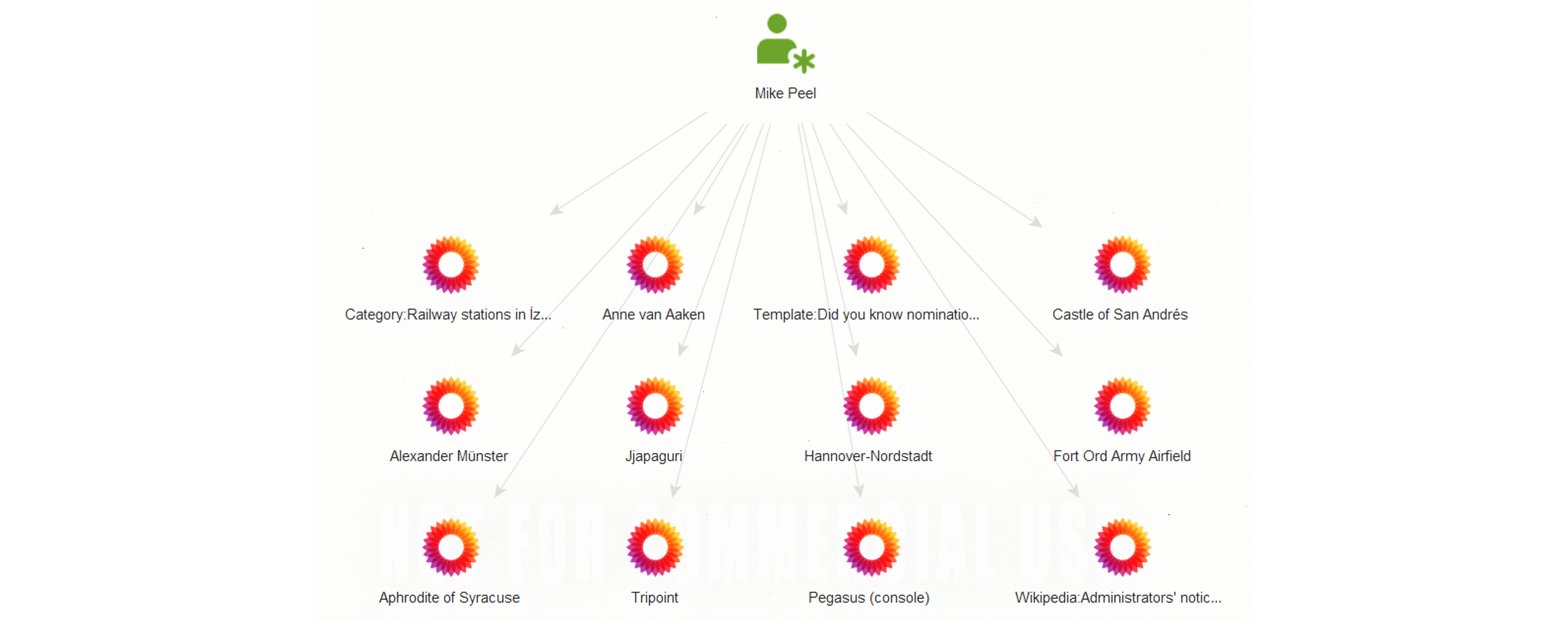
From the returned editor name or alias, we can investigate further using the To Pages Edited [Wikipedia EN] Transform which will return a list of other Wikipedia pages edited by this user’s account.
We hope that you find these updates to the Maltego Standard Transforms beneficial to your investigations!
Don’t forget to follow us on Twitter and LinkedIn and sign up to our email newsletter to stay updated on the latest news, tutorials, and events.