As a follow-up to Part 1 of our deep dive into gathering insights from the Dark Web, this article will focus on how we can use those insights to conduct a brand protection investigation.
One of the ways Maltego Transforms can be used is to query and extract Business Risk Intelligence data from Dark Web forums, torrents, beacons and other sources to pursue different types of investigations.
How Deep & Dark Web Intelligence Enhances Brand Protection Investigations 🔗︎
All activities carried out for brand protection seek to safeguard the reputation of organizations. In the context of this use case, we look at one way to reduce the likelihood of suffering financial losses resulting from insider threats, data breaches or other targeted attacks.
Access to Dark Web data can help organizations to ascertain:
- If the company’s name, products, offices, or VIP employees are being mentioned and in what context
- If the employee or customer credentials and data are being offered for sale after a data breach
- If there is an insider threat resulting in stolen products being sold, or
- If counterfeit products are being traded
Monitor Brand Mentions in the Dark Web & Identify Potential Threats 🔗︎
Let’s walk through a simulated scenario for a small investigation. The goal of this investigation is to monitor mentions of Contoso in the Dark Web and detect possible threats. Please note that the use case we are presenting here is only an example containing “dummy” data created for this purpose and that, as a result, the outcome is fictitious.
Step 1: Starting with a Domain Entity 🔗︎
To begin our investigation, we need to determine which Maltego Entities to use for running data queries. For those of you who are not familiar with Maltego, Entities can be anything from domain names, company names, phone numbers, email addresses, an alias or even a phrase. The Maltego Client provides over 20 standard Entities targeted for use in online investigations and offers a platform where users can build their individual Transforms.
For this example, we will use the “Domain” Entity. We will name this Entity “contoso[.]de”.
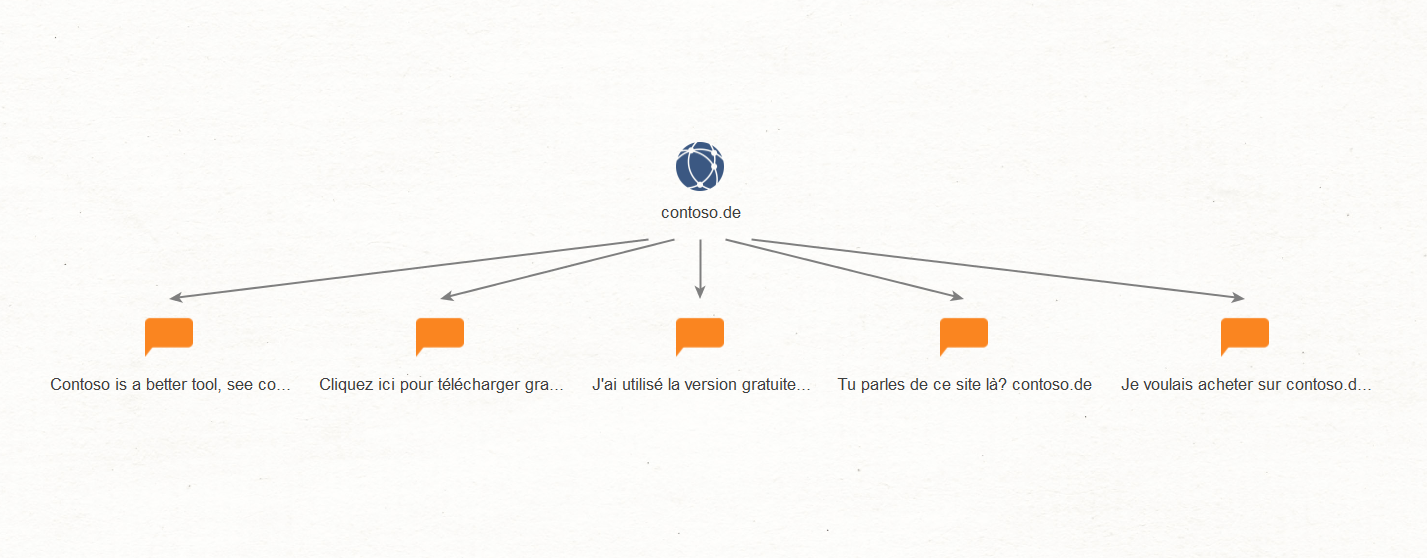
Next, we run a [Domain to Post] Transform (to learn how to run Transforms, click here). We received 5 search results in response to our query. By selecting each of the 5 posts we can read their contents on the Detail View.
Step 2: Analyzing Relevant Posts 🔗︎
After analyzing each of the posts, we can conclude that only the second result—from left to right— may lead to a potential threat, given its offering of what looks like questionable Contoso software.
As some investigations can become quite large, we can bookmark Entities, making it easier to return to specific leads as the investigation deepens. To use the bookmark feature, click the bookmark icon on the right side of the Entity.
The ability to differentiate between the types of leads is important and the Maltego Client allows the possibility of choosing bookmark colors by clicking the bookmark icon. We will bookmark the lead for our investigation in red.
Step 3: Running the Post to Thread Transform 🔗︎
It isn’t enough to know that a threat actor seems to be offering suspicious Contoso software downloads, we need to know if people are responding to him, and what they are getting. We can take this post and run a [Post to Thread] Transform. In this case, the query returns a “Contoso downloads” thread that allows us to continue our investigation.
Disclaimer: the concept of posts and threads varies across forums and sometimes, a post and a thread might be the same. Therefore, running a post to thread Transform might not be a “one-size-fits-all” solution.
Based on the results, we can assume that threat actors are indeed discussing questionable software downloads, that one of them offers downloads, and that some of them are interested in acquiring them.
Step 4: Running the Thread to Forum Transform 🔗︎
In the same way that breadcrumbs can be followed, we now go in search of the forum that hosted this thread by running a [Thread to Forum] Transform. We receive a result for a forum named “FRENCH DDW”.
Uncovering this forum not only further validates our results but also allows us to track down any other posts, threads, and threat actors that might represent a threat to our company. And, if this is a forum unknown to us, we should certainly add it to our list of targets for future monitoring activities!
Step 5: Running the Post to Alias Transform 🔗︎
As a final step, we run a [Post to Alias] Transform, attempting to identify the threat actor. The result returned shows that this individual goes by the screen name—alias—“XXDom”.
Next: Pivoting from Business Risk Intelligence Data to Extensive Investigations 🔗︎
Though this investigation is a simulation, in a real-world case, extending this type of investigation would be largely beneficial, based on results like these.
Extending an investigation means pivoting to and from Business Risk Intelligence data to Social Media, Cyber Threat Intelligence, Cryptocurrencies, OSINT data, etc. These actions could potentially aid investigators to discover not only the real identity of the threat actor, but even their physical location. It goes without saying that we would need to verify any results we derive from an alias e.g. emails, social media profiles, location, etc., as we don’t wish to make any false identifications.
And through this simple 5-step example, we’ve shown the potential of incorporating Business Risk Intelligence data to Maltego investigations to improve threat hunting strategies.
Business Risk Intelligence Data Integrations in Maltego 🔗︎
With Maltego and its Business Risk Intelligence data integrations with Flashpoint, Intel471, and ShadowDragon, visibility into Dark Web data can help organizations reduce the likelihood of an attack and help remediate one by speeding up the investigation and increasing the chances of identifying the responsible threat actor(s).
There are many potential use cases for investigations into Business Risk Intelligence with Maltego, which we will be sharing continuously. In the meantime, do not hesitate to contact our team via support@maltego.com if you have any questions about Maltego, Business Risk Intelligence investigations, and the offerings from our Data Partners.
Until next time!


![Results from [post to thread] Transform with bookmark on a lead Results from [post to thread] Transform with bookmark on a lead](/images/uploads/bri-ii-2.png)
![Results from [post to alias] and [thread to forum] Transforms Results from [post to alias] and [thread to forum] Transforms](/images/uploads/bri-i-3.png)




