Business Risk Intelligence provides valuable insight into threats stemming from the Dark Web. Given that a high number of incidents in the open web and the real world are rooted in the illegal activity taking place there, it has become increasingly relevant for investigators and organizations to gain visibility into and monitor this part of the internet.
But first, we need to understand the different tiers of the internet.
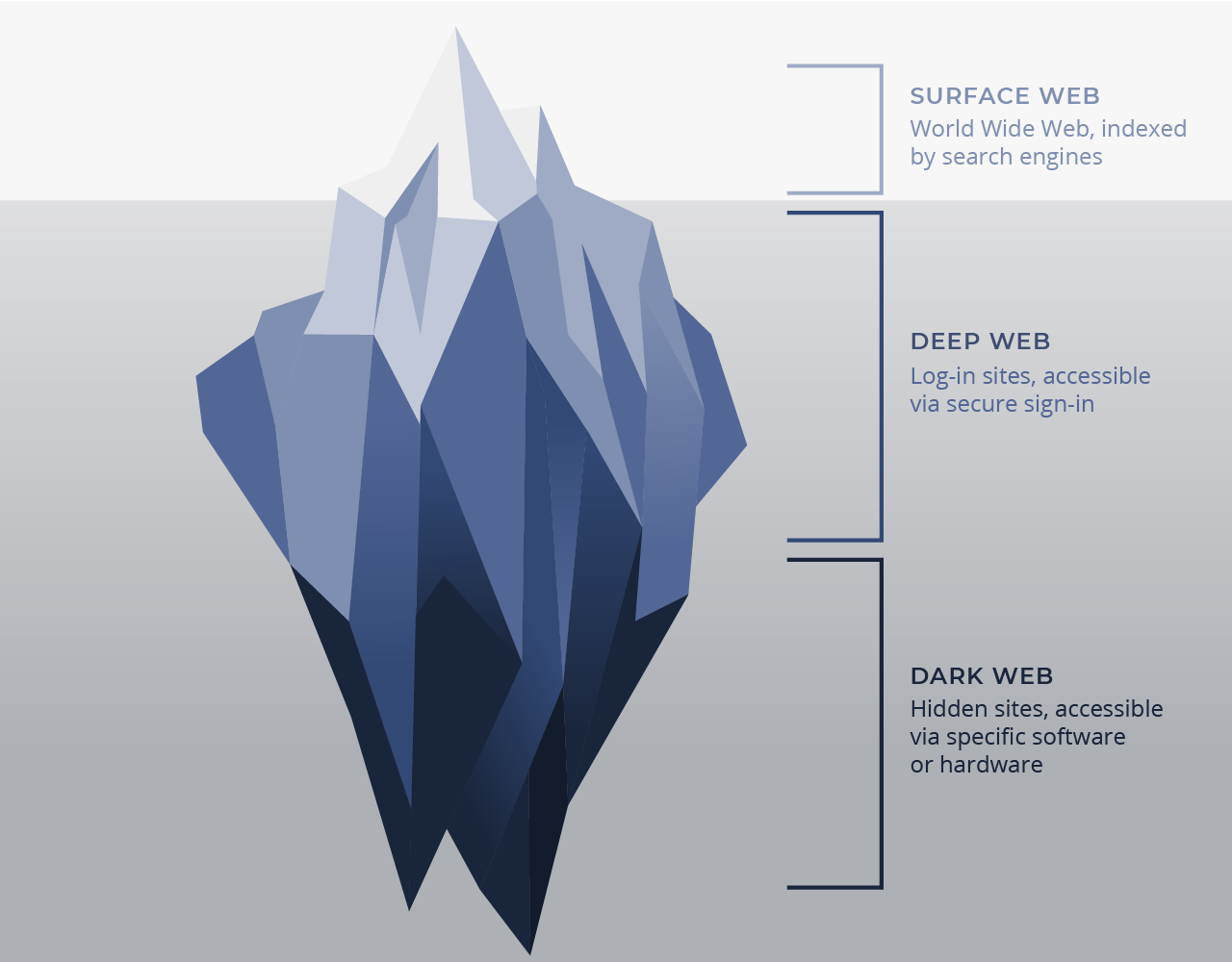
The 3 Tiers of Internet: Surface Web, Deep Web & Dark Web 🔗︎
First Tier: The Surface Web 🔗︎
The first tier is the surface web, a.k.a. the open or public web. Much like the tip of an iceberg, this is the part of the internet that is visible with common search engines such as Google and Bing which return results using page indexing.
All content that can’t be indexed is then invisible to these search engines. This is where the other two tiers of the internet - the Deep and Dark Web - come into play. They represent the non-indexed or invisible areas of the internet.
Second Tier: The Deep Web 🔗︎
The Deep Web is the area of the internet we all frequently access via secure sign-in. The content found here is private in nature and is commonly made up of the data in our personal emails, social media, online banking and other login dependent accounts. This also includes server data from all types of private and public organizations. This content can be accessed through the surface web.
Third Tier: The Dark Web 🔗︎
There are different ways to access the Dark Web. An example of a popular project used for this purpose is The Onion Router hidden service protocol a.k.a. Tor network or Tor Browser, which is undetectable by common search engines. Unlike the surface web, the addresses hosted here end with ‘.onion’ rather than with ‘.com’, ‘.org’, etc.
This part of the internet offers complete anonymity while surfing, and thanks to special encryptions provided by the protocol, website publishers remain anonymous. I2P, Freenet, GNUnet and ZeroNet are alternatives to the Tor Browser, but we won’t go into their specifics at the moment.
The high level of privacy and anonymity in the Dark Web has encouraged the proliferation of ‘dark content.’ For the most part, this type of content is shared in private forums, chats and online marketplaces where illegal goods and services are often traded. Since most payments are made in cryptocurrencies such as Bitcoin, it is almost impossible to track or attribute many of the transactions.
Deep & Dark Web Data Integrations in Maltego 🔗︎
With this in mind, Maltego has actively worked towards empowering investigators by integrating Business Risk Intelligence data providers such as Flashpoint, Intel 471 and ShadowDragon into the Transform Hub. As such, we make it possible to accelerate investigations through graphic analysis and data visualization allowing investigators to gather valuable insights.
This allows organizations using Maltego with Business Risk Intelligence to approach the issue of dark content and the threat it poses to them in a more strategic manner. And, by pivoting to and from data from our other Hub Items such as CipherTrace, SocialNet or Social Links, investigations can be expanded in search for attribution.
Using Deep & Dark Web Intelligence in Maltego for Brand Protection Investigations 🔗︎
In Part 2 of this series, we share demonstrate how investigators can protect their brands by querying deep and dark web intelligence in Maltego. Explore the use case and enhance your investigations now!
To stay up to date with other cool use cases, product updates and Maltego events, follow @MaltegoHQ on Twitter. If you have questions, requests, ideas or use cases you built that you want to share, we would love to hear from you on Twitter!